Daniel Miessler's Blog, page 79
September 6, 2019
My Favorite Superhuman Shortcuts

As I talked about in an earlier post, I just started checking out Superhuman. And the first thing I like to do with a new tool is learn its shortcuts.
Here are my core ones so far:
Basics & nav
This is how you search in Vim!
/ — search
shift-u — show unread
shift-s — show starred
c — compose
f — forward
enter — reply all
r — reply
shift-n — show new messages
cmd-enter — send
Unique
! — mark as spam
cmd—u — unsubscribe
cmd—; — use snippet
: — insert emoji
cmd-shift-7 — numbers
cmd-shift-8 — bullets
cmd-shift-9 — quote
tab — indent
cmd-] — increase indent
cmd-[ — decrease indent
Navigation
g—i — go to inbox
g—s — go to starred
g—d — go to drafts
g—t — go to sent
My favorites so far
My favorites out of all of these are:
/ to search
cmd—u — use snippet
g-i and g-s for nav
cmd-shift-i intro (move sender to BCC)
Overall, I really enjoy the extremely terminal-like feel to the interface.
Now lete’s see how I am getting along after a couple weeks.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
September 5, 2019
First Impressions of the Superhuman Email Service

Like many others, I’ve been observing the hype around Superhuman for a while now. I signed up to get on the list forever ago, but forgot about it until a member sent me an invite a few weeks back.
Looks like the marketing worked.
That’s when I found out it was $30/month, which seems exorbitant in the current market. So much so that I was curious whether it was worth it.
Setup

So one thing that was interesting about the setup is that you can’t just download the client, connect it to your Gmail, and be on your way.
Sep 7, 2019 — I now think this was essential to me learning how to use it.
Nope—you have to set up a consulting appointment and have someone walk you through everything.
Having gone through it, this serves three not so subtle purposes:
It makes sure you know enough about the product to not think it sucks just because you don’t know how to use it.
It makes it feel like the product was (somewhat) customized for you, which makes you feel (somewhat) special.
It onboards you enough that you feel like you have some momentum with it already.
There’s a weird cult-like feeling to it actually. It makes people want to use it just because others aren’t, and you’ve seen behind the scenes, and you’re doing things with your email that others can’t.
Don’t underestimate how powerful this effect is.
Oh, and if someone makes fun of you for paying $30 bucks a month for it—that’s becasue they just don’t get it.
wink wink
Anyway, I see this as a massive inoculation against trying the service and cancelling. It’s almost like Elysium, where you want to stop paying the $50/month but you also don’t want to be the dumbass who stopped paying for something that actually helps.
It’s ingenious marketing.
Anyway.
The email clients

So there are two clients: a desktop client and a mobile client.
I’ve been a Spark user for quite some time, and that seems to be their main competition besides Gmail itself, so a good amount of the features seemed somewhat familiar from that.
A good example is the swiping left or right to perform certain actions.
Overall, the basic look and feel of the clients seemed very similar to Spark, with a few exceptions.
Superhuman is cleaner and faster than Spark.
Spark has more features (see above).
Superhuman is more ambitious (see below).
Superhuman is truly trying to change email
The thing that grabbed me during the consultation was that my associate was seriously versed on email workflows, and productivity research, and even pushed back on the way I was doing things.
I was like,
Yeah, I like it this way because X and Y.
And he came back immediately with,
Well, we don’t recommend you do it that way. We built everything around doing it this way instead, and I suggest you at least try it that way.
He wasn’t rude about it, but he wasn’t playing either. He was serious. He honestly believed that this way (archiving vs. leaving things in the inbox) would make a massive difference.
Part of that is just being a good account manager. You don’t want people canceling because they didn’t see much benefit. But another part seemed to be a genuine desire to see people do email in a different and better way.
I liked that.
What Superhuman does better than any other client

