Daniel Miessler's Blog, page 99
June 4, 2018
The Most Exciting Features from the WWDC 2018 Keynote
You should read this article in its intended typography at: The Most Exciting Features from the WWDC 2018 Keynote
—

This year’s WWDC Keynote was all about software, and it had updates for iOS, macOS, watchOS, and tvOS. Here were my favorites.
iOS
Share back in photos
Siri shortcut integrations
Shortcut editor
Travel plans
Heading home
Screentime
Time limits
Allowances
Memoji
Personalized animoji
Group FaceTime with up to 32 people
Pivot directly from Messages to group FaceTime
Automatic workout detection, which is retroactive, and also works for stopping workouts
Lift to talk, no hey Siri
Walkie talkie
Siri shortcuts on Siri watchface
tvOS
Dolby Atmos
Zero auth
macOS
Mojave
Dark mode
Xcode in dark mode
Desktop slowly changes during the day
Desktop stacks
Gallery view
Video screen grabs
Continuity camera
News to the Mac
Voice memos to the Mac
Voice memos in cloud
Shutting down share and comments to avoid tracking
Avoiding fingerprinting by looking like everyone else
New mac app
0365 on the way
CreateML with custom data you can mess with in code playgrounds
UI kit iOS apps on Mac
—
I spend between 5 and 20 hours on this content every week, and if you're someone who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
June 3, 2018
How to Have Amazon Polly’s AI Voice Read Your Newsletter as a Podcast
You should read this article in its intended typography at: How to Have Amazon Polly’s AI Voice Read Your Newsletter as a Podcast
—

I’ve just published my first podcast episode (Episode 128) using Amazon Polly—Amazon’s AI-based text-to-speech engine.
Listen to the episode here.
It’s quite good—much better than the few others that I’ve tried.
What I quite like about it for my podcast is that I can use SSML syntax to insert pauses at appropriate points. For example, I like a one second pause between items, and then two seconds buffering section titles.
Here are the basic steps.

Complete your text.
Log into Amazon Polly’s console.
Paste piece of text into the window. Start with a small piece, for numerous reasons.
Wrap the text with a speak tag, like you see in the example above.
Insert any additional syntax, such as delays, optional different voices, speed differences, etc.
Close out with another speak tag (except the close version).
Download the voice as MP3.
You can now upload that clip as audio for your podcast or other type of production.
Enjoy!
Notes
You will have to keep each clip below 3000 characters, which is slightly annoying if you have lots of content in your shows. It just means you’ll have to break it into multiple clips, which was pretty easy to re-assemble using Adobe Audition.
—
I spend between 5 and 20 hours on this content every week, and if you're someone who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
Unsupervised Learning: No. 128
You should read this article in its intended typography at: Unsupervised Learning: No. 128
—
This week’s episode of Unsupervised Learning is now available. Subscribe below and get this episode’s podcast and newsletter.



This week’s topics: Pentagon background checks, China using machine learning in schools, Rusian ethnicity detecting AI, US Military presence in Africa, Atlanta lost dashcam footage, Kidnapping insurance, Technology News, Ideas, Recommendation, Aphorism, and more…
Become a Member to Get This Week’s Newsletter
—
I spend between 5 and 20 hours on this content every week, and if you're someone who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
Automated Situational Interpretation and Prediction (ASIP)
You should read this article in its intended typography at: Automated Situational Interpretation and Prediction (ASIP)
—

Any time you see us using cameras to feed a Machine Learning algorithm, I think we’ll start calling that Machine Learning Vision, and, eventually, Computer Vision.
The key point is that computers can parse video (and other sensor data) and figure out things that even humans cannot. The combination of audio, video, heat, other types of EM waves, etc., will all be used to determine human emotions, human activity, and—ultimately—human intentions.
Perhaps the final term for this will be something like Automated Situational Interpretation and Prediction (ASIP).
—
I spend between 5 and 20 hours on this content every week, and if you're someone who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
May 26, 2018
I’m Not (Overly) Concerned About Smart Speaker Security, And You Shouldn’t Be Either
You should read this article in its intended typography at: I’m Not (Overly) Concerned About Smart Speaker Security, And You Shouldn’t Be Either
—

