Daniel Miessler's Blog, page 37
April 11, 2022
News & Analysis | NO. 326
April 4, 2022
News & Analysis | NO. 325
Apple released fixes for two zero-days affecting Macs, iPhones, and iPads. They are critical CVEs that lead to code execution with kernel privileges. Update your devices immediately. More
There’s a critical RCE zero-day in the Java Spring Framework that can result in the complete takeover of a targeted system. Patch immediately. More Sponsor
Vanta — Making Security Compliance Easier to Manage
There are so many compliance platforms on the market, yet not all are created equal. As the leader in compliance automation, we know exactly what features to look for when choosing an automated platform.
We’ve compiled a list of the biggest differentiators to check for – and we explain how each feature works in order to make your job more efficient as you go through the compliance process. Check out our guide to the 5 must-haves in an automated security platform. Download Vanta’s 5 Compliance Must-Haves There’s also a critical RCE in Sophos Firewall which allows you to execute arbitrary code on the firewall. Sophos saw a few companies in South Asia being targeted with this attack and let them know directly. More
Ukraine’s Defense Ministry’s Directorate of Intelligence leaked personal data for 620 alleged Rusian FSB agents.
A leak from a Russian food delivery app (Yandex Food) shows the dining habits of Russia’s secret police. Yandex said the leak came from an internal employee and includes data on around 58,000 users. Bellingcat got a hold of the leaked data and was able to find GRU phone numbers, other officials associated with the Russian government, and then further link that data to addresses that confirmed their identities. More
Anonymous says they’ve leaked 15 GB of data on the Russian Orthodox Church’s charitable wing. More
TECHNOLOGY NEWSThe train system in the Netherlands had an IT outage which shut down the entire train system. “It is unfortunately not possible to run any trains today.” More | More
HUMAN NEWSThe US economy added 431,000 jobs in March, bringing the unemployment rate down to 3.6%. More
It looks like the supply chain issues might get a lot worse. Before it was Covid, and now it’s another outbreak in China combined with the war in Ukraine. More than a million containers used to go from Europe to China by train through Russia, and now they’re being rerouted by sea, and over 120 container vessels are stuck in Shanghai due to Covid. Everstream Analytics says these events will have effects similar to the Suez Canal blockage problem in 2021. More
Hubble found the most distant star ever seen at 12.9 billion light-years away, and it’s been named Earendel (from Tolkein). It’s at least 50 times the mass of the sun and at least a million times brighter. The coolest part of this is that we wouldn’t have been able to see it at all if it weren’t for a massive galaxy cluster that served as a gravity-based magnifying glass. More | Video
The human genome has now been mapped completely. You might have thought we did that already, but the last 8% or so took a very long time. A lot of that was what was called Junk DNA comprised of 151 base pairs of sequence data. More
A new study in Nature shows that Covid spike proteins create cognitive decline and anxiety in mice. More
In a new study in The New England Journal of Medicine, and the largest study of its kind, Ivermectin has been shown to be completely ineffective against Covid. More
CONTENT, IDEAS & ANALYSIS
A Custom Contact Sharing System — I created a custom personal contact sharing system for giving out my phone number, email address, and contact photo via vCard when I meet someone new. More
My Gaming Idea (2006) — I just remembered a gaming idea I had back in 2006 that reminds me a lot of what we’re now calling metaverse. It’s a pretty fun read. It also reminded me that I printed out multiple copies of this post and mailed it to my friends as copyright. Hilarious. More
Thinking About the Future of InfoSec (v2022) — A look at how I see InfoSec unfolding in coming decades, broken down by org structure, technology, regulation, insurance, automation/AI, and other factors. More
NOTESI’m psyched about these new Schlage smart door locks. They’re one of the first locks that use the Home Key feature within the Apple ecosystem, which is NFC-based lock functionality. So you can walk up to your lock and just swipe with your phone or your watch—even without re-authenticating to the phone (if you have Express mode enabled). More
Good News: My podcast surpassed 1 million downloads! Bad News: Those are my all-time stats, not my monthly stats like Making Sense and My First Million. More
DISCOVERYA Collection of Pentest Contracts and NDAs for Freelancers More
The Secrets of Lasting Friendships More
The Jokes That Have Made People Laugh for Thousands of Years More
“I would like to be paid like a plumber.” More
Learn About Concept Maps — This is what I’ve been looking to do with my Concepts page forever, and it’s the reason I’m so excited about moving my PKM to Obsidian. More
The Ultimate Personal Security Checklist More
The Tech Interview Prep Industry More
Dual 75″ 4K TV Floor Computing More
[ RECON ] ReconFTW — A recon automation system that focuses heavily on subdomain enumeration before heading into vulnerability assessment. More
[ CI/CD ] Dagger — A Lego-like DevKit for building powerful, repeatable, and portable CI/CD pipelines. More | Project
RECOMMENDATIONIf you’ve ever thought about getting into Solar for your house, now might be the time. I recently priced 4.8kWh worth of solar panels, plus a Tesla Powerwall battery, at around $21,000. Depending on your house (and how much sun you get) that can get you between 50% and 100% of your daily energy use, and massively reduce your reliance on the grid. I think the over-time savings element is less of a sell because it’ll take a while to earn that back in energy usage. My big thing is peace of mind against outages combined with adding to the resale value of the home. I have 18 Sunpower panels and 2 Tesla batteries and couldn’t recommend them more.
