Daniel Miessler's Blog, page 124
May 7, 2017
A Look at Application Testing in a Near Future
 For some silly reason I was just awoken by the following thoughts about how application tests will be done in the future. I’m thinking this starts phasing in over the next 3-10 years.
For some silly reason I was just awoken by the following thoughts about how application tests will be done in the future. I’m thinking this starts phasing in over the next 3-10 years.
The application will be decomposed using an automated tool to break it into the binary, the source, the network interfaces, the application-layer interfaces, and any other components / surface area.
The binary will be published to a harness location that allows approved tools and partners to access it in a standard way. This will include third party services, third party paid algorithms, as well as a host of free automated fuzzing algorithms.
The source code is published to a source code testing harness that works in a similar way. A set of free automated tools start working on it immediately, a beacon is published to the trusted consultancies that have paid for access to the test interface, and vetted individual testers will be notified as well that they can begin testing as well.
Network and application layer interfaces are enrolled into similar testing harnesses, which also spawn notifications to the tools, consultancies, and individuals who are partnered to test the application.
Submitted vulnerabilities, contracts for who is paid what based on what is found, are all handled by Ethereum, i.e., a smart-contract-based blockchain. This handles who found what, which items are duplicates, and how much was paid to find each vulnerability.
So it becomes all about the inventory of the components of the application and their arranging into a standard testing harness.
From there, tens, hundreds, or thousands of automated testing algorithms start firing to find vulnerabilities. They range from simple, rules-based systems to deep learning powered algorithms powered by terabytes of testing data for extremely similar apps—and those algorithms are updated continually.
Those algorithms are also competing with the human element, which might also have their own algorithms they can leverage as well. So human testers / researchers will be signed up for multiple contracts, using Ethereum or something similar. And when the notification goes out that an app has become available in a contract you’re a part of, you can immediately launch any of your automated tools as well as sit down to test yourself.
So imagine a binary sliding into a ship hangar, and a number of cables come from all sides and slide into their ports on the binary. 14 million people are notified that this binary is available for testing, and tens of thousands of algorithms start their work, which discovers vulnerabilities instantly and reports them to the blockchain.
Same for the remote components. The running application is slid into a similar hangar, and connectors touch the TCP/IP stack, the app layer in various ways, etc., and automated probes start instantly. The best common rulesets. The best ML/DL algorithms for that particular application type. A set of fuzzing algorithms kicks off that was just updated 12 minutes ago and is the best in the world at crashing these particular services.
For many applications that do or will have external public interfaces, notifications are also sent out to millions of independent testers simultaneously, with the only criteria being that they must be part of the Ethereum network that manages the integrity of contracts, submissions, and payment.
And then everyone goes to work on the app. All its components. Humans and algorithms battling it out. With findings streaming in over a high-integrity, high-transparency blockchain.
Insurance companies will require that applications be continuously tested using these types of harnesses, and they’ll be rated with various levels of security based on the type and duration of scrutiny the application has endured without finding additional vulnerabilities.
A number of these elements are already starting, or are already in place, but what I find most interesting about the model is breaking the app into components, using common interfaces for testing those components, and then a common contract and reporting mechanism based on the blockchain.
—
Ok, now coffee and breakfast.
Notes
I say applications here, but this is really any kind of security testing. And actually, not even just security. It’s a testing and validation framework, and the testing can have multiple forms.
A number of things will be needed to get this going, including some sort of mechanism for instancing. You can’t have everyone touching the same system at the same time. Especially for dynamic testing.
Side note: I really dislike posts titled, “The future of”, or “In the future”. It’s cliche. It’s pompous. It’s just bad. Need to figure out better ways to convey these types of interesting conjectures / predictions of what’s to come.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
May 6, 2017
How to Get Extracted Fields into Your Splunk Alerts
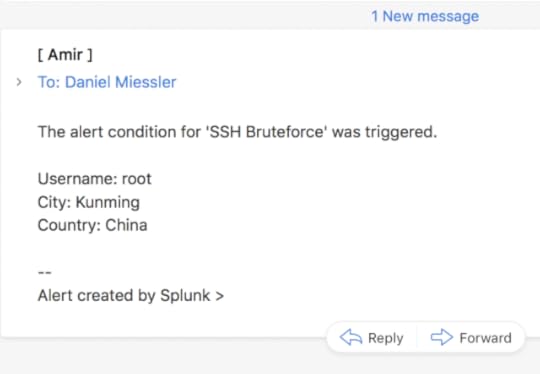
I’ve been continuing to improve my Splunk> game, and part of that has been improving the information that comes in email alerts.
The image above shows the final result I am looking for, where you get custom information that’s contextual to the alert that was generated.
The problem

The issue is that this doesn’t work by default. You can’t just save the search above as an alert and have it give you the results in the email above. What you’ll get instead is empty fields.
Here’s what the template looks like:
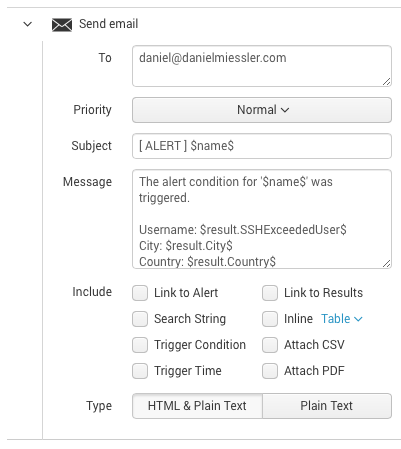
The issue is that those $result.City$ and $result.SSHExceededUser$ fields may not show up at all in the email, even if you make sure those fields are included in the search result.
The fix
The fix is easy enough, although I wish it weren’t necessary.

What you do is send your search result to the fields command, followed by the fields you want to be able to use in your email template.
Once you do that you’ll get the extracted results, as seen in the email above.
Hope this helps someone.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
May 3, 2017
Embracing Female Oppression as a Sign of Feminism
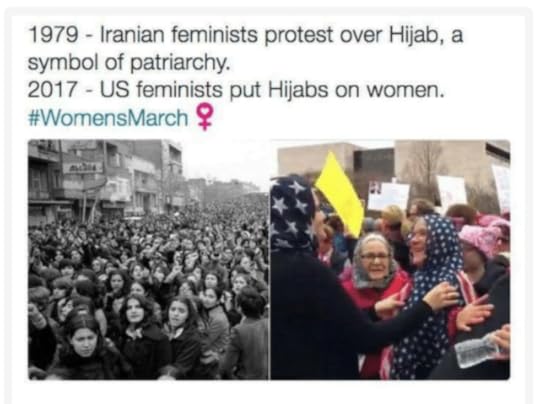
The regressive left, or Lupus Liberals as I like to call them, are heroically confused about the Hijab.
The source of the confusion seems to be that there are western people, especially men, who don’t like the Hijab for various reasons. Some are good, some are bad. Good reasons include not liking the fact that this is a religious practice that outright limits the rights of women. Bad reasons include bigots associating the hijab with everything else they hate in their xenophobic little brains.
But either way, because the Hijab is countered by many in the west, it’s now become impossible for these far-left types to see the issue clearly.
Basically, it almost doesn’t matter what the practice is—it simply becomes legitimate if it’s 1) ethnic or religious, and 2) opposed by people in the west.
The concept of the Hijab is unbelievably anti-liberal, and anti-feminist. That’s why it was protested by so many women in Iran when the law went into place. They didn’t want the Hijab. They saw it for what it was—a suppressive and oppressive force that affected only one gender.
And its source is equally non-liberal. The argument is that women need to cover their hair because it’s overtly sexual, and that men shouldn’t be expected to restrain themselves around women who are showing their hair openly. It’s basically a veiled form of, “If you dress like that you deserve to get raped.” It’s quite sickening.
And that’s the origin. That’s the religious and cultural backing for the practice. And, crucially, in many countries it’s required. Women who don’t wear it are looked down upon as whores and/or arrested in many countries that believe such things.
The counter argument goes something like this.
You don’t understand Islam. Islam loves its women, and it wants to protect and cherish them. That’s why you’re not supposed to show your hair, or talk to or shake hands with men who aren’t in your family. It’s because Islam loves women. And since I love Islam, and you’re attacking its practices, then that means you’re anti-Muslim, and anti-me. And I will protest your oppression.
So many American feminists are accepting and defending this line. The concept can be simplified as this: we already know white westerners are bad, so if white westerners dislike the Hijab then it must be worth defending.
The problem, of course, is that this also applies to other, extremely common practices in countries that embrace Islamic law. Honor beatings, honor killings, genital mutilation. These all spring from the exact same well as the Hijab. And in any normal light the feminist would oppose them outright. But since the west dislikes them, they must be worth defending.
Summary
As I said in the Lupus Liberalism piece, there’s a way out of this labyrinth.
Simply keep in mind that intolerance of the oppression of women and the intolerance of female equality are not the same. They’re both intolerance—and that’s what’s confusing the far-left—but one is being intolerant of attacks of womens’ rights, while the other is actually limiting those rights.
Those are not the same.
Don’t allow the labels and shapes of the debate participants to confuse this point.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
May 2, 2017
Unsupervised Learning: No. 76
This week’s topics: Verizon’s DBIR report, Chipotle (again), USAF bounty, NSA surveillance hampered, Android hacks, Taser and computer vision, Google fights fake news, Exercise types & mental skills, Perfect pitch recording, Lifecasting, RF X-Ray, discovered links, and more…
This is Episode No. 75 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 15 to 30 minute summary.
The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well.
The show is released as a Podcast on iTunes, Overcast, Android, or RSS—and as a Newsletter which you can view and subscribe to here.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 5K subscribers.
Recent Newsletters
04/23/2017 – Daniel’s Unsupervised Learning Newsletter: No. 76
04/23/2017 – Daniel’s Unsupervised Learning Newsletter: No. 75
04/16/2017 – Daniel’s Unsupervised Learning Newsletter: No. 74
04/09/2017 – Daniel’s Unsupervised Learning Newsletter: No. 73
04/02/2017 – Daniel’s Unsupervised Learning Newsletter: No. 72
03/26/2017 – Daniel’s Unsupervised Learning Newsletter: No. 71
03/19/2017 – Daniel’s Unsupervised Learning Newsletter: No. 70
03/13/2017 – Daniel’s Unsupervised Learning Newsletter: No. 69
03/06/2017 – Daniel’s Unsupervised Learning Newsletter: No. 68
02/27/2017 – Daniel’s Unsupervised Learning Newsletter: No. 67
The podcast and newsletter usually go out on Sundays, so you can catch up on everything early Monday morning.
I hope you enjoy it.

__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 28, 2017
Why You Should Be Using More Emoji

If you’re over 30 you’re probably a bit averse to using emoji to communicate.
You probably think it’s unprofessional, that it’s “not real language”, or that it’s a fad that will go away soon. My opinion is that it’s a permanent part of communication (although it’ll evolve into richer forms), and that if you’re not using it you’re limiting yourself.
First, it’s extremely efficient. You can communicate a surprising amount of information with an image, and the range of emotions you can convey is vast.
Second, it’s a new language type, and ignoring it only hurts you, not others.
In short, you can benefit from the expanded range of communication that it offers, and staying embedded in active zeitgeists keeps your mind nimble by exposing it to constant change.
Embrace it, and let it help you grow.
Start using emoji.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 26, 2017
The Jobs Most Vulnerable to Automation

TABLE 1. — The most and least automatable jobs.
Any parent or teenager not thinking very hard about this list is putting themselves at a severe disadvantage.
And a lot of the jobs will surprise you. Being a waiter at a restaurant is remarkably resilient because the robots required to move around quickly, juggle lots of food, make quick adjustments, read peoples’ temperaments, attitudes, etc., and adjust accordingly—those are not skills that will come cheap to restaurants any time soon.
But few people are making much money being a waiter, so it’s not necessarily a job to look forward to as someone in high school, or as a parent of someone in high school.
Same with being a low-end medical person, like taking care of the sick and elderly. That’s not easy to replace with automation, and we’re going to need LOTS of these people, but it also won’t pay much money at all, or command much respect.
Then there are tons of jobs that command lots of respect, but that are based on pattern recognition, like Radiologists, and Stock Traders, and Investment Bankers. Looking at radiology films, images of potential skin cancer, etc., are skills that took 10-15 years to master in the past, and hundreds of thousands of dollars in schooling to qualify for. So people who could do it made lots of money.
But now they’re being beaten at their game by algorithms. There are numerous examples now of algorithms finding issues in radiology films, identifying cancer, making better stock trades, etc., than the best humans in the world.
Importantly, when you improve an algorithm, you just copy it over and it works for whoever’s using it. You can give it to one or 1,000,000 people simultaneously, because it’s just technology. High-end humans are hard to create and hard to replicate. It takes a lifetime, tons of money, and lots of luck. The tech is going to win that race, and it already is. And that’s with them entering the game just a few years ago.
Summary
If you want to stay employable, and highly valued, you should be thinking about what is hard for AI and/or robots to do. This won’t keep you safe for decades, but it might protect you for the next 10-20 years at least. After that, it’s hard to say what won’t be vulnerable to automation.
If you care about someone’s future, make sure they understand this issue. Don’t let people you care about chase money right into a brick wall built by smart robots.
Notes
The referenced piece can be found here.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 23, 2017
Unsupervised Learning: No. 75
This week’s topics: DoublePulsar in the wild, vigilante IoT worms, Bose listening headphones, PoS hacking sentence, Google ad blocking, best anti-aging exercises, unqualified Indian engineers, , discovered links, and more…
This is Episode No. 75 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 15 to 30 minute summary.
The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well.
The show is released as a Podcast on iTunes, Overcast, Android, or RSS—and as a Newsletter which you can view and subscribe to here.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 5K subscribers.
Recent Newsletters
04/23/2017 – Daniel’s Unsupervised Learning Newsletter: No. 75
04/16/2017 – Daniel’s Unsupervised Learning Newsletter: No. 74
04/09/2017 – Daniel’s Unsupervised Learning Newsletter: No. 73
04/02/2017 – Daniel’s Unsupervised Learning Newsletter: No. 72
03/26/2017 – Daniel’s Unsupervised Learning Newsletter: No. 71
03/19/2017 – Daniel’s Unsupervised Learning Newsletter: No. 70
03/13/2017 – Daniel’s Unsupervised Learning Newsletter: No. 69
03/06/2017 – Daniel’s Unsupervised Learning Newsletter: No. 68
02/27/2017 – Daniel’s Unsupervised Learning Newsletter: No. 67
The podcast and newsletter usually go out on Sundays, so you can catch up on everything early Monday morning.
I hope you enjoy it.

__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 21, 2017
Monitoring SSH Bruteforce Attempts Using Splunk

I do lots of monitoring on my site (I’d rather watch logs than Netflix) which I’ll talk about in separate posts, but today I want to talk about SSH. I’m going to cover how I log, how I get those longs into Splunk, and what kinds of searches and alerts I have set up.
Getting Splunk to monitor SSH logs
First off, I’m running Ubuntu 16.04, and SSH natively logs to /var/log/auth.log. So the first thing I do is go to Settings –> Data Inputs –> Add Data within Splunk, and then add /var/log to the inputs. That basically makes it so that Splunk monitors every log file coming under that directory, which is most logs on an Ubuntu system.

Image 1. — Telling Splunk to monitor a directory.
What questions are we asking?
The next thing to figure out is what we want to know about incoming SSH attempts. It’s a common problem within security that people just start making metrics without thinking about their questions first. My questions were:
Who’s trying to log in with an invalid user?
What user are they trying to use to log in?
Where are they coming from?
The first question requires us to look for invalid user entries in the logs. The second requires us to extract that user out of the log. And the third question requires us to get geolocation from the connecting IP address.
Performing the extractions
So within Splunk, there are a few tools that help us do this.
To find invalid users you simply search for entries like that in the logs, and the string happens to be, literally, “invalid user”. You get some junk in those results which you can clean up with a couple of NOT statements, leaving you with the following search.

Image 2. — Your starting query.
This gives you results like the following:

Image 3. — A basic search result.
This is decent, but we can do better. You can see that we have invalid users here in each entry—in this case admin, but the power of Splunk is taking fields inside of raw log files and turning those into actual fields you can manipulate and play with.
For that, we need to do some field extraction. To do that, click on the “>” in any individual search result, click the Event Actions pulldown, and select Extract Fields.

Image 4. — Starting a field extraction.
Extracting the user
First we’re going to extract the invalid user, and we do that by picking the Regular Expression option, selecting the word “admin” in the log, and saving it as SSHInvalidUser. Now we have that as a field, which looks like this in search.
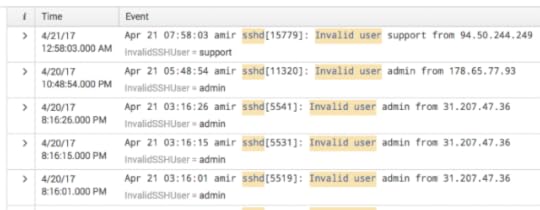
Image 5. — A result with the invalid SSH user extracted.
Getting geo information
Now to figure out who’s launching these attacks against us, we’re we need to convert that IP address we see into a location. Splunk does this automatically now with a built-in function called iplocation. But first we need to extract that IP into a variable of its own.
So we go through the process above and select the IP address this time, and save it as InvalidSSHIP. So now we have two different variables stored: InvalidSSHUser, and InvalidSSHIP
Then we add the following to our search query: | iplocation InvalidSSHIP, which looks like this.
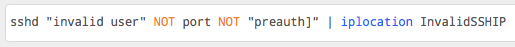
Image 6. — Search results with geo information.
Which then gives us these interesting new options to the left of the results.
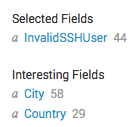
Image 7. — New field labels.
We now have “City” and “Country” as options, and further down we have “Region” as well. So Splunk has automatically translated all those IPs into locations.
Adding fields to search results
Now that we have all these fields extracted, let’s add them to the search output. Just click the “All Fields” button to the left, and select the ones we’ve created. Results now look like this:

Image 8. — Search results with all fields visible.
That’s coming along nicely. We can now see the country, the city, and the username they tried to log in with!
Using Splunk’s analysis capabilities
Now that we have the components in place, we can start having fun with what Splunk does for us automatically. The fields to the left area all clickable.
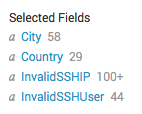
Image 9. — Clickable field names.
And when you do click on them, they expand out into a statistical view.
Viewing by country
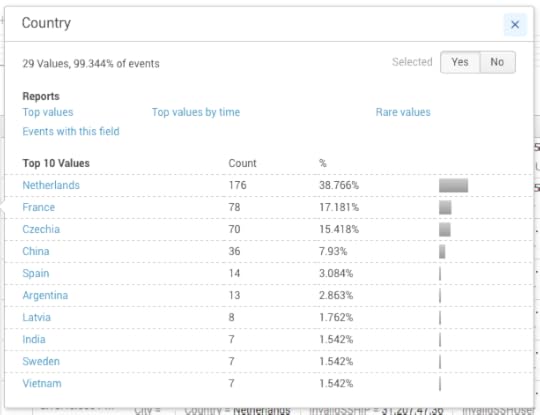
Image 10. — Top attacking countries.
Viewing by invalid username

Image 11. — Top attempted usernames.
And then finally, graphing the results by clicking “Top values” in one of those boxes.
A graphical view of most common attempted users
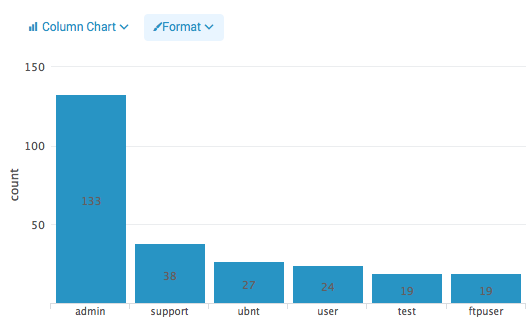
Image 12. — Top attempted users shown as a bar chart.
Summary
Bottom line here is that it’s possible to do all kinds of fun stuff with default SSH logs, a free Splunk installation, and just a few minutes.
Happy hunting.
Notes
I didn’t mention how to install Splunk on Ubuntu, but it’s basically a two minute process. You download the latest .deb package from the Splunk website and do dpkg -i $PACKAGENAME. That’s it.
I don’t work for Splunk nor have any relationship with them. If I did I’d say so clearly at the top when I mentioned the product. I’ve just loved and used the product for years.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 20, 2017
AWS IAM Security Terminology Primer

What is IAM
IAM Users
IAM Roles
Access Keys
IAM Policies
Security Groups
AWS naming can be a bit strange, and there are a lot of components within their security infrastructure, known as IAM. This page will introduce you to the various components are and what they’re used for. Keep in mind this is just a primer; there’s a lot more nuance to many of these areas than we’re going to talk about. But this should get you going.
What is IAM?
First, IAM stands for Identity Access Management, and it’s pronounced, “I am.” It manages both authentication, i.e. ensuring people are who they say they are, and authorization, i.e., ensuring entities are allowed to do what they’re asking to do.
IAM Users
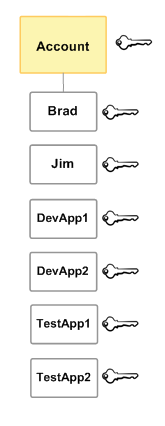
IAM Users are not separate AWS accounts—they’re users within your account. You have your primary AWS account, which is your email and password to get into the AWS Console, and those credentials can function as root on any system within your account. So be careful with it, and don’t use it to administer your infrastructure.
IAM Users are what you should use instead, both for yourself and for any other function you need to give access to. This can include people, applications, etc. Each user can have their own password and their own access keys (see below).
Best practice per Amazon is to create an IAM User for yourself, give it admin permissions, and use it to do all your administration, including creating other users. You should also lock down both the root user and any administrative users using 2FA, which now supports authenticator apps such as Google Authenticator, OKTA Verify, etc.
IAM Roles
IAM Roles are like user skin suits. They have permissions assigned to them, but they don’t have credentials because you’re assuming that role with an existing user. They’re good for when a given role is done by different people at different times.
Access Keys
IAM Access Keys are basically SSH keys. It’s a bit more complicated than that because there are other types of keys, but for getting started you can think of Access Keys and SSH Keys as synonymous.
Policies
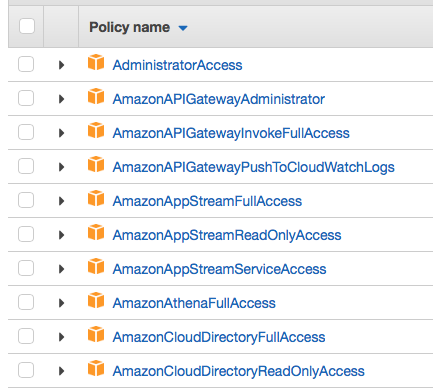
IAM Policies are fairly straightforward—they’re documents that encompass one or more permissions and let you define actions, resources, and effects (allow or deny). You can assign them directly to users, but it’s recommended that you assign them to groups instead, and then assign users to those groups.
Security Groups

Security Groups are strangely named. If you’ve been in security for a while and are hearing the term for the first time you’d probably assume they’re similar to…well, groups.
Nope. They’re basically firewall rules.
You define the protocol, port, and what source IP can access that port. And there are some presets for common ports, e.g., HTTPS, SSH, ICMP, etc. One cool feature, though, is that you can share the rules across different boxes without recreating them, almost like policies, except for network traffic.
Summary
Ok, here they are again in quick form.
The default user within AWS is your email/password you logged in with. You don’t want to use that to manage any boxen. Create a new user to do that.
IAM Users are what they sound like, and you can use them for apps as well as people.
It’s best to enable 2FA on any admin level account.
Roles are user skin suits. They’re for temporary functions, like “Backup Administrator” or something, which might have different people doing it.
Access Keys are basically SSH Keys. They’re how you authenticate to your infrastructure.
Policies are collections of permissions that can be assigned to users (not preferred) or groups (preferred).
Security Groups are essentially firewall rules that you can use across different boxes.
I hope this helps someone get up and running in AWS faster than they would have going through the documentation themselves.
Notes
If you spot any egregious errors in my simplifications, do let me know so I can fix them.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 19, 2017
My Thoughts on ELYSIUM Basis

I’ve been into supplements since my early 20’s. I’ve just always been intrigued by the possibility of being a better version of myself, via whatever means.
A supplement has emerged recently called ELYSIUM Basis that is generating significant chatter in a few circles, and the reason for that is it’s associated with anti-aging.
It’s quite controversial, but it’s backed by a powerhouse of medical professionals from MIT, Harvard, Stanford, Columbia, etc., who are adding legitimacy to the project.
The FDA is militant about such things. You basically can’t claim to address specific ailments without going through extraordinary hoops, and the process is extensive. Elysium is nowhere close to that, so all they can do is sell a “supplement”.
The pitch is simple: there’s a chemical that is far more plentiful in young people than old people, and BASIC (the name of the supplement) is supposed to significantly increase the amount of that chemical. They did a study on mice and extended their lifespans by 40%, and I believe they’re working on human trials.
I’ve been taking it for a few months now, and some pretty crazy things have happened to me since doing so. Most notably, I have had my lower back pain and a really bad, persistent achilles tendon injury pretty much disappear within the last couple of months.
But I can’t tie the effect to BASIC directly. I had a break in physical activity for almost three months over the holidays and start of the year due to being sick. Even more significantly, I’ve started taking 5,000 IUs of Vitamin D daily, which is widely considered to be the vitamin to take if you are into supplements. Most people don’t get nearly enough, it’s strongly tied to your immune system health, and my levels were very low when I checked at the end of last year.
So my body feels way better. I feel smarter. I feel springy. And it’s great to not have pain when I exercise or go on walks.
But Vitamin D is known to be highly associated with immune system health. So what if I had such low Vitamin D levels that my immune system wasn’t able to heal properly? And what if it Basis had nothing to do with the improvement?
Seems quite possible.
Or maybe it was the Basis. Or maybe it was some combination, or one or more variables that I haven’t even considered. Either way, I’m continuing to take both right now, and continuing to see benefits. I’ve not the time or patience to conduct an unofficial study where I stop one and then the other and properly record my state at various times.
One of my jobs with this site is to bring you interesting ideas, so this is one. Basis might be an anti-aging drug that could extend your life by 40%, which you should start taking as soon as possible. Or it could be complete crap.
I’m taking it because it might be something massively powerful, and could have major effects. And the risk seems very low if it does nothing.
So if you have my passion for supplements, an interest in anti-aging as a field, and the ability to eat $50/month for an unsubstantiated claim, I’d consider checking it out.
Notes
BASIC also contains resveratrol, which is supposedly an anti-aging ingredient in red wine.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers



