Robert E. Davis's Blog, page 4
November 9, 2011
Managing the growth and impact of virtual machines and memory - part 2
Demand paging is a technique wherein computer memory is divided into fixed-length blocks. These fixed-length blocks, commonly referred to as pages, can be effectively exchanged or swapped back and forth between primary and secondary storage...
[image error]
[image error]
Published on November 09, 2011 05:42
November 2, 2011
Managing the growth and impact of virtual machines and memory - part 1
IT virtualization represents the creation of a seemly boundless version of an IT resource to the end-user. Historically, once a suitable means of multiprogramming was discovered for processing datum, efforts to expand the utilization of IT were...
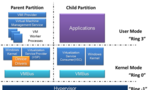

Published on November 02, 2011 08:09
October 26, 2011
Governing IT: Setting control objectives - part 3
Reflective of ensuring effective IT control objectives, undertaking IT risk management provides the framework that enables future activity to take place in a consistent and controlled manner. As a particular, prioritization enables appropriate...
[image error]
[image error]
Published on October 26, 2011 08:28
October 19, 2011
Governing IT: Setting control objectives - part 2
COBIT enables an entity to set clear control objectives for IT through the combining of previously discussed individual IT design and operational areas. Specifically, the eight IT managerial areas are grouped into four domains: Plan and Organize...
[image error]
[image error]
Published on October 19, 2011 08:42
October 12, 2011
Governing IT: Setting control objectives - part 1
Reducing IT related errors, mistakes, omissions, irregularities, and illegal acts should be an explicit policy of every passive or active entity. Institutionalizing such a policy requires documenting and conveying “statements of objectives...
[image error]
[image error]
Published on October 12, 2011 08:50
October 5, 2011
Information security management: Developing objectives
There exist various theories regarding managing employees. Behavioral management theorists believe leadership traits are not genetic. Thus, leaders assume distinct behaviors that can be studied and applied according to individual perceptions of...

Published on October 05, 2011 09:18
September 28, 2011
Compliance through automation: Continuous Monitoring - part 3
To ensure effective continuous monitoring, adequate segregation-of-functions must be sustained. Continuous monitoring and segregation-of-functions are not new control concepts. Yet, technological integration issues can be a barrier to implementing...
[image error]
[image error]
Published on September 28, 2011 08:13
September 21, 2011
Compliance through automation: Continuous Monitoring - part 2
To enable effective deployment, the three levels of continuous monitoring must operate harmoniously. The data provisioning level supplies raw datum for analysis after completing the collection process. This collected data can be extracted from...

Published on September 21, 2011 06:04
September 14, 2011
Compliance through automation: Continuous Monitoring - part 1
Commonly, a Management Information System (MIS) is deployed to permit performance monitoring to assess compliance with adopted standards and enable corrective actions and/or process improvements to an entity’s control systems. Generally...
[image error]
[image error]
Published on September 14, 2011 07:51
September 7, 2011
Compliance through automation: Expert Systems - part 3
To assist in assessing decisional acumen, most managers are under observation for situational responses impacting the entity. Therefore, information reliability is critical. During the final stage of preparation for deployment, an expert system...

Published on September 07, 2011 10:44