APHORISM“History is the discovering of the principles of human nature.”
— David Hume
No related posts.
April 3, 2022
My Custom Contact Sharing Solution

I’ve been excited recently about the prospect of attending some cons this summer. One of the things that sucks most about cons, or about meeting new people in general, is sharing information with them.
Paper cards are kind of done. And while there a ton of apps for doing contact sharing, they all require you to sign up for some third party. So even if there’s some cool QR Code functionality going on, all those QR Code scans and profile updates are going through their server. Or you could do the hand-eachother-your-phones thing, but that’s become less popular recently.
I just wanted something simple:
You meet someone you want to share your info with.You take some very quick action.They now have your contact info—in the form of a vCard on their phone.Those are the requirements.
I was initially thinking I’d just create my own QR Code, which points to a vCard hosted on my own server. And then I’d get that vCard printed on some kind of cool Titanium physical card that goes in my wallet. But that requires that I pull out the wallet, and then the card, and then put those back when I’m done.
So I decided to do everything on the phone, which for me is an iPhone.
Luckily, iPhone has touch-based accessibility shortcuts now, where you can open certain apps by tapping the back of the phone. iPhone also has Shortcuts, which allow you to automate almost anything you can do on a phone.
So here’s what I built.
I used Chrome to create a QR code that points to a limited-info vCard hosted on my own server.I created a custom URL that has that QR code on it.I created a Shortcut on the iPhone that opens that URL in my browser on my iPhone.I created a Touch accessibility shortcut that calls that shortcut when I double-tap the back of my phone.Done.
So now when I meet someone new, I pull out my phone, double-tap the back, and they’re shown the view you see above (except with the real QR code).
I think this will hold me over until the iPhone has native NFC-based contact sharing.
March 29, 2022
News & Analysis | NO. 324
News & Analysis | NO. 328
March 25, 2022
The Actual Pronunciation of GIF, from the Creator

Steve Wilhite giving the correct pronunciation as his Webby Award acceptance speech
The pronunciation of GIF is one of the oldest and most aggressive internet debates. Some of these will never be settled, but luckily with the GIF debate there’s an actual answer.
The creator of the GIF, Steve Wilhite, not only pronounces it as “jif”, but he says that’s is the only proper way to say it.
The image above is his acceptance speech for a lifetime achievement award at the Webby’s in 2013. His speech was itself a GIF, which you can see in the image above. This, in my opinion, shuts down all counterarguments.
The creator of a thing has the ability to not only name that thing, but to determine a correct pronunciation. Like Linus did with Linux.
I actually prefer the hard-g pronunciation to “jif”. And I get all the arguments for why it should be a hard-g.
Doesn’t matter.
If the creator tells you how to pronounce it—and how not to pronounce it—there’s your answer.
March 24, 2022
How to Disagree
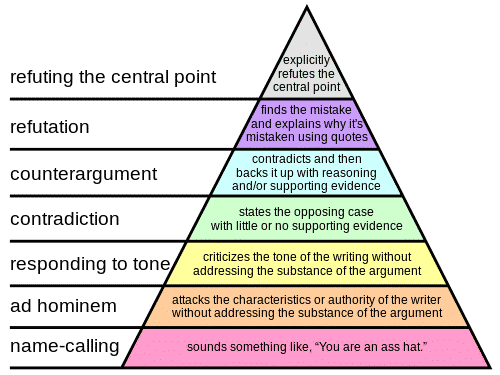
Paul Graham has a great piece on how to disagree with people in the best possible way.
He provides a hierarchy, with 7 being best:
Name-callingAd hominemResponding to toneContradictionCounterargumentRefutationRefuting the central pointThe TL;DR here is to evaluate any argument you’re having with someone, and see where each participant is in the hierarchy, and work to get to refuting the central point.
March 21, 2022
News & Analysis | NO. 323
No related posts.
March 20, 2022
Thinking About the Future of InfoSec (v2022)

I’m starting a new series with this 2022 edition where I think about what Information Security could or should look like in the distant future—say in 2050. The ideas will cover multiple aspects of InfoSec, from organizational structure to technology.
I’m doing this for fun—basically to see how dumb I look later—but I also hope it’ll drive interesting discussions on where things should go.
IntroductionOrg StructureTechnologyRegulationInsuranceAutomation / AICareersDistant FutureA Future ExampleSummaryIntroductionAt the highest level, I think the big change to InfoSec will be a loss of magic compared to now. In the next 15-30 years we’ll see a move from wizardry to accounting—and a much more Operational Technology approach to the discipline in general.
A big part of this will be simply doing the basics well, in a standardized way. We’re currently in pre-teen years here, which is the source of most of our problems. That means asset management, identity, access control, logging, etc. It means most similar types of products (APIs, hosts, datastores, etc.) looking and behaving similarly, with similar controls and interfaces regardless of vendor or implementation. It means standard APIs for auditing and controlling configuration and access to these systems, in addition to using them, so that you can continuously and programmatically determine an object’s security level.
Let’s look at the aspects that will contribute.
Org Structure
I think security will live within engineering in the future, much like building “secure” bridges isn’t a separate department within civil engineering. There’s not a “bridges don’t fall down” department because bridges aren’t supposed to fall down. We’re just not there yet with (info)security because it’s a brand-new field.
I think this might mean that security becomes a smaller oversight function up with the C-Suite, with strong collaboration with the CFO and the head of legal.
There will be a large Operational team that does nothing but monitor everything to ensure they’re within tolerances. This includes making sure only the right people are looking at the right data, only the right people are logging into the right systems, that services are available with enough 9’s, that they’re responsive, etc. Essentially the business will see what the risk tolerance is for all these items, and that’s what the Ops team will monitor in their dashboards. Again, like a factory.
AWS is one of the few things I could see being around in 20 years.
This smaller security team will be responsible for analyzing data from the various telemetry sources and ensuring that everything is within tolerance. This will include things like cloud configurations for open protocols, open ports, authenticated entities, encryption at rest, encryption in transit, who is accessing what items, etc.

They’ll basically be watching massive dashboards and managing responses to stimuli when things happen that are out of the ordinary, and then coordinating with the various oversight groups (foreshadowing: insurance) who are jointly monitoring and/or asking questions about their security posture.
TechnologyI think the main difference we’ll see in security tooling will be the integration with the actual IT applications, much like security engineering will be integrated with regular engineering. So there will be some security tooling still, but it’ll be more oversight-based rather than doing the main part of the work.
Similar to AWS now actually, where you have EC2 and Kubernetes configuration, and you have security configurations within those tools. There are separate security offerings from AWS, but from my view we’re already seeing a lot of that tooling move into the core services themselves. The security tooling becomes more about policy, dashboards, and reporting.
RegulationSome of this depends on the state of the world, i.e., how powerful centralized governments actually are in 20+ years, but let’s assume it’s much the same as now, just more. If that’s the case, we should expect laws to evolve to shorten the time in which incidents must be reported, and we should expect this for not just government organizations, but for corporate entities as well.
Basically, the argument will be made that everything is connected, and that people depend on these corporate services, therefore they’re national infrastructure to some extent. And thus you must report issues in a very timely manner. As the tech evolves I think they’ll require that 1) certain high-scrutiny organizations will require a giant monitoring brain that the government can tap into when needed or—in some cases—continuously.
HT to Jeremiah Grossman to also being very early to seeing the role of insurance in InfoSec.
Don’t worry, companies will feel more comfortable about this because the insurance companies will already be in that system. It’s good news / bad news.
Regulators will be everywhere. You’ll have to report things very quickly, and there will be severe fines for not doing so. The main difference from today will be that 1) there will be more reporting required, at shorter intervals, and many of those reports will need to basically be real-time through technology—at least for high-criticality gov/private organizations.
InsuranceLike Jeremiah and I have been talking about for years, I think insurance will be a major player in the future of InfoSec. Much of this maturity we’re going to see will come from innovations from organizations that have the most to gain from improvement. When it comes to cars and houses, that push came significantly from insurance companies.
You need these inspections or else you can’t get insured. You need smoke alarms. You need this. You need that.
We don’t yet know what those things are for security, but I can tell you who really cares what they are. Insurance companies. And they’re already instituting all sorts of visibility practices, like requiring that you install a black box on the network to get a sense of your environment. Exactly like Progressive asking you to install a box in your car that can monitor how you drive. Or health insurance companies asking for access to your mobile phone’s Health app.
The result of this is easily predictable: as insurance companies determine what works and what doesn’t, they’ll start requiring certain solutions and rating solutions in general.
Did you know Michellin Star Restaurants are associated with Michellin tires? It’s weird how history plays out like that. They did a campaign about restaurants you could encounter while driving (on Michellin tires, obviously), and that turned into a cornerstone of the restaurant industry.
Well, expect to see Allstate Ratings for Zero Trust solutions too. It’s a lot more inevitable than the Michellin thing, actually, because insurance companies are the ones who are incentivized to find out what actually works. Because then the insurance companies can steer their customers to use those solutions to reduce their own payouts.
Automation and AII was going to put this in the Technology section, but it’s worth its own treatment. Machine Learning will continue to soak into all of the world’s technology, and that includes security technology. It’s hard to say, but I do anticipate being able to replicate Level 2 or even Level 3 security analysts in some small domains when the technology is highly advanced and when attack types are relatively static, but most of the benefit of ML will come not from adding 20 L3 analysts, but instead from adding 100,000 mid-level interns.
The more standardization we have in our tech, and the more logging is required, the more data there will be to look at. This problem is not solved by getting more people into the security field. There’s too much data for humans on the planet to analyze, period. This is already true, and it’ll be many times more true in 2050. Automation is needed to filter and curate the data that humans see, and as time progresses the distinction between automation and AI/ML—at least in information technology—will continue to blur.
ML will have the biggest impact in answering questions like the following, at scale:
Was this action fraudulent?Is this a legitimate transaction?Was this action performed by the user it was associated with?What is the weakest point of entry into this company or country?Where should we attack?Where should we anticipate attack?Among these billions of vulnerabilities, what should we fix first?What change should we make to improve outcome X the most?A good definition of AI is what computers can’t yet do, which is always moving.
In short, ML will continue to become more like statistics, charts, databases, and computers—i.e., a standard way of solving problems in any organization. It’ll just blend into businesses in the same way that your business isn’t considered special for having a Postgres database. One big AI-based innovation step will be general AI, which may or may not happen in the timeframe we’re discussing.
The next aspect of this, which could have been put in the Technology section as well, is CCE, which stands for Continuous Chaos Engineering. The field is also known as AD for Anti-fragile Design, but “AD” was too overloaded as an acronym that people have been using CCE. The point of these processes is to not only continuously monitor to make things are in an ideal state, but to constantly add stress to the system—of different types—to ensure that the system can handle it.
SCs (Stress Campaigns) are constantly run an arm of engineering to ensure that not only could we survive these if they happened, but in order to actually improve from what we learn. So if we send a massive amount of traffic to a key API endpoint as part of a new SC, and we see X amount of deterioration of the service, we might send an immediate request to boost that service’s on-hand service nodes.
The operational teams monitoring the state of the IT infrastructure will have the challenge of not always knowing (but perhaps sometimes) when an issue that takes a parameter out of compliance comes from an actual natural problem, a member of the offensive team trying to do something malicious, or a real attacker attempting an attack. Some teams will tag activity with various labels (OFFSEC, CHAOSOPS, UNKNOWN, ATTACKER22301 etc.) to help with that attribution, but part of operations will sometimes be having regular operators not know the difference.
CareersOk, cool. So what about people? What will it mean to be in security in like 2050? I think the answer is:
More Electrician-types (tradespeople connecting things according to documented specs)More Data Analysts (statistics and ML background, combined with data visualization)Security Executives become factory fore-people, i.e., overseeing an operational function, combined with broadcasters of narrativeThere are still variation in electrician implementations, too.
So we’ll have millions of people employed to install and configure the various types of tools needed in a business. I think these tools might blur between the tools themselves vs. the security tooling. For example, if people come to install Salesforce they’ll be installing it and configuring it to plug into your internal data lake and brain. So, just like electricians, there will be well-known inputs, and well-known outputs, and it’ll just be a matter of figuring out where to put what.
In other words, when Allstate and the State of Massachusets come to connect to your company’s IT Brain, called Conito, provided by Databricks (now owned by Amazon like everything else), everyone will be using the same nozzles and connectors.
Join the Unsupervised Learning CommunityI read 20+ hours a week and send the best stuff to ~50,000 people every Monday morning.Careers will be more cleanly broken into functions like:
Installing things according to regulation and standardKnowing the current configuration of a given system at all timesAnalyzing the data from all systems to get that into dashboardsEvaluating dashboards to determine which changes to configuration should be madeMaking configuration changes and evaluating their impactContinuous monitoring of those dashboards to flag anomaliesUsing AI/ML to make smarter and smarter recommendations based on the data availableTaking the output of data analysis and dashboards and turning that into narratives for partners, management, investors, insurers, regulators, etc.If this sounds boring, yes, it will be. That’s the point. That’s what happens when you move from wizards to book-keepers. Wizards deal with the unknown. The arcane. It’s where few people know what’s happening, and everyone looks up to them. This is bad for business because it’s not repeatable.
Accounting is repeatable. Arithmetic is repeatable. And so will be identity, access control, logging—once we hit our late 20’s and early 30’s as an industry.
What does this mean for “jobs in security?”
It means you’re installing products for an internal company. You’re installing products for Allstate, which means for Allstate’s customers. Or you’re using data analytics and data science to look for patterns in the data in FooCorp’s Cognito install. Or you’re a configuration validator who makes sure every product is installed to standard, with all inputs and outputs working correctly.Or you’re an engineer working on improving the products themselves.Or you’re an executive telling the data security story to your stakeholders.Will there be OFFSEC people? Red team? Blue team? Absolutely. All of this still has cruft in it. Even though it’ll be 95% better than today, that 5% will still be able to cause havoc and the loss of a lot of money.
So there will still be some arcane magic users, but they will become fewer and fewer as time goes on. And they’ll increasingly need to be strong developers skilled with analysis and manipulation.
Distant FutureThis gets fuzzier as we move forward, obviously. But let’s try to add some decades and see what changes the most.
I think the simplest answer is “fewer people”. As the tech keeps improving, it also gets better at installing itself, continuously checking its own configuration, raising alarms when it’s not working, etc. That means fewer people required to do those pieces.
So it’s fewer and higher-skilled people doing data analysis on what the dashboards are telling us, and creating better dashboards, rather than doing the installs themselves. And then it’s fewer but higher-skilled executives taking that data into conversations with stakeholders.
And then of course there are the people working on the actual products. This will increasingly be elite work for the best programmers in the world since an increasing proportion of “basic development” will be within the capabilities of AI/ML by then. But again, remember that these people will largely be working for the technology companies, not for security companies. They’ll just be working on security features for Cognito, Salesforce, or for AWS’s equivalent at the time.
I anticipate there will still be security companies, but that they’ll largely be incubators for candidate security features for inclusion in the bigger IT products. So the company takes a copy of Cognito and their competitor, spends a few months working on a cool set of new security features, and then they take that to the market. And if the feature is strong those companies will buy the code and/or the team.
In other words, I think much of the current security market is based on how poorly the industry does the basics. AWS exists because local IT within companies was a dumpster full of burning tires. Asset management companies exist because nobody knows what they have, and therefore what to defend. Endpoint companies exist because OS’s haven’t been great at identity, access control, and allow-listing applications and content. As those basics improve, that functionality moves back into the core products.
AWS will have asset management and continuous monitoring. Microsoft will have endpoint protection. Databricks will have data security built-in. This does raise the question of monopoly, and how companies will be inspired to innovate if they’re the consolidated big companies at the table, and I think the answer will have to be some combination of this feature development model for startups along with regulation that pushes higher and higher standards for organization protection.
I can easily see AWS being broken out relatively soon.
That’s a weird thing to type, actually, and it’s why I’m doing this exercise. As companies like Salesforce and AWS get bigger through success and acquisitions the incentive to innovate will eventually slow down. And furthermore, if you’re on AWS and they provide like everything for your company, it’s going to be pretty hard to migrate over to some new upstart’s offering if it’s in conflict with AWS in some way. The momentum to stay with AWS will continue to build because new companies won’t have the resources to offer similar stability or support.
A Future ExampleAmaya works for Progressive, which is the main player in auto and Cyber Insurance.
She is an expert with Cognito, a formerly Databricks and now AWS tool for unifying all IT feeds (which include security) into a single place. It’s basically the brain of most enterprise IT infrastructures. She is going into a medium-sized business that’s having issues with their telemetry meeting insurance and government standards. In other words, not everything is configured correctly, logging, to the right places, at the right verbosity levels, and at the right cadence. And it’s not all being sent to a single place.
She starts with the AWS infrastructure and applies a Cognito template that does a bunch of analysis (AI/ML stuff) to look at everything that exists, all of its existing settings, etc. She then selects a policy template that accounts for what Progressive is asking for, as well as the State of Michigan where the company resides, plus some additional asks from other stakeholders. That takes a few minutes to finish because it has to look at every setting in all of AWS and determine current state and end state.
She then launches CogniBot, which is a set of hundreds of thousands of ai-automated applications that spider and crawl and log into things dynamically given the credentials and authority she’s been given to do this project. This allows the bots to learn the delta between what they see in the configurations vs. what actually exists in the infrastructure. CogniBot systems coordinate to look at the external perimeter, internal access controls, listening services, all software versions, etc. Essentially the same thing the configuration tool looked at, but it’s doing it dynamically via active and passive probing.
These are left to run for between 3 days to a month, to listen on the network, to watch traffic patterns and other aspects of the business that aren’t as clear from static analysis, and to generally provide peace of mind that the migration to the new Cognito Template will not cause disruption to business.
Upon her return, Amaya will review all the data with her team, meet with the customer, coordinate a time for the changes, and then begin migrating all AWS settings to the new policy. This will happen in a phased approach that Cognito’s intelligence came up with—including automated rollback if problems are detected during the process. Cognito will continuously monitor the state of business during the migration and ensure that all business operations continue to function throughout. They start with datastores, then move to network access, then to endpoint lockdown, etc.—all the way through the systems controlled by AWS.
This will change access controls, enabled protocols, storage settings, and pretty much every configuration option that has a bearing on Progressive’s and the State of Michigan’s controls, as defined in their templates.
At the end of the migration, Amaya and her team look at the new Cognito dashboards, which show all the data and new telemetry flowing into the Amazon Databricks backend. They see that every cloud server, every application access, every authentication challenge, every endpoint action, etc.—are all being logged into Cognito, and we are currently sitting at 94% compliance. It appears that the policy rollout could not hit some percentage of endpoints because they were hard-powered-down, and we’re waiting for them to re-associate.
Her team will continue to monitor this, and now they start thinking about the next project. Salesforce. Terabytes of data is being created for this company per week within the system, but the storage configuration and logging are not compliant with 7 different states, Ireland, Iceland, or Papua New Guinea. Or with Progressive, which is why she’s been assigned to the project.
So now she’s going to take the Cognito templates for all those jurisdictions and run them against the petabytes of data for this customer, as well as every setting that pertains to protecting that data, and will produce the configuration changes to get it compliant. Most importantly, it will not only lock down all those settings but will enable verbose logging for all events and send it all to the Cognito instance within the company.
Months later, Tariq is enjoying his new position as head of security for the company, and he’s having his coffee while looking at the Cognito dashboards. Everything is running within appropriate tolerances, and has been for several weeks. There are occasional Orange or Red events where configurations go out of compliance, or where an object fails to report in with telemetry, but those are quickly accounted for by the massive operational team they run.
This team essentially watches the Cognito dashboards and takes corrective action whenever anything goes out of compliance, followed up by the RCA team taking an action item to ensure that never happens again.
SummaryAs our industry moves from our pre-teens to our 20’s and 30’s (2030-2050?), we’ll transition from Wizards to Accountants.Much of this will center around doing the basics of asset management, identity, access control, and logging well.AI and Automation will remove the need for a lot of the manual work of installing and monitoring products.We will soon see large, monolithic, ML-powered products that take in all telemetry from everything, and produce unified dashboards.Insurance and Regulation will push towards this, driving the standardization and operationalization of InfoSec.Security will increasingly blend into engineering, both at the technical level and within organizational charts.As part of operationalization, the concepts of resilience and antifragility will become major considerations.The mid-game (who knows what endgame is) involves a massive operations team monitoring centralized dashboards and responding when things go out of tolerance. Not security dashboards. Company dashboards. Which include security and lots of other types of metrics and risk-levels that need to be kept within tolerances.NotesOne thing that detracts from the factory metaphor is that factories generally account for first-order chaos, or static threats like equipment failure. Cyber is different because the attacker knows the current state of their abilities as well as defenses, and can modify their behavior accordingly. I think this will slow, but not stop, the inevitable march towards boring dashboard InfoSec.Credit to Caleb Sima for some enlightening seed thoughts on the integration of security and engineering.Ironically, heavy automation seems to open the door even more for OFFSEC and Blue Team, because the more we blindly depend on autonomous technology the more vulnerable we could become to everything suddenly breaking—either on accident or on purpose.Image from Langara. MoreMarch 19, 2022
Google Has Opened the Door To Cloudflare
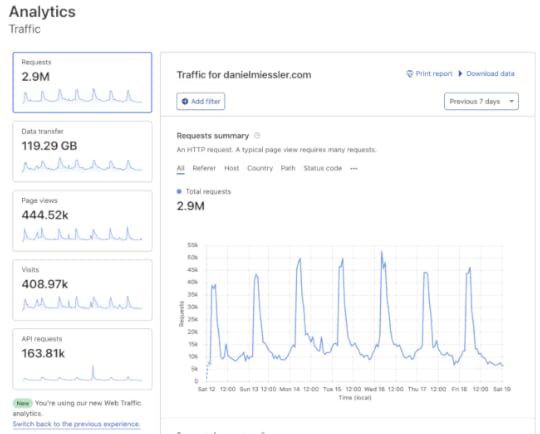
I’ve been complaining for years about Google’s various UI/UX problems.
As the most recent example, I got a notification that I had over 10,000 views on the site yesterday. Cool. Well, except I had those views on Wednesday, and got the alert yesterday.

Yes, they have a service called traffic “alerts” that doesn’t send an actual alert until 24 hours later. That’s not an alert. That’s a report—barely.
But no big deal. Probably an easy fix, right? Let’s just let them work on it? Nope. I and others have been complaining about this same exact problem for over 6 years, including sending support emails into the least monitored inbox in the Sol planetary system.
They don’t care, and even worse, they don’t seem to realize that they should. A recent Hacker News post asks an important question: If Google Sucks So Bad, Why Are People Still Using It?
Good question, and I think the answer is quite simple—Google’s features and stability have thus far been more compelling than its faults because there hasn’t been a strong enough competitor.
I think Cloudflare is changing that.

Clouflare is Borging-up tons of internet spaces that used to belong to other companies. And they’re doing it while providing stable services and a modern UI.
Join the Unsupervised Learning CommunityI read 20+ hours a week and send the best stuff to ~50,000 people every Monday morning.They’re cutting into the WAF space, third-party web integrations, zero trust, internal VPNs, content distribution, DNS hosting, and countless others.
Importantly, they are constantly innovating and—check this out—they answer support requests. They’re responsive. They’re listening and they’re adjusting to what they think customers need.
This is the Star Trek opposite of Google doing all these same services. For them, they build a cryptic UI, that people struggle to use, and they proceed to not change that UI for years and years. Best part of it? There’s no one to email. No one to call. It’s basically saying:
Hey we made a thing without any care for how easy it is to use, but it’s kind of the most stable thing out there because we’re Google. Maybe you’ve heard of us. Oh, and don’t complain because nobody’s listening. You’re welcome.
How I Imagine Them Talking In My Head
We accepted that. I accepted that. Despite saying for nearly a decade that I was done with Google. I never left because I never could.
And I can’t shake the feeling that Cloudflare knows this, and that they’re working to pull all these core-internet-infrastructure services from them.
I hope they do.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers





