Robert E. Davis's Blog, page 7
April 13, 2011
IT audit fieldwork: Generally accepted processes - part 2
Robert E. DavisCollection of sufficient evidential matter required for compliance with the third generally accepted standard of audit fieldwork affects the IT auditor as to the type of evidence to be collected and as to the means of acquisition. For...April 13, 2011

Published on April 13, 2011 08:00
April 6, 2011
IT audit fieldwork: Generally accepted processes - part 1
Robert E. DavisIT auditing is similar to, and yet different from, auditing manual systems. The fieldwork processes are similar in that compliance and substantive tests are still performed within the context of generally accepted auditing standards, whereas the...April 06, 2011
[image error]
[image error]
Published on April 06, 2011 10:01
March 30, 2011
IT audit verification planning: Resolving technique selection - part 2
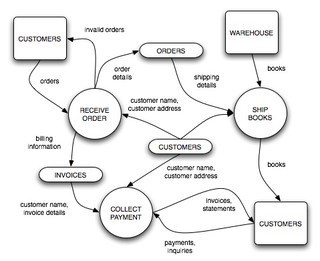
Robert E. DavisAuditing IT configurations involves performing compliance and substantive tests on a selected information asset as an integrated unit. Integration can refer to various activities including: combining the separate testing of programs and files into...March 30, 2011

Published on March 30, 2011 07:55
March 23, 2011
IT audit verification planning: Resolving technique selection - part 1
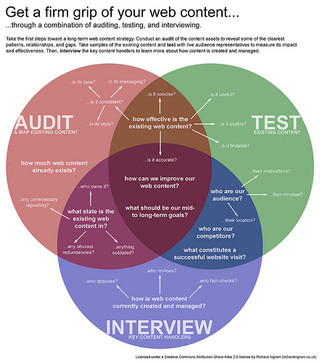
Robert E. DavisThere are a variety of techniques available to the IT auditor for compliance and substantive testing when performing assurance engagements. Selecting a technique appropriate for the assurance task at hand, however, can be difficult.Analytically,...March 23, 2011

Published on March 23, 2011 08:39
March 16, 2011
Information security management: Application protection - part 2
Robert E. DavisTo dispatch FCPA information reliability requirements, an information security manager should identify, understand, test, and document internal accounting security controls for information assets. Essentially, an information security manager...March 16, 2011
[image error]
[image error]
Published on March 16, 2011 07:14
March 9, 2011
Information security management: Application protection - part 1
Robert E. DavisLegacy law or regulation replacement is a common occurrence within most governments when circumstances appear to discredit legal mandate enforcement. However, the U.S. Sarbanes-Oxley Act (SOX) of 2002 does not supersede the U.S. Foreign Corrupt...March 09, 2011


Published on March 09, 2011 12:07
March 3, 2011
Assistive technology for the disabled: Computer access - part 3
Robert E. DavisSoftware applications enabling output data decodingAccessing a computer is generally pursued to acquire knowledge or convey information. Yet, if results of an inquiry or responses from the audience cannot be translated into understandable messages...March 03, 2011


Published on March 03, 2011 21:04
February 25, 2011
Assistive technology for the disabled: Computer access – part 2
Robert E. DavisFor those with a high-level of paralysis, such as amputated arms or an immobilizing progressive illness (e.g. MD, ALS, or MS), another available option that can be used separately or jointly with EMG technology is the Integra Mouse. This device is...February 25, 2011

Published on February 25, 2011 19:54
February 20, 2011
Assistive technology for the disabled: Computer access – part 1
Robert E. DavisThere are two prevailing definitions associated with assistive technology. For the generalist, assistive technology is any equipment that enhances the ability of students and employees to be more efficient and effective. While for the specialist,...February 20, 2011
[image error]
[image error]
Published on February 20, 2011 10:50
February 11, 2011
Information security management: trans-border communication protection – part 2
Generally, a VPN is recognized as a confidential data plexus that employs the public telecommunication infrastructure while maintaining privacy through the utilization of a tunneling protocol and security procedures. A VPN can provide remote...

Published on February 11, 2011 07:52



