Daniel Miessler's Blog, page 41
January 16, 2022
Your Value Comes From Your Output

work output miessler
I’m not sure who needs to hear this, so I’ll just put it here in hope it reaches someone who does.
Your value to most people in the greater uninterested world comes from your output.
Not your ideas. Not your talent. Not your potential. Your output. The fruits of your labor, not the labor itself.
Effort might be visible to those around you, but it’s not visible to the world. It’s is like a scream in space: you screamed, but nobody heard you.
I think about this a lot when I’m in self-reflection mode—a.k.a, beat-myself-up mode.
Where are my accomplishments? How often have I been on the Sam Harris podcast? How many entries does my work have on Wikipedia? How many patents do I have? How many books have I written? How many people read those books?
In short, what mark am I making in this world?
Those are the questions I ask myself, but that’s not quite the point of this. My bigger point is that you should never think that you deserve to be in any of those things if you haven’t done the work and produced tangible output from it.
Tangible output.
Sam (Harris) has people on his podcast all the time, and I consider it an ultimate honor to be asked onto that show. There are lots of bigger shows, with bigger audiences, but Sam picks his guests based on the impact they’re having on the world. He brings people on that he thinks are contributing to the world in a meaningful way.
When I’m measuring myself, and my work, and my actions, and my habits—I regularly think about what it would take to be invited onto that show. Or to have 10 entries in Wikipedia. Or to get more patents. Or to be asked onto Bill Maher.
Many B-level players in any field have this strange fascination with being part of the A-team. To be invited to their parties. To be on their shows. To be part of their elite group. Whether that’s in sports, or media, or business. And they use their considerable intellects to think about various ways they can convince the A-team to let them in.
Being smarter, funnier, better looking, etc.
Maybe if I did X instead of Y—then I would have been invited to be part of that group…
But it’s mostly bullshit.
What people either don’t know—or don’t want to accept—is that the way to get invited is by putting in the work on a valuable problem and having some success. You have to grind—often in complete silence and anonymity—for some period of time. Maybe weeks, maybe months, maybe decades.
And even then you might still never be noticed. You might still die in the squalor of invisibility. But at least you have a chance.
The short answer here is grinding. Finding an interesting problem, getting the proper training (or training yourself if your discipline will allow you to achieve recognition that way), and then working like Edison for as long as it takes.
That’s it. That’s the secret. Hard fucking work. Quiet work. Which results in actual benefit to the planet.
It’s not sufficient, but it is necessary.
Join the Unsupervised Learning CommunityI read 20+ hours a week and send the best stuff to ~50,000 people every Monday morning.So why am I writing this down? Because someone might need to hear it. When I figured it out it was a big revelation to me, and I want to pass it along to anyone who might benefit.
Don’t wish you were in the club. Don’t find ways to sneak in. Do the work required to be respected by the people who are already in. Do that work quietly. For its own sake. And forget about the club.
That’s the best possible way to get in.
Don’t tell painters you love their painting so you can be invited to paint with them. Just paint.Don’t tell hackers you love hacking. Just hack.Don’t tell thinkers you love thinking. Just think. And write down those thoughts.Don’t tell successful businesspeople that you love money and creativity. Start a business and make some money.To be respected as a dancer by dancers, you have to dance.
ActionSo what can you do about this if you’re not currently dancing?
If you’re someone who cares about being respected in some particular circle, I think there are two primary things you need to ask yourself:
Are you working on a question or a problem that is worthy of the field?Are you making consistent and valuable contributions towards answering that question?If you’re not working on a worthy question or problem, you should find one. And if you’re not doing good work towards a good question, you need to change that.
Within the context of this endeavor.
Avoid the allure of confusing effort or being busy with output. If you’re not making tangible contributions to this problem you’ve chosen, it’s nearly the same as doing nothing.
You must both be focused on the right thing, and be contributing meaningfully.
SummaryYour value to the people you respect is in the output you can produce within your field.If you want to be part of an elite group, as a peer, don’t waste your time trying to convince them of your worthiness.Instead, find a quality problem in that space and make a plan to produce meaningful results towards solving that problem.More than anything, the world judges people by their tangible output.NotesThere are sometimes exceptions where a trick or persistence combined with luck can get someone into an elite group, but the moment is usually fleeting if you don’t have what it takes to remain.There is a whole other dimension of reality in which I don’t agree at all with this post. Perhaps I’ll do a rebuttal post at some point and give that other perspective. Spoiler: friendship and kindness and love aren’t “outputs”, but they’re still worthy endeavors.Yes, I’ve read Ayn Rand, but not recently. And I don’t find her ideas about this type of thing all that compelling. But yes, I do see the similarities.Image by drawlab19.January 13, 2022
Gaming is Metaverse 1.0

People are hyped about the metaverse, and it’s honestly understandable. First, we’re going through some shit as a species right now. Social tension, the best part of Star Wars’ last three movies were the previews, and there’s a global pandemic. Part of this metaverse hype is just being excited to be excited, and I get it.