So here’s what I absolutely love about Superhuman.
It’s designed for keyboard interaction.
Not a little bit, but from the ground up. I can use Vim commands to navigate mail. Escape is a major player in the workflow. There’s a central command invocation interface (Cmd-K) that presents you tons of options.
And in general it’s just clearly designed to be used with high efficiency. And that combined with the philosophy of Zero Inbox, archiving vs. letting things accumulate in the inbox, etc., all make it a truly different thing.
It doesn’t feel like just a slightly faster and better Spark or Gmail. It feels different enough to be its own thing, which is admirable given how little has changed in email clients since Gmail came out.
Thoughts
I’m still in my first day, so I can’t tell you much more than these first impressions.
I’m actually already an Inbox Zero guy anyway, so that won’t be one of the switches.
Most importantly, I can’t tell you if it really will change anything about my workflow, or if it’s going to pretty much be email as usual. But I will update this post with thoughts after 1-3 weeks.
Summary
It really does feel different than other offerings.
$30 is a lot of money, so it better be a lot better.
Absolutely love the Vim-y feel to the interface.
Loved the true belief and conviction from the onboarding team.
I don’t love the sneaky lock-in techniques, but I understand them.
Ultimately, I think it’s worth trying out if you are willing to honestly try a better way of doing email.
But if you’re just looking for a better version of Spark, it’s probably not going to be worth $360/year.
See you in a bit for the update!
Update: Sep 6, 2019 — So it’s been a couple of days now and honestly it’s becoming pure bliss. The shortcuts are better than I could have imagined (it reminds me of my Mutt days), and I’ve converted to complete Inbox Zero by archiving absolutely everything. I think I’m definitely going to become a permanent customer. More updates to follow.

Update: Sep 7, 2019 — Loving the gorgeous backgrounds when you hit Inbox Zero. Here’s my summary so far, which could almost serve as a marketing line: It’s cleaner than Spark, faster than Gmail, and with an artistically minimalist design! Only thing I would like is the ability to customize some of the shortcuts, so I can make it even more like Vim. And an integrated inbox for multiple accounts. More updates to follow.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
First Impressions with Superhuman

Like many people I’ve been hearing the hype about Superhuman for a long time now.
I signed up to get on the list forever ago, but forgot about it until a member sent me an invite a few weeks back.
Looks like the marketing worked.
That’s when I found out it was $30/month, which seems exorbitant in the current market. So much so that I was curious whether it was worth it.
Setup
So one thing that was interesting about the setup is that you can’t just download the client, connect it to your GMail, and be on your way.
No. You have to set up a consulting appointment and have someone walk you through everything.
Having gone through it, this serves three not so subtle purposes:
It makes sure you know enough about the product to not think it sucks just because you don’t know how to use it.
It makes it feel like the product was (somewhat) customized for you, which makes you feel (somewhat) special.
It onboards you enough that you feel like you have some momentum with it already.
There’s a weird cult-like feeling to it actually. It makes people want to use it just because others aren’t, and you’ve seen behind the scenes, and you’re doing things with your email that others can’t.
Oh, and if someone makes fun of you for paying $30 bucks a month for it—that’s becasue they just don’t get it.
wink wink
Anyway, I see this as a massive innoculation against trying the service and cancelling. It’s almost like Elysium, where you want to stop paying the $50/month but you also don’t want to be the dumbass who stopped paying for something that actually helps.
It’s ingenious marketing.
Anyway.
The email clients
So there are two clients: a desktop client and a mobile client.
I’ve been a Spark user for quite some time, and that seems to be their main competion besides GMail itself, so a good amount of the features seemed somewhat familiar from that.
A good example is the swiping left or right to perform certain actions.
Overall, the basic look and feel of the clients seemed very similar to Spark, with a few exceptions.
Superhuman is cleaner and faster than Spark.
Spark has more features (see above).
Superhuman is more ambitious (see below).
Superhuman is truly trying to change email
The thing that grabbed me during the consultation was that my associate was seriously versed on email workflows, and productivity research, and even pushed back on the way I was doing things.
I was like,
Yeah, I like it this way because X and Y.
And he came back immediately with,
Well, we don’t recommend you do it that way. We built everything around doing it this way instead, and I suggest you at least try it that way.
He wasn’t rude about it, but he wasn’t playing either. He was serious. He honestly believed that this way (archiving vs. leaving things in the inbox) would make a massive difference.
Part of that is just being a good account manager. You don’t want people canceling because they didn’t see much benefit. But another part really seemed to be a desire to see people do email better.
I liked that.
What Superhuman does better than any other client
So here’s what I absolutely love about Superhuman.
It’s designed for keyboard interaction.
Not a little bit, but from the ground up. I can use Vim commands to navigate mail. Escape is a major player in the workflow. There’s a central command invocation interface (Cmd-K) that presents you tons of options.
And in general it’s just clearly designed to be used with high efficiency. And that combined with the philosophy of Zero Inbox, arvhiving vs. letting things accumulate in the inbox, etc., all make it a truly different thing.
It doesn’t feel like just a slightly faster and better Spark or GMail. It feels different enough to be its own thing, which is admirable given how little has changed in email since GMail really.
Thoughts
I’m still in my first day, so I can’t tell you much more than these first impressions.
I’m actually already an Inbox Zero guy anyway, so that won’t be one of the switches.
Most importantly, I can’t tell you if it really will change anything about my workflow, or if it’s going to pretty much be email as usual. But I will update this post with thoughts after 1-3 weeks.
Summary
It really does feel different than other offerings.
$30 is a lot of money, so it better be a lot better.
Absolutely love the Vim-y feel to the interface.
Loved the true belief and conviction from the onboarding team.
I don’t love the sneaky lock-in techniques, but I understand them.
Ultimately, I think it’s worth trying out if you are willing to honestly try a better way of doing email.
But if you’re just looking for a better version of Spark, it’s probably not going to be worth $360/year.
See you in a bit for the update!
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
The Fundamental Differences Between Vim and Other Editors
I’ve been deep-diving on Vim lately, as I tend to every couple of years.
Check out my Vim 2019 Update.
In this rotation I’ve gone deeper than ever before—including going back to what makes Vim, well, Vim.
So this piece will capture as succinctly as possible what makes Vim different from other editors.
Emacs
Reminds me of Android actually.
Basically, the whole thing with Emacs is utter, complete, and absolute configurability. If you can think of it, you can have it.
That’s nice I guess, but as someone once said,
Thanks, I already have an operating system.
I don’t mean that in a purely dismissive way, even though it sounds like it. I get that it’s cool that Android and Emacs have ultimate configurability. I really do. I played in those worlds for some time myself, and it really can be enjoyable.
I just prefer an editor that can I don’t have to think about.
But what I came to realize is that configurability is inversely correlated with both intuitiveness and predictability, and I prefer those.
Vim’s intuitiveness and dependability comes from language legos
As it turns out, the reason Vim is so intuitive is because it works like a language. If you know English well, and you know how to say, “I want”, and you tend to like cookies, then you know how to say, “I want cookies.”
But if you later learn that you like cake as well, you don’t have to relearn a completely new phrase. Instead, you can just combine what you know, “I want”, with the new thing—“cake”.
That makes it so that you don’t actually have to remember that much once you know the keywords, which are:
There are others as well.
d: delete
c: change
y: yank
So those are basically verbs, and the nouns are equally intuitive:
w: word
s: sentence
p: paragraph
And then you have modifiers, like to t, and find f, which move up to and on top of the next instance of whatever you type next. So this would delete everything up to the next period (.).
dt.
Delete. To. Period.
That’s so easy to remember because we already know English, and Vim works in the same way! And the universal format looks like so:
Other editors—for whatever reason—don’t have this. They actually come up with largely independent commands for each thing, and they claim this is a strength because it’s infinitely configurable.
That’s cool. I get that. But the brain doesn’t have infinite recall, and you want your mind focused on your content—not on recalling a massive list of custom commands.
Bottom line here: Once you learn Vim you actually have far less to remember because you’re just connecting lego blocks that you already know from regular language.
Notes
I learned a lot of this over the years from a few great posts and videos. Here, Here, and Here.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
September 2, 2019
A Conversation with Ken Modeste

A while back I had the opportunity to chat with Ken Modeste, Director of Connected Technologies at UL, and I wanted to capture some of my takeaways from that conversation.
I had the conversation as part of the media at Blackhat 2018.
Here are some of the questions I asked:
What is the mission of UL at this point?
How does that relate to cyber?
How are you different from other organizations with similar charters?
Are you looking to do anything in the consumer space?
What projects are currently going on that you’re excited about?
First, let me say that I just thoroughly enjoyed speaking with Ken. It’s rare that I agree with someone so much on the topic of securing connected devices.
His big thing on the soul of the company was this:
We’re try to build foundations that can grow.”, which I think is exactly the right note to hit.
Ken Modeste, UL
Some of his other quotes:
You don’t wan to come up with a standard that’s 500 pages that becomes purely academic.
…and
Standards need have to have testable criteria.
…and he was quick to point out:
Test, not audit. You can audit an organization, and a process, but you can’t audit a product, you have have to validate and test the product.
Multiple areas within UL
One of the things we talked about was the structure of UL itself, where he explained there are several groups.
Finance
IT
CyberSecurity (Industrial, consumer)
ULCyber
UL CAP (cybersecurity cap)
The worst issues
I then asked Ken what he thought the worst issues were affecting connected devices, which I was curious about because I run the OWASP IoT Security project.
He gave a list that resonated quite strongly with me.
Weak or known credentials
Secure communication
No backdoors
Security configuration
He had an interesting point about this on Twitter as well, saying:
If you called these devices unsafe instead of insecure, you might have better results.
Takeaways
Ultimately what I like best about Ken is that he’s optimistic about the future.
He said that while there’s a propensity for nation states to cause some hiccups, he’s happy with how fast we seem to be adapting to problems.
He believes strongly that the best way forward is to link things to safety, because that’s something people understand.
As my final question I asked him how close are we to having a connected device safety rating on a product in the store?
He said that the problem with consumer goods is that people (companies) don’t want to cut into their small margin, and asked further if consumers would pay more for a 4 rating vs. a 3.
He prefers a binary approach to ratings instead, such as saying something more like, “X product is UL Approved”.
Don’t give the customer work, just tell them they can buy it or not.
100% agree on that, but I think there’s some room as well for a nutrition label, so maybe the answer is to have both.
Anyway, it was an enjoyable conversation with Ken, and I have honestly slept better knowing that people like him are spending their days working on this problem.
You can find Ken on LinkedIn, and on Twitter.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
Unsupervised Learning: No. 192 (Member Edition)

This is a Member-only episode. Members get the newsletter every week, and have access to the Member Portal with all existing Member content.
Non-members get every other episode.
or…
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
August 31, 2019
Day-1 Skills That Cybersecurity Hiring Managers Are Looking For

I’ve written before about the paradox of hiring managers not being able to find entry-level cybersecurity candidates, while many people with decent training or even degrees in the field cannot get hired.
As it turns out, it’s not really that hard to explain.
The Military takes you from zero to hero.
In extremely large and long-term-focused organizations—like the Military—this gap is understood, so they spend time building extensive, standardized programs that can take anyone off the street and turn them into professionals over time.
Most startups are just happy to be alive, and aren’t anywhere close to thinking about how to systematically grow security talent.
Some large companies do actually grow talent, but not enough.
In most companies—and especially startups—they don’t have programs that spin people up from nothing because they simply don’t have the time. They’re dealing with their own pressing problems, like trying to convince partners that they aren’t a complete dumpster fire (which they often are).
The result is that they need to hire people that already know how to do things.

The security engineer skills that managers need right now
This is a perfect example of when a hack is needed.
So here’s the secret that nobody’s talking about. It’s absolutely possible to hack your way into an entry-level position in security.
The trick is being able to convince the hiring manager—and their team—that you can do the tasks that they need most. Luckily, many of those tasks are somewhat standardized, and this article will take you through them.
If you’re on any security team at a junior to mid-level, these are exactly the types of things you’re likely to spend your first few years working on.
Technical skills

So many of these are a combination of soft and hard skills.
Product Selection:
Scenario: Your manager tells you that the CISO read about endpoint protection on the wall of an airport, so now we need to do that immediately, and it’s your job to find the best one.
Tasks:
Learn About The Space: Figure out who the main players are in the space, so you can understand what the capabilities are.
Determine Your Requirements: Untangle exactly what we need from an endpoint solution.
Create a Scorecard: Create a system for rating all selected products based on your criteria, with as little bias as possible.
Meet With Vendors: Get with vendors and learn about their products to see who you can eliminate quickly and who will be in your testing group.
Eliminate All But Your Top N Products: Using what you learn combined with your criteria, get your candidates down to 2-5 vendors.
Product Testing: Do the best testing you can on these products, in a fair way that represents how your company will use them.
Write Your Analysis: Create an artifact describing the selection and testing process, and which product was selected.
Present Your Findings: Depending on the company and the size of the project, you might have to present your artifact/analysis to various managers to move the project forward and get support.
More junior members of the team often do only one of these tasks.
This is really a full-stack kind of job because you have to make big decisions, organize your thoughts, come up with fair criteria, make sure you don’t miss things in your testing, and then make a compelling argument in your analysis and recommendation.
This is a great place for bug bounty folks to slide into a team’s DMs.

Ad-hoc Security Assessment:
Scenario: Your team has just learned that some website—which we just found out about—is about to go live tomorrow morning at 9AM. And it has not had a security review. Your manager calls you and tells you to take a look real quick to see if we need to spend political capital to have the site launch delayed.
Tasks:
Perform a Quick Web Security Assessment: Fire up Burp and/or any other commercial tools you might have and start manually testing the site for vulnerabilities. While you run some automated scanners using a set of test credentials, you also run through your manual testing methodology to look for P1 – P3 vulnerabilities.
Write Your Analysis: You found out that the site allows enumeration of usernames and passwords, and once logged in there’s an IDOR vulnerability that allows one customer to pivot to see other customers’ data. So you have to write this up in a 1-3 page report, with screenshots. And you have to do it in a clear-headed, matter-of-fact way that doesn’t aim to embarrass the team that built it.
Present Your Findings: After midnight there’s a call with the product team who built the app, and your manager asks you to explain why these things are bad, and why we can’t just launch the site and fix these later.
There are many types of security assessment, but the most common are tiny little risk assessments where you ask very simple questions like: Where’s the data, how does it travel, how is it stored, who has access to it, how is logging handled, is the system connected all the way through to incident response, etc.
You’ll basically be doing these assessments constantly, often multiple times per week—with each taking just a few minutes. Before long you’ll barely even know you’re doing it.
This one is one of the hardest to prepare for, since it’s strongly based on experience.
Preparing for and Handling an Audit:
Scenario: It’s Friday afternoon, and you just got told that Sarah, who normally handles all technical audit work, is out of the office next week unexpectedly for a death in the family. The auditors are onsite Monday morning at 8AM, and you need to 1) make sure all of our technical controls are in place, 2) be completely honest with them, and 3) they better not find anything—we’re depending on you.
Tasks:
Learn the Audit Standard: Very quickly spin up on what a SOC2 audit is.
Find Out Our Current State: Now that you know what they’ll be looking for (that took a bunch of Friday night and Saturday morning), now you have to figure out where they’ll be looking at our stuff, and what state it’s in.
Answer Questions About Our Controls: Be able to respond sensibly about how we are (or aren’t) meeting a particular standard that’s being asked about. The amount of wiggle room here is remarkably (and sadly) very large, and the more technical and smart you are the better shape you’ll be in. Honesty is rewarded by good auditors, and they often give time to make quick fixes before the audit is completed.
Create a List of Follow-ups: Take a list of findings from the auditor and go do all the relationship-straining leg-work to go get those things fixed throughout the entire company.
Follow-up with the Auditor: Come back to the auditor and show them (days or weeks later) that all the outstanding items have been addressed.
Dealing with auditors is a great example of the breadth of skills required to be a security engineer. When you’re handling an auditor you need to be extremely versed in many types of security, the controls that are involved, the reasons they’re asking their questions, and what exactly can be done to come to an arrangement regarding remediation.
Tech skills can really help here, but the best teacher is experience on this one as well.
Integrating a New Security Product:
Scenario: Your company just implemented a new NextGen CloudChainAI Firewall (Barracuda’s latest product), and your manager tells you to get it integrated with your (tee hee hee) centralized logging solution.
Tasks:
Talk to Your Logging People: Just kidding, that person is you also. But pretend it isn’t. Find out how they take in logs, over what protocol, how that delivery will be monitored, how to get an alert if logging stops, etc.
Determine What Events Should Be Alerts: Knowing what you know about the device, and the types of functions it performs, determine what types of issues we care about knowing immediately, that that must be monitored 24/7.
Find out How the Appliance Does Logging: Get credentials and go into the new device’s administrative interface, figure out where logging happens, and send the logs there. Configure or arrange those integrations with the appropriate folks in Incident Response.
Write Some Code To Integrate with The Appliance’s API: There’s also an API for pulling more detailed data, and you need to add that to the centralized metrics dashboard. So you write some Python and JavaScript, using its documentation, to use your keys, pull the API, and write to an internal web page.
The steps required to do this integration could be as simple as pointing logs, all the way to integrating with SOAR systems, talking to multiple teams for their touchpoints, etc.
This is where previous developers can prove their worth as junior team members.

Create a New Tool:
Scenario: Your group just got access to a new domain blacklist, and it has a pretty well-documented API. But now that makes 5 total blacklists your team is subscribed to. Your team lead asks you to create a single internal API that queries all of them, with extremely fast performance.
Tasks:
Create a New API: Create a new API using whatever language is used internally to aggregate all the existing APIs, search against them, and provide a YES/NO answer in less than 200 ms.
Create Documentation and Examples: Create documentation that includes how to call your new service in Go and in Python.
Note: Programming isn’t strictly required for all security positions, but for situations like we see above, it’s highly beneficial and preferred by managers.
Soft Skills

I’ve mentioned them multiple times already in the technical sections above, but being able to communicate is invaluable. There are many technical people who can implement or break their butts off, but they’re not desired on teams because they can’t interact with others.
You want to have both.
Here are the main soft skills you want to make sure you have.
Excellent Writing: I believe strong writing is the Uber-skill because clear writing requires clear thinking. The focus should be on being concise, and doing so with as little bias as possible.
Fast Learning: The best thing you can possibly say to a manager who asks you to do something you don’t know how to do yet is, “I can’t do that yet, but I should be able to within a day or two.” Those are true skills. Nobody can do everything. The question is how quickly you can jump into something new and become proficient.
Mentorship: In addition to being a great communicator and being quick to learn new skills, you’re also likely to be considered a better member of the team if you’re someone who lifts others and shares your knowledge. Don’t be the person who tries to make others depend on you so you’ll be more needed. It works in the short-term, but people eventually see it as selfishness and insecurity. Help others, and the Karma will return to you.
Summary
This summary has solidified for me why the skills gap exists. These tasks are not easy—even for someone who’s been in the field for 1-3 years. And that’s precisely why hiring managers keep passing up on lots of applicants.
You’re either able to do these kinds of tasks on your first Monday, or the team is likely to see you as a detractor rather than an asset. Because now they not only don’t have someone who can do the work, but you’re taking cycles away from someone else on the team to spin you up.
The key is to try to get as good at these things as possible before your interview.
Know the various product spaces, and the main players in those spaces. And be able to talk about how you might run a comparison between them.
Know how to quickly assess any type of system, whether it’s some financial system you’ve not yet seen the tech for, or a new security product that someone is deploying, or a website that’s about to go live. Know how to come up with a smart assessment methodology very quickly, and how to present findings in a concise and compelling way.
Know how to handle auditors—from being able to talk the tech with them, talk about the controls, and negotiate and follow through on negotiated remediations.
Get your programming skills to the point that you can hack together a quick client in Go or Python for accessing APIs, pulling data from a website, interacting with products, processing lots of text, and producing basic output. Few things (other than writing) will help you more in your career.
Sharpen your writing. Crisp and clear.
Be adaptable. Be the one who can take almost any task and learn it and execute.
Be the one with positive energy that is willing to help others.
The one thing to focus on
The one thing to focus on is convincing the hiring manager that you can be useful on day one. That’s it.
And learning to be good at the skills above, along with the ability to convey those through your LinkedIn, your projects, and your interview, is what’s going to make you stand out.
TL;DR: If you can convince the hiring manager that you can take projects within a week of starting, you’ve got a really high chance of getting an offer.
Notes
Top image from Crowdstrike.
There are other entry-level security positions, such as SOC analysts, that many companies definitely need. But those positions tend to be at larger organizations that have the infrastructure to take junior people and grow them, whereas this article is focused on what you can do to become a versatile member of a general security team in a smaller company where people are asked to do lots of things.
Michael Coates made the excellent point that a key reason for the skills gap is that not enough companies are doing what the Military is doing in growing talent. But in the startup world that’s completely understandable. Most startups are lucky to even have security people at all in a world where the entire company is still an experiment.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
August 29, 2019
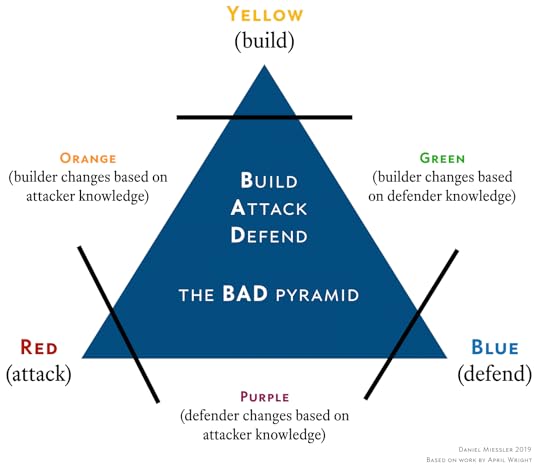
The Definition of a Green Team
As I talk about in my article on Red, Blue, and Purple Teams, there are many advocating for other team types beyond just those colors.
See my article on the different Security Assessment Types.
In April Wright’s work—who appears to have started the idea of these alternative team colors—the new ones look like this.
Yellow: Builder
Green: Builder learns from defender
Orange: Builder learns from attacker
Other groups have proposed a White team as being compliance and audit related.
The Green Team
The earlier in a term’s life the more drift you’re likely to have in its definition.
Here we’ll talk a bit about the concept of a Green Team, which according to my experience has a bit of a different meaning than the definition above. My best definition of a Green Team based on numerous conversations and a good amount of research is the following:
Green Team, infosec
An offensively-trained and defensively-focused security team dedicated to working with development and infrastructure groups to address issues discovered using offensive security techniques systemically and at scale across an organization.
See all my Information Security Articles
Note that this is not a baked definition, as the term is very new and has still yet to receive wide adoption. But taking that as a starting point, here’s how I break down the most important components:
The team has an adversarial/offensive security focus, meaning their discovery techniques come from Red Team and/or Pentesting mindsets.
Their mission is fixing things as efficiently as possible, across as much of the organization as possible.
Differences between Green and Red
Using this definition, the primary difference between Green and Red is that Red is focused on improving the Blue Team, meaning the company’s ability to detect and respond to the Red Team and real adversaries.
The Green Team, on the other hand, is focused on removing as many of the vulnerabilities and misconfigurations used by the Red Team as possible, and doing so as efficiently as possible across the entire organization. So they’re thinking about where the mistakes are being made at an organizational level, and they’re going to the source to work to change behavior.
Where the Red Team helps Blue to detect and respond, the Green Team uses those same skills to remove footholds for attackers across the company.
Examples of this would include things like working with the people who build new Linux images, or with cloud admins, or with app developers to make sure all these groups are doing things like using secure defaults, disabling older protocols, enabling logging, and doing anything else that reduces attack surface and removes footholds for attackers.
Team structures
If you think about it, Red and Green are quite similar in some ways. Both use the attacker mindset and highly manual techniques to do things that automated scanners miss when looking for vulnerabilities.
Additionally, both could potentially be broken into two phases of discovery and follow-up. In the case of Red, you first find issues by running your campaigns, and then you share that information with the Blue Team. With Green, you first find issues and you then go to the various organizations and work to address them at the most fundamental (build and configure) levels within the organization.
This potentially makes it possible to unify offensive discovery to some degree—or in some situations—and then break off into the separate learnings phases.
Summary
Red uses the offensive security mindset to discover issues that improve Blue.
Green uses the same techniques to fundamentally address the issues that allow Red to succeed.
Both have discovery and follow-up phases, which could potentially be combined in some ways in some organizations.
The Green moniker is still quite young and could either not survive or could evolve into a meaning not captured here.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
August 25, 2019
Unsupervised Learning: No. 191
.errordiv { padding:10px; margin:10px; border: 1px solid #555555;color: #000000;background-color: #f8f8f8; width:500px; }#advanced_iframe {visibility:visible;opacity:1;}#ai-layer-div-advanced_iframe p {height:100%;margin:0;padding:0}
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
Do Upper-middle Class Crime Victims Need to Check Their Privilege?

I was thinking the other day that complaining about being a crime victim in San Francisco is an act of privilege.
I’m not talking about crime against other people that are struggling here.
I don’t say that to complain about it, but rather to marvel at it. It’s not that I think it shouldn’t be true—it’s just that I’m so surprised that it is.
Think about this: if you’re doing well in San Francisco, working in tech or finance or whatever, and someone grabs your wife’s iPhone while she’s walking down Market street, or busts out your car’s windows so they can sleep (and urinate) in it, how does your complaint not include a classist element to it?
If you’ve been stolen from, it means you have something to steal. And if someone is desperate enough to break into a car to sleep or urinate, then the amount they improved their life should have massively outweighed the amount it inconvenienced yours.
Speaking of that, San Francisco just adopted new language guidelines that require convicted felons to be referred to as “returning residents”, and other euphemisms, because calling them felons is damaging to their character.
This got me thinking more about this violent conflict of intuitions.
Let’s say someone is sleeping at home and gets woken up in the middle of the night. Someone barges into their bedroom, hits them in the head with a baseball bat, knocks them out, and when they wake up their cash, their jewelry, and their video game console has been stolen from their house.
In one world, the person who broke in and assaulted someone would be a criminal, and worthy of scorn from the community.
But in another world—which I do not deny is real—that person is what San Francisco might call, a “Recipient of Negative Privilege”. In short, bad things happen to them due to other peoples’ privilege.
Why are they homeless? Because our government won’t educate and house people.
Why are they on drugs? Because our government won’t provide good jobs and mental health care facilities.
Why are they violent? Because we would rather build jails than schools.
These are all true things. The victim in this case is actually the attacker, because he’s the one with such a shit life that he has to break into peoples’ houses to get enough money to survive.
But at the same exact time—and equally true—we have the fact that personal responsibility (as illusory as it is at the level of biology and physics) must exist as a backstop for human civilization.
You can’t build a just society, where people treat each other well, if everyone believes that their choice to be a bad person can ultimately be blamed on someone else. It’s untenable.
This is the paradox that San Francisco—and the entire West—is stuck in today.
The world is unfair. Both advantages and disadvantages compound over time. And without extreme pressures (Piketty) such as war or disease, the results of those disparities will represent as growing education and wealth privileges over time.
Our challenge is to find a way to hold two opposing ideas in our collective minds simultaneously:
The world is unfairly scripted by nature and nurture, and becomes more unequal over time
For society to work, people must behave as if they have full moral responsibility for their actions
In the first case, we must be the external force that equalizes things—so that war and famine doesn’t have to. And in the second case, we have to maintain law and order so that the powerful, rich, and lucky don’t just build a wall between themselves and the Unfortunates.
As it turns out, it’s not just life that’s Absurd. It’s everything about our lives.
Our society is Absurd because Free Will is absurd.
The person who broke into your BMW to defecate could not—based on the laws of physics—have done otherwise—unless the universe were different at that exact moment. He had a bad set of variables, and you had a good set. Congratulations on picking your genes and your upbringing. And yet we must behave as if this guy had full control over the state of the universe.
The illusion is necessary.
Anyway, I think the approach by San Francisco is a mistake. For one, it’ll get Trump re-elected because it’ll force left-leaning people with cars full of poop to vote defensively. And second, the illusion of control is actual extremely empowering for people trying to improve themselves.
Because while it’s true that a given struggling person will either succeed at pulling out of their tailspin or not, we don’t know which it is. So we have to teach the illusion that it’s up to them to decide—that it’s all about personal responsibility and hard work—and then see if they can reach escape velocity.
That’s the only way out of any of this—for individuals, for cities, for countries, and for humanity in general.
We have to act as if it’s up to us to be better, and hold ourselves accountable.
—
Become a direct supporter of my content for less than a latte a month ($50/year) and get the Unsupervised Learning podcast and newsletter every week instead of just twice a month, plus access to the member portal that includes all member content.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers