Daniel Miessler's Blog, page 119
August 4, 2017
My Friend and his Girl

I have a friend who I’ve always wished I was closer to. He is one of the kindest and happiest people I know.
He’s like an ancient power source that produces hugs, smiles, and laughter.
He’s also famously popular with women. Everywhere I see him he’s surrounded by multiple girls tying to learn more about him. It’s like holds court with the best and most beautiful wherever he goes, except the court is based on having a good time instead of being pretentious.
And he likes to party. He brings it with him. As soon as he shows up, that’s where the alcohol is, that’s where the women are, and everyone immediately starts having one of the best times of their lives.
Then he met a girl.
This girl pulled him from that world. She changed him. She showed him what it meant to be a better person, and he became one just by being near her.
I only heard about this from a distance. Through other friends.
He met someone. Someone who changed him.
I was going to see him at EDC this year, but he didn’t come. I was going to text him and give him a hard time about why he wasn’t there, but decided against it. He probably regretted not coming and would only feel worse if I pinged him.
I’m glad I didn’t.
He told me that they had tickets to EDC, and that they planned to surprise me and my friend Jason there. He was so fucking happy that we’d finally get to meet her.
But he didn’t come, and we didn’t get to meet her. Because she’s gone.
The woman who changed him so completely. The woman who had rebuilt him from the inside out. She came into his life in an instant, and then left in another.
And now he is devastated.
I just talked to him and tried to give him the best advice I could for dealing with something where advice cannot matter.
I wish I had met her. I wish I had known this beautiful person who has affected my friend in this way. The woman who has touched and improved his life in such a short time. I am so sad that I din’t meet her.
He’s been working on ways to continue propagating her energy in this universe. I asked him to try to explain what she was. What she was to him. I want to know this. I want to experience it. For him, and for her.
I am here if you need me, my friend, and I am so sorry for what you have lost.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
On Giving Advice to Friends
Free Will and Punishment
An Atheist Debate Reference
Ron Paul is Seriously Flawed as a Candidate; We’re Just So in Love With Him That We’re Not Paying Attention
Ron Paul’s Flaws as Seen by One Die-Hard Supporter
August 1, 2017
How I Just Saved $5,500 on my EC2 Bill in 5 Minutes by Switching to a Reserved Instance
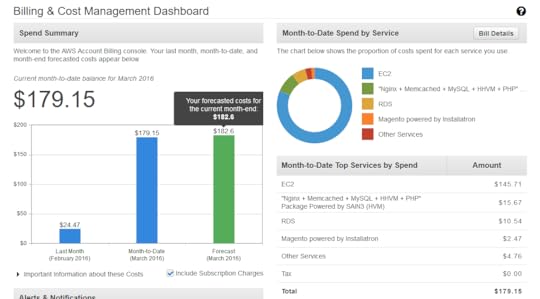
I just lowered my Amazon EC2 bill, over 3 years, from $6,120 to $583. Or, put another way, I just saved myself $5,500 dollars.
Here’s how it happened. I was in Vegas this week for BlackHat / DEFCON and was hanging with my friend Saša Zdjelar in the hotel and messing with EC2 (as one does in Vegas).
We were talking about how Amazon basically releases new stuff every 12 minutes, and that it’s so hard to keep up with all of the features. And at one point he says,
Hey, have you seen these Reserved Instances?
I say no. Or maybe. Or I think so. Because I’m not sure which kind Reserved instances actually are. Amazon is famously bad at naming things, and I can’t remember if those are the ones where you have dedicated hosting, or if it’s the kind where you pay less to get leftover resources from other peoples’ boxes.
Turns out it’s neither. It’s not even a type of instance—it’s a type of billing.
Basically, it’s for people who plan on running a specific size of EC2 instance, in a specific availability zone, for an extended period of time. Say from 12 to 36 months.
So if you build and destroy your boxen every 37 minutes or something this isn’t for those systems. It’s for systems that are relatively static, like a personal or company web server. In my case I host this site on EC2, and I have a box dedicated for that purpose.
I was paying around $160 a month for my T2.Medium with lots of options enabled. I just took that to $583 over 3 years, which is around $24 dollars a month. If this holds true it’s basically gone from the most expensive host I’ve ever had to the least expensive.