Metaverse lore has lots of fun stuff in it—from AR/VR to headsets to avatars to moving between worlds. But I think we can reduce the metaverse to one concept and two axes.
The metaverse is about experiencing a better life than in meatspace.Most important to this is content.Second most important to this is interface.ContentContent is life. It’s the source of meaning. It’s what gives provides us with evolution’s nectar of happiness in the form of hormone releases when we struggle and achieve something.
Throughout history we’ve had this naturally. Survival was hard. Mating was hard. Everything was hard. So you were rewarded by evolution with a squirt of happiness if you just survived.
But then you had to reproduce as well, and if you were able to find someone and make some babies, more squirts for you. You’re not dead, and you’ve passed on some genes. Evolution is happy with you, and you die a relatively happy person.
Then modernity comes and fucks everything up by making everything easy. There’s no faster way to create depression than to remove struggle and attainment.
With automation and AI, more and more humans are becoming what Yuval Harari calls the Useless Class. It’s not meant to be harsh. It just means there will soon be billions of poeple who can’t do anything better than a machine can do, and that’s a problem in our current society.
So. That brings us back to Content.
Gaming provides an escape from reality. For some it’s just a temporary distraction, like masturbation, or going for a walk, or watching a dumb TV show. But for people who are deeply unhappy, it’s more than a distraction: it’s an alternate existence that protects their defeated psyche from reality.
People need Life Loops that provide meaning. Their own version of rolling the boulder up the hill. And there’s a lot of research that shows that addiction isn’t a drug problem as much as it’s a lack of connection problem. A lack of meaningful Life Loops.
In short, if meatspace content sucks, people will look for alternative content. And that’s what gaming is to millions upon millions of people.
The content matters, though. People probably don’t lose as many marriages to Tetris as World of Warcraft, and that’s because of the attraction factor of the Life Loops that are offered.
Tetris has a loop of sorts. But it’s very short, and very shallow. It’s not overly life-like. It’s more like meditation or knitting.
World of Warcraft—and other games like it—have many aspects of real-life that people enjoy, and thus it’s easy for the brain (and evolution) to get confused about which life its supposed to reward with a squirt of happiness.
What’s more meaningful: your kid getting an A- in science, or you getting a new piece of epic gear and a promotion within your guild?
As I’ve said before, having alternate life loops can be problematic.
If you have no worthy struggles in your life, or no capability to rising up and achieving in the face of those struggles, you might opt for a place where you can grind and achieve.
So WoW is clearly better than Tetris in this regard, but it’s still nowhere near the pinnacle of the Content axis. Let’s think about what pinnacle content might look like.
Fortunately, it’s pretty easy to see what it’ll look like. All we have to do is look at the best and most popular books, manga, and movies.
Find the protagonist in those stories, whether it’s epic fantasy or romantic erotic novels, and then imagine an AI-generated game in which you’re the main character.
You get bullied some. You have some bad times. But you develop a special gift. Most people don’t know you have it, but it comes out some times, and you hide it from everyone. Except maybe your best friend.
And there’s a love interest. Or a dark potential lover that’s unattainable and dangerous, but who’s somehow taken an interest in you. Or a threat arises that only you can face, using these new powers, that very few people know you have.
But here’s the thing: it’s not the same experience, playing this game, for you and for someone else. No. All the characters are different. They look different. Different voices. Different quirks. Both good guys and bad guys and extras. Even the plot changes from player to player and instance vs. instance. That’s the power of AI.
Watch Total Recall if you haven’t.
So, what we’ll have is deep and meaningful games, largely generated by AI, with tons of customization and tweaking options, that could take weeks or months—or even years—to develop and climax.
So in meatspace you work at the Amazon factory training Bingo the robot how to do your box-stacking job, but you don’t care because in reality you’re Tristian the Bastard Sword Weilding Slayer of Dragons. And you have a deep mission to defend a town that you’ve spent years protecting and growing and nurturing. Plus a woman you’re in love with, who is technically an AI but you don’t even care anymore.
That’s Content. This is not fiction, this is inevitability. This is where all gaming is going.
This is true not only because it’ll develop naturally as an evolution of gaming, but because governments will realize the only way to pacify billions of people is by providing them a Life Loop that doesn’t involve revolution. So the militaries around the world will pay the gaming companies to make better and better stuff.
InterfaceNow let’s talk about the interface into these worlds. With Pong, or Tetris, or whatever Gen-1 game, it was barely even life-like. But it was enough to pretend with an active imagination.
You’re touching some sort of physical interface, just with your hands, and pressing some sort of buttons. Good. Fair enough. It gets it done.
As we move ahead a few decades, we can now sit in a wonderful chair, look at life-like and beautiful graphics on giant displays, and hear everything in sound from every angle.
Join the Unsupervised Learning CommunityI read 20+ hours a week and send the best stuff to ~50,000 people every Monday morning.That’s a huge jump, but you’re still looking at a flat screen, and you’re still mashing buttons. One of the biggest transitions of interface will be moving from mashing buttons that are shortcuts to physical action to performing some emulation of that physical action. For example: swinging down with your arm to forge a sword in the game.
We saw this in Ready Player One, and we see some of it already in current AR/VR games like Beat Saber. The better the interfaces get, the more realistic all those interactions will be, with you actually doing them—either with your body or your brain.
The next level of this will be what we already know is coming from multiple companies. Meta. Apple. MagicLeap. All these companies are supposedly working on headsets that will make these gaming experiences more realistic. And that means from a visual and sound perspective, but also from an action perspective.
Again, think Beat Saber. That’s the way you’ll be doing sword fights before too long.
The endgame there is what Elon is working on with Neuralink. Who knows if he’ll land it or not, but we do know it’ll eventually land. And that’s the ultimate interface because then there’s no difference at all between thinking about doing it and doing it.
Thought becomes the action. And that action gets translated in both directions back to the brain and back to the game. That means you get to feel pain, and anger, and lust, and sex, and fighting, and jumping out of a plane, and all the different things you can do in meatspace. But better.
Maybe there will be a whole set of intermediary steps between headsets and brain interfaces, like the sensory suits we see in lots of films, but I think we might just skip those. There’s a chance we’ll just move from better and better headsets, skip the suits, and go right to brain interfaces.
But who knows.
Content + Interface

However we get there, and however fast, our inevitable motion as a species is upwards and to the right on this graphic.
The content will be highly randomized, highly customized just for the player, and so meaningfully deep and rewarding that it’ll be better than anything you can imagine in life. It’s hard to compete with being Superman and saving the world and winning the girl, over the course of multiple years of deeply meaningful game time.
It’ll be even more engaging when it’s beamed right into your brain.
It’s especially hard to do that when it was all experienced through a headset you can wear for 12-hours straight, and that projects a visual and sound field that feels nearly realistic, and which allows you to move and jump and kick and thrust (swords, settle down) like real life. When you get done with a 10-hour session and you’re sore and sweaty, that’s going to be a boon for human health. Physical at least.
EscapeDespite what Pinker says, life is getting harder for humans, not easier. Or said another way, it’s getting easier which is making it unbearable.
As normal people continue to be crushed by the banality of meatspace, stripped of opportunities for worthwhile struggle and attainment, more and more of them will abandon it for something better.
There are now over 3 billion active gamers in the world.
Gaming is not fundamentally different than the metaverse; it’s just less-evolved in content and interface. It’s just an earlier version.
Gaming is Metaverse 1.0.
January 10, 2022
News & Analysis | No. 313
A North Korean cyberespionage group called Konni has been linked to attacks on the Russian Federation’s Ministry of Foreign Affairs. These attacks started with credential stuffing and then loading malware to steal intelligence. More
Venture funding in the cybersecurity space crossed $20 billion in 2021, and the last quarter set a new quarterly record of $7.8 billion. More
Part of the Pegasus spyware package has been uploaded by a security researcher to Github. More
QNAP has warned its users to get its NAS devices off the internet, and it’s given instructions on how to do so. This comes after months of repeated vulnerabilities affecting the devices. More
SSH 8.9 will include agent restriction, which will have two main functions: “a safe runtime store for unwrapped private keys, removing the need to enter a passphrase for each use, and a way to forward access to private keys to remote hosts, without exposing the private keys themselves.” More
The US military is working hard to counter the threat posed by hobbyist-level drones. The problem is that they’re both small and cheap, and you can strap explosives to them. Possible solutions range from lasers to microwave blasts. More
Vulnerabilities: VMware has patched a bug affecting ESXi, Workstation, and Fusion | System Takeover More WordPress has been updated to address multiple vulnerabilities | DoS MoreIncidents: The New York State Office of the Attorney General has warned 17 companies that 1.1 million customers have had their accounts compromised using credential stuffing. MoreCompanies: Google has purchased Siemplify—a late-stage Israeli company in the SOAR space—for around $500 million. More
TECHNOLOGY NEWSApple has become the first company to hit $3 trillion dollars in market cap. It was also the first to hit $2 trillion, and if it has any success with a rumored headset and car, it’ll probably be the first to $4 trillion. I attribute a lot of this to Tim Cook and his expertise in managing a supply chain. More
GameStop is getting into NFTs. More
Blackberry devices stopped working on January 4th. For real this time. More
OpenSea, the largest NFT trading website, is now valued at $13 billion dollars. More
Twitter is rolling out a new test feature where people do video reactions to tweets, like TikTok. More
It’s been 15 years since Steve Jobs revealed the iPhone. I remember where I was that day, and what I was doing. It was a big day for me, and it lead to me becoming an Apple person when I was not at all before. More
HUMAN NEWSA record 4.5 million Americans quit their jobs in November. The number of open positions fell from 11.1 million to 10.6 million in October. More
Between 2009 and 2018, the proportion of adolescents reporting having no sexual activity (including masturbation) rose from 29% to 44% among men, and from 50% to 74% for women. More
The Mayo Clinic fired 700 unvaccinated employees due to noncompliance with vaccination policy, which is around 1% of its workforce. More
A nasal spray that prevents dementia is moving into human trials. It combines an antibiotic and resveratrol to combat plaques in the brain that are known to be associated with cognitive decline. More
1 out of every 153 American workers works for Amazon. More
CONTENT, IDEAS & ANALYSIS
The Unsupervised Learning Everyday Carry — Many have asked what my EDC is, i.e., what tools and gadgets I keep on my person and use every day. This member-only post answers that question and goes into why I use each item. More
Mentor vs. Nemesis — I enjoyed this piece on how many great people weren’t encouraged by mentors as much as they were energized by a nemesis. I see this dynamic a lot in life, where there is a health tension and competition between friends and peers in a particular space. The bug bounty space is a great example, where you have a lot of very smart hackers and creators putting out content. They’re friends, but they’re also competing. And some of them have one or more nemesis’ that drive them to be better. I’m not sure the right balance of positive and negative—of push and pull—but I do think that it’s natural to be driven by negative competition. I personally use a different tactic, which is competing with the best in the world, including people who are dead, and demanding that I get to that level.
I vs. T-shaped People: Which Are Better For Which Jobs? — This was an interesting piece and discussion on Hacker News about someone who typically looks for I-shaped people (narrow and deep) vs. T-shaped people (broad and shallow), but who also happened to notice that most of their best projects had a good mix of both. I tend to look for people who are unicorns in this way: being mostly T, but with one or two I-like areas.
NOTESNot sure who’ll notice, but I simplified the newsletter design for this episode, especially around the header. If you noticed and cared, let me know what you think.
We had a great UL Book Club today discussing Good Strategy, Bad Strategy. The next book has been chosen and we even have the next couple picked out after that. Great discussion today, and can’t wait for the next one!
I continue to struggle with blatant plagiarism of my content online and am looking for a solution to it. If you all know of anything, please let me know. More SPONSORED DISCOVERY
PlexTrac: The Purple Teaming Platform
PlexTrac is the premier cybersecurity reporting and workflow management platform. With PlexTrac, security service providers and teams of all sizes can cut report writing time in half, streamline workflows, improve collaboration and communication, and gain a real-time view of their security posture.
Head over to PlexTrac.com/UnsupervisedLearning to download our Writing a Killer Pentest Report white paper to learn how PlexTrac helps cybersecurity practitioners produce quality work faster so they can focus on winning the right battles Download the Whitepaper
DISCOVERYI just bought a couple of these masks, which came highly recommended by Clive Thompson. We’ll see how they do I’ll report back. More
My Personal Notetaking Journey More
The Rise of Performative Work — “It’s not what you do. It’s how ostentatiously you do it.” More
Ethereum’s Reference on Smart Contract Security More
AI is Eating The World’s Workforce With Job Automation More
6 Ways to Delete Yourself From the Internet More
GovInfo RSS Feeds — A massive list of RSS feeds that let you track what the government is doing, from bills to budgets to congressional committee meetings, and more. More
The Wall — Near-real-time animations of geostationary satellites. More
Keyboard Drill — An elegant website that helps you learn to type faster. You give it a target WPM, and it drills you until you get that fast on various words. More
ffuf — My favorite web fuzzer, which is written in Go. More
nuclei — The future of vulnerability scanning (in my opinion). It’s YAML-based signatures for finding issues across multiple protocols. More
nuclei templates — A repository of check types that can be used with Nuclei. More
A TomNomNom Recon Tools Primer — A previous post of mine going over my favorite recon tools from @TomNomNom. More
RECOMMENDATIONSpend this time in January to lock in a solid daily routine. As James Clear says in Atomic Habits. We don’t rise to the level of our goals; we fall to the level of our systems. That means you need a good system. This is mine, which I spent like a week researching and writing during the holiday break. But it doesn’t matter so much which one you use. It matters more that you actually have one, and that you use it rather than relying on luck or hope. Find an algorithm that will get you to where you want to be, and follow it.
APHORISM“The three most harmful addictions are heroin, carbohydrates, and a monthly salary.”
— Nasim Taleb
January 9, 2022
The Unsupervised Learning EDC Setup
January 2, 2022
News & Analysis | No. 312
December 29, 2021
Losers Exist, Don’t Hire Them

This is an internet re-post of a piece by Bryan Goldberg that is no longer available online.
–
by Bryan Goldberg
About a year ago, my sales operations team needed to hire an Account Manager. We had a handful of candidates in the interview pipeline, but one of them had far more relevant experiences than the others. So we interviewed him first, in hopes that it might save us a bunch of time.
He passed the first wave of the gauntlet, earning positive marks from a Director in our group, and he was also well-reviewed by the peers who he would be working alongside. “He’s been doing this for five or six years, and he can definitely achieve what we need from him,” was the consensus.
But then it was time for him to interview with me. I didn’t ask him very many questions about sales, advertising operations, invoicing, collections, or any of the handful of other tactical skills we wanted. I just grilled him on the bottom fourth of his resume — you know, the one about hobbies and college.
And when I asked him about his BA in English, which he had earned about five years earlier, he got nervous. “What was your favorite century of English literature,” I asked. But he hadn’t really focused on any particular era. Nor did he have an opinion.
“Did you have a particular affinity for poetry, drama, old novels?” He punted on that one too.
“Well, what was your favorite book? Or your favorite author?” He stared at me somewhat blankly.
“Oh, well, there were a bunch. None that really jump out at me right now. It was kind of a long time ago, you know? My memory is a bit hazy,” he said with a chuckle, before talking about how fun college was. I laughed politely, wrapped up the interview in 15 minutes, and informed the team that we would not be hiring this candidate.
Many fine professors and senior executives have written books about team-building and how to be a great manager. At some point, I will write about this meaty topic for PandoDaily. But here’s an amuse bouche until then:
Don’t hire losers.
They might be able to do the job for which they are hired. But that is not good enough. Especially at a startup where you are able to hire a lot fewer people than you would like.
As it turned out, we eventually did find someone for that position, with a lot less relevant experience. But she learned the job in about six weeks, and her upside enabled her to take on a lot of the unforeseen — and valuable — tasks that the previous candidate would have stumbled around.
And the good news is that it’s really easy to detect losers. Here are some things you can ask a potential candidate to find out:
“Tell me about what you studied in college, and what were some of your favorite classes?” A person who spent $120,000 and dedicated four years of their lives to any pursuit better be able to speak eloquently for five minutes on that humongous experience. Or else they are a loser.
“Tell me about your hobbies…” A person who has no hobbies, and can’t even exaggerate one, almost certainly lacks the ambition to make your company valuable. They are probably a loser.
“So, what do you think about our website?” If the applicant hasn’t performed even the most basic due diligence in preparation for the interview, then they have no common sense. And if they are too weak to offer an opinion on a matter, that is a huge negative. There’s a Smash Mouth song about people like that.
“Which of your previous jobs did you enjoy the most?” Applicants screw up this question so often, you’d think that you were quizzing them on Fermat’s Last Theorem. How can you know if they are a fit for your work environment, when they can’t even tell you about a work environment that appeals to them? There’s a Beck song about people like that.
These sorts of questions are great, because they can help identify winners even amongst the nervous, “I don’t interview well” types of people who may warm up and shine on the job. And I’ve hired a lot of great people who don’t interview especially well. But when I jump into the above questions, they are able to speak eloquently to how dynamic and thoughtful they are as people.
Lesser managers will try to stump candidates with horrible brain teasers along the lines of “Describe a time you got into a bad situation and resolved it effectively?” — or crap like that. Those questions are not necessary. All you will do is filter out some good people who have not yet mastered the art of the interview.
But if a candidate can’t even tell you why they liked their last job, or what they got out of their college experience, or any of the million other questions that speak to their basic humanness… Then no amount of experience will make them valuable.
They are losers. They are out there. And you should not hire them.
–
NotesIf Bryan Goldberg ever brings this post back online at a new site, I will remove this version.Image by Hallie Bateman.December 28, 2021
My Predictions for Crypto

First off, nobody has any idea what’s going to happen. Let’s be clear about that. These are musings—nothing more.
I see the current crypto hype as three distinct phenomena—with descending levels of longevity.
The IdeasThe TechThe HypeThe ideasI think the ideas are most likely to survive for decades, which are:
A digital replacement for reality where the other 80% can find meaning away from meatspace (metaverse)A shared, decentralized computer (Ethereum/et al)Removing the middleman (de-$FOO)Decentralized finance (defi)Smart contracts Digital validation of ownership (NFTs)Decentralized and autonomous organizations (DAOs)The techThe next most fragile in this list is the technology itself. So, blockchains. Bitcoin. Ethereum. NFTs built on top of current blockchains. Etc.
There’s no way to know if the current iteration is stable, or if it’ll completely fail in a few months/years, cause a new Dark Ages for these ideas, and be resurrected in 5-20 years when the tech or society is ready.
Many of the ideas above can be implemented using existing, non-crypto technologies, so there’s no reason to assume that crypto is an inevitability.
The hypeThe most fragile of all these is the hype, which is not sustainable. The number of companies being formed right now that are raising billions of dollars in “value”—all based on mania and FOMO—is completely insane.
There’s no way the top of this doesn’t blow or slide off within 1-3 years. Even if this first iteration IS THE ONE, we’d still see consolidation at the top that removes 60-95% of the players from the board.
The predictionsThere are obviously more than two options.
OPTION 1 — We get it right the first time with Bitcoin/Ethereum, and society is reshaped in the image of decentralization, smart contracts, and digital ownership. Many lucky entrepreneurs become owners of billion and trillion-dollar companies in the course of the next 10 years. Massive consolidation happens, and something like 2-5% of the coins/chains survive.
OPTION 2 — The whole thing fizzles out in the next several months to a couple of years. Either regulation, performance issues, or vulnerabilities basically kill off Bitcoin and Ethereum, and they take down the entire ecosystem with it. It’ll be like the AI Winter of the 1970’s, except for crypto. But the ideas above survive, and they start getting implemented in 5-10 years using traditional, non-crypto-based technologies. Somewhere around 10 years later another hype cycle may start around crypto, depending on how successful the implementation of the ideas was using non-crypto tech.
I’m personally betting on #1, but I’d not be surprised at all if #2 happened.
The only thing I’m highly convinced of is that the Ideas will not die. I believe they’ll keep re-emerging as themes regardless of whether they’re implemented using crypto or traditional technology.
A Correction is Coming, and That’s Ok

People have been talking about a stock market crash correction for years now, and for good reason. We’ve seen massive growth for years that’s usually followed up by a drop (see above).
But I’m tracking another narrative that’s pretty damn compelling—namely the narrative of “So what?” If you draw a line through that graph—including all the crashes—it’s absolutely heading upwards.
Simple doesn’t always mean right.
So my read on this is pretty simple: Yes, we might have a correction soon, in fact we should expect one. But that doesn’t mean you shouldn’t be in stocks.
The only question is how long you plan to be in the game.
If you are trying some sort of scheme to get rich quickly, with this stock or that stock, yes—you might get burned by a correction. But if you’re buying solid stocks, or index funds, and you plan on holding them for 10, 20, or 30 years, I think the data shows you’re pretty safe.
We’ve seen lots of market crashes, but not a single one that wasn’t followed by stocks hitting new highs.
Now keep in mind—this doesn’t account for a total collapse of the economy, or the downfall of the United States, or the end of civilization. There are no guarantees that past trends will continue.
My only point here is to not be overly concerned about the trend of corrections, becase that trend sits within the trend of recoveries that take stocks even higher.
SummaryPeople think we’re likely to see a correction in stocks soon.The data show that this is likely, although nobody knows when it will be.Some think this is a reason to avoid stocks.I and others think a correction is not only likely, but virtually guaranteed, and that this is only scary if you are working some sort of short-term scheme.If you are investing in the stock market longterm, using strong stocks and/or index funds, you will likely survive this coming dip to see the other side.What to Do Instead of New Years Resolutions

I’ve been anti-new-years-resolutions for a while now.
My reason is simple: I don’t like gimmicks. And that’s what most resolutions are. They’re nice stories that people tell themselves about how they’ll be better next year.
Here’s the simple truth about these types of resolutions: If you had the ability to eat less, or exercise more, you wouldn’t wait until the end of December to make those changes. Anyone capable of such discipline would make the change immediately—not at the end of the year.
But it’s not all bad news for next-year planning. I think there are a few tasks that fit well with an annual cadence, and you might as well get them done between December 15th and January 1st when you have some downtime to reflect.
My annual life optimizationsYou don’t rise to the level of your goals; you fall to the level of your systems.
James Clear
This isn’t the same as buying a gym membership; it’s a commitment to a schedule.
Optimize your daily routine and commit to staying with it. I just redid mine and published it here.Make sure your life is backed up, and that you have functioning auto-backups in place.Get to a zero inbox. I use Superhuman, so that includes all Starred email too.Make a list of the people you should be interacting with regularly in the coming year. This means taking people off the list and adding others. The criteria will be different for everyone, but I recommend something like the following:It’s harsh, but in order to be great you need to limit the type of energy you’re absorbing from the people in your life.
Drop people who are negative or toxic, and who are unwilling to put in the work to improve themselves. Add a few people who work harder than you and/or have some measure of success that you wish to achieve.Add a few people who are up-and-coming grinders who could benefit from your position and knowledge.So, cut the negative people, find some people who push you, and find some people to help on their journeys.
This is my longer list.
Review your evergreen books. Bring up your most important books, or at least your favorite passages from them, and re-absorb them. Mine short(er) list of favorites includes:Atomic HabitsMeditationsNever Split the DifferenceA Guide to the Good LifeThe Evolution of EverythingI don’t generally have time to re-read all of my favorites, but I use Kindle Highlights (and now Readwise) to review my favorite snippets. If you don’t have your books marked up in this way, take this opportunity to do that.
SummaryResolutions are fantasies.Use the time to perform annual tune-ups on your systems instead.Update your daily routine with what you’ve learned in the last year.Make sure your most important text, documents, and images are backed up properly, with automation.Manicure the list of who you’re going to associate with this coming year.Re-consume and re-process your favorite wisdom from your favorite books.I hope you have a wonderful 2022.
NotesMake sure your routine includes regular pings to people you care about tell them that they’re awesome, and that you care about them.December 22, 2021
Comparing My Top Four Security Podcasts/Newsletters
I get asked a lot what my go-tos are for security content. My top four recommendations are Darknet Diaries, Risky Business, Unsupervised Learning (yes, my own show), and TL;DRSec.
As for including my own show, I’m too old and well-read for false humility or arrogance.
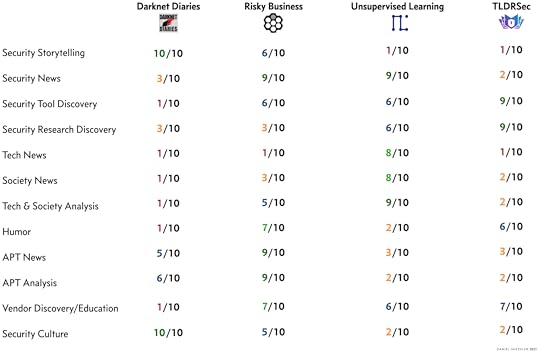
What’s so interesting about these four is how different they are. I did this analysis so I could capture what I cared about and how each of them provides those items in different amounts—which allows me to make better recommendations to people.
Here’s my analysis and summary.
Show identityDarknet Diaries is, first and foremost, a storytelling podcast. It is, without question, the best produced and executed podcast in security, and arguably anywhere. It has the quality level of a professional podcast series put out by NPR or the New York Times. But it isn’t just production quality—it’s the quality combined with the content. Jack dives deep into fascinating stories and topics like a combination of Columbo and Malcolm Gladwell, pulling threads and peeling layers and describing the process as he goes. This podcast should have a warning label for anyone doing any other profession when they start listening, because a few episodes of this show might make them want to start a career in security.Risky Business is a security and hacking news show, with a secondary note of vendor exposure and education. Patrick applies his journalism background to cover security stories in an entertaining way, especially when he’s accompanied by his regular partner, Adam Boileau, who is a professional penetration tester. Patrick is from Australia and Adam is from New Zealand, so they’re both cheeky, which keeps their rendition of security news not just informative but also entertaining. They also have regular interviews with interesting people, and have sponsor slots that expose the audience to new security companies and their tools. Risky Business is—at least in my circles—the most known and most popular security news podcast.Unsupervised Learning is a show that explores the patterns in security, tech, and society. My primary emphasis for this show is efficiency, i.e., giving people as much quality information and ideas as possible in the shortest amount of time. The broader scope of the show is polarizing because it’s not a pure security show, or a pure tech show, or a pure show about society. Patrick from Risky Business once told me it was a “thinking podcast”, which I’ll happily accept. Think of it as a zoomed-out view of what’s happening in security, tech, and society—combined with analysis, original thinking, and a Discovery section that lists the best stuff I’ve found in my reading from the last week.TL;DRSec is a newsletter centered around security research. Clint applies his academic background (he actually has a Ph.D. but never mentions it), to find and summarize the best security tools and presentations. Many newsletters have sections for tools, including my own, but Clint’s is the best because it’s his entire focus. Many of the tools he covers are centered around cloud security, but he often has sections for network security, mobile security, and many other areas. As I’ve said before, Clint’s is the one security newsletter that I will not skip a week on, and will not stop until I’ve read the entire thing. I open more links in his newsletter than for any other.AnalysisSo, since this is all about recommendations, let’s look at the attribute breakdown and see what we can learn.
One thing that jumped out at me was that Darknet Diaries had really low scores in a lot of areas I care about, but it was the only show with 10s. And it had two of them. I like this. It means it knows what it is and it leans heavily into that. Like I said, if you’re up for being entertained and educated about the world of hacking, there is simply nothing better.Coming less from the scorecard, I’ve found there are generally two types of people when it comes to podcasts: people who need to be entertained to listen, and people who are simply searching for nuggets they can use elsewhere. I am in the second category, which is why I built a show around that. But if you’re looking for humor and entertainment, I’d say you should move towards Risky Business and avoid Unsupervised Learning. And if you’re looking for a super-efficient (but somewhat antiseptic) injection of content/ideas, I’d say go with UL. Note that TL;DRSec doesn’t have a podcast, so it’s not really rated on this count.One thing that Risky Business has that Unsupervised Learning and TLDRSec doesn’t have, is a strong sense of attacker activity. With Patrick’s curiosity and Adam’s pentesting focus, they aren’t just talking about what happened but they also focus on linking the activity to a given threat actor, and mentioning other attacks they’ve been associated with. If you like being up to speed on what the bad guys are doing, from a security news perspective, Risky Business definitely has that covered. Darknet Diaries does that as well, but at a much narrower scope and in much more depth. Unsupervised Learning, over the course of a year, ends up being less like a security show and more like a thinking and analysis show from the perspective of a security professional. Like I said, that’s either good or bad, depending on what you’re looking for. The show attempts to give not just the stories and the details, but the context and patterns and impact that they have on our lives. That’s the goal anyway.TL;DRSec is highly focused on exposure to great research and does a really good job of highlighting the people behind that work. Clint is an extremely kind and positive person, and it shows in his newsletter. He is constantly lifting people up, exposing their work to people who might be interested, and making connections people with similar interests. You can think of Clint as a security research maven who is the most aware person out there of what people are working on. Combine that with his own technical expertise and you have a brilliant guy and a wonderful newsletter.SummaryThese are my top four recommendations for people to read or listen to within security.They are very different.Darknet diaries you have to listen to regardless. End of story.Listen to/read Risky Business if you like Aussy/Kiwi snark combined with in-depth coverage of attacker groups.Listen to/read Unsupervised Learning if you want security news combined with context, ideas, and analysis of how it impacts us as humans.Read TLDRSec if you want the best exposure to the best security research, delivered in a positive and uplifting way.I hope this helps you.
NotesThe original version of this piece had Adam as Australian. Apologies.Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers