Robert E. Davis's Blog, page 9
December 26, 2010
Information security management: measuring performance - part 2
Do you like this story?Maturity modeling utilizing benchmarking techniquesIT security maturity modeling can measure the established control environment and controls within processes. Typically, the defined maturity modeling scale addresses entity-centric processes from...
Published on December 26, 2010 16:47
December 18, 2010
Information security management: measuring performance - part 1
Do you like this story?Though IT security service management can include a plethora of indicators, adequate service value measurement is not demonstrated in the sheer number of indicators considered. Practical IT security service delivery and support utilization...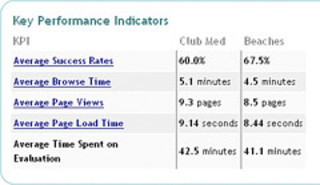

Published on December 18, 2010 09:26
December 12, 2010
Information security management: legal compliance alignment - part 2
There are numerous global, regional as well as national laws and regulations focusing on information assets protection (IAP) requiring professional consideration. In particular, at the global level, the World Intellectual Property...[image error]
Published on December 12, 2010 08:51
December 4, 2010
Information security management: legal compliance alignment - part 1
Institutionalized information security governance defines the information assets safeguarding perimeter inside which an entity should operate. Whereas, legal compliance management ensures structural boundary segments are sturdy and the entity...[image error]
Published on December 04, 2010 20:00
November 29, 2010
Information security management: electronic commerce - part 2
EDI is commonly defined as the transfer of data between different companies utilizing networks. Inadvertent data loss during transmission reduces the cost savings generally associated with EDI deployment. Furthermore, message integrity issues can...
Published on November 29, 2010 03:07
November 22, 2010
Information security management: electronic commerce - part 1
With an ever-increasing number of organizations and individuals relying on the Internet to exchange confidential and sensitive information, adequate message security continues to be a technological management concern. Serviceable standard...
Published on November 22, 2010 04:23
November 15, 2010
Service Level Management of Cloud Computing
Service Level Management (SLM) defines, negotiates, controls, reports and monitors agreed-upon service levels within predefined standard service parameters.
Published on November 15, 2010 11:32
Information security management: critical incident response elements – part 2
There exist various theories concerning managing employees during a crisis scenario. Nevertheless, security incident response tactics should be viewed as a unique application of contingency management theory that can be coupled with sound risk...
Published on November 15, 2010 04:55
November 12, 2010
Online Data Communication Access Controls
Access controls over communication devices may not be effective in an online infrastructure unless certain communication techniques are deployed.
Published on November 12, 2010 19:44
November 8, 2010
Information security management: critical incident response elements – part 1
Information technology is completely secure when resources are utilized and accessed as intended under all circumstances. Through delegation, every entity manager assumes responsibility for maintaining an adequate control system that safeguards...
Published on November 08, 2010 02:38