How to migrate to the Reserved Model
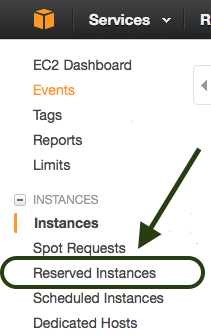
The way to get to Reserved billing is counterintuitive.
Basically, you have to pretend that you’re buying a new instance, of the Reserved type, with the exact same attributes of the one you want to convert. Upon making the purchase you will have converted the other one.
It’s gross, but it works.
Navigate to https://console.aws.amazon.com/ec2/v2/home.
Click on Reserved Instances.
Select an instance that matches the one you want to replace the billing on, for both instance type/size and instance availability zone. For example, mine was T2.Medium and US-East-1a.
Make the purchase.
So what then happens is that Amazon finds your running On Demand instance and converts it to a Reserved instance. And now if you go into billing you should see that reflected.
And more importantly, if you go into your instances dashboard you’ll just see the same ones you had before. You haven’t actually purchased a new box; you’ve just converted the one that matched those specs from On Demand to Reserved.
For anyone running a box in EC2 that isn’t likely to change in size or location over one to three years, I highly recommend you check out Reserved Instances. They could save you a massive amount of money, just like it did for me.
Notes
Yes, the title is clickbaity. I try to avoid such tactics with my site, but in this case I think it’s warranted because 1) it literally describes what happened, and 2) it would likely to be ignored if I wasn’t that clear about the benefit.
Thanks to Sasa for repeatedly insisting I look at these things. I had become jaded against changing instance types because of the damage to my brain from Amazon Naming Trauma (ANT), and he helped me get through it.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
A vim Tutorial and Primer
Information Security Concepts
The Ultimate Speed Guide for WordPress on NGINX
A Security-focused HTTP Primer
A DNS Primer
I Just Saved $5,500 on my EC2 Bill in 5 Minutes by Switching to a Reserved Instance

I just lowered my Amazon EC2 bill, over 3 years, from $6,120 to $583. Or, put another way, I just saved myself $5,500 dollars.
Here’s how it happened. I was in Vegas this week for BlackHat / DEFCON and was hanging with my friend Saša Zdjelar in the hotel and messing with EC2 (as one does in Vegas).
We were talking about how Amazon basically releases new stuff ever 12 minutes, and that it’s so hard to keep up with all of the features. And at one point he says,
Hey, have you seen these Reserved Instances?
I say no. Or maybe. Or I think so. Because I’m not sure which kind Reserved instances actually are. Amazon is famously bad at naming things, and I can’t remember if those are the ones where you have dedicated hosting, or if it’s the kind where you pay less to get leftover resources from other peoples’ boxes.
Turns out it’s neither. It’s not even a type of instance—it’s a type of billing.
Basically, it’s for people who plan on running a specific size of EC2 instance, in a specific availability zone, for an extended period of time. Say from 12 to 36 months.
So if you build and destroy your boxen every 37 minutes or something this isn’t for those systems. It’s for systems that are relatively static, like a personal or company web server. In my case I host this site on EC2, and I have a box dedicated for that purpose.
I was paying around $160 a month for my T2.Medium with lots of options enabled. I just took that to $583 over 3 years, which is around $24 dollars a month. If this holds true it’s basically gone from the most expensive host I’ve ever had to the least expensive.
How to migrate to the Reserved Model

The way to get to Reserved billing is counterintuitive.
Basically, you have to pretend that you’re buying a new instance, of the Reserved type, with the exact same attributes of the one you want to convert. Upon making the purchase you will have converted the other one.
It’s gross, but it works.
Navigate to https://console.aws.amazon.com/ec2/v2/home.
Click on Reserved Instances.
Select an instance that matches the one you want to replace the billing on, for both instance type/size and instance availability zone. For example, mine was T2.Medium and US-East-1a.
Make the purchase.
So what then happens is that Amazon finds your running On Demand instance and converts it to a Reserved instance. And now if you go into billing you should see that reflected.
And more importantly, if you go into your instances dashboard you’ll just see the same ones you had before. You haven’t actually purchased a new box; you’ve just converted the one that matched those specs from On Demand to Reserved.
For anyone running a box in EC2 that isn’t likely to change in size or location over one to three years, I highly recommend you check out Reserved Instances. They could save you a massive amount of money, just like it did for me.
Notes
Yes, the title is clickbaity. I try to avoid such tactics with my site, but in this case I think it’s warranted because 1) it literally describes what happened, and 2) it would likely to be ignored if I wasn’t that clear about the benefit.
Thanks to Sasa for repeatedly insisting I look at these things. I had become jaded against changing instance types because of the damage to my brain from Amazon Naming Trauma (ANT), and he helped me get through it.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
A DNS Primer
The Shape of the Coming Global Dystopia
A vim Tutorial and Primer
Information Security Concepts
A tcpdump Tutorial and Primer with Examples
July 19, 2017
My Thoughts on the DEFCON Cancellation Meme
If you’ve not seen it yet, there’s a meme going around saying DEFCON is cancelled. It seemed to be purely a good fun troll, but it’s been gaining in popularity over the last couple of weeks.
Then this morning I found what appears to be the official meme manifesto, and it made me wince a bit. Kind of like something good that’s slightly turned.
Let me try to explain.
First, I think the piece is trying to do multiple things at the same time.
I think it’s trying to be funny, which it is.
It’s trying to troll some noobs, which it does.
And finally, it’s trying to say some serious things about the industry, which is where I think it lands squarely in the Uncanny Valley.

The Uncanny Valley is where something like a CG character is almost perfect but is off just enough to cause alarm (see Tom Hanks above). And, importantly, if it were less perfect—in a movie the character would be more cartoony, and in a piece of satire it would be more obviously so—it would be accepted without issue. But because it sits right on the line it causes unease. And that’s precisely the sensation I got.
A few points from the text:
I believe that we are in a post-hacker world. We still need innovative security researchers but we need professionals. We need to shed the “hacker” persona that is denigrating us. We should strive to be professionals, making the Internet a safer place rather than exposing vulnerabilities that can be leveraged by criminals and terrorists.
This one is a clear attack on those who think it’s immature to pursue true research and disclose vulnerabilities, and I absolutely agree with the point. There are nuances of course, but in general this is not something that the community benefits by giving up.
It is my belief that attendance at amateur conferences such as ShmooCon, Summercom, Toorcon, HOPE and even CCC will soon begin to dwindle. As current attendees mature they will become the next generation of security professionals, not hackers. What I’ve said is probably disturbing to some of you, but it is our current reality.
This is also a solid and deeply cutting point, saying that too many professional types have lost the curiosity and true hacker nature.
Professionals have professional credentials. If you want to participate in the security industry, you should obtain the appropriate certifications. ISC2, SANS, EC-Council and many vendors offer well regarded security certifications.
This one is a bit ‘on the nose’, but entertaining.
The next two sections are where I started feeling the Spidey Sense go off. On the national security topic I get the point of opposing blind trust in the government, but I worry it’s hinting at the position that anything under the guise of NATSEC is bad. That’s unhelpful.
Then it talks about privacy, and makes fun of the notion that nothing should be considered private. This is a hard one because I agree with the straw man that they’re knocking over, which is the “if you’ve got nothing to hide” argument. 100% agree.
But I also think privacy is going away, and that it is inevitable. This is because of the future of technology, data exchange, society, etc.—not because christian republicans are awesome, and ‘Merica. They’re two separate forces. I oppose one, and I believe the other to be inevitable. The piece conflates these two in an overly simplistic way.
Then we get this vibe as well. It’s actually all throughout the piece, but it’s most pronounced here.
I plan on writing a book covering many topics during my growth form a hacker to a security professional. Feel free to approach me at Black Hat or other conferences to discuss these issues.
The “professional” bashing is the weakest part of the piece, and it’s what produced the Uncanny Valley feel for me.
It’s basically taking real, solid points, making them well and in a funny way, and then at the same time bashing hackers and/or wannabes who are transitioning to being professionals.
This is non-binary.
There are many hackers who become security professionals
There are many non-hackers who pretend to be hackers and then become security professionals
There are many non-hackers who don’t pretend to be hackers and become security professionals
There are many noobs who are neither, and who are trying to become one or both
I don’t get the professional hate, or the conflation of complex topics. It’s not useful.
National security is a thing, and it needs good security people to help.
You can’t blindly trust the government, because ‘Merica.
You can’t give up privacy because some Republican told you you’re a criminal if you don’t.
It’s ok to be a wild hacker in your younger years and then become a professional later in life.
Becoming a professional doesn’t have to mean compromising your values.
If these are in conflict for you it’s because you see the world too simplistically. The world is messy, and it requires nuanced and constant re-evalutation to navigate practicality while remaining true to core principals you believe in.
I wish things were as simple as this manifesto makes them out to be. It was easier for me when they were. But that’s the Fox News approach. It’s compartmentalizing everything into neat boxes so that you know who’s a real hacker, who’s a sell-out, that the government is bad, etc.
I get it. It’s clean. But reality isn’t clean. And true hackers figure out how to be good, in a dirty world, as a professional.
I agree with 90% of what’s being said here, and trolling noobs should never go out of style, but we shouldn’t pretend that the world is simple, because it isn’t.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
How to Build a Successful Information Security Career
A Guide to Information Security Certifications
The Difference Between a Programmer, a Hacker, and a Developer
Information Security Concepts
Web Application Security Testing Resources
July 15, 2017
When Do You Step in to Stop Poor Countries Destroying The World’s Rain Forest?

Brazil just opened 860,000 acres of the Amazon rain forest to pilfering by big corporations. It’s been happening for a long time, but the speed has dramatically increased in recent years.
This will be unpopular, but the Amazon is not a national treasure that Brazil has the right to destroy. It’s not like we in the U.S. decided to destroy Mount Rushmore because we want the rock. There’s plenty of rock elsewhere in the world.
Not so with the rain forest. It’s a finite resource, and it’s being pissed away because Brazil is poverty stricken.
To me this is like a 6-year-old agreeing to burn the only cure for cancer (that he found in his backyard) for $10 so he can buy a Coca-cola and a family size bag of M&Ms.
Yes, I’m aware of how horrible that sounds.
I see both extremes. One is that you can’t just walk into a sovereign country and tell them how to treat their natural resources ever time you disagree with their policies. Especially not if you’re the U.S., which is basically the primary imperial power in the world today, and a country that uses (and wastes) massive amounts of natural resources itself.
The other extreme is that you don’t want to sit and watch the cure for cancer (an apt analogy, as it turns out) disappear on the account of political correctness or political sensitivities.
The Amazon is a literal source of hundreds of our medicines, and the more we lose of it the more new medical breakthroughs will be delayed or never discovered at all.
That’s not a Brazil problem. That’s a humanity problem.
So the question is, since we know you can’t just be the U.S. and tell them to stop, and we also can’t sit back and watch them destroy a global treasure because they are poor…when do we step in?
And who is “we”?
I think it really needs to be the world, not just the U.S., or Europe, or whoever. It’s got to be a large group that represents the world. The U.N. or something.
Maybe they need to buy it to preserve it. And maybe that technique should be used in other countries as well. The U.S. is killing off the only supply of something? The U.N. buys it and prohibits its destruction. And so on.
All I know for sure is that both extremes are bad. Interdiction reeks of imperialism, especially if it comes from the U.S. or Europe. And non-action is impotence and cowardice at a criminal scale.
sound of saws buzzing and the clock ticking
Notes
Image from Getty.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Cancer is an Age Problem
My Response to Sam Harris vs. Very Bad Wizards on Free Will
An Evil Speech Obama Gave to Kids
The World Needs a Federation
Concepts
Universal Income and Population Control Are Inexorably Tied

A lot of people—me included—are excited about the concept of Universal Basic Income. This is the idea of eliminating all or most of the need for someone to struggle to survive, thus giving them time to dedicate to higher-level efforts like art, science, etc.
A basic example would be someone who wishes they could be a painter, or a musician, or an architect, but they can’t afford to go to school or to practice their art because of their main bills. Basic Income would provide an amount of money for free to them, and every other citizen, so that they didn’t have to worry about basic housing and food costs, so that they were free to pursue their passions.
The consensus among many experts is that this isn’t just a nice idea, but that it’s about to be essential. The problem is that there are too many people and the jobs are getting automated away. So we need to be able to create value in ways other than performing basic tasks like transporting things from a to be, or doing basic management tasks that can be done better by computers.
Here’s the problem in the simplest form:
More and more people.
Fewer and fewer jobs.
Something has to give.
Basic Income is just one approach, but it seems most realistic of the numerous bad options. And even with Basic Income this doesn’t solve the issue completely. You still have other questions to answer:
Where is the money coming from if fewer and fewer people are creating value, and the amount of Basic Income required keeps going up?
How can we be sure that those receiving the Basic Income will use their spare cycles to create new value?
Can we be sure that new types of jobs will be created once computers and automation take most existing ones? It’s not guaranteed to go down the same way it did in previous industrial revolutions.
The numbers game
One thing that always troubled me about Basic Income is the numbers.
Some percentage of the population will use the income to simply do nothing, and then to reproduce. Another percentage of the population will create a lot of new value and also reproduce. And another group will create value and not reproduce.
But what percentages will be in each? It matters a lot.
If we have some mixes we get a new economy based on new value, and life is good. And if we have another mix the system will implode under its own weight.
But let’s say that we’re watching it become bottom-heavy and untenable. And the issue is too many people reproducing and not producing value.
What do you do?
That is the single most important question around Basic Income in my opinion. Even more important than whether new types of value can be created or not. It’s a question of numbers. How few people can support how many, and for how long?
There are a few sliders in this equation.
Number of value producers.
Amount of new value created.
Amount of people consuming and not producing.
The speed of reproduction of each group.
Put these into a spreadsheet and mess with the numbers. I’m not qualified to do so, but I am guessing that the numbers are pretty scary at the extremes.
To me this leads to the following prediction:
Basic income will happen, simply because there’s no better alternative.
The numbers involved will inevitably lead to calls for population control.
There will be proposals to limit children of people who only have basic income, income requirements for having kids over a certain number, rating the value contributed to society for additional kids, etc.
I don’t see how this won’t happen.
Whenever you think of Basic Income, keep this in mind. It’s a great idea, but there’s a blade on the handle.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Daniel Dennett is Wrong About Free Will
An Encoding Primer
Whose Responsibility is it to Provide Jobs to People?
How to Build a Successful Information Security Career
Ideas
July 14, 2017
The Universal Arc

I’m creating an EDM album. Well, designing one. I’m creating the concept, the theme, the title, the song titles, the feel of each song, the type of music I want for each, the type of lyrics, etc.
But I’m likely going to get someone else to create the music because it’s not something I have time to learn right now.
So here’s the concept.
Album
The album is called Universal Arc, and it’s about the journey of life within this universe. Not just human life, but including human life. Any civilization, on any planet, in any galaxy, throughout the universe. The “arc” refers to the story arc, which typically goes from primordial soup, to surviving as animals, to breaking away from the animals, to becoming intellectual, to avoiding self-destruction, to escaping the solar system, and finally merging with other life forms in the universe. The endgame is to avoid the heat death of the universe as one or more super-intelligences trapped within a dying world.
The songs in the album correspond to the phases in this journey, and convey the emotions thereof. So the song titles should tell you where you are in the arc, and each song should have the feel of that phase.
Songs
The songs in the album will correspond to phases in life evolution and/or the struggles that are faced in that phase. Current song names are listed below, along with the music type and possible lyrical content or themes.
Primordial
Style: Ambient
Musical and Lyrical Themes: organization, gurgling, chaos, disorder, time, eons, millions of years, birth
Animal
Style: Drum and Bass
Musical and Lyrical Themes: animal, tribal, energy, fighting, raw, savage, killing, sex, competition
Dawn of the Intellect
Style: Ambient, Minimal, House
Musical and Lyrical Themes: positivity, rebirth, intellect, intelligence, formulas, science, logic, death of religion
Self-destruction
Style: Hardcore, Hardstyle
Musical and Lyrical Themes: death, biological warfare, meteor strikes, global warming, nuclear holocaust
Post-human
Style: Deep House, Minimal, Trance
Musical and Lyrical Themes: super-intelligence, experience is everything, virtual fantasy worlds, vr is reality, arbitrary distinctions between fantasy and reality, hedonism, identity, merging with the collective
New Home
Style: Minimal, Ambient
Musical and Lyrical Themes: search, loneliness, fear, hope, desperation, silence, deep space, missing home
Others
Style: Drum and Bass, House, Deep House
Musical and Lyrical Themes: avoiding conflict with others, finding friends, battles, merging with other super-intelligences, surviving as a collective
Entropy / Escape
Style: Ambient, Minimal, House
Musical and Lyrical Themes: sadness, slow death, eternal sleep, fade to blackness, death of the universe, silence, silence, a tiny hope, an opening, ESCAPE, a path to another universe, a new beginning
Notes: This song is in two parts. It starts off about the death of the universe, and as the song runs and fades out at around 8-10 minutes, it just stays super minimal for minutes. Then, after some time, Escape starts, and it becomes about leaving this universe through a wormhole or whatever method to find another universe to start anew.
Notes
I will have someone actually create art for this, so the image above isn’t permanent.
I appear to have already found a friend to work with on this, so I’m extremely excited. I’ll keep updating the song names and concepts as time goes on.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
The Life or Death of Harry Potter
Free Will and the Absurdist Chasm
An Atheist Debate Reference
The Two-lever Argument Against Free Will
The Grand Music Project
Good App Features Become OS Features
People are really upset that 1Password appears to be forcing users to store their password data in the cloud.
Whenever stories like this come around I get asked what I use for passwords, and since I use lots of different things I simply respond with what I believe to be a truth about tech features.
If something is good enough to spawn an entire space within applications, such as location sharing, password storage, live video streaming, etc.—expect that functionality to come to the operating systems as well.
Put another way, the operating system is where most core functionality will ultimately reside, and applications are basically testing grounds for those capabilities.
I think this is an interesting way to think about things if you’re a company looking to get into applications. You have to ask yourself:
How long will this functionality exist as an application vs. being folded into the operating systems?
I think there are exceptions to this rule, or perhaps there are types of application functionality that will simply take too long to absorb. Core applications like Facebook, Twitter, AirBnB, Reddit, etc.—these all seem pretty resistant to collapse into the OS.
But why is that?
I’m thinking in realtime here, but perhaps it’s because those are really interfaces to user-generated content, and displaying such content in new and interesting ways is something that moves too quickly to integrate into the OS.
This is in contrast to something like navigation, finding your friends, or checking the weather, where this type of functionality is part of regular, natural human workflows.
That’s perhaps not a foundational distinction. I’ll do more thinking on it.
But what does seem clear is that there are not many applications that people use on a regular basis. The idea of making an app and becoming rich is a bit strange at this point, and the reason for that is that people really only use a few applications in their day to day lives.
If people only use, say, ten applications during the course of a week (not counting the default ones in their OS), then it’s going to be extremely difficult to either bump one of those ten or become the eleventh.
Perhaps we can imagine these as 25 core workflows, which are divided between applications and the operating system. And maybe the question turns into which workflows go to apps vs. the OS.
But the key point here is that it appears to be a bit of a zero-sum game. There is a finite number of workflows that a given human will have, and that humans will have on average. And both apps and operating systems will divide these up.
So as an application developer I think it’s important to have that number of workflows and the allocation thereof as a key data point for all decisions.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Multi-dimensional Vulnerability Hierarchies
Web Application Security Testing Resources
Ideas
An ICS/SCADA Primer
An Information Security Metrics Primer
July 10, 2017
Unsupervised Learning: No. 85
This week’s topics: The future of security testing, nuclear plant hacks, Android malware, satellite decryption, wildcard certs, military encryption, gsuite protections, WWE S3, tesla 3, jawbone, drone hacking, mental aging, millionare GPAs, discovery, recommendations, the weekly aphorism, and more…
This is Episode No. 85 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 15 to 30 minute summary.
The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well.
The show is released as a Podcast on iTunes, Overcast, Android, or RSS—and as a Newsletter which you can subscribe to and get previous editions of here.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 10K subscribers.
The podcast and newsletter usually go out on Sundays, so you can catch up on everything early Monday morning.
I hope you enjoy it.

__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Unsupervised Learning: No. 78
Unsupervised Learning: No. 76
Unsupervised Learning: No. 73
Unsupervised Learning: No. 75
Unsupervised Learning: No. 71
July 9, 2017
Calligraphy Class

We did a calligraphy class today, and I feel an obsession coming on.
Typography, calligraphy, writing utensils—these are pure beauty to me.
This was a short beginner course, and we’re going to sign up for the intermediate one as well, which covers things like building your own “font”, using digital tools like Adobe Procreate to practice, etc.
It’s also extraordinarily relaxing to do calligraphy.
Really enjoyed it. 13/10. Would recommend.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
How To Keep Track Of Your Book Collection
A tcpdump Tutorial and Primer with Examples
Security: Implementing A Secure And Usable Internet Password Scheme
The Relationship Between Horsepower, Torque, and Acceleration
A tar Primer
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers



