Daniel Miessler's Blog, page 125
April 19, 2017
My Thoughts on Elysium BASIC

I’ve been into supplements since my early 20’s. I’ve just always been intrigued by the possibility of being a better version of myself, via whatever means.
A supplement has emerged recently called Elysium BASIC that is generating significant chatter in a few circles, and the reason for that is it’s associated with anti-aging.
It’s quite controversial, but it’s backed by a powerhouse of medical professionals from MIT, Harvard, Stanford, Columbia, etc., who are adding legitimacy to the project.
The FDA is militant about such things. You basically can’t claim to address specific ailments without going through extraordinary hoops, and the process is extensive. Elysium is nowhere close to that, so all they can do is sell a “supplement”.
The pitch is simple: there’s a chemical that is far more plentiful in young people than old people, and BASIC (the name of the supplement) is supposed to significantly increase the amount of that chemical. They did a study on mice and extended their lifespans by 40%, and I believe they’re working on human trials.
I’ve been taking it for a few months now, and some pretty crazy things have happened to me since doing so. Most notably, I have had my lower back pain and a really bad, persistent achilles tendon injury pretty much disappear within the last couple of months.
The problem is that I can’t tie the effect to BASIC directly. I had a break in physical activity for almost three months over the holidays and start of the year due to being sick. Even more significantly, I’ve started taking 5,000 IUs of Vitamin D daily, which is widely considered to be the vitamin to take if you are into supplements. Most people don’t get nearly enough, and my levels were indeed down when I had a checkup at the end of last year.
So my body feels way better. I feel smarter. I feel springy. And it’s great to not have pain when I exercise or go on works.
But Vitamin D is known to be highly associated with immune system health. So what if I had such low Vitamin D levels that my immune system wasn’t able to heal properly? And what if it BASIC had nothing to do with the improvement?
Seems quite possible.
Or maybe it was the BASIC. Or maybe it was some combination, or one or more variables that I haven’t even considered. Either way, I’m continuing to take both right now, and continuing to see benefits. I’ve not the time or patience to conduct an unofficial study where I stop one and then the other and properly record my state at various times.
One of my jobs with this site is to bring you interesting ideas, so this is one. BASIC might be an anti-aging drug that could extend your life by 40%. Or it could be completely ineffective in humans.
I’m taking it because it might be something massively powerful, and could have major effects. And the risk seems very low if it does nothing.
So if you have my exact passion for supplements, an interest in anti-aging as a field, and the ability to eat $50/month for an unsubstantiated claim, I’d consider checking it out.
Notes
BASIC also contains resveratrol, which is supposedly an anti-aging ingredient in red wine.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 17, 2017
Unsupervised Learning: No. 74
This week’s topics: Shadow Brokers, fingerprinting Netflix traffic, Magneto vuln, Juniper advisories, Amazon speaker tech, Facebook’s 100Gbit optical switches, Google Hire, Minecraft currency, a solar-powered water harvester, OWASP Top 10 draft comments, remote SSH, EC2 and NAT firewalls, deep learning is a black box, discovered links, and more…
This is Episode No. 74 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 15 to 30 minute summary.
The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well.
The show is released as a Podcast on iTunes, Overcast, Android, or RSS—and as a Newsletter which you can view and subscribe to here.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 5K subscribers.
Recent Newsletters
04/16/2017 – Daniel’s Unsupervised Learning Newsletter: No. 74
04/09/2017 – Daniel’s Unsupervised Learning Newsletter: No. 73
04/02/2017 – Daniel’s Unsupervised Learning Newsletter: No. 72
03/26/2017 – Daniel’s Unsupervised Learning Newsletter: No. 71
03/19/2017 – Daniel’s Unsupervised Learning Newsletter: No. 70
03/13/2017 – Daniel’s Unsupervised Learning Newsletter: No. 69
03/06/2017 – Daniel’s Unsupervised Learning Newsletter: No. 68
02/27/2017 – Daniel’s Unsupervised Learning Newsletter: No. 67
The podcast and newsletter usually go out on Sundays, so you can catch up on everything early Monday morning.
I hope you enjoy it.

__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 16, 2017
Is Trump Pursuing Innovation at Any Cost?

