Robert E. Davis's Blog, page 3
January 25, 2012
Effective employment practices for protecting IT - part 2
Usually, it is easier to purchase an automated solution addressing IT control practices than to change an entity’s culture. Nevertheless; even the most secure system will not achieve a significant degree of protection if utilized by &...


Published on January 25, 2012 05:39
January 18, 2012
Effective employment practices for protecting IT - part 1
Based on extensive research by various knowledge leaders, the greatest harm or disruption to IT-based information services emanates from intentional or unintentional actions of internally employed individuals. Frequently, information systems...


Published on January 18, 2012 06:12
January 11, 2012
Right-sizing IT controls - part 3
The risk management process introduces a systematic approach for identifying, assessing, and reducing risks as well as maintaining defined acceptable risk levels. Stepwise, an IT risk assessment should be considered a key risk management practice...
[image error]
[image error]
Published on January 11, 2012 08:30
January 4, 2012
Right-sizing IT controls - part 2
At the IT departmental level, precise organizational unit responsibilities should be documented. Correspondingly, utilizing a bottom-up approach can assist in clearly defining roles and responsibilities for each IT unit as well as the IT...
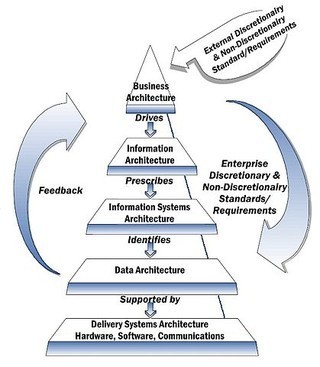

Published on January 04, 2012 06:23
December 17, 2011
Year in review: Assistive Technology - 2011
During 2011, I found myself posting various technology themes, what follows are five of my personal favorites. Why developing an IT Balanced Scorecard is important to the City of Philadelphia (January 7, 2011) - According to an International City...

Published on December 17, 2011 09:42
December 14, 2011
Right-sizing IT controls – part 1
IT has enhanced control processes. It has enabled opportunities for utilizing close-loop control systems and provided the means for more timely corrective actions. Unfortunately, IT has also introduced the potential for a detrimental proliferation...

Published on December 14, 2011 06:36
December 6, 2011
Managing the dynamic uncertainties of IT - part 3
An adequate IT plan describes predetermined objectives, goals as well as ambit with sufficient supporting detail to guide risk assessment development. Correspondingly, IT risk assessment plans should reflect applicable IT standards and practice...
[image error]
[image error]
Published on December 06, 2011 22:06
November 30, 2011
Managing the dynamic uncertainties of IT - part 2
Selecting a discretionary IT risk management framework imposes defining spending limits, work assignments and information decisions for creating and managing a viable strategically aligned IT management plan. IT risk management frameworks...

Published on November 30, 2011 07:05
November 23, 2011
Managing the dynamic uncertainties of IT - part 1
Most entities operate in an environment that is influenced by perceived stakeholder values; the entity’s mission, vision and values; community and organizational ethics and culture; applicable laws, regulations and policies; as well as...
[image error]
[image error]
Published on November 23, 2011 06:13
November 16, 2011
Managing the growth and impact of virtual machines and memory - part 3
Though a process virtual machine can be considered an application-orientated system virtual machine; process virtual machine uniqueness resides in the provisioning of “a platform-independent programming environment that abstracts away...
[image error]
[image error]
Published on November 16, 2011 06:42