I have a 1,001 friends in InfoSec who I hear things like this from on a regular basis:
I’d never put one of those things in MY house! I’m in security! They’re going to find flaws in those things, you wait and see!
Then when something happens, like a private conversation being sent to a random person, they inevitably bring their I Told You So game.
I also read enough to know it could be me that’s wrong about this.
I find the whole thing mostly silly. I think it’s an example of security people being emotional rather than doing actual threat and risk analysis. Dan Kaminsky had this comment on Twitter that captures it humorously.
I understand the Alexa bug well enough to put together a detailed guide to replicating it.
— Dan Kaminsky (@dakami) May 26, 2018
One of my friends just commented, dude, it's a butt dial. Alexa reimplemented the butt dial. Sucks, but nobody suggested throwing out phones, because of butts.
He's got a point.
These are consumer scenarios; it’s a whole separate game if you’re putting these things at work and integrating them with backend systems.
So let’s ask the question: what are we actually imagining as threat scenarios here? I’ve gone through them myself and they’ve panned out as absolute garbage. Let’s look at a few of them.
Amazon is Actually Storing Everything, From Every Echo: Cool, so they’re the evil empire, and also thousands of times more effective than the NSA. They have a team of 1 million people trained to extract juicy things and use them to blackmail you or sell you products. And they send a copy to the government so if you ever do anything bad they can arrest you.
My analysis?
Not worth the risk to them.
Too hard to keep secret.
Too hard to actually execute.
Next scenario…
Someone Finds a Flaw in Echo And Can Listen In to Your Conversations: So there’s some really bad bug where someone can send you an email or text message while you’re at home, and it sends a command to your Echo and turns on recording, and then also sends that recording to the attacker.
My analysis? Sure, that’s bad, but think of how many things have to fail for that to work. First, Amazon is going to guard against this like it’s Ebola in AWS because their entire SmartHome play is based on trust. And for a company that’s literally running the entire internet via AWS, I think they’ll be pretty good at that. Second, the targeted attack has to work. The attacker has to somehow pick you, find a way to reach you, send you the attack, and it has to go through your various defenses. That will definitely work against people, but the odds of it happening to you are really low.
Next one…
There’s a Massive Internet-based Bug That Allows Attackers to Listen to Any Smart Speaker Device: Let’s say there’s a vulnerability so bad that all the attacker needs is the user’s Amazon-associated email address, and they can then listen to all Echo’s associated with that account.
My analysis: First, this is 1) not impossible, and 2) really, really bad. But you know how long that vulnerability would exist and be exploited before someone either alerted Amazon or leaked it to someone? Not long. So, could the worst possible thing happen quietly for a period of time, during which you get targeted, and during which time you say something holistically stupid or sensitive that an attacker takes advantage?
Yes, absolutely possible. But unlikely. That window is small, and unless you’re really important, and really prone to saying dumb and/or sensitive things at home, this isn’t likely to happen. And that’s assuming the vulnerability exists that makes it possible.
The internet of poo
To be clear, I don’t think we’re even close to seeing how ridiculous the Internet of Trash (IoT) will be. We’re going to see massive mistakes. Massive misconfigurations. Leaked data. Leaked recordings. All of it. It’s going to happen. Hell, it’s already happened. And it’ll get way worse before things improve. But being hacked by your smart speaker is just not a likely scenario.
Being personally targeted by some sophisticated attacker, who uses a 0-day smart speaker vulnerability to record you and cause you harm—is an emotional fear and little else.
Who is this attacker anyway?
A cybercriminal? A government red-teamer? A random security researcher with a grudge against you?
You need to ask why these people would spend time attacking you, because they damn sure will be asking the same thing. These attacks are expesnive in numerous ways. They take time and effort, and they burn precious exploits. And here’s nothing an attacker hates more than wasting time, effort, and good vulnerabilities on a target that isn’t likely to return anything.
So ask yourself: are you that important? I’m not. And I think I can get a whole lot more important and still not be important enough. Nobody cares, and especially nobody with the skills to use 0-day smart speaker vulnerabilities to hurt you.
Besides, there are far easier ways to hack someone. If I wanted to hack me—or anyone like me—it’d be easy. Not because I don’t have solid defenses—I do—but if you’re targetted by someone skilled, it’s remarkably easy to get in and mess your life up.
If you or me—or almost anyone in infosec—is targeted by someone with even modest offensive security skills, you’re going to lose. And not by a little bit.
You don’t avoid being hacked by professionals by having strong passwords, antivirus, and not owning a smart speaker. You avoid being hacked by being part of the 99.999999% of the planet that attackers don’t care about.
That’s why you shouldn’t worry about people hacking Smart Speakers.
You’re probably not interesting enough to target, and being uninteresting is actually your best defense.
If a vulnerability applies to a large number of people, your data will be lost in the noise (see not targeted).
Any vulnerability that allows a casual attacker to target an individual will be fixed very quickly, and the odds of you having a major negative impact during that tiny window are low.
If you are both targeted—and it’s by a skilled attacker—you’re going to get hacked through your email and laptop/phone anyway—not through your smart speaker.
So now, take that remaining risk—which absolutely is not zero—and compare it to the advantages offered by products like Echo.
To me, and many other infosec people, that risk is simply worth it because it’s offering something in return.
Not only is the functionality useful sometimes, but I also personally feel that it’s my job to be on the front lines of this battle, which means wading around in The Internet of Trash so that others don’t get as dirty.
We’re the shepherds through this mess, and it’s our job to embrace this beautiful and broken future that’s hurtling towards us.
Hug it, so it can’t stab you (as hard).
Summary
Casual attackers won’t be able to hack you through your smart speaker because it’s non-trivial.
Professional attackers won’t need to hack you through your smart speaker because it’s super easy to do other ways.
The risk for most consumers is far lower than the benefits, and the goal of security is not to get risk to zero—it’s to make it low enough to function normally without fear.
If you’re in security yourself, consider using these devices as part of your duty to help protect and educate the masses.
Notes
If you do decide to use IoT devices like I advocate here, know that there’s a major difference between devices from someone like Amazon, which has billions of dollars to lose and works very hard on security, vs. some no-name vendor from China. Be picky about what you install.
Also, no matter what vendor it is, put IoT stuff on its own network. Just assume it’s doing something shady and you will never be disappointed. Ok, not never. But less often.
—
I spend between 5 and 20 hours on this content every week, and if you're someone who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
May 24, 2018
Economic Inequality is the Norm, Not the Exception
For typography reasons I recommend you read this piece in its original form at Economic Inequality is the Norm, Not the Exception
—

I read and think a lot about technology, automation and how it will impact humanity.
One of the most important dynamics there is the potential for technology to increase income inequality, and for automation to take jobs from those who need them most.
For some reason—perhaps my being born and raised in the San Francisco Bay Area—I have mostly seen that change as new. I’ve been writing essay after essay warning that there was about to be a new and extreme separation between the top 5% rich and the bottom 80% poor.
I still think that, but after reading books like Thomas Piketty’s Capital in the 21st Century, and a couple dozen others, I’ve started to absorb his idea that inequality is normally high, and it’s only certain types of dramatic events that change that.
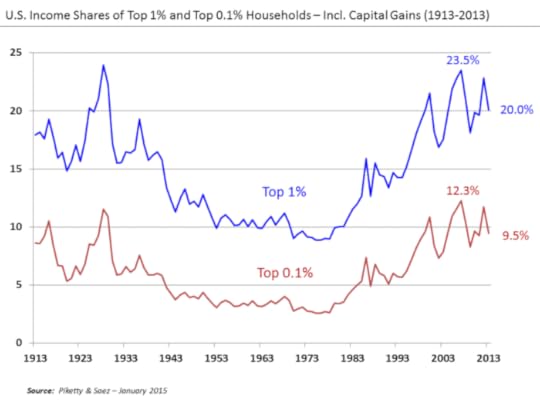
The big wars brought remarkable economic equality to the United States and Europe, for example, but inequality was high before then, and it’s returning to that state now.
But that’s just going a hundred years or so backward. What about looking back centuries or millennia?
I’m not a historian, but it seems to me that the difference between the rich and the poor has usually been quite vast. Let’s just take some civilizations that I can invoke from memory.
Sorry to anyone I’ve angered with this hurried list.
Ottomans
Egyptians
Mayans
Aztecs
Chinese
Greeks
Romans
Mongolians
Incas
Persians
Assyrians
Mesopotamians
Again, I’m not an expert on any of these civilizations, but after some basic searches I can’t find any indicators that these were equal societies. They tended to have strong delineations between class, race, and religion that determined or influenced what your potential and ceiling was as an individual.
And we know this is the case for much of the last 500 years all over the world. There are the nobles, the aristocracy, the special people, and there is everyone else. And in the “evolved” societies that transitioned to being the rich and the poor, even though the old labels often correlated with this status.
Anyway, the point here is not to say that inequality is ok because it’s always been that way. That’s silly. We also used to die of bad dental hygiene and used to think smells caused sickness, not the other way around. Progress is a good thing.
To oppose inequality we must oppose our human nature and human history.
I think we need to remember how new the idea of equality is as a concept. It was present in early Christianity as a concept of equality under God, was nurtured by the Stoics, and was introduced politically in the just the 1700s.
Until the eighteenth century, it was assumed that human beings are unequal by nature — i.e., that there was a natural human hierarchy. This postulate collapsed with the advent of the idea of natural right and its assumption of an equality of natural order among all human beings. ~ PLATO.STANFORD.EDU
It was then that thinkers started mixing the idea with government via Hobbes, Locke, Kant, Dahrendorf, Rousseau, Dworkin, and Vlastos. A major milestone in that journey was the French Revolution, where the people fundamentally rejected the idea that a small elite should have everything while everyone else had nothing.

The French Revolution
So we basically had a hundred years or so after the French Revolution and before the Industrial Revolution, where technology made it much easier for a few to make vast quantities of money. It also brought more material things to the masses, to be sure, but the fruits from those goods were not divided equally.
But then the wars happened, and as Piketty shows, major wars are an equalizer. To be more accurate, actually, catastrophes are equalizers.
Some call the economic unification of 1914-1945, The Great Compression.
Basically, when things are calm, the classes quickly separate into rich and poor. Then, if something happens to disrupt society—like a war, or a famine, or an epidemic—then the existing order is disrupted and things get mixed up again. Like a drink you have to regularly shake to keep homogenous.

Stratification in the fermenting process
The lesson for me was seeing that the default was the opposite of what I thought it was. Growing up I thought the default was equality and there must be an orchestrated evil at play to force the separation. But it seems that’s not the case.
Start Membership
Thank you,
Daniel
May 23, 2018
The Single Reason Harry Potter is Better Than the Marvel MCU
I spent lots of time on typography, so you should read this article in its original form at The Single Reason Harry Potter is Better Than the Marvel MCU
—

I’ve been having a heated discussion with a friend about why I can only take Marvel movies so seriously, and why it’s objectively lower quality entertainment than Harry Potter.
There are spoilers below for Harry Potter, Infinity War, Deadpool 2, and The Bible.
The answer is death.
Humans, as a rule, don’t value that which they cannot lose, and our lives are the ultimate case in point. We care about death because it’s final and that’s what makes it matter. It’s the same in any good story because good stories mimic reality.
It was sad that Dumbledore died in Harry Potter not because it happened, but because it was permanent. Same with Hedwig, and Dobby (a free Elf). And Snape died to save Harry because of his love for Harry’s mother.
It’s not the dying that makes death significant. It’s the utter permanence of the condition.
This is also the entire foundation for caring about action and danger. Action doesn’t matter much if it doesn’t involve risk. And there is far less risk if you cannot die.
That brings us to the Marvel Universe.
We just watched Thanos kill half of the franchise. They all disappeared. Into literal dust. Killed by the most powerful weapon in the universe.
Except they didn’t. Spider-Man already has his new movie announced, so that’s a bit of a tell there.
Do we really think they killed Thor, and Black Panther, and Captain America? Of course not. They’ll roll back time and resurrect everything. And Deadpool just did it again (twice) in the second movie.
The difference between Potter and Marvel is that Potter is a story and the MCU is a soap opera.
It’s disgusting.

Dumbledore is dead. Snape is dead. Dobby is dead. And these sacrifices cannot be reversed or undone. That’s what makes them meaningful.
When someone gets hit with Avada Kedavra, there’s no coming back.
The Marvel Universe isn’t bad because it’s fantasy, or because it’s about superheroes.
It’s bad because nothing that happens in it actually matters.
Notes
It’s different, by the way, if the death and rebirth is on purpose and is artfully weaved into the story, like for Neo or Potter.
[ BONUS BIBLE SPOILER ] The worst example of nullifying a sacrifice is Jesus. He was alive for an eternity before he died, he’s alive now, and he will be alive for eternity in the future. He was actually only “dead” for three days, and since he is basically God he obviously knew he was coming back anyway. Worst sacrifice ever, but it’s still the foundation of the top religion on planet earth. Maybe the MCU has a chance after all.
—
I spend between 5 and 20 hours on this content every week, and if you're a generous type who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
May 14, 2018
Security Report Analysis: 2018 DBIR Report
I spent lots of time on typography, so you should read this article in its original form at Security Report Analysis: 2018 DBIR Report
—

In this Security Report Analysis (SRA) series I look at various security reports and pull out the main points.
This doesn’t replace a complete and detailed read of these reports, but it exposes you to some of the key takeaways that you might not otherwise have seen.
REPORT: The 2018 DBIR Report
Key points
These points are a combination of the report’s actual points combined with my own interpretation of them. Some of the analysis is not theirs, in other words. Don’t take this as me putting words in their mouths, but rather me trying to parse and interpret for my and your benefit.
This year’s report covers 53,308 security incidents, 2,216 data breaches, 65 countries, 67 contributors
More of the same: same attacks are still working because same weaknesses still exist
73% attacks were outsiders
12% attacks were nation states
Financial was the lead motive, followed by Espionage
Errors were 17% of breaches
The top malware type was ransomware (39%)

90% of accommodation industry breaches involved POS systems
Healthcare is the only industry where insider threat is greater than outside (56%)
In the public sector (government), Espionage was the motive in 44% of cases
Most attacks across industries are opportunistic, but in Manufacturing 88% are targeted
The Information and Retail sectors were most plagued by web application attacks
66% of breaches took months or longer to discover
94% of security incidents and 90% of confirmed data breaches fall into DBIR’s nine incident classification patterns across all years

DBIR recommendations
Be vigilant
Make people your first line of defense
Only keep data on a need-to-know basis
Patch promptly
Encrypt sensitive data
Use two-factor authentication
Don’t forget physical security
My analysis

The top two issues that resulted in breaches (not just incidents) were Web Application Attacks and Miscellaneous Errors. I find that fascinating and familiar.
The recommendations from DBIR don’t seem right to me.
For web apps that means:
Finding all your web applications
Performing regular vulnerability assessments on them
Remediating issues such as SQli, L/RFI that can cause the difference between a breach and an incident.
Check out Jeremiah Grossman’s essay on this topic.
I think there should be more focus on the acute problems causing the first n most likely causes of breaches, because not all vulnerabilities lead to losses in equal proportion.
I launched a service called Helios that addresses this problem directly.
For Miscellaneous Errors, you need to be watching your environment continuously, and ensuring that if something moves into an undesired state, you’ll know about it immediately.
Spending money on threat intelligence when you don’t have asset management and monitoring is like being 100 pounds overweight from cheeseburgers and dumping money into multivitamins instead of reducing calories and exercising.
There is just too much focus on edge cases in our industry. It’s not usually the 0-day that’s going to get you, or North Korea. It’s the admin portal that’s been sitting out there for weeks without you knowing. It’s the websites you didn’t know about that are running two-year-old unpatched frameworks. It’s the EC2 boxes that have Mongo on them full of your data with no credentials. And unprotected S3 buckets.
It’s the big stuff.
Work on that first.
—
Anyway, another stellar report from Verizon. I think this report should be an InfoSec Event every time it’s released.
The week it comes out, every infosec team should take a day out of meetings and go through the results to see if they should adjust any of their priorities.
REPORT: The 2018 DBIR Report
Notes
While this capture can be helpful, I suggest reading the whole report for full context. The writing was remarkably easy to move through.
The interactive version of the report was quite strong as well. Link
—
I spend between 5 and 20 hours on this content every week, and if you're a generous type who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
May 13, 2018
The Waking Up Podcast: Sam Harris vs. Sean Carroll on Free Will
I spent lots of time on typography, so you should read this article in its original form at The Waking Up Podcast: Sam Harris vs. Sean Carroll on Free Will
—

Sam Harris recently had Sean Carroll on his Waking Up podcast, and to my delight they arrived pretty quickly at the free will topic.
You can read more of my free will content here.
Carroll is both a physicist and a compatibilist, which was both surprising and exciting. It was surprising because I naturally expect hard science types to be incompatibilists (my own bias), and it was exciting because I couldn’t wait to hear his argument.
I’ve already been flirting with my own version of almost-compatibilism, in what I call The Absurdist Chasm. This is basically the argument that humans are unable to functionally operates as an incompatibilist in the ways that matter, e.g., trying to be a better person, planning for the future, etc. Basically, the moment you start planning you’re assuming that something you can do could make a difference, which it can’t.
This is a subtlety that I’m trying to warm Sam up to, with little success so far. I think the answer comes to us from Camus’ Absurdism, which is what that piece is about.
The discussion
Anyway, here’s how the debate between Sam and Sean proceeded.
They both agreed Libertarian free will was false.
Sam talked about the ability to have done otherwise.
Sean gave some background on the multiple universes idea, which is a prevailing theory at this point.
Sean said that Sam’s concept of “other options” was strange because it ultimately came down to not knowing what the other options were. So basically, because we couldn’t know what the other options were, it’s the same as us making choices.
Sam asked to confirm this—i.e., that the opening for free will lies in our lack of knowledge of all the variables.
Sean agreed.
Sam confirmed this by asking if we knew everything would this erode this view of freedom.
Sean agreed.
Sam then said that it didn’t matter how much we knew because if someone as rolling dice and we were doing it, it wouldn’t make us free.
I’m paraphrasing Sean here, but I believe I’m doing it accurately.
Sean then made the main point, which is that the model of us making choices is simply a matter of a best, usable description of what happens with humans. He’s not claiming it’s particularly accurate, or true, or precise. He’s saying it’s most true and most useful.
Analysis
This argument from Sean was fascinating to me because I see his point and I agree with him. He’s saying it’s a useful model to imagine humans as making choices. 100%.
Where I think he’s going wrong is not realizing that different questions require different models.
If you’re asking 10,000 people what kind of shows they like to watch, or whether they want to go into engineering or social sciences, then we should use that model. It makes no sense to talk about degree selection, or food preferences, at the level of physics or biology. It’s just people making choices.
But when the question changes to something like:
What should be done with violent criminals?
That model of “humans make choices” suddenly fails for anyone who simultaneously understands the biology and wishes to be just. Sam’s example here was spot on.
If there were a pill that could cure you of psychopathy, then when someone killed people we’d simply call them sick—not evil.
In short, our criminal just system will vary significantly based on whether we use the “people make bad choices” model or the “evil people are broken” model.
So I think they were almost communicating, but not quite. This is sadly a common occurrence on Sam’s podcast, but I think that’s usually because 1) malice on the part of the guest, or 2) the topics are so nuanced.
I think Sam is obviously right about the fact that seeing humans as making real (Libertarian-like) choices is a poor model handling human criminal justice in a lot of cases. And I think Sean is obviously right that that same model is just fine for most everyday situations.
So this brings me back to The Absurdist Chasm. The truth is that we need to be able to do what Camus’ advocated. We have to know the impossible truth while simultaneously behaving as if the fairytale were possible.
We have to become comfortable with living as Compatibilists for 99% of situations, all the while knowing that reality is Incompatibilist.
To some that makes them Compatibilists. To me—and I think to Sam—that makes us Incompatibilists.
Once again it comes down to semantics. And I think Sam should do his best to address this specific Absurdism issue with new guests like Sean and also with Dan Dennett the next time he talks to him.
In one mode we’re talking about true nature of the world, and in another we’re talking about the way we conduct our everyday, human lives. That’s why Camus is so relevant here.
It’s that tension between the emptiness of reality and our innate optimism that defines so much of our existence.
Notes
Both Sean Carroll and Dan Dennett have single syllable first names followed by double consonant versions of their last names. And both are Compatibilists.
—
I spend between 5 and 20 hours on this content every week, and if you're a generous type who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
John Gruber Wrong About the Duplex Demo
I spent lots of time on typography, so you should read this article in its original form at John Gruber Wrong About the Duplex Demo
—

John Gruber of Daring Fireball took a big shot at Google Duplex recently.
He basically said that the way the demo was conducted should make us doubt the legitimacy of the tech.
Why not demo it live? Why only play recordings? When is it rolling out to actual customers? Was there a hands-on after the event where members of the media or conference attendees could talk to Duplex? It’s totally credible that Google would be the first to achieve something like Duplex, but the fact that all they did — as far as I’ve seen — was play a recording just seems off. It feels like a con.Source: Daring Fireball
I disagree.
I think the demos were spot on, and accurate.
The danger of doing a live demo is that you have so little time, and you might hit a snag.
The person might not answer
It might be a bad connection
It might be a scenario that the AI doesn’t pick up
Other things we’re not thinking of
If there is 5% chance that that would happen, and a 95% chance that it wouldn’t, they’re still taking a massive risk by doing the demo because they could destroy the product’s reputation in one shot when it actually is super useful even in its current state.
So unless they’re lying about being close, and about it being useful already, I think they did the right thing.
And we’ll know that anyway by how quickly it comes to the market.
—
I spend between 5 and 20 hours on this content every week, and if you're a generous type who can afford fancy coffee, please consider becoming a member for just $5/month…
Thank you,
Daniel
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers



