Daniel Miessler's Blog, page 89
January 18, 2019
Those Bashing Smart Locks Have Forgotten How Easy it is to Pick Regular Ones

There’s currently a major backlash in the InfoSec community against so-called “smart” locks.
And it’s not just by people who naturally overreact to change, or from people outside of InfoSec: there are plenty of smart people in our field—whom I respect greatly—that are making loud noises against this technology. So I want to make it absolutely clear that 1) there are smart arguments on both sides of this discussion, and 2) I’m still open to being wrong about this.

People picking locks at an Infosec event
My main argument isn’t that smart locks are great security, or that IoT security is fine, or that the new is always better than the old—or any of that garbage. I lead The OWASP IoT Security Project—-which details precisely how insecure IoT systems can be, and I’ve personally been finding these kinds of flaws in real devices for over a decade.
IoT Security is still a garbage fire, and we’re just starting to get our collective arms around the heat and smell of the problem. So you’re not going to hear the “IoT Security is Great” argument from me. What you’re going to hear from me is an appeal to practicality and risk management by asking a very simple question:
What’s easier for your most likely attacker to bypass—a regular lock, or a smart lock?
I’m not a lockpicking expert, by the way, but that’s kind of the point. You don’t have to be to get past most locks.
Many people in InfoSec have been to security conferences where they’ve learned in a matter of minutes how to open most locks with basic lockpicks. And once you’ve practiced for any period of time you can open the most commonly used house locks in mere seconds. And that’s not even talking about bump keys, snap guns, or any of the other more advanced techniques that are now available.
I’m not saying smart locks have good security—I’m reminding people that regular locks have virtually none.
The problem I see in this discussion is that we’ve somehow—in the information security community—forgotten about the risk that we have already accepted. For hundreds of years we’ve protected our homes and businesses with lock technology that’s absolutely trivial to bypass for anyone who spends even the slightest effort.
Threat modeling brings reality into focus
This is why threat modeling is so important: it allows us to move away from the open-ended theoretical discussion and into the world of the scenarios you’re most likely to face. So let’s do a few scenarios and see where we end up.
I honestly ran through this threat model not knowing where it would take me, which is why they’re so valuable.
You live in a middle-class neighborhood in Middle America, most of the people in the neighborhood are teachers, cops, DMV workers, and just regular folk. There’s very little violent crime, but there have been some home break-ins recently due to the opiate crisis.
You live in a high-tech housing area in a big city full of the smartest tech workers in the world, e.g., one of the Facebook housing units in Menlo Park, or a similar place in Seattle or Austin.
You live in a very established and nice neighborhood with an active neighborhood watch, where everyone knows everyone else, and all crime is very rare.
You live in a high-property-crime area in a big city. It’s supposed to be getting better soon as people work on clean-up efforts, but cars and homes are getting broken into often, with people finding things stolen, drug paraphernalia left behind, etc.
I think these are decent approximations of the bulk of people’s living situations in the United States. So for each of these attack scenarios, let’s ask ourselves: who the attacker is, how they’re getting into the house, and whether they’re going to have more, less, or equal success facing a regular lock or a smart lock.
I’m also not a property crime expert, so feel free to correct me if you are.
Now let’s model some attackers:
Drug-addicted, looking for anything to sell or trade for opiates
Mid-tier professional thieves who go after mid-tier neighborhoods for TVs, computers, jewelry before moving on or getting caught
High-end professional thieves who go after jewelry, art, and the content of safes
Neighborhood kids looking for opportunities for fun or to find something to sell for quick cash
Disgruntled delivery people
Roving package thieves
Now let’s start combining these targets with their potential attackers in likely scenarios:
Addict as threat actor
Addicts vs. Middle America: Why not kick in the door or break a window?
Addicts vs. High Tech Area: Why not kick in the door or break a window?
Addicts vs. Super Nice Area: Why not kick in the door or break a window?
Addicts vs. High Crime Area: Why not kick in the door or break a window?
Mid-tier Professional as threat actor
Mid-tier vs. Middle America: Pick the lock, go through window, kick door
Mid-tier vs. High Tech Area: Pick the lock, go through window, kick door
Mid-tier vs. Super Nice Area: Pick the lock, go through window, kick door
Mid-tier vs. High Crime Area: Pick the lock, go through window, kick door
For the mid-tier and above, if everyone in a neighborhood had a basic smart lock with a pin pad set to the same thing or something, that could be a good way in.
High-end Professional as threat actor
High-end vs. Middle America: Mismatched target, unlikely to attack smart locks
High-end vs. High Tech Area: Possible smart lock attacks to steal computers or intellectual property
High-end vs. Super Nice Area: Possible smart lock attacks, but easier entry available
High-end vs. High Crime Area: Mismatched target, unlikely to attack smart locks
Neighborhood kids as threat actor
Neighborhood kids vs. Middle America: Possible smart lock attacks, if it’s trivial
Neighborhood kids vs. High Tech Area: Mismatched target, unlikely to attack smart locks
Neighborhood kids vs. Super Nice Area: Possible smart lock attacks, but risk is probably not worth it
Neighborhood kids vs. High Crime Area: Why not kick in the door or break a window?
Disgruntled delivery person as threat actor
Disgruntled delivery person vs. Middle America: Possible, but they already have tons of opportunity to break the law and steal merchandise every day, and they’re more likely to avoid chances to be caught (logs, video, etc.)
Disgruntled delivery person vs. High Tech Area: Possible if easy enough, since the payoff might be sufficient? But why not pick the lock?
Disgruntled delivery person vs. Super Nice Area: Possible if easy enough, since the payoff might be sufficient? But why not pick the lock?
Disgruntled delivery person vs. High Crime Area: Other options seem better than spending time on hacking the smart lock.
Package thieves as threat actor

Package thieves vs. Middle America: Seems like they’d prefer to pick a lock vs. mess with a smart lock location because smart lock people are likely to have a camera in or around the house.
Package thieves vs. High Tech Area: Seems like they’d prefer to pick a lock vs. mess with a smart lock location because smart lock people are likely to have a camera in or around the house.
Package thieves vs. Super Nice Area: Mismatched target, unlikely to attack smart locks (you don’t go to Beverly Hills to break into homes and steal their Amazon packages)
Package thieves vs. High Crime Area: Other options seem better than spending time on hacking the smart lock.
Whew. Ok. That was fun.
So we did see a few situations where attacking a smart lock could make sense, assuming they were similar enough for it to be quick and easy—like in a housing complex for tech employees (in say 5 years). But in most cases I think this cursory analysis shows that either:
It’s easier to kick in the door or go through a window (or pick the lock) than it is to even look at a smart lock, or…
Attackers are likely to start associating smart locks with video capture, remote monitoring, and lots of other IoT-ish functionality, which will mean a higher risk of getting caught.
Summary
There are smart people arguing against smart locks, and it’s a discussion worth having.
IoT Security isn’t good, and so neither is smart lock security.
We forget the risks we’re used to—and in this case the thing we’re forgetting is now easy it is to pick a lock or kick in a door.
If you run through the scenarios you’re likely to face, you’ll see that very few of them make it easier to get into your home because you have a smart lock, since you either have a threat actor mismatch or the alternatives are simply better for the attacker.
The fact that people with smart locks are likely to have cameras and other smart security technology is likely to become a significant deterrent soon—if it hasn’t already—which will result in more people just moving on to the next home instead of messing with your house.
I think all of this combines to this:
If a smart lock gives you significant features and convenience—above what you get with a normal lock—then it’s likely to be more than worth the risk tradeoff.
This is because it won’t be about replacing good security (old lock) with good security (IoT lock), but rather about replacing no security with something equally bad that’s more convenient and that might be a deterrent as well.
Notes
The front door is bad overall security for a home, and just changing your lock don’t solve that.
To me, the best argument against smart locks is that with a common door you already have the weakness of the existing conventional lock, and if you are still able to access that regular lock mechanism when you install a smart lock then you’ve simply *added* attack surface rather than changed it. In other words: you’ve now combined the weakness of the legacy lock with the weakness of the smart lock, which can only make the overall result weaker.
If you can think of other abuse cases that I haven’t included, please let me know. For example, how to combine the internet vector with the local/physical side.
The other complication with this discussion is that there are many potential combinations of the basic control variables, e.g., the strength of the door structure vs. being kicked in, the ease of entering via windows compared to the door, and the type of crime in the area in question. It’s much different, for example, if we’re defending against young, smart rich kids who might break in and steal the Amazon packages in your foyer while your maid is upstairs, or if you’re defending against frazzled adults looking for meth money.
I’d also say that there are many “smart” locks that are just trivial to bypass because they’re just garbage. And in those cases it just requires that knowledge to take advantage, and there I’d side with them being *worse* for security. But I think those are likely to be spread out and hard to take advantage of.
Another key point is that it’s possible to oppose smart lock implementation without even arguing that they’re easier to bypass. I have a friend/associate who is currently being told that her whole building is being “upgraded” to smart locks, which will be able to log everything and send those logs to some random startup, without her knowledge or transparency. In short, there are privacy concerns in addition to the larger physical access question.
January 17, 2019
Summary: The Dichotomy of Leadership
9/10
My One-Sentence Summary
Content Extraction
Takeaways
My book summaries are designed as captures for what I’ve read, and aren’t necessarily great standalone resources for those who have not read the book.
Their purpose is to ensure that I capture what I learn from any given text, so as to avoid realizing years later that I have no idea what it was about or how I benefited from it.
My One-Sentence Summary
The best leaders manage the balance between the extremes of a few core attributes: confidence and humility, discipline vs. creativity, mentoring vs. firing, training hard vs. smart, leading and following, and empowering vs. micromanaging.
Content Extraction

A few of the major leadership attribute spectrums
Empower others, but be willing to step in with micromanagement temporarily if things get out of hand
Don’t be so dominating and intimidating that your leaders can’t step up and lead themselves
Discipline is great, but too much leads to a lack of creativity
Too much creativity and not enough discipline leads to sloppiness and mistakes
All quotes here are from the book itself unless otherwise indicated.
“The three components of great training are realism, fundamentals, and repetition.”
Plan enough to provide comfort when things go wrong, but not so much that you limit creativity
Train in a very realistic way, but don’t overtrain in a way that removes their motivation or overwhelms them with information
Be confident and willing to push through your strategy with others, but also remain humble about the ability for the world to serve you lessons, and about your team’s ability to teach you things you don’t know
Ensure that when you’ve gone too far in one direction in these attributes, that when you correct you don’t overcorrect by going too far in the other direction
Takeaways
The whole book is about constantly adjusting the balances between extremes across multiple leadership attributes.
The key is to be aware of what those attributes are, what their extremes are, and what the downsides are of going too much in each direction.
Great leaders, in other words, are those who can maintain optimal levels of each attribute according to what’s needed to best accomplish the mission in the short and long-term.
You can find my other book summaries here.
Notes
There is a previous book by the same two guys, called Extreme Ownership, and while it was good, it did emphasize the extremes of each point that was made. This book corrects that by focusing everything on the balances that have to be constantly adjusted for the situation. This is basically the better version of the first book, but you can still benefit from the first one as well.
January 14, 2019
Unsupervised Learning: No. 160 (Member Edition)

This is a member-only even episode. Members get the newsletter every week, as well as access to all previous episodes, while free subscribers only get odd episodes every other week.
Why I Think the NSA is Releasing a Free Reverse Engineering Tool This Year at RSA

The NSA is releasing a free reverse engineering tool this year at the RSA security conference in San Francisco.
A lot of people are asking about the motive of the NSA releasing a free reverse engineering tool at RSA this year.
— ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ (@DanielMiessler) January 9, 2019
Theories include: it’s a backdoor, it’s a tracking mechanism, etc.
My opinion? Recruiting.
It’s a PR move to attract talent post-Snowden/ShadowBrokers.
Many in the security community—who have an understandable and healthy distrust of the NSA—are wondering if there could be a backdoor in the software, if they’re using it to spy on people, etc. The various theories are interesting reading.
And reducing the loss of talent they already have.
I think the answer is much simpler—they’re using the release of the tool to inject some goodwill into the community in hopes of attracting new talent.
In short, it’s all about recruiting.
Between Snowden, the ShadowBrokers leaks, and the damage caused by EternalBlue and NotPetya, I’m guessing morale is at a dangerously low level and they need to do something to raise interest and motivation for working there.
Releasing an open-source tool to help people do reverse engineering, while simultaneously training people how to be good guys and gals is a pretty smart move in my mind.
The simplest explanation is usually the right one.
— Lesley Carhart (@hacks4pancakes) January 9, 2019
Someone mentioned on Twitter that the move reminded them of The Last Starfighter, where an alien spaceforce used a video game to find top talent to help defend the world. I think that’s spot on.

The hero plays a video game that’s actually a trainer
The military has been doing this for years as sort of an open secret, and they spend tons of money making the military and government appear in a positive light in Hollywood movies.
Some might think that’s gross, but I think the worst part about it is the fact that so few people notice—or would even care if they knew. It’s the same kind of thing here with this release. It smells exactly like public relations. But is that really a bad thing?
I wish they’d just come out and say it. Own the fact that it’s a bit of PR, and recruiting, and camaraderie all in one.
Despite the failings of the NSA in recent years, I don’t know many Americans who think we don’t need them. And to do their job well they need talent. And for that talent to perform they need to believe that they’re on the good side.
Or they’re Mr. Burns waiting to pounce—who knows…
I see the overture as a good thing. It’s them eating a piece of humble pie, and cautiously reaching out to the community with a gift. I hope we accept it, and I hope it makes the tenuous bond between us stronger.
Because like it or not, we need each other.
The last thing we need—with Russia and China owning us with impunity—is to be fighting amongst ourselves.
January 10, 2019
A Remarkably Clear Overview of The Border Security Situation
I recently stumbled onto a podcast with Scott Adams about border security, and what I learned from it not only surprised me, but also Scott Adams as the host.
I used to be a huge Scott Adams fan, but that went away when he revealed himself to be one who places his tax rate above the welfare of his community and planet. I still respect his writing and mind, however.
He brought on a guest named Brandon Darby, who’s a border security expert, and he did so presumably to get him to say he supported the wall on our southern border. What happened, however, was much more interesting.
The expert proceeded to completely obliterate Scott’s, Scott’s audience’s, and my understanding of the security situation on the border. Here’s a rough summary of what was said and what I learned:
Darby would not actually say if he supported the wall or not—much to the dismay of both Scott and his audience. This really surprised me, since Darby is a writer for Breitbart, and I just assumed the whole Breitbart cohort was pro-Trump and therefore pro-wall.
Darby’s opinion was actually far more nuanced than that. He said he was for security on the border, but that a wall by itself could absolutely not provide that.
Scott pressed him harder, and what basically came out was that Darby believed a full wall with full lockdown at every entry point would be better security for us—and better safety for the incoming migrants—than what we’re doing now, which is a highly-porous, partial solution—was far worse.
In short, open borders would be better security, and a full lockdown would be better security—and this half-measure that we’re doing now is causing a major portion of the problem.
Darby repeatedly showed himself to actually care about not only our security in the U.S., but the horrific situation for the migrants as well.
Basically, when the border is partially open, it encourages people to bypass security in unsafe ways. If it were completely open they wouldn’t have to and it would make things safer. And if things were completely locked down—at all ports, all airports, all entrances—then there would be enough of a deterrent to keep people from trying. But we’re stuck in the middle.
But the most interesting part came when Darby broke down the actual security situation in Mexico, and what the U.S. should be doing to fix it.
Essentially (talking from his position that I find compelling but am not enough of an expert to fully endorse), Mexico is a partially failed narco-state (his wording). They’re in extraordinarily bad shape, and that’s the cause of all the violence.
He believes the best thing the U.S. could do is declare a number of key cartels to be terrorist organizations, which would freeze their assets and cause them all sorts of friction that would help Mexico itself.
Basically, right now we’re letting the cartels do what they want, which removes the rule of law, which makes people desperate to flee to the U.S.
In short, if we really wanted to reduce the massive numbers of people trying to get here illegally, we’d help them regain control over their government and their country by putting pressure on certain cartels—which would bring the others in line.
I was blown away, and so was Scott.
He was so expecting to have this expert on to tell us how the wall was a good idea. And honestly, if he sounded credible, I would have changed my opinion. I’m open to reality model updates, which is the whole reason I listened in the first place—to hear the best opposing arguments to my current opinion.
And I got one, but not in the way I imagined. And it was remarkable.
Summary
A wall would not really help at all unless we did lots of other things along with it, which are definitely not going to happen.
The best solution is completely open or completely closed. It’s the middle ground that’s hurting us.
If we really wanted to help—at a strategic level—we’d use the State Department’s counterterrorism capabilities to help Mexico get the cartels under control, which would return Mexico to some state of normalcy and reduce the number of people risking their lives to come here.
For anyone who cares about this border security situation, I recommend you listen to this podcast with a willingness to change your opinion.
I’m glad I did.
January 6, 2019
Unsupervised Learning: No. 159

Unsupervised Learning is my weekly show where I spend 5-20 hours finding the most interesting stories in security, technology, and humans, which I then curate into a 30-minute podcast & companion newsletter.
The goal is to catch you up on current events, show you the best content from around the web, and hopefully give you something to think about as well.
Subscribe to the Newsletter or Podcast
How to Monitor a Website’s Uptime for $0.75/month on Amazon

If you’re like me, you care if your website goes down.
There have been services available for years that monitor your site and let you know if it goes down. The one I’ve been using for over a decade is Pingdom, which is great. It gives you tons of advanced options like searching for text within probe responses, controlling where your probes come from, etc.
But the plan I had was around $15/month—which I found a bit pricey since I just needed basic monitoring.
Being an Amazon fan, and knowing that they seem to have an offering for everything, I started digging into whether I could create a simple monitor on their platform. And sure enough—you can—on Route 53.
Route 53 Monitor Geos
And the process is dead simple.
1) Log into your AWS Console and navigate to the Route 53 dashboard.

Adding a Route 53 Check
2) Configure your check based on your site attributes and preferences.
I recommend setting your check to the minimum of every 30 seconds, with all geos enabled, and set the threshold to a single failure.
3) Save your check configuration.
You now have a check that will monitor your site—every 30 seconds—and let you know via email if it ever goes down.
For $0.75.
Pingdom and the like are great for heavy lifting, but this more than does the job for me.
How Nassim Taleb is Both Right and Wrong About IQ

Nassim Taleb is making loud noises about how IQ is basically a big scam, and how it doesn’t mean anything. Like usual, he’s onto something, but also like usual his passion and snark is causing him to miss something major.
For the record, I think Taleb is an absolute genius. I’ve read all of his books, and some of them multiple times.
He’s basically saying that you can have a super high IQ and not be famous and rich like he is, which is of course true. His examples were highly-paid back office people at major investment companies. In his mind, losers, evidently. Of course they’re probably making between 200-500K/year.
So guess what? Yes, IQ should matter—to most people. Why? Because it’s correlated with academic success and therefore income. Ask most parents if they care about those things.
7) I put "IQ" in "" as I don't believe that measured IQ includes ability to tinker aggressively, real IQ for me. #GreenLumber #AntiFragile
— Nassim Nicholas Taleb (@nntaleb) March 11, 2017
Now if you’re Nassim Taleb, or the head of an art gallery, and you are being asked to pick your new best friend, or book author, or top poet, does IQ matter that much? No. He’s clearly focused on creative hackers and innovators. Because that’s what he values.
But if you’re trying to predict if someone is going to be a lawyer, or a doctor, or an engineer, or lots of major careers that make decent money, you can do much worse than looking at their IQ score.
IQ is not a cognitive worth score. Or a “does this person have value” score. Or even an intelligence score. It’s a very specific type of test for a very specific type of performance, and that type of ability happens to be correlated strongly with outcomes people really value.
So Taleb is simultaneously right and wrong. It all depends on the question you’re trying to answer. The thing you’re trying to predict.
If you are trying to predict if someone is going to be a remarkable artist, or a great friend, or a moral hero—no it doesn’t matter. But if you’re trying to predict future success in school and in the workforce, in terms of income, it’s a pretty strong signal. So for some it means nothing, and for some it means quite a lot.
I also find it hilarious when famous people who get noticed for bashing IQ almost inevitably have high ones. I’d bet Taleb’s score is way over 120. It’s pretty easy (and common) for people with high intelligence to talk about how little it matters. It’s like privilege in that way, well, perhaps because it is one.
Summary
Yes, IQ matters (to a lot of people) because it strongly predicts academic success and income.
No, that is not a measure of a person. Creativity matters. Kindness matters. And IQ measures a fairly limited number of things about a person’s mental capabilities.
Taleb is right if he’s attacking people who think IQ is some kind of magical thing that guarantees you’re a genius. It doesn’t.
But he’s wrong if he’s saying we should throw it out as uninteresting and unworthy of study.
January 5, 2019
How to Ctrl-Alt-Delete in VMware

Few things are more annoying than being stuck inside a bad UI, and withinin virtualization environments is a common place for that to happen.
Here’s how to do the three-finger-salute inside VMware.
Regular: Ctrl+Alt+Del
Full-sized Mac keyboard: FwdDel+Ctrl+Option (Delete below Help key)
Abridged Mac Keyboard, Fn+Ctrl+Option+Delete
January 3, 2019
Site Traffic Metrics for 2018

So the biggest story for my site’s traffic in 2018 is the Google Algorithm Changes that I wrote about here.
It was a bloodbath, basically.
I am currently at 50% of my traffic as compared to the beginning of 2018. But I’m hoping that’ll re-adjust as Google tries to figure out who has authority on various topics and who doesn’t.
Here’s some browser data—with Chrome still dominating.
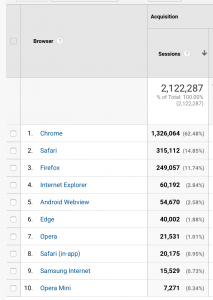
And here’s some social media numbers.
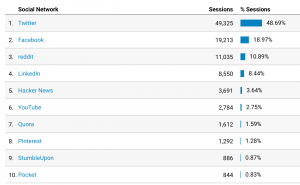
Overall I still had way over 2 million pageviews, so it was still a good year. But I can’t help but feel like the year was a bad one due to losing 50% of my traffic starting around July.
I really hope Google re-adjusts and brings me back to my former levels—and hopefully even more given the work I’ve been doing on cleanup.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers




