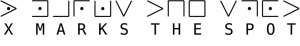Holly Tucker's Blog, page 74
December 5, 2012
Mysterious Cipher Cracked 300 Years Later
by Annie Vreeland (Vanderbilt University)
 75,000 characters, 90 different cipher letters, 105 pages, and 300 years later, Kevin Knight and his colleagues finally cracked the mysterious Copiale Cipher. The Copiale Cipher is a manuscript from the 18th century belonging to a German secret society known as the “Oculist Order.” The only plaintext that appears among the mix of Roman and Greek letters and abstract symbols is “Philipp 1866,” the alleged owner of the manuscript, and “Copiales 3,” which is where the secret document got its name. The document was discovered in a library in East Germany in 1970, but was neglected until 2011 when teams in the US and Sweden cracked, studied, and released the Cipher. Kevin Knight, a computer scientist at the Information Sciences Institute at the University of Southern Califonia, started deciphering the Copiale Cipher as a weekend project. Knight’s curiosity overtook him and he began to collaborate with Beata Megyesi and Christiane Schaefer of Uppsala University in Sweden, who helped him decipher the first 16 pages of the document.
75,000 characters, 90 different cipher letters, 105 pages, and 300 years later, Kevin Knight and his colleagues finally cracked the mysterious Copiale Cipher. The Copiale Cipher is a manuscript from the 18th century belonging to a German secret society known as the “Oculist Order.” The only plaintext that appears among the mix of Roman and Greek letters and abstract symbols is “Philipp 1866,” the alleged owner of the manuscript, and “Copiales 3,” which is where the secret document got its name. The document was discovered in a library in East Germany in 1970, but was neglected until 2011 when teams in the US and Sweden cracked, studied, and released the Cipher. Kevin Knight, a computer scientist at the Information Sciences Institute at the University of Southern Califonia, started deciphering the Copiale Cipher as a weekend project. Knight’s curiosity overtook him and he began to collaborate with Beata Megyesi and Christiane Schaefer of Uppsala University in Sweden, who helped him decipher the first 16 pages of the document.
Imagine receiving a 105-page note that was comprised of a combination of letters and abstract symbols, with no word spacing, no chapter breaks, and no illustrations – where would you even start the decoding process? Kevin Knight, Dr. Beata Megyesi, and Christiane Schaefer asked themselves the same question. Not knowing the language or topic of the document, they went with their gut feeling and assumed that the letters sprinkled throughout the text were Roman and Greek characters. The code breaking team tried 80 different languages, when they finally decided to give up on their hypothesis. It turns out the letters were nulls, meaning they were thrown into the mix to confuse and mislead readers, “somewhat like how pig Latin adds the suffix ‘ay’ to words in an attempt to confuse listeners” (LiveScience 2011). The only meaningful characters left for Knight and his team to decode were the abstract symbols that had never been seen before.
The team then came up with a theory that similar shapes represented the same letter or groups of letters, “for instance, the symbols with the circumflex ^ over them were actually the letter “E” (LiveScience 2011). This means that the Copiale Cipher is an advanced substitution cipher; basically letters like “th” are replaced with symbols such as _*. At this point, it would be helpful to know what language to translate these symbols into. Knight and his team hypothesized that the plaintext language was most likely German, as the book was located in Germany and the spelling of ‘Philipp’ in the inscription was German. So thus far, Knight assumed that it is a substitution cipher, where letters are replaced by symbols, and the plain text language is German. The next step he took was to look at the frequency analysis. This is where the computer calculates how often different symbols occur and where they occurred together. They found one three-symbol combination in the cipher text that translated into “cht,” a standard German trio, which confirms their hypothesis. The frequency analysis allowed them to evaluate what letters are most common in German and compare it to what letters appear most often in the cipher, which is how Knight could tease out enough letters to identify the words “Ceremonies of Initiation” followed by “Secret Section.” At this point, after many possibilities are eliminated and the team was set on a hypothesis and started to use the computer as an aid to fully translate the document.
The 75,000-character document was written on double-watermarked paper and was bound by gold and green brocade paper. The manuscript was found after the Cold War in the “archive of the East Berlin Academy, which later merged with West Berlin Academy to become the Academy of Arts, Berlin” (Baker 2012). Analysts of the paper believe it dates back to around 1760-1780. Although the origin of the Copiale cipher is unknown, Knight and his team were able to make sense of the entire plaintext. They found that the manuscript was divided into three parts. The first part of the document described the Oculist society rituals, the second part discusses other 18th century Masonic rituals, and the third part discussed other forms of modern Freemasonry. The Society’s rituals include “the initiation of a candidate and the first few degrees of progression” (Baker 2012). During this time, the book of Oculist society law was presented, the apprentice learned secret lessons, and there were ceremonies of initiation. If someone wanted to be initiated into this society, they must first pledge secrecy and fidelity to the Oculist society. They are then presented with a blank piece of paper and asked to read it aloud, but confess that they do not have the ability to read it. They are then given eyeglasses and asked to try reading aloud again and the answer is still no. But wait, the ritual gets weirder: the Master then plucks a hair from the candidate’s eyebrow and washes his eyes. When the candidate looks back down at the blank sheet, there is a book of teaching for apprentices instead. With the instructions from this book on how to behave as an apprentice, the pledge is finally initiated into the society. The second part of the Copiale document describes typical 18th century Masonic rituals. The final part “provides an insight into other forms of contemporary Freemasonry,” (Baker 2012) for example the Scottish rites that were popular in Germany at that time.
The Copiale Cipher is a newly discovered and deciphered code that allows us to look into the customs of a German secret society. From the brief description of the ritual, it appears that the Oculist Order was obsessed with ophthalmology, the study and treatment of the eye. Interestingly enough, Knight claims that the symbol of many secret societies is the eye, which helps to explain the society’s fixation. This insight also implies that the members of the Oculist Order were not necessarily ophthalmologists themselves. On another note, this cipher is special because many Masonic ciphers still remain unbroken today. The fact that Knight has cracked this cipher provides other code breakers with techniques and algorithms that can be used in machine translation and are useful when deciphering other unknown texts. Following Knight’s efficient deciphering technique, you now have all of the tips for deciphering that mysterious 105-page note that lands on your doorstep.
This post is part of a series of essays on the history of cryptography produced by students at Vanderbilt University. The students wrote these essays for an assignment in a first-year writing seminar taught by mathematics instructor Derek Bruff. The essays are shared here, in part, to give the students an authentic and specific audience for their writing. For more information on this cryptography seminar, see the course blog.
Works Cited:
Baker, D. (2012, June 22). The Oculist’s Secret Society. The Optician, 243(6357), 22-23. doi:1026948309
LiveScience, C. C. (2011, October 26). Copiale Cipher: How a Secret Society’s Code was Finally Cracked. The Christian Science Monitor, Science. doi:900584643
Image: “eye,” Helga Birna Jónasdóttir, Flickr (CC)
Prying Open the Pigpen Cipher
by Marco Tiburcio (Vanderbilt University)
 Today, your local, run-of-the-mill inmate – say, inmate 3087A, passes a note along to inmate 2065B. Circa 1863, a Union prisoner of the Confederate Army secretly sends a letter describing his whereabouts to his fellow troops. In the early 18th century, a Masonic text, some letter of correspondence or sacred order, is recorded by one of the most interesting and elusive societies to have ever existed.
Today, your local, run-of-the-mill inmate – say, inmate 3087A, passes a note along to inmate 2065B. Circa 1863, a Union prisoner of the Confederate Army secretly sends a letter describing his whereabouts to his fellow troops. In the early 18th century, a Masonic text, some letter of correspondence or sacred order, is recorded by one of the most interesting and elusive societies to have ever existed.
Separated by generations, all three instances share a single commonality – the inmate, soldier and Freemason would each be able to read each other’s notes despite the fact that, for the sake of secrecy, they are not writing in the standard English alphabet. No, they are not drawing pictures (although they kind of are), and no, they are not simply writing in a different language (although they might as well be). What they are in fact doing is employing a cipher system which dates back to the dawning of Freemasonry. This cipher, for the time being, can be referred to as the Masonic or Rosicrucian cipher (Pratt, 1942).
Unfortunately for the prisoner, soldier and Freemason, none of their messages are relatively secure. Surely, an inmate has plenty at stake if the contents of his message are intercepted – perhaps a few more years to his sentence. And of course, the military application of a cipher should ensure a safeguard against enemy eyes. The concept is pretty simple. Ciphers or codes are born from secrecy, serve secrecy, and by way of function, are themselves kept secret. So why is it that you, I, or even a school child can decipher the very same coding system used by one of the most cryptic societies to have ever existed? It’s a little embarrassing.
To answer this question, an understanding of the cipher’s historical context and mechanical construction is necessary. True to its name, the masonic cipher was supposedly created, and knowingly employed, by the Freemasons. Freemasonry, as it is called, falls under the category of “secular fraternal organization” (MacNulty, 2006 p. 9). To define it in more concrete terms, “…it is a society of religious men in the sense that it requires its members to believe in the existence of a ‘Supreme Being’” (MacNulty, 2006 p. 9). In accordance with their “….commitment not to reveal certain things,” the fraternity created its own cipher, which bares resemblance to that of the ancient Knights Templar (MacNulty, 2006 p. 269). Its first date of use, however, remains unknown due to the fraternity’s secrecy (Pratt, 1942).
Interestingly enough, the cipher is a simple substitution cipher in which each letter of the alphabet in use is assigned a different letter or symbol (Butler & Keeney, 2001). Both in theory and practice, this type of cipher is considerably weak, especially if the construction of the cipher involves a notable pattern, which the Freemason’s cipher does.
Example of a pigpen cipher and its deciphered message.
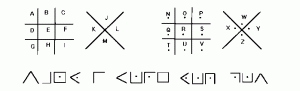
Its construction, though best explained visually, can be defined as the arrangement of an alphabet into a series of grids. Though there exist many variants of the cipher, the masonic cipher follows the illustrated principle. The twenty-six letters of the alphabet are arranged into “two Tic-Tac-Toe grids and two diagonal variations of the grid” (Butler & Keeney, 2001 p.159).
Because each pair of grids is identical in shape and form, one of each pair is distinguished by the placement of dots within each cell of that grid. This results in four differing grids with one letter in each individual cell: one tic-tac-toe grid with dots, one without, one diagonal grid with dots, and another without. Because the grids represent pigpens or tic-tac-toe grids, the cipher is more commonly and creatively referred to as the pigpen cipher, or the tic-tac-toe cipher (Butler & Keeney, 2001).
The cipher is employed by representing each plaintext letter with the cell surrounding it, resulting in a message encoded by a series of varying, though similar, geometrical shapes as shown below.
The construction of the pigpen cipher. The cipher text here reads “Mary I love you too.”
The simplicity of the pigpen cipher allows for several important strengths. Firstly, and perhaps most importantly, the cipher is considerably easy to learn. Minimal math is involved, little time is consumed, and the symbols are only as complicated as you make them out to be.
Secondly, the pigpen cipher is relatively easy to memorize. Because the code can be committed to memory, a tangible and potentially intercepted key need not exist. This is the problem with many ciphers throughout history, for their keys would be intercepted, thus making that current key useless in practice (Kahn, 1996). The cipher is also very versatile. Because the construction, order of letters and orders of the grids and cells is entirely up to the cryptographer, many variations of the cipher exist.
Unfortunately for those using the cipher, simplicity also gives way to weakness. For starters, the cipher is easy to recognize if one is familiar with its construction. Notice a series of slightly varying symbols and voila, you can immediately attempt decryption. At said stage of decryption, one might realize that it is almost as easy to crack as it is to recognize (obviously a major fault in the cryptographic world). Simply arrange the cells into their respective grids, and through intuition of trial-and-error and frequency analysis (in which you assume the most common symbols correspond to the most common letters in the English language), arrange the letters until a coherent message is formed.
So why, then, did the Freemasons encourage this weak method of encryption? Simply put, back in the 1700s, you only had to hide text from those who could actually read. Provided that someone with prying eyes was literate, the fact that the cipher was relatively new to the era also served as a buffer for decryption. Hopefully now, given a message in pigpen, you or I would have some luck decrypting it. In the 1700s, however, the cipher would surely stump us for lack of familiarity.
In fact, in December of 1863, the pigpen cipher stumped the Union army (Kahn, 1996). After intercepting an envelope addressed to a rebel agent, Postmaster Abram Wakemen of New York turned the letter over to the Secretary of War. The letter, as you might have guessed, was entirely enciphered in “…a complicated mixture of symbol ciphers” (Kahn, 1996 p.218). Unable to decrypt the intended message, the War Department handed the responsibility to the “Sacred Three.”
David Homer Bates, Albert B. Chandler and Charles A. Tinker, the accomplished cryptographers referred to as the “Sacred Three,” first noticed the five different kinds of signs used in the text (representing the five different types of grids used). They also had some luck in that commas separated each word from another, as would spaces in plaintext. Whoever encrypted the message was even courteous enough to leave some plaintext in the letter. But most importantly, in a flash of insight, Bates recognized the use of a pigpen cipher, “which had been used as a price marker in the Pittsburgh store in which he had worked as a boy” (Kahn, 1996 p.219).
By focusing on the heading, which included the standard date and address from which the letter was sent, the three deciphered the message within four hours “with the President hovering about anxiously” (Kahn, 1996, 219). Despite the presidential motivation, this argues against the security of the cipher. As it turns out, the message included details regarding the manufacture of Confederate plates for printing money, all of which were promptly seized shortly after decryption.
Flash-forward by a century and a half, and today the pigpen cipher has made its mainstay in the prison and crime underworld, where it persists and evolves as inmates and criminals avoid detection by the authorities. Surprisingly, the cipher need not be written, for it can be spoken. In the spoken variation, each letter of the alphabet is assigned a number. The grids of the pigpen cipher are then used to arrange the letters in some order, and numbers are assigned one per cell from left to right across all of the grids. An inmate, in order to express himself, would simply shout the numbers from his cell, essentially spelling out all of the words he wishes to communicate (Butler & Keeney, 2001).
The “Clock Code” method has also evolved from the pigpen cipher. Around the perimeter of a single grid, twenty-four letters are arranged, with two in the center. The letters are each marked by their orientation in respect to the center of the grid, and a time of day is designated, which designates where A would be, followed in succession by each letter of the alphabet. This variation is best noted for its versatility (Butler & Keeney, 2001).
The pigpen cipher, therefore, has persisted by its convenience and flexibility, rather than security. Though borne out of secrecy, it is forged in simplicity, and is thus used today as a quick substitute for plaintext conversations, or stimulating puzzle for schoolchildren. Despite its relative lack of complexity and challenge, it is interesting to note its use and relevance throughout the centuries and in today’s modern society. That said, in preparation for a run-in with the law, initiation into Masonic society, or capture by Confederate troops (the likes of which deserves a blog post all its own), practice the pigpen cipher for yourself here, or pick up the nearest children’s spy novel in which you’ll be sure to find some example of this simple cipher.
This post is part of a series of essays on the history of cryptography produced by students at Vanderbilt University. The students wrote these essays for an assignment in a first-year writing seminar taught by mathematics instructor Derek Bruff. The essays are shared here, in part, to give the students an authentic and specific audience for their writing. For more information on this cryptography seminar, see the course blog.
References
Butler, W. S., & Keeney, L. D. (2001).Secret messages: concealment, codes, and other types of ingenious communication. New York: Simon & Schuster.
Kahn, D. (1996). The codebreakers: the story of secret writing ([Rev. ed.). New York: Scribner.
MacNulty, W. K. (2006). Freemasonry: symbols, secrets, significance. London: Thames & Hudson.
Pratt, F. (1942). Secret and urgent; the story of codes and ciphers.. Garden City, N.Y: Blue Ribbon Books.
Sinkov, A. (1968). Elementary cryptanalysis; a mathematical approach.. New York: Random House.
Images: “In Code,” Jonathan_W, Flickr (CC); “A pigpen message,” Wikimedia Commons; “Pigpen,” Ron Gervais
December 4, 2012
Shakespeare’s Secrets: A Hidden Cipher in Literature’s Greatest Works?
by Kristin Davis (Vanderbilt University)
William Shakespeare has for centuries been considered one of the greatest literary figures of all time, but a secret cipher hidden within the very pages of his plays may tell an exceedingly different story, one of forbidden marriages, a forgotten prince, and most of all, the genius of one man: Francis Bacon.
Born in sixteenth century England, Sir Francis Bacon was not only Lord Chancellor of England under James I, but was also a brilliant philosopher (British Broadcasting Company, 2012). Though not appreciated in his time, one of Bacon’s greatest achievements was a simple cipher he incorporated in his written works called the Baconian cipher (Sherman, 2010). The Baconian cipher does not possess great strength against decryption; instead its immense power and intrigue resides in its ability to make mystery lie, or appear to lie, in everything.
 While most ciphers’ strengths dwell in the difficulty of finding the key to unlock a pattern, the Baconian cipher’s power lies in the challenge of uncovering its existence (Sherman, 2010). The cipher is only a simple substitution cipher in which one letter (or group of letters) stands for one other letter. The letters never change what they stand for as long as the same key is used throughout a message (Worley III, 2003). The Baconian cipher employs this substitution method by assigning a string of five letters consisting of only a’s and b’s to each letter in the alphabet. The arrangement of a’s and b’s in the five letter sequence determines the alphabet letter in the message (Worley III, 2003).
While most ciphers’ strengths dwell in the difficulty of finding the key to unlock a pattern, the Baconian cipher’s power lies in the challenge of uncovering its existence (Sherman, 2010). The cipher is only a simple substitution cipher in which one letter (or group of letters) stands for one other letter. The letters never change what they stand for as long as the same key is used throughout a message (Worley III, 2003). The Baconian cipher employs this substitution method by assigning a string of five letters consisting of only a’s and b’s to each letter in the alphabet. The arrangement of a’s and b’s in the five letter sequence determines the alphabet letter in the message (Worley III, 2003).
If a message contained only strings of a’s and b’s, it would be quite obvious to a cryptologist that some sort of cipher was used. Francis Bacon’s genius lies not in this simple substitution cipher, but in the fact that his cipher could be wielded to make, in Bacon’s own words, “anything mean anything” (Sherman, 2010). With the extra twist of steganography, which is concealing messages through deception, a-form and b-form can be two types of anything, from black and white to plus and minus, not just text (Sherman, 2010).
In Bacon’s traditional method, he replaced a’s and b’s with a-form fonts and b-form fonts (Worley III, 2003). For example, an enciphered message would be created by writing a seemingly innocuous message then changing the font of the letters so that bolded letters represent a’s and italicized letters represent b’s (Worley III, 2003). To decipher the message, the recipient would identify the a-forms and b-forms and use Bacon’s key to determine the alphabet letter signified by the string of five forms.
Innocuous Message
This is a Baconian cipher text
Cipher Text
Codes
C / O / D / E / S
aaaba/abbab/aaabb/aabaa/baaab
Process of Enciphering
aaaba/abbab/aaabb/aabaa/baaab
This i/s a Bac/onian/ ciphe/r text
Steganography
This is a Baconian cipher text
Being at its base only a substitution cipher, the method needed to break the plain cipher requires only knowledge of letter frequencies in the English language (Singh). To break the cipher, one first needs to accomplish the most challenging task of identifying the cipher is being employed. Next, one separates the letters of the message into groups of five and identifies the pattern of a-forms and b-forms. Because one five-letter group stands for one alphabet letter, one looks up the known frequencies of letters in English and matches them up with the frequency each five-letter group appears in the message (Worley III, 2003). For example, if the pattern “aabba” appears twelve percent of the time in the message, and the letter that appears twelve percent of the time in English is “e,” it can be inferred that “aabba” stands for “e.” Though cryptanalysis seems simple, this assumes the cryptologist first knows the cipher exists. Without a careful eye, a cryptologist could pass over the cipher not knowing its existence or spend years fruitlessly and frustratingly looking for something that was never there.
 The unique complexity and mystery of the Baconian cipher has enticed cryptologists for generations to find patterns in chaos and hidden messages in everything from poetry, music, and most famously, Shakespeare. Though Bacon’s cipher was never adopted for military purposes, and Bacon only created it for his own amusement, his cipher took the literary world by storm (Sherman, 2010). Much like seeing pictures in the clouds or faces on the moon, cryptography enthusiasts began to see hidden a-form and b-form letters in everything.
The unique complexity and mystery of the Baconian cipher has enticed cryptologists for generations to find patterns in chaos and hidden messages in everything from poetry, music, and most famously, Shakespeare. Though Bacon’s cipher was never adopted for military purposes, and Bacon only created it for his own amusement, his cipher took the literary world by storm (Sherman, 2010). Much like seeing pictures in the clouds or faces on the moon, cryptography enthusiasts began to see hidden a-form and b-form letters in everything.
One of the most famous results of Bacon’s cipher was widely considered “The Greatest of Literary Problems” (Sherman, 2010). After Shakespeare’s plays were written, literary analysts began to doubt that William Shakespeare of Stratford had been the true playwright (Sherman, 2010). The anti-Stratforians, as they called themselves, argued that Shakespeare, the uneducated, barely literate peasant, could not have produced such grand works (Baxter, 1915, p. 548). A promising alternative to the Stratford Shakespeare was Sir Francis Bacon (Sherman, 2010). After the discovery of De Augmentis, in which Bacon himself explains the workings of his cipher explicitly, literary analysts scoured the Shakespeare plays for the Baconian cipher (Friedman, 1957, p. 189).
In the early twentieth century, a prominent figure in the search, schoolteacher Elizabeth Wells Gallup, claimed to have broken the Baconian cipher found in the Shakespeare plays by analyzing the original folios to produce “alphabet classifiers” that determined whether a letter was an a-form or b-form (Sherman, 2010). Gallup deciphered pieces of text that seemed to indicate that Francis Bacon not only wrote the works historically contributed to Shakespeare, but also works of Spenser, Peele and Green, and Marlowe (Gallup, 1910, p. 17). Most consequential of all was that the cipher text claimed that the Virgin Queen Elizabeth I was no virgin at all, but actually the mother of Francis Bacon (Gallup, 1910, p. 6). This history-altering revelation meant that Bacon would have been the rightful heir to the throne and therefore the last Tudor, not Elizabeth (Gallup, 1910, p. 6). During Elizabeth Gallup’s time, even well respected thinkers such as Mark Twain, Walt Whitman, Sigmund Freud, Henry James, Henry Miller, and Helen Keller were “Baconians” (Sherman, 2010). As Gallup’s theories generated interest within the general public, millionaire businessman George Fabyan organized a group of cryptographers who worked on, as Fabyan explained, “wrestling from Nature, her secrets” (Sherman, 2010).
Fabyan not only greatly expanded Gallup’s work on the Shakespeare ciphers, but also more importantly introduced a young William Friedman to Francis Bacon’s ciphers (Sherman, 2010). Starting as an assistant to Gallup, Friedman began to doubt the methods used to decipher the texts (Friedman, 1957, p. 210). William Friedman and his wife, Elizebeth Friedman, began to notice inconsistencies in Gallup’s method of determining a-form letters and b-form letters (Friedman, 1957, p. 210). Friedman observed that often only Gallup would be able to see the differences in fonts and would often change her methods to “fix errors” to make the cipher text intelligible (Friedman, 1957, p. 210). Though Friedman would later disprove Gallup’s methods altogether and determine the Shakespeare project futile, this first exposure to the world of ciphers created the man that would soon go on to be one of history’s greatest cryptographers (Sherman, 2010).
Friedman was such a proponent to the development of cryptography that he not only coined the term “cryptanalysis,” but also served as chief cryptographer of United States for more than thirty years, co-invented the US Army’s best cipher machine, broke the Japanese PURPLE code in World War II, and wrote papers that gave cryptography its mathematical foundations (Sherman, 2010). Throughout his life, Friedman remained fascinated by the Baconian cipher that began his career.
While a colonel in the army, Friedman kept on his desk a picture of soldiers to whom he had just taught a class about cryptography. Though at first the picture seems like any other war memento, on closer examination one might notice how some soldiers are not looking at the camera. An even sharper eye might notice that the pattern of looking towards and away from the camera spells out Friedman’s favorite Baconian axiom: knowledge is power (Sherman, 2010).
Though Bacon may not have enciphered messages that he authored Shakespeare’s plays or was the son on Queen Elizabeth I, Bacon’s cipher and the reactions to it changed not only the field of cryptography, but also the future of technology. Bacon, with his two-letter alphabet, was, according to the Center Cryptologic History, “the inventor of the binary code that forms the basis of modern … computers” (Sherman, 2010). Though the authorship mystery of Shakespeare may never be solved, Bacon’s cipher created the career of one of the greatest cryptographers of all time and formed the basis for binary code, the language of computers. Francis Bacon’s ability to hide mystery within the mundane forced others to look past the obvious to appreciate the mystery within everyday life.
This post is part of a series of essays on the history of cryptography produced by students at Vanderbilt University. The students wrote these essays for an assignment in a first-year writing seminar taught by mathematics instructor Derek Bruff. The essays are shared here, in part, to give the students an authentic and specific audience for their writing. For more information on this cryptography seminar, see the course blog.
Works Cited
Baxter, J. P. (1915). The Greatest of Literary Problems. New York: Houghton Mifflin Company. British Broadcasting Company. (2012). Francis Bacon. Retrieved October 27, 2012, http://www.bbc.co.uk/history/historic_figures/bacon_francis.shtml.
Friedman, W. F. (1957). Shakespearean Ciphers Examined. Cambridge: Cambridge University Press.
Gallup, E. W. (1910). Concerning the Bi-literal Cypher of Sir Francis Bacon: Pros and Cons of the Controversy. London, England: Howard Publishing Company.
Sherman, W. H. (2010). How to Make Anything Signify Anything. Cabinet (40).
Singh, S. (n.d.). Substitution Ciphers. Retrieved October 27, 2012, from The Black Chamber: http://www.simonsingh.net/The_Black_Chamber/crackingsubstitution.html.
Worley III, G. G. (2003, February 26). Baconian Cipher. Retrieved October 25, 2012, from Computer Science at the University of Central Florida: http://www.cs.ucf.edu/~gworley/files/baconian_cipher.txt
Pictures
Bacon, F. (1623). De Augmentis Scientiarum Libri IX. London: In officina Ioannis Hauiland.
Bacon, F., Spedding, J., Ellis, R. L., & Heath, D. D. (1882). The Works of Francis Bacon. London: Longman.
The Lorenz Cipher and the World’s First (Secret) Computer
by Emily Dinino (Vanderbilt University)
When people think about cryptography during World War II, they typically imagine the Enigma, an enciphering machine built by the Germans. When people think of the first programmable computer, they might recall the ENIAC, developed at the University of Pennsylvania in 1945. However, few people know of the Lorenz cipher machine, or the real first electronic calculator, Colossus.
 After the epic failure of their World War I cryptography efforts, Germans entered WWII dedicated to building the ultimate cipher. Germany employed The Lorenz Company to design a teleprinter cipher that would ensure secure radio communication. The Lorenz Company built teleprinters using a strategy created by American Gilbert Vernam in 1918. The teleprinters were based off of the 32-character Baudot Code, as opposed to the standard 26-letter alphabet used in other ciphers, such as the Enigma. The Baudot Code consists of five rows and some number of columns. Each letter is represented by a sequence of 5 symbols, one symbol per row, where each symbol is either a dot or cross. For instance, the letter A might be represented by +..+.+. Random characters were inserted into the cipher text to conceal the message. Plain text was converted to symbol representation and combined with these obscuring letters to produce the cipher text. When the receiver combined the cipher text message with the exact same set of obscuring characters, they can undo the process and reveal the plain text. Vernam had concluded that if the paper used in communication was pre-punched with a completely random set of excess characters, the cipher would be unbreakable. This essential element of the cipher required that both ends of communication use the same pre-punched paper, which was impossible in wartime (Carter).
After the epic failure of their World War I cryptography efforts, Germans entered WWII dedicated to building the ultimate cipher. Germany employed The Lorenz Company to design a teleprinter cipher that would ensure secure radio communication. The Lorenz Company built teleprinters using a strategy created by American Gilbert Vernam in 1918. The teleprinters were based off of the 32-character Baudot Code, as opposed to the standard 26-letter alphabet used in other ciphers, such as the Enigma. The Baudot Code consists of five rows and some number of columns. Each letter is represented by a sequence of 5 symbols, one symbol per row, where each symbol is either a dot or cross. For instance, the letter A might be represented by +..+.+. Random characters were inserted into the cipher text to conceal the message. Plain text was converted to symbol representation and combined with these obscuring letters to produce the cipher text. When the receiver combined the cipher text message with the exact same set of obscuring characters, they can undo the process and reveal the plain text. Vernam had concluded that if the paper used in communication was pre-punched with a completely random set of excess characters, the cipher would be unbreakable. This essential element of the cipher required that both ends of communication use the same pre-punched paper, which was impossible in wartime (Carter).
Unable to implement this security feature of Vernam’s original concept, The Lorenz Company instead designed a machine that would create these excess characters. However, the machine was unable to produce completely random characters; the characters the machine did produce were referred to as “pseudo-random.” Lacking Vernam’s intended stream of random information mixed among the real cipher text, the transmissions did not properly hide the cipher text. Bletchley Park, Britain’s decryption establishment, ultimately capitalized on this seemingly small error—the lack of complete randomness—to decrypt the Lorenz cipher (Sale).
The British first intercepted German communications enciphered with the Lorenz cipher in 1940. John Tiltman, a codebreaker at Bletchley Park, was intrigued by these teleprinter messages, referred to by the codename “Fish.” Tiltman was familiar with the Vernam system and soon recognized that the messages enciphered with the Lorenz cipher utilized the Vernam method. A section of Bletchley Park, known as the Testery, was dedicated to decrypting the German teleprinter messages. The Testery had little success until August 30, 1941, when the Germans made a crucial mistake.
A German operator was transferring a 4,000 character message from one station of the German Army High command to another operator at a different site, possibly Athens to Vienna. The operator used his Lorenz machine to send the receiving operator an indicator that was twelve letters long and used German names. The receiving operator used this information to set up his machine and told the sending operator to go ahead and send the message. The sending operator sent 4,000 characters by hand before the receiving operator replied in German: “didn’t get that – send it again.” Both the sending and receiving operators reset their Lorenz machines to the initial position, a completely prohibited action. The sending operator, once again, keyed in the message by hand.
The crucial mistake occurred in human error. Had the sending operator worked like a machine, the second message and the original message would have been identical, with the exact same keys. However, human error, no doubt due to annoyance and fatigue, caused the sending operator to make mistakes and key a slightly different second message. Had the two messages been exactly the same, the British interceptors would merely have received a useless duplicate of the cipher text with the same actual message and the same pseudo-random excess characters designed to mask the message. Luckily for the British and unfortunately for the Germans, this was not the case. The first message began with SPRUCHNUMMER, German for “message number.” The second time the sending operator keyed in the message, he keyed SPRUCHNR, NR meaning the same thing as NUMMER (Sale). But meaning was not the concern, secrecy was. From this point on, the two messages differed, yet the machine inserted identical pseudo-random characters into the message. This caused the cipher texts to be different. Identical obscuring characters in two different messages with the exact meaning made it easier for the British to identify what these excess pseudo-random characters were (Carter).
British interceptors immediately took interest in these messages, due to the use of the same twelve-letter indicator, and hastily sent them to Bletchley Park for Tiltman to examine. Tiltman used his knowledge and experience to guess SPRUCHNUMMER as the start of the message, allowing him to realize the similarity between the two messages. Tiltman was able to decrypt both messages and used his addition techniques to uncover the excess characters created by the German Lorenz machines. The German errors of re-using a starting position and not keying identical messages allowed Tiltman to crack the cipher and understand the role of the Lorenz machine, without ever seeing a Lorenz machine or knowing how it worked!
Tiltman passed on his discovered sequence of excess characters to Bill Tutte, a recent addition to Bletchley Park. Tutte analyzed the streams of bits in each of the five channels and realized certain patterns when he used a repetition of 41. It became clear that the repetitions could not simply be random, thus indicating that the number 41 held some importance. This discovery allowed Tutte to fully understand the workings of the Lorenz machine (Sale).
In 1942, the Post Office Research Labs at Dollis Hill created a machine similar to the Lorenz using the information discovered by Tutte. Frank Morrell created this machine and called it “Tunny.” This allowed the code breakers at the Testery in Bletchley Park to decipher German messages once they discovered the initial settings of a given message. However, discovering the settings took the Testery four to six weeks, making successfully decrypted information old and useless. To solve this, mathematician Max Newman created an electronic machine that used Tutte’s method to automatically uncover the initial settings for German messages (Carter). This machine was constructed at Dollis Hill and named Heath Robinson. The name “Heath Robinson” was chosen in honor of the cartoonist Heath Robinson who designed incredible machines. Heath Robinson worked well, but Newman later collaborated with engineer Tommy Flowers and others such as mathematician Alan Turing to invent Colossus, the ultimate machine that speedily deciphered the Lorenz Cipher (Sale).
Colossus was fully functioning and breaking the Lorenz Cipher in mere hours, just in time for D-Day (Carter). Using Colossus, British and American forces deciphered messages that allowed Eisenhower and Montgomery, commanders of the allied forces, to receive essential tips on German beliefs and actions. These messages revealed that Hitler had been successfully deceived by the phantom army located in south England and the phantom convoys heading east on the Channel. These phantom armies utilized inflatable tanks and media manipulation to deceive Hitler. Hitler believed the attacks would come from the Pas de Calais and he kept the Panzer divisions in Belgium. This information allowed British and American troops to respond more effectively.
After D-Day, French telephone and teleprinter lines were bombed and the Germans had to communicate with radio, further increasing the amount of intercepted messages and increasing the need for Colossus machines. By the end of the war, there were ten Colossus machines at Bletchley Park. Throughout the war, 63 million characters worth of German messages were successfully decrypted (Sale).
When Japan surrendered after the drop of the atomic bombs, the war quickly came to a close. Eight Colossus machines at Bletchley Park were torn apart and two were sent to Eastcote in North London, then to GCHQ, the Government Communications Headquarters of the UK, in Cheltenham. These two were also torn apart in 1960, and any drawings of Colossus were also burnt then to keep the Colossus a wartime secret. In the 1970’s, information about Colossus re-emerged, and a movement to rebuild a Colossus machine was started by Bletchley Park’s curator, Tony Sale. A new Colossus machine was fully reconstructed in Bletchley Park in 1996. 1996 was a significant year: the 50th anniversary of ENIAC, what the world had believed to be the first electronic digital calculator. This myth arose because Colossus was successfully hidden in secrecy for so many years (Sale).
The Lorenz Cipher and Lorenz machines used by the Germans forced the incredible technological advancement of the true first electronic digital calculator, Colossus. These amazing machines and ciphers played crucial roles in World War II activity, notably impacting the outcome of the war. The Lorenz Cipher and implementing machines advanced cryptography on the side of enciphering and Colossus was revolutionary technology for decrypting. These ciphers and machines have forever left their mark on history and cryptography.
This post is part of a series of essays on the history of cryptography produced by students at Vanderbilt University. The students wrote these essays for an assignment in a first-year writing seminar taught by mathematics instructor Derek Bruff. The essays are shared here, in part, to give the students an authentic and specific audience for their writing. For more information on this cryptography seminar, see the course blog.
Sources:
Carter, F. (n.d.). Colossus and the Breaking of the Lorenz Cipher. Bletchley Park. Retrieved November 7, 2012, from www.bletchleypark.org.uk/content/lorenzcipher.pdf.
O’Connor, J. M. (2000). Bletchley Park. History Articles. Retrieved November 7, 2012, from http://www.historyarticles.com/bletchley_park.htm.
Sale, T. (n.d.). The Lorenz Cipher and how Bletchley Park broke it. WW II Codes and Ciphers. Retrieved November 7, 2012, from http://www.codesandciphers.org.uk/lorenz/fish.htm.
Image: “Lorenz machine,” Timitrius, Flickr (CC)
December 2, 2012
Bollywood Bunkum
By Julia Gregson (W&M Contributor)
My next book is partly to do with a group of intrepid young women, both English and Indian, who became midwives and health educators in India after Independence in 1947.
 It’s never easy to track down exactly what starts a book off in your mind, but I do know that in the case of my next book, one of its seeds came from a gem of a book which I bought four years ago whilst researching East of the Sun. I plucked it from a dusty pile on a street stall. It’s called The Women of Maharashtra and is a portrait of some of India’s most exceptional women. A fierce and feisty lot they look, too.
It’s never easy to track down exactly what starts a book off in your mind, but I do know that in the case of my next book, one of its seeds came from a gem of a book which I bought four years ago whilst researching East of the Sun. I plucked it from a dusty pile on a street stall. It’s called The Women of Maharashtra and is a portrait of some of India’s most exceptional women. A fierce and feisty lot they look, too.
Reading it again made me realise what a trap it is to generalise about Indian women, so often characterised as submissive, feminine and downtrodden. While the usual shock-horror stories about suttee, child brides and dowry deaths make good fiction, they are by no means the whole story. This old book of photographs celebrates between its battered covers the Indian women of the 40s, 50s and 60s who became airline pilots, judges, film directors, communist activists and school teachers.
They were well-educated, most eschewed arranged marriages and many had fathers who supported education. Some even went to prison for their beliefs.
Take Durga Bhagwat, for example: one of India’s most acclaimed scholars. Named after the angry goddess, she demanded to go to school, and when her family refused just turned up and demanded to be taught. Eventually her grandfather conceded. “Let the pest go to school”, he said. Once there, she soaked up the learning she’d craved and would even bang her head against the wall to toughen herself up. She needed this toughness in later life: during the 1975 emergency she was a fearless critic of Indira Gandhi’s policies and was imprisoned for several months.
Nalini Ladhake was another formidable Indian woman. Born in a wandering tribe to a traditionally-minded mother and a progressive, she studied, became a teacher and, horrifying her mother, married outside caste and community. She became an activist, social worker and educator.
Beware of the Bollywood Bunkum version of history too, I guess.
December 1, 2012
In Need of a Good Wife: Mail-Order Brides
By Kelly McNees

Uriah Oblinger
In Need of a Good Wife tells the story of a fictional group of mail-order brides traveling west from New York City to Nebraska after the Civil War. These characters agree to marry men with whom they’ve shared only a handful of letters, and one of the best part of drafting this novel was imagining what those letters might look like.
I found a source of information in the correspondence between Nebraska settler Uriah Oblinger and his wife Mattie, who were separated for several years while Uriah settled the land he acquired through the Homestead Act of 1862. The Oblingers’ marriage was not arranged through the newspaper or mail—they met as children in Sunday school—but they faced the same challenges my characters would on the unsettled frontier: drought, sickness, and even grasshopper plagues. Their deep love for one another carried them through the difficult years. Many of their letters opened with sentences like this one, from Mattie to Uriah in 1868:
“Here are those familiar words again[.] I only wish I could utter them in your hearing[.] They would be much more sweeter to me[,] yes[,] I would love to lean over your shoulder and whisper [‘]Dear Uriah[’] in your ears and you would have to be very careful or you would get a kiss[.]”

Mattie Oblinger
Few of the characters of In Need of a Good Wife are lucky enough to feel this kind of affection for the men they are meant to marry, though some find happy endings in unexpected ways. But I like to think that echoes of the Oblingers’ moving love story have found their way into my novel.
Kelly O’Connor McNees (http://www.kellyoconnormcnees.com) is the author of In Need of a Good Wife and The Lost Summer of Louisa May Alcott. She lives with her husband and daughter in Chicago. You’ll find Kelly on Twitter and Facebook.

November 30, 2012
SALIERI and MOZART…who were they really? And how did Peter Shaffer write AMADEUS?
I have read a huge amount about Mozart: his letters, biographies, etc. I own cds of all the music he ever wrote and I wrote a novel called MARRYING MOZART (Viking Penguin) about the young Mozart and the four young musical Weber sisters, one of whom he married (eventually). But the shadow of the movie AMADEUS is a long one, and there is hardly a time when I go to speak about my novel that someone does not ask if Wolfgang Amadé Mozart was really just a funny little man in a white wig. Well, no; he was a very great composer and as a matter of fact he never would act as he did in the film except when breaking into the third bottle of wine with good friends, for which one cannot blame him. In court he was terribly dignified.

my novel about Mozart’s courtship days
The hilarity when it came was a release from a serious childhood. He had been a child prodigy at six. “Remember, you are a genius,” his father told him again and again. And so he went out in the world which mostly did not want genius. And all that scatological humor? It was common in the Austria of his day; it is common even now a friend from Bavaria told me. His mother and father wrote cheerfully to each other that way.
And what about Salieri? Did he have less talent that a plodding first year piano student? Did he really promise his celibacy to God for a great gift of composing? And most importantly, did he kill Mozart? The answer to all these questions is no. Salieri was a very gifted composer; he did not have the original genius of Mozart but then who else did? He was a major figure in the development of late 18th-century opera. As for celibacy, he was married with eight children and had a mistress. And last, he never killed anyone. He lost his mind at the end of his life and imagined he had killed Mozart, but indeed they were on friendly terms. Salieri tutored Mozart’s son and cheered on Mozart’s music.

Mozart – was he just silly?
Nevertheless, AMADEUS is a wonderful movie! And it did include Salieri’s consecration of his music to God, a piece of moving and true history.
In the film and play we have the skill of a historical novelist or, in this case, a historical playwright. But why on earth did Peter Shaffer portray Mozart like that? When asked, he explained he portrayed Mozart as remembered through the eyes of a crazed old man who was dying likely from syphilis which was tragically common then.
Yes, Shaffer made a villain of poor Salieri and a fool of Mozart, but he did more good than harm. Millions of people first discovered Mozart’s music through the movie, and the almost forgotten Salieri has had many of his operas brought back to the stage. The movie did with Mozart what no novel can do. It showed him as a cocky little fellow swaggering through Vienna with a wine bottle in his hand and his music roaring in his head. By using the bold strokes of contrast between the two men (such contrast as never was) it made a moving plot line and a great story.

Salieri – was he a man of no talent?
Almost ten years ago I used my lifelong love and study of Mozart (and my years singing his music as a high soprano) to write my novel MARRYING MOZART, not of tragedy and death but of his stumbling courtship years when he found his wife. For those of you in the New York City area, the novel with have its premiere as a singspiel (an opera with a great deal of dialogue), for four performances only mid-December 2012. The novel adaption is by Michael Capasso and music is by Mozart! What better? Tickets may be reserved here. http://dicapo.com/season/03mozart.html.
________________________
About the author: Historical novelist Stephanie Cowell is the author of Nicholas Cooke, The Physician of London, The Players: a novel of the young Shakespeare, Marrying Mozart and Claude & Camille: a novel of Monet. She is the recipient of the American Book Award. Her work has been translated into nine languages. Her website is http://www.stephaniecowell.com
November 29, 2012
What’s In A Book? A Brief History of Book Ciphers
 by Malak Elmousallamy (Vanderbilt University)
by Malak Elmousallamy (Vanderbilt University)
“You can do a lot with a book, besides read it!”- Albert C. Leighton and Stephen M. Matyas
Ever wondered what those numbers in the letter Sherlock Holmes received in The Valley of Fear had to do with the murder of John Douglas? Or how a Bible Michael stole in season two of Burn Notice dominated the entire season’s plot? Or why the coordinates on the back of the Declaration of Independence in the movie National Treasure led to the discovery of the most elusive treasure in history?
The answer is that they were all clues to revealing the content of hidden messages that employed the technique known as book ciphers. Book ciphers are a means of enciphering written communication using a piece of text from a book as the key. As it turns out, this method of concealing information holds true beyond the entertaining world of fiction and has been a recurring phenomenon throughout history. (Leighton and Matyas, 1985)
Throughout the history of cryptography, there has been an unrelenting battle between code makers and code breakers- each desperate to gain the upper hand. Cryptographers worked continuously to create new ways of enciphering messages, and cryptanalysts were equally persistent to reveal their content. It comes as no surprise then, that in 1526, almost seventy years after the first efficient method of commercial printing was discovered, (British Library, n.d.) cryptographers were already thinking about how to use a book in order to obscure a message. Jacobus Silvestri, one of the ancestors of cryptography, was the first to describe a true book cipher. He recommended the use of a codebook as a means of concealing information and devised a sort of dictionary with root words placed in multiple columns. Every row and column is assigned a unique symbol and additional symbols were allocated to commas, question marks and other grammatical inflections. The Voynich manuscript, whose origin and content remain a mystery, is believed by some to have been enciphered using this technique. (Leighton and Matyas, 1985)
By 1586, Blaise de Vigenere had already thought of several ways to use a book for cryptographic purposes. His first suggestion was to place a transparent sheet over the pages of a book and underline the words one wished to include in the message. The recipient of the message, or in this case the transparent sheet, would then place the sheet onto their own copy of the book and match the lines to the words on the page in order to reproduce the message. This was a rather primitive and impractical method of concealing messages since finding the desired words in the order they are found in the message, on a page or so of text is unlikely. His next suggestion, and what is arguably the most widespread version of a book cipher, is to match letters in a text using a triple coordinate system. This basically means that the first number of the coordinate referred to a page number in the book. The second number referred to a line, and the third number referred to the location of the letter in that line. For example, if you were trying to encipher the letter ‘C’ using Singh’s The Code Book, then you would go to the first page, second line and fourth letter of that line, encrypted as (1,2,4). That way, any combination of letters or words could be manufactured using a relatively small text. The advantage of this method is that one needs only to memorize a short piece of text, perhaps a popular poem, without running the risk of having to carry a codebook around and risking it falling into the wrong hands. However, this process of encoding individual letters can be tedious and time-consuming, and there is much room for error. It is also not unbreakable because the text used as the key can potentially be located, and the process of encryption can simply be reversed. (Leighton and Matyas, 1985)
In the eighteenth century, Christian Breithaupt modified this method of enciphering messages by suggesting the use of the numbers for the page and line in which the desired letter occurs first. This means that the key is restricted to the first few pages of a book as opposed to the book as a whole. He also echoed the sentiment that this method does not provide as much security as cryptographers would like since a clever investigator might find out what key book was used. Later in the century, Philip Thicknesse writes of a similar method in which a numeric code is used to refer to words in a book by page, line and word number. (Leighton and Matyas, 1985)
With the urgency presented by the American Revolution looming in the air, several adjusted and improved versions of book ciphers were produced. Numbering schemes were adopted which allowed for the enciphering of individual letters. This made the process somewhat more practical and precise. An example of which is in the letters that Benjamin Franklin received from his translator, Barbeu-Dubourg, in Paris on June 10,1776. Barbeu-Dubourg explains that security can be achieved by numbering each letter in the key text, as opposed to numbering the entire word or just the letters in a single word. For example, if a line began with “Mary Queen of Scots,” then the letter M would be numbered 1. The letter A would be numbered 2, and the letter Q would be numbered 5, as opposed to going back to 1 again. Implementing this numbering technique avoids the confusion as to which word is being used as the key. (Leighton and Matyas, 1985)
Finally, in modern-day history, we encounter book ciphers in the form of the elusive Beale Ciphers. These ciphers are thought to have been left by a man named Thomas Jefferson Beale in which he detailed the exact location, content and owners of a substantial treasure. The second of these ciphers was successfully decrypted some years later and included a description of the treasure. This cipher was constructed using a version of the Declaration of Independence as the key, where every word was numbered in order. To decrypt the text, the numbers in the cipher text were matched to the numbered words in the Declaration of Independence. By taking the first letter of the selected words, the hidden message could be reconstructed. The other two ciphers, which are thought to detail the location and owners of the treasure, have yet to be cracked. (Singh, 2000)
Book ciphers continued to develop over time and eventually led to the creation of what is considered the only unbreakable cipher. The running key cipher, which is the only method of concealment that has withstood cryptanalysts’ efforts, is constructed by using the book as the key text. In this case, the individual letters in the text are used as the key and avoid repetition. For example, if you were to use Singh’s The Code Book as your key, then you would begin to encrypt the plain text “meet at dawn” using the first line, “On the morning of…”. The first letter of the key is ‘O’ and so we would go to the row that starts with ‘O’ in the square drawn below and encrypt ‘M’ as ‘A’, and so on. The security of the running key cipher lies in its continuity- that is that the key does not repeat itself. The key is simply comprised of the words of the novel, which do not have a recurring patter. In this way, the running key cipher can withstand all the conventional methods of cryptanalysis.
So, the next time you are about to dismiss some seemingly unrealistic code or cipher you see in a movie or read in a book, think about how it might actually be based on reality, and how the real world is really much cooler than we think it is.
This post is part of a series of essays on the history of cryptography produced by students at Vanderbilt University. The students wrote these essays for an assignment in a first-year writing seminar taught by mathematics instructor Derek Bruff. The essays are shared here, in part, to give the students an authentic and specific audience for their writing. For more information on this cryptography seminar, see the course blog.
References
Leighton and Matyas, A.C.L. and S.M.M. (1985). The history of book ciphers. Proceedings of CRYPTO 84 on Advances in Cryptology.
British Library. (n.d.). Gutenberg Bible: The Basics. Retrieved from http://www.bl.uk/treasures/gutenberg/basics.html
Singh, S.S. (2000). The Code Book: The science of secrecy from ancient Egypt to quantum cryptography. New York, NY: Anchor Books.
November 23, 2012
Gadgets and Gimmicks of the Civil War

Civil War playing cards, circa 1862.
During the first few weeks of April 1861, even before the smoke of Fort Sumter had faded, the greatest assemblage of hucksters in the nation’s young history began hawking an eclectic variety of wares. The mid-19th century, with its rapid proliferation of daily newspapers and the penny press, marked the first time people recognized the opportunity to commercialize a war effort, to infuse patriotism with the spirit of consumerism, and advertisements were typically more imaginative than true. While many inventors and pitchmen genuinely hoped to improve soldiers’ comfort and convenience, others took advantage of an unsophisticated public caught up in jingoistic fervor. Below, a sampling of goods and gadgets available to both soldiers on the front lines and those cheering them on:
• A number of products promised to ease the hardship and privations of camp life. If a solider could handle the extra 15 pounds he might carry Milligan’s Patent Mess Kettle, complete with its 18 cooking utensils. There was also Strong’s Patent Army Trunk and Portable Bedstead, one of many brands of a combination folding cot, lounge, and camp chair that could be neatly collapsed into a two-foot bundle. John Wheeley Lea and William Henry Perrins, the men behind Lea & Perrins Worcestershire Sauce, hoped to make their product a staple at camps by vowing it would “add greatly to the health of the soldier!” The makers of Dr. Holloway’s Ointment promoted their product’s ability to heal everything from smallpox to saber cuts to gunshot wounds. Soldiers seeking a temporary escape partook of “hasheesh candy,” 25 cents per piece or $1 per box, which purported to be “a most wonderful Medicinal Agent for the cure of Nervousness, Weakness, Melancholy, Confusion of thoughts, etc. Under its influence all classes seem to gather new inspiration and energy.”
• During the long stretches of downtime, soldiers entertained themselves by listening to “Army Musical Boxes,” advertised as a “Cheerful Companion for the Soldier.” Union playing cards featured flags, stars, shields, and eagles for suits, and a colonel, a goddess of liberty, and a major for king, queen, and jack. Writing desks were available everywhere (Union soldiers had a choice of “McClellan” or “Stanton” writing desks, named after the general and the secretary of war, respectively), each consisting of a piece of hardboard and a packet of supplies. One popular choice was the Union Prize Stationary package, which came with a dozen envelopes, paper, a pen holder, two steel pens, one pencil, a sheet of blotting paper, 75 recipes for camp cooking, and a picture of General George McClellan. Soldiers could also buy counterfeit Confederate money for use in the South, paying just $5 for $20,000.
• Fencing instructors became ubiquitous, offering lessons on fighting with swords and bayonets. One weapons manufacturer introduced a handy saber with a pistol built into the hilt. In 1862 Richard Gatling, the son of a North Carolina planter, invented the “Gatling gun,” a forerunner of the modern machine gun. It was a repeating gun with six barrels arranged in a circle, and was fired by turning a crank that made the barrels rotate. As a barrel reached a certain spot on the gun, a cartridge was automatically loaded and discharged. By rapidly turning the crank, the operator could fire many rounds in a short period of time. (The Union Army bought Gatling’s gun, added an additional four barrels, and used it on a limited basis during the Civil War.) Naval officers bought P. Getz’s Patented Waterproof and Life Preserving Trunk, which could support 250 pounds—a convenient device to have handy during any maritime mishap. For the more reluctant soldier, the Police Gazette offered pamphlets entitled “How to Get a Discharge” and “How to Get a Furlough,” both for the bargain price of ten cents.
• Anyone curious about what George McClellan, Stonewall Jackson, Robert E. Lee, and Irvin McDowell looked like could purchase cartes de visite, small, pocket-sized photos usually sold in packets of eight for $1. Pictures of the “Heroes of Gettysburg” were on sale in New York by July 9, 1863, not even a week after the battle.
• When it was finally over, women doused themselves with “Union Bouquet Pefume,” just 25 cents per bottle, and watched the boys come marching home.
Karen Abbott is the New York Times bestselling author of Sin in the Second City and American Rose. Her next book, a true story of four female Civil War spies, will be published by HarperCollins in 2014.
Sources: “The Civil War Was a Pitchman’s Paradise,” by Frederic S. Klein. Civil War Times Illustrated, June 1963; David B. Sachsman, S. Kittrell Rushing, Debra Reddin Van Tuyll, The Civil War and the Press. New Brunswick, NJ: Transaction Publishers, 2000; Michael Varhola, Life in Civil War America. Cincinnati, Ohio: Family Tree Books, 2011.
November 22, 2012
How wind power won the American West
By Carol Clark (Atlanta Science Tavern Contributor)
There is something both comforting and mournful about the creak of an old windmill coming to life in a breeze. The metal skeletons and pinwheel faces of windmills tower over the loneliest of places, totems to the people who staked a claim on vast, empty plains, where they stayed attuned to the slightest shifts of weather.

Texas Windmill (Carol Clark)
Growing up in northeast Texas, I’d occasionally catch glimpses of these whirling relics silhouetted in the distance, as our car rushed through the scraps of rural landscape separating suburbs and cities. But I didn’t fully appreciate windmills until I went to the annual meeting of the Society of Environmental Journalists last October, held in the West Texas town of Lubbock.
Lubbock is set in the Southern High Plains, where the economy is fueled by oil, gas, agriculture and wind. This year’s SEJ conference was themed: “Whiskey is for drinking, water is for fighting over.” Several hundred writers, scientists and policy makers descended on the town. We broke into groups for field trips, moving like flocks of flightless birds across the plains, baked by the relentless sun and scoured by the gritty wind. We learned about the hard-scrabbled history, recent record drought, and possible future scenarios of this remote, yet influential, region.
One of the highlights for me was the story of the humble windmill’s key role in settling parts of America where surface water is scant, including the Southern High Plains.
In 1854, American Daniel Hallady invented a self-governing windmill, which automatically turned to face whichever way the wind blew. Weights allowed the wooden blades to swivel in a way that also controlled the speed of operation, to reduce wear and tear on parts and the chance of breakage in strong winds. It was simple, streamlined and affordable for pioneer families who wanted to tap underground sources of water. Larger windmills sprouted up every 20 miles or so along railroad lines, where they were needed to pump water for steam engines.
A visit to Lubbock’s American Wind Power Center drove home the importance of the windmill to opening up the West. The center’s collection of vintage wind machines gives you an idea of the high regard, and even affection, people must have felt for them. Their makers branded them with romantic names like “Iron Man,” “Eclipse,” and “Star.” Windmill weights entered into the realm of folk art, taking on whimsical shapes of squirrels, horses and roosters.
Wandering beneath the gently whirring blades, I imagined how soothing the sound must have been to people who relied on windmills for their water.
The windmill helped power a sustainable way of life for decades across the Southern High Plains. Things tilted out of balance during the Great Plow Up. The U.S. government artificially raised the price of wheat and encouraged farmers across the Plains states to rip out deep-rooted native grasses and ramp up crop production to feed the troops in World War I. The result was the environmental catastrophe known as the Dust Bowl. During the 1930s, the wind churned up all that loose dirt and spun it into dark, boiling clouds that suffocated toddlers, obliterated the sun and swept away livelihoods.
The dust had scarcely settled when the main lesson of that disaster was largely forgotten: Excess comes at a heavy price.
By the 1950s, advances in electrical pumping technology had made the windmill nearly obsolete. Farmers and ranchers from Nebraska to West Texas could now exploit their underground water supply, known as the Ogallala Aquifer, to an extent never before possible.
It took 12 million years for rain to seep down and fill the Ogallala Aquifer, one of the world’s largest underground water systems. During the past 50 years, we’ve emptied half of it, mainly through intensive irrigation.
So what does the future hold, for West Texas and the rest of us, as the climate warms, the population booms, and the demand for fuel, food, water and other consumer goods keeps growing?
It depends on how you spin the story.
Oil and agriculture boosters downplay the looming questions surrounding our heavy reliance on fossil fuels and industrial-scale irrigation. And West Texans can now boast about renewable energy, since the region produces more wind power than any other state. The old-fashioned windmills have morphed into sleek, high-tech wind turbines. So what if they lack charm: Utility-scale wind turbines, some with blades as long as 120 feet, can generate massive amounts of electrical power.
The “whump-a-whump” of a giant wind turbine in full bore has been compared to heavy sneakers tumbling in a dryer. That’s the sound of progress. And how comforting, to be reminded that we can harness the wind and generate electricity to rapidly dry our latest pairs of designer sneakers.
Carol Clark is Senior Science Communicator at Emory University, where she edits the Web site eScienceCommons.