I’ve been having a crazy thought the last couple of months that I couldn’t quite capture. Then my friend Saša hit me with a similar idea this morning.
It’s kind of scary, and it goes like this:
Trump believes that economic growth will heal all wounds in the country.
He believes it’ll fix our position in the world, add jobs, fix crime, and generally make America great again.
He thinks that once America is feared, respected, and 100% acknowledged as the world leader again, the people will be happy, stop fighting with each other, and we’ll see a period of extreme prosperity.
Because of this belief, he’s basically looked for every single thing he can find that—according to him—is slowing down American innovation and prosperity.
That means the EPA, high taxes, our businesses going overseas, and regulation in general.
It might also mean being involved in an active, innovation-spawning war—not like Iraq or Afghanistan. Something scarier and more visible. Something that spawns companies to innovate in the war space, which will speed up technology coming to the public sector.
In short, he might be removing all regulations and taking us to war because it’d be fantastic for the economy. And he knows that if the economy grows, we start innovating like crazy, and we become the de-facto leaders of the world again, everyone will completely ignore the bad ways we got there.
I’m not saying this is what he’s thinking—or even that if it were, that he’s going about it in the right way. I see several things he’s doing actually harming such a plan.
Gutting the EPA
Ignoring global warming
Defunding planned parenthood
Killing net neutrality
(I’ll probably think of several more)
But then again, maybe those harm the country and planet long-term, but don’t stop such a plan from working.
The Oops Theory
Another possibility is that he’s just a wrecking ball doing all the wrong things for all the wrong reasons, but that those will have the same effects as if he were executing the theory above.
So the economy opens up massively and some good things happen, and he thinks it was because of his deft hand in a thousand different matters, when in fact it was more of an accident than anything else. In short, he creates WWII like conditions through buffoonery rather than by design.
Summary
Trump might be playing a very specific game of aggressive economic growth.
The plan could be to make the U.S. extremely dominant, even if that means removing all safety checks on the economy and taking us to war.
The anticipated result would be growth not seen since the late 40’s and early 50’s, and Americans praising him despite many disliking his methods.
Again, I’m not saying he’s doing this, but in certain lights, at certain angles, it kind of looks that way.
Notes
Thanks to Saša Zdjelar for engaging with me on this topic.
For all the trolls who might accuse me of thinking this is a good idea, I voted for Neil DeGrasse Tyson. Take your hate somewhere else.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
AWS EC2, Default NAT, and Security Groups

One of major differences I’ve noticed after making the switch from Linode to AWS is how network security works.
On Digital Ocean, Linode, and most other VPS hosts, when you get an IP the IP is live on the internet. People can ping it directly, in other words (assuming you allow that in your OS itself), and any service you present to the world can be reached at that address.
No so with EC2 instances.
With EC, your OS has an IP (say on eth0 for example), but that’s not the live IP that’s hosting your services. AWS abstracts that IP behind your public IP, which is completely separate.
Security groups
AWS has a concept called “Security Groups”, which happens to be an abysmally bad name in my opinion.

TABLE 1. — Security Groups in AWS.
It’s a bad name because they’re basically firewall rules.
They control what passes from your public address back to your private one—just like with an enterprise or consumer NAT / firewall system.
Keep in mind, this isn’t the extent of AWS security configuration at all; they have multiple ways of controlling roles, access, permissions, and many other granular areas of security, but those are all named something else.
Security “Groups”, are lists of rules saying what ports are allowed to reach your private IP address, which makes zero sense to me. That name should apply to Roles, or User Groups, or something like that—not to network access control lists.
Anyway, the naming is wonky but the functionality is sound. I love the idea that you could accidentally open up an insecure listening service on your host, and if you hadn’t also passed that port into the box via a Security Group rule (gag), then you still wouldn’t be exposed to the outside world.
I think the reason for this is Amazon knows that developers use AWS to tinker and mess about. And if you aren’t careful you can spin up a bunch of boxes, put some sensitive data on them, open up a port/service, and then maybe forget about them.
Then the first time you hear about it again is when Brian Krebs reaches out to your company for comment because your database is on PasteBin.
So it makes a lot of sense to have this second failsafe of firewall rules, which are fairly locked down by default.
Summary
Most VPS providers give you a single, live IP which is both your local IP and your internet IP.
EC2 gives you two IPs—one local, and one internet—and you have to open/pass traffic back to your internal one using “Security Groups”, which are basically firewall rules.
Notes
I’m not sure the mechanism that’s used by AWS to create this abstraction, i.e., if it’s technically NAT or something else. Either way, it’s definitely performing address translation at the network layer, so I’ll just call it NAT for simplicity’s sake. There are actual NAT Instances that you can set up with AWS as well, though, so there is some distinction they are making.
I’ve generally found AWS to be far superior to the hosts I’ve used in the past, and if you’re thinking about switching I highly recommend it. I recommend EC2 vs. Lightsail, since you get to play with more of the AWS toys that way (but it is more expensive).
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Summary: Sapiens
[ NOTE: These book summaries are designed as captures for what I’ve read, and aren’t necessarily great standalone resources for those who have not read the book. Their purpose is to ensure that I capture what I learn from any given text, so as to avoid realizing years later that I have no idea what it was about or how I benefited from it. ]
Concepts
The cognitive revolution started around 70,000 years ago.
The agricultural revolution around 10,000 years ago.
The scientific revolution around 500 years ago.
The main thing humans do that other animals don’t is organize around ideas that don’t physically exist.
Homo sapiens means wise man.
Humans first evolved in Africa around 2.5 million years ago.
Chimp groups top out at around 50. Humans top out at around 150.
Humans have been living in a dual (real/fantasy) reality since the cognitive revolution.
We think humans were just as smart and capable 30,000 years ago.
Humans domesticated the dog around 15,000 years ago.
It’s much easier now to pass along crap genes.
He says there’s no evidence we’ve become more intelligent over time.
There’s a law that says luxuries become necessities, and then create responsibilities.
There’s an Inca writing system based on knots of different colors and strings for words and numbers.
The whole planet is moving towards one-world culture.
Religion is the third great unifier of humanity. The other two were money and empires.
Monotheism adopts the polytheist concept of patron saints.
Buddhism teaches that we always want more, and that suffering comes directly from craving.
First level chaotic systems don’t react to predictions, second level do.
The scientific revolution started in Europe 500 years ago, and humans have massively improved from it.
The best test of knowledge is not truth, but utility.
Military effort drives technology very quickly.
We used to try to give meaning to death, now we’re working to prevent it.
Capitalism is as much the victor in the scientific revolution as science was.
The European ideology of exploring and studying the world was what made it stand out as special.
The creation of credit spawned the growth of mankind.
The big idea from Wealth of Nations was that increasing profits leads to increasing wealth and prosperity for all.
Capitalism only works when profits are re-invested into creating new things.
All credit is based on the idea that science and technology will continue to improve.
Evolutionary Psychology says basically that we continue to feel the same drives that we had earlier in our evolution.
More people die from suicide and car accidents than war in modern times.
The costs of war continue to increase, so there is less of it. Basically, trade is more lucrative than war, so it’s winning.
Belief in an afterlife gives people meaning in the present.
Buddhism shares the belief that happiness comes from inside the body, not outside.
Evolution is giving way to intelligent design.
In the future we become the gods (cue up Homo Deus)
[ Find my other book summaries here. ]
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 14, 2017
Summary: Homo Deus
[ NOTE: These book summaries are designed as captures for what I’ve read, and aren’t necessarily great standalone resources for those who have not read the book. Their purpose is to ensure that I capture what I learn from any given text, so as to avoid realizing years later that I have no idea what it was about or how I benefited from it. ]
Concepts
Intelligence will decouple from consciousness.
Humanism is the obsession with human experience.
Liberalism is the obsession with human freedom.
Dataism is placing data processing at the center.
Dataism will be the end of humans because computers / AI will be better at data processing than we are.
As humans become transparent to data processing systems (and AI) they will know far better what we should do than we will.
AI will know us better than we know ourselves.
The goal changes from having experiences ourselves, to sharing those experiences and getting them into the collective.
People are going to have to become comfortable with the idea of giving up control to a system that they cannot understand. Already there are many systems that are basically black boxes to us, and that’s the way most everything will go.
People will think they can/will resist the temptation to depend on the system, but when they see how superior the results are, they’ll use it. Plus it’ll happen slowly so that people don’t just switch suddenly from not using it to doing so. It’ll take a couple decades for the tech to mature and for attitudes to change.
Interestingly, young people everywhere, and especially in Asia, are already very much in the Dataist mentality, where they don’t care nearly as much about personal privacy, and care much more about sharing and getting great recommendations from the system.
[ Find my other book summaries here. ]
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 13, 2017
How to Connect to a Local Port on a Remote SSH Server

If you ever have a web server (or other type of server) running on a remote Linux box, and you want to connect to it using your local system, here’s how you do it.
ssh -i ./.ssh/key.pem -N -L 8081:localhost:8000 user@host
This reads as:
Authenticate using a key.
The port you’re listening on on your local system is localhost:8081.
The port you’re listening on on your remote Linux box is localhost:8000.
You’re connecting as user@host.
Then you just go to your browser and browse to: localhost:8081, and you’ll be touching the local port 8000 on the remote box.
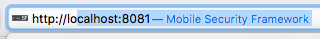
Hope it helps someone.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 11, 2017
Comments on the OWASP Top 10 2017 Draft

I’m going to make some comments about the proposed 2017 update of the flagship OWASP Project—the OWASP Top 10.
Before I do, I just want to say that as a present and former leader of multiple OWASP projects (IoT Security, Mobile Top 10, Game Security Framework, etc.) over the last seven years, I empathize with the difficulty of making these lists. It sucks to work for weeks, months, and sometimes years to get consensus on something, only to have 1,000 internet randos fly by and crap on it. Please accept my comments as constructive criticism rather than hate. I appreciate what you do.
Initial impressions and analysis
So here are some of my thoughts on the new proposed organization of the categories.
I hated A7 initially
My averse reaction to it was immediate, negative, and strong. It’s called Insufficient Attack Protection, which struck me as just a horrible name. The reason for this I’ll explain more in my next point. But then I read the full page description on it, and I definitely see where they were going with it.
It’s basically detection and response (which includes patching), which I think is a phenomenal addition to the list. I do dislike the name, though. So I started thinking about better names, as I’ve done a million times in my various OWASP projects, and quickly realized all the better names are four to five words long.
Insufficient Detection and Response
Lack of Detection, Response, and Patching
Etc.
So they probably battled over this point for days or weeks or months, only to arrive at a not great solution of, “Insufficient Attack Protection”. It’s a noble attempt, although I might still try to convince them still to change it to, Insufficient Detection / Response.
Anyway, short version is I love the category but really dislike the name.
A more fundamental problem
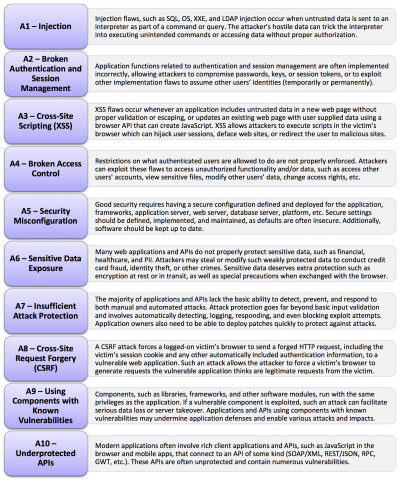
TABLE 1. — The current proposed 2017 list (April 2017).
This brings me to the reason I moved away from “Top 10” for the OWASP IoT Security Project. With that project, the Mobile Security Project, and virtually every other list-based effort that I’ve encountered, I’ve seen the project team run into the same wall.
They’re mixing different types of security issues into a single list.
What we’ve done with these different OWASP projects is collect different forms of “bad things”, which can include any of the following:
Vulnerabilities
Threats
Risks
Miscellaneous Bad Hombres
Etc.
The differences between these are quite important, and blending them all together into a single list can be problematic. But the biggest problem is when people on the project team don’t agree on the definitions, their differences, or whether or not it’s ok to mix them in a single list.
So let me just ask you, dear reader: What is the OWASP Top 10 a list of?
Is it a list of vulnerabilities? Not really. Injection isn’t a vulnerability; it’s a category of vulnerability. Same with Auth and Session Management, Access Control, Security Misconfiguration, etc. Then you have XSS and CSRF that are individual vulns.
So we have a list of 10 somethings—and on that list we have a mix of parents and children, containers and contents, buckets and water. That kills me. Always has. Especially since people don’t usually realize it’s happening during the discussion, and even when they do we can’t agree on terms.
So then we have Underprotected APIs. That’s not even a category. And it’s definitely not a vulnerability. It’s like a…thing. And I love it actually. I think it’s a good item to be on the list. But what is it? And does it belong on this list?
Hard to say.
My thoughts on OWASP lists
So here are some of the ideas I’ve had regarding this composite listing problem.
I think we need more discreet and granular lists that clearly indicate what they are and who they’re for. In the IoT Security project we’re doing this by having more sub-projects within the project. We’re trying to break vulnerabilities into vulnerabilities, attack surfaces into attack surfaces, risks into risks, etc. I don’t want to cross the streams. I’ve not solved the problem, but that’s what we’re working towards.
I think the OWASP Top 10 could benefit greatly be calling itself what it is—a list of things to consider and avoid when building web applications. That’s not pretty. It’s not catchy. It doesn’t sound as cool as “Top 10 Vulnerabilities”. But it’s more honest. If it’s functional to make it a composite list, then lets do it. But let’s not lie to ourselves about it.
Perhaps it could be the Top 10 Risks—if we were to argue that each item includes probability and impact not just within each vulnerability but in relation to each other. In other words, the project team says something like:
We the OWASP Top 10 Team have studied x amount of data and have ranked not only the prevalence but the impact of all these issues as they relate to overall web application risk. The list is a composite of vulnerabilities, categories of vulnerabilities, and considerations, and we’ve determined that this is the order in which you should work to prevent these types of issues within your own web applications.
I don’t know that they are saying that, or that they can based on the data they have considered, or that they would even want to. Is the number actually a rank of priority, or is it just a designation so you can keep track? Not everyone knows the answer to that, and it should be more clear.
Summary
This is a hard problem, and I applaud the work that has been done.
The TL;DR here for me is that I think this is a great list of things for developers to avoid doing in their own applications, but I’m not happy with the seemingly confused way we get there. Not just in this project, but in all similar projects. We’re just throwing things in these lists with no regard for taxonomy, hierarchy, or any other structure. That would be ok with me if we were explicit about that, but I don’t think we are.
I think more clarity on said structure could help significantly.
Hopefully my comments are taken with the love that produced them, and can lead to some additional conversation and/or clarity around the structure of not just this list, but other OWASP projects going forward.
Happy to be part of that conversation if anyone wants to engage.
Notes
Jeremiah Grossman had a great suggestion, which was “Lack of Web Asset Inventory”, or something similar. I loved it, but the issue is that the OWASP lists are supposed to be for makers and breakers primarily (at least as I understand the history and current zeitgeist), and the lack of inventory point—while powerful—is clearly an organizational issue, not an issue with a single application or system. For that reason I’m not convinced that it fits in the current form of OWASP Top 10. But perhaps in a better version, or in an orthogonal project.
Speaking of OWASP projects, I’ll be at the OWASP Summit in London in June. If you’re going, let’s meet up while we’re there.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
On Forcibly Removing People From Your Private Business

There’s been another incident with United this week. This time they created their own overselling problem, let people actually board the plane and get seated, and then told them that four people had to get off the plane because employees needed to fly.
Nobody volunteered to give up their seat—even after being offered increasing sums of money—so they had the system pick someone at random. That person was a doctor and he refused to get up, so they called the police and had him forcibly removed.
It was ugly. He tried to grab onto the seats to avoid being pulled out by the police, and ended up being knocked unconscious and dragged from the plane with a bloody mouth.
Analysis
I took massive heat on Twitter when I posted this about the incident.
CRAZY IDEA: If you refuse to move when a flight attendant tells you to get up, you should expect bad things to happen.
— ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ (@DanielMiessler) April 10, 2017
It should have been obvious that I didn’t agree with United on this, or with the decision to forcibly remove someone for their own damn mistake. But that evidently wasn’t obvious, and people basically accused me of supporting the United decision, and violence in general. It was strange, but that’s the danger of expressing opinions on sensitive topics in 140 characters.
Anyway, here’s my overall analysis of the situation, after thinking about it for part of a day.
Airplanes are private property belonging to the airline that owns them.
When you’re on private property, the owner can ask you to leave at any time, for any reason.
If you don’t leave, they can call the police to remove you.
If you then resist the police, in this police-state climate, the odds are very good that you’re going to get hurt.
This truth is significantly magnified on airplanes, because of 9/11.
That being said, if you’re dumb enough as a private business to call the cops and have someone forcibly removed from your business, for your own mistake, then you should expect the sky to fall on you as a result.
You have every right to eject people out of your business, using the over-enthusiastic police, for any reason at all, but we the people have the right to avoid doing business with you ever again because of your stupidity and cruelty.
This seems to be precisely what happened.
United caused their own problem here due to overbooking as a policy and then letting people get fully seated before ejecting them. That was heroic-level stupidity, and it will justifiably harm their business for a long time to come.
But the passenger was arguably just as stupid. When a group of large cops walk up to you, and tell you to get out of your chair—on private property—it doesn’t matter who’s right or who’s wrong at that point. You can sort that out later, with your checkbook or with a lawyer. But while they’re telling you to get up, it’s time to get up.
Police are massively over-militarized in this country, and far too eager to use force. You combine that with being on an airplane, and you have a completely predictable situation if you grab the furniture and try to resist them on private property.
Nothing about this should be surprising at this point. United deserves every bit of the fallout they’re getting, and the doctor should have moved when the police got there—not because of how police should behave, but because of how we know they do behave.
There’s a natural tendency when we hear about an incident like this to find exactly one (1) cause for the problem. But sometimes there are many causes, and this is one of those times. United started everything in motion, and the passenger chose to grab the furniture and scream when the cops showed up instead of leaving the plane and taking action afterwards.
They both should have known better.
Notes
Keep in mind I’m not a lawyer, so maybe there’s some subtlety to commercial airplanes that makes them more like public property. But I don’t see it myself. It seems clear to me that the plane is the property of that airline, and that they can make almost any decision they want to about who can fly and who cannot, and then back that decision up with police. That, however, is a double-edged sword, because if they’re dumb enough to call the police to remove someone for THEIR MISTAKE, then they will pay the price in the market, which is precisely what’s happening.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
April 10, 2017
Unsupervised Learning: No. 73
This week’s topics: Word 0-day, BrickerBot, iOS GIF, Russian arrested, Tizen, OilRig, APT10 MSPs, Dallas sirens, ATM drilling, Watson golf, Uber Italy, AI memory, links, projects, and more…
This is Episode No. 73 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 15 to 30 minute summary.
The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well.
The show is released as a Podcast on iTunes, Overcast, Android, or RSS—and as a Newsletter which you can view and subscribe to here.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 5K subscribers.
Recent Newsletters
04/09/2017 – Daniel’s Unsupervised Learning Newsletter: No. 73
04/02/2017 – Daniel’s Unsupervised Learning Newsletter: No. 72
03/26/2017 – Daniel’s Unsupervised Learning Newsletter: No. 71
03/19/2017 – Daniel’s Unsupervised Learning Newsletter: No. 70
03/13/2017 – Daniel’s Unsupervised Learning Newsletter: No. 69
03/06/2017 – Daniel’s Unsupervised Learning Newsletter: No. 68
02/27/2017 – Daniel’s Unsupervised Learning Newsletter: No. 67
02/21/2017 – Daniel’s Unsupervised Learning Newsletter: No. 66
02/13/2017 – Daniel’s Unsupervised Learning Newsletter: No. 65
02/06/2017 – Daniel’s Unsupervised Learning Newsletter: No. 64
02/06/2017 – Daniel’s Unsupervised Learning Newsletter: No. 63
The podcast and newsletter usually go out on Sundays, so you can catch up on everything early Monday morning.
I hope you enjoy it.

__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers





