Daniel Miessler's Blog, page 115
September 26, 2017
Why Biometric Data Breaches Won’t Require You To Change Your Body

Image by burak kostak
I hear a lot of people in InfoSec say things like,
I guess if my biometrics get hacked I’ll just change my face! Or, New Security Best Practice—Change face, eyes, and fingerprints every 90 days!
These are funny, but it’s important to realize that there’s a difference between you and pictures of you.
Imagine, for example, that there’s a security guard at the TSA that authenticates people using a comparison of images from a stick figure camera.

from XKCD
If you look at these pictures above, taken by Randall Munroe with that camera, you can see differences in the people, and those differences are used to authenticate them. So if the TSA guard knows that Philip is the guy with the beret, he can either let him in, or not.
These pictures could be out there in the world, circulated in airports, and even read by automated scanners to determine who to let in or not let in, but we wouldn’t be tempted to say that these pictures have stolen us in some foundational way.
In the case of the stick figure camera this is obvious because the stick figure image of Philip that it makes is just a a feeble abstraction of the real Philip.
The part a lot of people are missing is that modern biometrics are just stick figure cameras with better resolution.
They don’t capture eyes, or voices, or fingerprints. What they do is make crude diagrams of those things.

But wait, you say. Stick figure diagrams can’t confuse humans into thinking they’re a real person! And you can’t log into an iPhone with a stick figure diagram of a fingerprint, while you can with TouchID data.
That’s true, and that brings us to the second piece of this idea: it’s the combination of the diagram and the reader that matters.
Humans don’t authenticate other peoples’ faces based on reality either. They actually create a representation in the brain of a person they’re viewing, as perceived by the eyes, the brain, etc., which is turned into a concept.
It’s just another drawing. The original, eye-based kind.
Then the reader—going back hundreds of thousands of years—was also the human eye (and brain), and that completed the pair: the eye takes the image, stores it as a concept, and then the eye reads it and checks for a match.
With modern biometrics we have a different pair: a machine takes the diagram, and a machine reads it to see if it matches. But it’s still just a representation of the thing and not the thing itself.
Why does this matter?
Because to change the authentication system you just have to change either the image or the reader. The object itself is largely irrelevant.
The more complexity you have in a stick figure drawing, the more choices you actually are making about what to sample and how to store that representation. With a system like TouchID there was a lot of data there, and a lot of choices about how to capture it (sensor), manipulate it, and then store it (algorithm). With FaceID there’s far more.
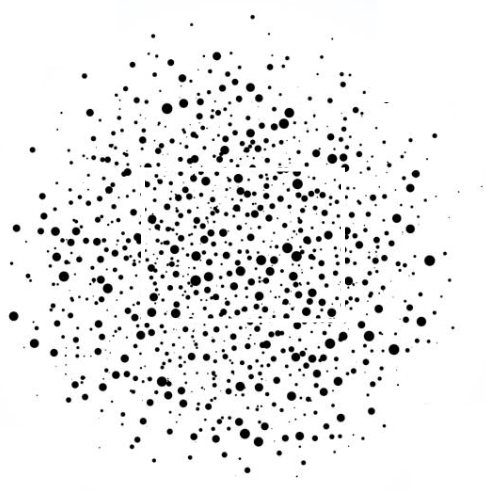
Imagine a representation of a fingerprint in a biometric system as something like a randomly situated, three-dimensional matrix of dots the size of a basketball. As you rotate this ball around in your hands, with all the various sizes of the dots, and distances between them, that’s the fingerprint. That’s your stick figure picture.
And if you adjust the algorithm for capture of the image, or the algorithm for how it’s saved into the 3D array of dots—in any way— well, now you have a completely different image.
And most importantly, you now have to update all your readers to understand the data in that image as being a fingerprint that belongs to someone.
So what’s the takeaway here?
The magic of a biometric system is in the pairing of the diagram data and the reader, and it’s up to us—as people who make and deploy technology—to determine what those diagrams look like and what readers check those diagrams for authenticity.
So—no—we’re not in danger of needing to change our faces, eyes, or fingerprints anytime soon. If there were a breach of biometric authentication data at some point in the future (it’s when, not if) all we’ll need to do is update the software (and/or hardware) that reads the abstractions of those biomarkers.
It’s important to note, of course, that “just update your systems!” isn’t nearly as easy as it sounds. We should expect some percentage of systems to be deployed that will accept leaked versions of your likeness for a period of time after a breach. But we shouldn’t conflate that problem with needing to change our faces.
Biometric authentication is all about creating and comparing technical facimiles of what we are, and the solution to a biometric data breach is updating those abstractions, not updating ourselves.
Notes
I find it both interesting and sad that after all that it still brings us back to patching.
It’s also fascinating to realize the difference between spoofing vs. a machine vs. spoofing vs. a human. The ability to edit human voices and make them say anything you want, for example, is about to become a major disruptor.
There’s a separate problem of being able to spoof things with such great accuracy that no sensor will be able to tell the difference between it and the real thing. Take for example a molecule-by-molecule match of a person or something. It’s far away, but we need to be aware of the limitation.
Thanks to Steven Harms for talking through some of these concepts with me.
_
If you enjoyed this, you can explore my other content, subscribe to my newsletter, and/or show support for my work.
Format Painter in Apple Pages

I mostly use Microsoft Word for documents because Office is the platform of business, but in my more creative side projects I tend to use Apple’s Pages.
One of the things that Word does really well is copying formatting from one place to another. They have a feature called Format Painter, and it can be invoked in any Office app using the little paint brush icon.
Here’s how to get the same effect in Apple’s Pages.
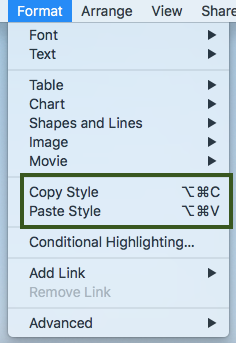
Select the text you want to transfer the formatting of.
Navigate to Format --> Copy Style, or ⌥⌘C.
Navigate to the text you want to transfer the formatting to.
Navigate to Format --> Paste Style, or ⌥⌘V.
Hope this helps someone!
_
If you enjoyed this, you can explore my other content, subscribe to my newsletter, and/or show support for my work.
September 25, 2017
Unsupervised Learning: No. 94
This is episode No. 93 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 30 minute summary. The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well…
This week’s topics: Deloitte hacked, Equifax fumbles, SEC hacked, iCloud ransom, Adobe PGP facepalm, Verizon S3 buckets, CCleaner, tech news, human news, ideas, discovery, recommendations, aphorism, and more…
Listen and subscribe via…



Read below for this episode’s show notes & newsletter, and get previous editions…
Infosec news
Deloitte had its email system hacked (which looks to have possibly been Microsoft’s O365) via an administrator account that lacked 2FA. The breach was discovered in March of this year but could have been going on since late last year or possibly even longer. Link
Equifax has been sending concerned customers to a phishing site for weeks, and now we’re learning that they bought their identity protection service in August when they (but not the public) probably knew about the breach. We (and definitely I) cannot know that the truth is as bad as them strategically planning to make money off their own error, but at this point I wouldn’t be surprised. Link
Someone hacked the SEC last year, and accessed what the SEC is calling “nonpublic information”. It appears that the hack was used to make trades and earn profit. In July a report came out saying that the SEC lacked basic security controls. Luckily it’s just our economy we’re talking about. Link
Some Apple users have had their iCloud accounts hacked—likely by sharing passwords with another account that’s been compromised and published online—which resulted in the attacker locking their Macs remotely and then demanding money to unlock them. Link
Adobe posted their private PGP key on their blog. These people must have cursed the gods in a previous life or something. The whole company is like a giant Flash vulnerability. I’m loving the subscription model for their tools, though. Link
Verizon has had another data leak via—you guessed it—an unsecured Amazon S3 bucket. The content was scripts, server logs, etc. that included internal usernames and passwords. Link
The CCleaner tool has been infected with malware and has compromised at least 700,000 PCs, and Cisco’s Talos group believes that the authors attempted to get inside 18 major tech companies for the purposes of espionage. Link
ISO has rejected two NSA-designed encryption algorithms, apparently because they aren’t sure they can trust the NSA. Fair enough. Link
Swiping to enter your passwords on Android is an extremely weak protection against shoulder surfing, with 64% of attackers being able to reproduce a login after observing only one example. Link
Patching: Apache, iTerm2
Technology news
Google bought part of HTC’s smartphone team for $1.1 billion in a move that looks to be an acquihire of around 2,000 HTC employees and a longterm commitment to more seamlessly merging their hardware and software on mobile. Link
It looks like the GPS accuracy of our personal tech (and probably cars) will get upgraded in 2018 from 5 meters to 30 centimeters. And not only is it far more accurate, but it’ll work way better through buildings and other obstructions. Link
London will not renew Uber’s license in the city, citing quality concerns. Link
The Washington Post has a bot that’s posted over 850 articles in the past year. It’s mostly been factual updates, but expect this to upgrade in quality and start pushing on human talent before long. Change is coming swiftly here. Link
Human news
A massive new study of over 130,000 people across 17 countries has shown that even minor daily activity like vacuuming or walking to work (150 minutes per week) can reduce one’s chances of dying of any cause by 28%. And people who spent more than 750 minutes walking briskly reduced their chances of dying early by almost 40%. Basically, do anything active for 30 minutes a day. Link
Some economists are predicting a labor shortage due to the combination of economic growth and more and more people exiting the labor market (many of which are getting on disability and taking opiates). I’m interested in how this prediction will intersect with my own analysis of motion towards the gig economy, individual influencer/brands for services, and companies preferring to use contracted/temporary employees. Link
Scientists put slime mold onto a map of Tokyo and it quickly built the same train system that humans did. Link
Making projectiles out of Tungsten is evidently quite effective. Link
Ideas
With Facebook and Google You Are Literally the Product Link
Gender Dysphoria Contradicts Both Conservatives and Liberals Link
Co-working (in an office) may be getting popular because it’s about team productivity, not individual productivity. So while it may be true that YOU work better remotely, that doesn’t mean the team gets more done that way. Interesting perspective. I think a balance is needed. Link
Text Size and the Quality of Content Link
Discovery
Israeli researchers exfil data from air-gapped networks using infrared camera LEDs. Link
Explore Neural Networks in your browser. Link
Counterintelligence for Cyber Defense Link
An interesting perspective on “the Notch” on the iPhone X that basically says it’s going to become the new distinctive feature of iPhones. Link
Android Oreo has a number of significant security improvements, including stronger separation of third-party and core Android components, and an improved update mechanism. Seems like a solid security update. Link
A study indicating that IQ maps pretty directly to income. I don’t have enough statistics training to quickly check his work, but the tone seemed genuinely curious and non-biased. Link
AWS Extender — A Burp plugin for testing the security of Amazon S3 buckets. Link
Git Secrets — Prevents you from committing secrets to your repository. Link
Mindweb — a full (and visual) computer science curriculum online. Link
SniffAir — A wireless sniffing system by Rob Fuller (@mubix). Link
RepoSsessed — A project of mine that scans GitHub repos for various types of vulnerabilities (currently focused around secrets). Link
Notes
Haven’t read as much in the last week or so, but I’m still finishing The Fourth Turning and Essentialism.
I’m all Apple’d up with the latest gear (except the iPhone 8 because I’m waiting for the X). I have a new Space Grey Aluminum 42mm Series 3 watch on the way (with LTE), and just installed my new AppleTV with 4K. It’s stunning.
Recommendations
What You Need to Know About Climate Change. I know some of my readers are skeptics, and I know some of you are not. Regardless of which group you fall into I urge you to listen to this podcast. I’m one of those people who’s convinced that we are causing extraordinary warming, but I’ve always hated the fact that there don’t seem to be clear explanations of how we know there’s a problem. That’s precisely what this episode addresses. Link
reddit.com/r/wholesomememes — a Reddit sub dedicated to being excellent to each other. It’s just positive stuff, and I’m telling you that you should incorporate it into your routine. It might change how you see humanity in a positive way. Link
Aphorism
“The important things are always simple. The simple things are always hard. The easy way is always mined.” ~ Murphy’s Laws of War
You can also sign up below to receive this newsletter—which is the podcast’s show notes—every week as an email, and click here to get previous editions.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 10K subscribers.
And if you enjoy this content, please consider supporting the site, the podcast, and/or the newsletter below.
Monthly Support
A subscription is the most helpful way to help me continue making content.
Supporter - $5 / monthMember - $25 / monthPartner - $50 / monthPatron - $100 / monthOther amount
$
SubscribeOne-Time Support
You can also make a one-time contribution of any amount.
$
Send
Thanks for listening. I’ll see you next week.

_
If you enjoyed this, you can explore my other content, subscribe to my newsletter, and/or show support for my work.
September 24, 2017
One of the Coolest Features in watchOS 4 is the Flashlight

The flashlight is one of the most important features on any personal device. You occasionally need light, and when you do you need it to be convenient.
The flashlight on the iPhone and Android devices is pretty good, but it’s a bit inconvenient because you have to dig into your pocket or purse for your phone, do the finger magic, and then hold the phone to aim the light.
Using the flashlight on the Apple Watch is way easier.
Raise your wrist.
Swipe up from the bottom.
Click the flashlight button.
Go back to doing what you were doing with both hands.
You can also swipe to the left to get 1) a flashing light, and 2) a red light, which I intend to use during astronomy sessions when I don’t want to mess up my night vision.
Enjoy.
_
If you enjoyed this, you can explore my other content, subscribe to my newsletter, and/or show support for my work.
With Facebook and Google You Are Literally The Product

IMAGE BY STEPHEN WOLFRAM
A lot of people don’t get the significance of being a product.
It doesn’t just mean that you have value, or that you’re important. What it means is that you’re the thing being sold.
There’s confusion around this because of ads. Everyone has ads, right? The New York Times has ads, Facebook has ads—whats’s the difference?
The difference is that with the New York Times, the product is the newspaper. It’s what’s being sold to the reader, and then the attention of that reader is then sold to advertisers.
Facebook is doing something different. It’s selling attention, for sure, but its main product is the data it has on its users. In this way it’s more like a data broker, like Acxiom.
The entire game for companies like these is to have better data about you then their competitors. And then people pay them, and then they give your data to them.

Facebook excels at this because so many billions of people use the capture mechanism (the Facebook website). Facebook—the website—is the data capture device for their main business. The more you give it, the more they can do their data analytics and improve their product.
The magic here is in selling extremely precise ‘audiences’ like ‘Jew Haters’ or ‘Librarians with eczema’.
When someone buys an add they want as many clicks as possible, and the whole trick there is showing the ad to the right people. And since Facebook knows everything about everyone, and their AI can tell them who relates to who, they can tell you how to expand your audience to the next best/largest group.
So if you want to sell your ‘Jew Hater’ stuff you can sell to the Anti-semite audience, but turns out you’ll do really well with the ‘American flag enthusiasts’ as well. Math tells us strange things sometimes.
Anyway.
The point is that these highly accurate audience types are created by the combination of data + AI, and THAT is the product that’s sold.
You are the data. You are the product. And that’s why they’re making billions of dollars per quarter.
The Facebook website is just how they gather it.
_
If you enjoyed this, you can explore my other content, subscribe to my newsletter, and/or show support for my work.
September 19, 2017
Gender Dysphoria Contradicts Both Conservatives and Liberals
One of my favorite things to observe and study is how reality breaks models, and Gender Dysphoria is a strong example.
Gender Dysphoria
noun
The distress a person experiences as a result of the sex and gender they were assigned at birth.
Liberals and conservatives often have extreme views around gender identity that conform to their own rigid life view.
Conservatives think boys are boys and girls are girls, and that any time you see one acting like the other it’s because they were poisoned by bad parenting, bad culture, or Satanas—the demonic angel cast out of heaven by the creator of the universe.
Many liberals are now fond of thinking the exact opposite, which is that there’s no such thing as boys and girls, and that any time you see someone acting like one or the other it’s because of bad parenting, bad culture, and ultimately the institutionalized sexism that caused both.
Gender Dysphoria shatters both of these myths with a single backhand.
It shatters the conservative model because many of the children who experience this suffering the strongest are those who have the most gender-aligned culture in their lives. They’re told from birth that boys do boy things and girls do girl things, and their entire culture and existence reinforces that message via family, friends, peers, music, etc.
In short, if it were all about the culture, you wouldn’t have Gender Dysphoria in places where the culture strongly pushes gender role models.
On the other side, it shatters the liberal model because the fact that someone could be one thing physically and feel extreme suffering because they’re not the other clearly indicates that there are two different things in the first place.
In short, if there’s no difference between boys in girls at a fundamental level, then it wouldn’t matter to little girls or boys which gender they were, and they wouldn’t experience the pain and struggle of being the wrong one on the outside.
Summary
If it were all culture then you wouldn’t have the effect in places where people only get the programming of their external gender.
If there weren’t strong differences in how people want to look or behave based on being masculine or feminine, then it wouldn’t matter to anyone which they were externally.
The only conclusion that seems to fit here is that there are obviously core differences in how people want to look and behave based on how masculine or feminine they are, and that trying to oppose this truth by willing the opposite is both futile and harmful.
There is such a thing as masculine—which produces the desire to look and behave a certain way—and there is such a thing as feminine—which produces the desire to look and behave another way. And it appears abundantly clear from people expressing gender traits almost immediately after birth that this is a fundamental biological reality.
Also, if it weren’t true that the genders want to emote in different ways then you wouldn’t have millions of people expressing overwhelming relief to finally look and behave in the opposite role.
The gender politics that we see in both forced gay conversion therapy and in attempts to remove the concept of gender differences are mistaken in the same way: they oppose obvious truth because they don’t want to accept the policy changes that would follow if they admitted they were wrong.
If conservatives are wrong (which they are) they would have to accept that some kids are actually the opposite gender than they appear on the outside. And if liberals are wrong (which they are) they would have to accept that there is a biological foundation to differences in male and female behavior, and that it might be ok for some of those differences to play out in culture and society.
Neither side wants that, and that’s why they oppose the evidence.
Notes
When I say “conservatives” and “liberals” I’m referring to the subset of those groups who hold these traditional or mainstream views of these topics. There are obviously many who might self-apply these labels who don’t hold these same views on gender.
This in no way says that this is a binary issue. Hormones aren’t binary, and neither is culture, so it seems obvious that everyone exists somewhere on one or more scales related to these issues.
_
Every Sunday I put out a list of the most interesting stories in infosec, technology, and humans. Subscribe
September 18, 2017
Unsupervised Learning: No. 93
This is episode No. 93 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 30 minute summary. The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well…
This week’s topics: Equifax fallout, BlueBorne, Microsoft RCE, iPhone X, Dumping AWS, Cassini, tech news, human news, ideas, discovery, recommendations, aphorism, and more…
Listen and subscribe via…



Read below for this episode’s show notes & newsletter, and get previous editions…
Infosec news
It looks like the issue that lead to the Equifax leak was an Apache Struts issue that had not been patched for a couple of months. The CIO and CSO have been encouraged to explore other opportunities. There is a lot of focus in the InfoSec community around the fact that the CSO had a music degree. As I wrote about here, I think it’s completely irrelevant. Link
Eight (8) vulnerabilities were revealed in Bluetooth, which are collectively being called BlueBorne. Some allow RCE and others are less severe. They affect nearly all versions of Android and Windows, which means billions of devices. iOS 10 is not vulnerable, which accounts for 89% of iOS devices as of September 6th, 2017. Link
Microsoft has put out patches for numerous issues, including for a serious RCE flaw in .NET. An attack using this vulnerability was found being used by the FinSpy commercial spyware product (also called WingBird). Link
Gartner says attacks against Android increased by 40% in Q2, evidently due largely to increased adoption of mobile banking. Link
Facebook has been creating audiences that match “Jew Hater” and similar extremist views, and then selling ads against those tightly optimized audiences. People wondered what evil would be possible when you have lots of great data. This is it. Link
South Park’s season premier purposely invoked Alexa for (I’m guessing) tens of thousands of people. It’s funny this time, but there will be versions of this in the future that won’t be humorous, e.g., changing the temperature in millions of homes and overwhelming power distribution systems, making purchases, opening doors, etc. Link
With some exceptions, consumer routers continue to be a security dumpster fire. There’s a new cluster of issues in some D-Link routers, ranging from RCE to the standard fare of hardcoded credentials, weak update mechanisms, etc. It’s like we’re not even trying. Link
Patching: BlueBorne, Flash, Coldfusion, Microsoft, D-Link Routers
Technology news
Apple released its iPhone X (ten, not ex) last Tuesday. I’m a complete Apple acolyte but can’t help but notice that all the main features (edge-to-edge display, wireless charging, and facial authentication) have already been out for months or years from other vendors. What I find so interesting about this is that it’s still likely to dominate because it’s so good at execution. As I wrote about here in 2007, Apple’s magic is in implementation rather than feature count. I expect the iPhone X to be the same with face authentication especially—with the effect being that it will seem Apple invented it even though they didn’t. Sometimes it’s about being first, but more often it’s about being the first to do it well. Link
HP has unveiled an unholy Z8 workstation of doom, with up to 28 cores and 3TB of memory. Link
Dropbox moved off of AWS, and I think we’re likely to see a lot more companies doing the same. It’s a pendulum swing issue. We went heavy to the Cloud side, and now it’s correcting a bit. I have a number of customers who are pulling back in simply due to cost. I’m not convinced they’ll see it the same way after they fully spin up the new stuff internally, but maybe they will. It depends on a lot of things, including the business you’re doing, the quality of your team, how efficient you are, etc. But we should expect these swings to keep happening until things stabilize technology-wise. Which right now is effectively never. Link
Starbucks will update its wireless chargers remotely so that they will support the iPhone 8 and X soon. Link
Human news
The Cassini spacecraft fell into Saturn on Friday morning, ending a flawless 20 year mission in space. This is a planet millions of miles from us, and they predicted the exact moment they’d lose radio contact down to a few minutes. Unbelievable. Link
A new study has given support the the Extreme Male Brain Theory of autism, which says that autistic boys and girls are basically exhibiting extreme versions of male traits, e.g., systematic vs. empathic thinking. They tested many boys and girls and found that autistic children of both genders had “hypermasculinized” faces, which is consistent with the theory. Link
A large new study of 7,985 adults over 45 years old showed a significantly higher chance of death among those who were sedentary. The recommendation was to break up sedentary periods with periods of activity. Sounds obvious when you say it like that. Link
When Seattle raised the minimum wage it made restaurants find ways to pass costs onto customers. One of the ways they evidently cut corners is by reducing their attention to hygiene. Link
A Stanford study has found that 99% of microbes in our blood has never been seen before or classified. Link
Facial recognition is about to go mainstream in the U.S. because of the iPhone X, but China has been doing it for years. They use it for things like discouraging jaywalkers and people who take too much toilet paper. Yeah… Link
Price changes in US consumer goods and services from 1997 to 2017. Spoiler: college and education way up, child care and healthcare up significantly, housing food and transportation up some, and software and tech gadgets way down. Quite a good visualization. Link
Daniel Kahneman, author of Thinking Fast and Slow, has been called out in a blog post on his use of a number of studies on Social Priming in his book that evidently have an extremely low reproducibility index. Social Priming is the theory that subtle cues can significantly and subconsciously influence human behavior. Shockingly, Kahneman showed up in the blog that raised the issue and basically said, “Yep, my bad. I should have known better.” Link
Ideas
A Rudimentary Threat Model for Password vs. TouchID vs. FaceID — how to determine your most important threat scenarios and then determine which authentication controls are best for you. Link
How to Tell If You Should Hire an InfoSec Person With a Music Degree — why it’s ridiculous to filter people based on formal education in InfoSec. Link
What if Attackers Pivot from Ransom to Extortion? — exploration of a potentially nasty switch in strategy that attackers could make against vulnerable companies. Link
The Most Important Skill You Can Cultivate — an essay by Andres Karinkovic about developing resilience as a life strategy. Link
Discovery
Godel, Escher, Bach: A Mental Space Odyssey, presented by MIT. Link
A story from 1999 where Palestinians refused to adopt “Zionist” Daylight Savings Time, which caused confusion about what time it was. As a result, two bombs went off an hour early during transport and killed three of the attackers. Link
These bacteria hide in tumors and consume chemotherapy drugs. Link
The front-facing camera on the iPhone X is basically a Microsoft Kinect. Link
I’ve not read it yet, but this Broken Earth book trilogy looks fantastic. Hugo winner two years in a row, and the third one just come out. Bumping to the top of my list. Link
Writing Prompts — A Reddit sub that gives you super interesting prompts for a short story (or even a novel). Reading these makes you realize how bad today’s mainstream movies are. If someone built movies around these ideas rather than what normally see we’d have some fantastic stuff. Same goes for Anime, actually. The stories in Anime are so much more creative than those in mainstream western movies.
The most male and female occupations, since 1950. Link
The Reason Today’s Kids Are Bored at School, Feel Entitled, Have Little Patience, and Few Real Friends — I normally dislike these types of articles, but this one seems extremely on point. Link
50 new features in the iPhone X, in case you’re wondering whether to get it or the iPhone 8. Link
Hack — a typeface designed for source code. Link
Whitelisting Cloudflare Using IPTABLES Link
Deprecated Linux networking commands and their replacements. Link
What’s new in IDA 7.0. Link
Testing for SSRF. Link
Notes
I’ve changed the settings on my newsletter signup form on the website. I’ve had numerous people tell me that it’s annoying, and I’ve asked the people who make the code to be better at detecting if someone is already a subscriber. I’ve basically set it to not annoy someone for an entire year once they do anything with it, and I’ve also set it to only popup when you leave the site rather than after a certain amount of time. Sorry for the annoyance; I’m trying to fix it.
I don’t see myself getting another iPad anytime soon, and this is especially true since they’re making me buy a giant phone (the iPhone X doesn’t come in the small or medium size). I love the iPad for drawing, but I don’t think I do it enough to justify the purchase. And the other use case of reading is not compelling (or convenient) enough when the iPhone X’s screen is now so large. It’ll feel good to dump the iPad and only have the iPhone and Watch.
I experienced the strongest sense of anthropomorphism in a long time with the death of the Cassini probe (see?). I honestly felt so proud for it, and so sad that it just did its job perfectly and then became a beautiful meteor and then nothing. It moved me, even after I saw it for what it was. We’re strange things, humans.
I’m working on a creative project that will start as a role-playing game but might eventually make it into computer form. It’s mostly a modern/tech-based game but quickly branches into other genres. The primary goal is to build a story arc that’s designed rather than improvised using elements that I’ve enjoyed from many other mediums. Supremely challenging. If any of you are writer / designer types and want to hear more, let me know.
I have a friend who is, for various reasons, desperate to get an MRI done in Seattle, and is wondering the best way to go about it. He’s tried going through normal channels and has been told he doesn’t need one by a couple of different doctors. So the question is: if your life depended on getting an MRI, but regular doctors wouldn’t listen to you, what are the options? If anyone is in the medical field in or around Seattle and has a way to make this happen, or even just some ideas, I’d be infinitely grateful.
Recommendations
This is Water is a must-see 9-minute video. It’s one of the few things that’s changed my philosophical mental model over the last several years, and I hope it does the same for you. Watch it. Share it. Link
Godel, Escher, Bach: A Mental Space Odyssey, presented by MIT. Link
How to perform a good programming interview. Link
The Flowing Data website. Link
Aphorism
“Action is the foundational key to all success.” ~ Pablo Picasso
You can also sign up below to receive this newsletter—which is the podcast’s show notes—every week as an email, and click here to get previous editions.
Newsletter
Every Sunday I put out a curated list of the most interesting stories in infosec, technology, and humans.
I do the research, you get the benefits. Over 10K subscribers.
And if you enjoy this content, please consider supporting the site, the podcast, and/or the newsletter below.
Monthly Support
A subscription is the most helpful way to help me continue making content.
Supporter - $5 / monthMember - $25 / monthPartner - $50 / monthPatron - $100 / monthOther amount
$
SubscribeOne-Time Support
You can also make a one-time contribution of any amount.
$
Send
Thanks for listening. I’ll see you next week.

_
Every Sunday I put out a list of the most interesting stories in infosec, technology, and humans. Subscribe
September 16, 2017
How to Tell If You Should Hire an InfoSec Person With a Music Degree

It’s the only chart you’ll ever need for this. You’re welcome.
The InfoSec industry is full of top talent that has no degree, art degrees, and STEM degrees. It’s also full of bottom talent in all those categories. You simply can’t tell how good someone will be at their job based on how much—or what type—of formal education they have.
You might think you can, but you’d be wrong.
Google thought they could too, and they did a massive study on it several years ago to find the magic education level, the magic school, the magic whiteboard skills, etc.
Turns out there was no magic degree, no magic school, and no magic puzzle question that could predict how good an employee would be.
So it might be fun to talk about how the Equifax CSO had a music degree, because we automatically—as human pattern matchers—want to assume that this was the reason the company got hacked on her watch.
But the truth is that I don’t know why it happened, and you probably don’t either.
Maybe she was incompetent and she was hired for political reasons
Maybe she was incompetent and she was hired as part of the buddy system
Maybe she was competent and got unlucky
Maybe she was competent but negligent in this case
Maybe she was competent but faced the most elite hacker ninjas in the world and there was nothing she could have done
It could have been a lot of things, but—like the Google hiring issue—precisely zero of these options hinge upon whether she had a music degree.
We as the InfoSec need to take guidance from the intelligence community and realize that you look like an idiot when you give strong opinions on topics without the facts needed to form those opinions.
We can do better.
_
Every Sunday I put out a list of the most interesting stories in infosec, technology, and humans. Subscribe
September 14, 2017
A Rudimentary Threat Model Framework for Password vs. TouchID vs. FaceID

[ Full size image. ]
There’s been a lot of discussion around Apple’s replacement of TouchID with FaceID on the new iPhone X. There’s conversation around the overall security of biometric authentication vs. as well as comparisons of TouchID security vs. that of FaceID.
Unfortunately, the usual question being asked is something like:
Which is more secure?
But what they should be asking is a more nuanced:
For my particular situation, am I more secure using a password, TouchID, or FaceID?
This is the reason Threat Modeling is important: it highlights the fact that it’s impossible to understand the efficacy of a control without understanding how it’ll be attacked.
I built the system above to highlight this concept as it relates to different types of personal device authentication. It’s a crude model, but it shows the key considerations and how they map to reality. Here’s the structure of the model.
First it captures realworld scenarios that you might face (threats).
It has you prioritize which of those scenarios matter the most.
Then it captures how well the three options (password, TouchID, and FaceID) will do against those scenarios.
So here’s the methodology for determining which auth system makes the most sense for you.

You put your top three (3) scenarios in order, and each gets a multiplier. Your first most important gets 3x, the second gets 2x, and third gets 1x.
Then the four (4) different security levels (LOW, MEDIUM, HIGH, MAX) are given numeric values as well, going from one to four (1-4). See above.
Then for each scenario you multiply the scenario multiplier by the control value (1-4 based on the rating), and then add them up going down the scenarios.
Going through the controls
Now we run the numbers multiplying the scenario weight by the control strength for each control.
Passwords
So, considering just the Password control
Convenience (3) x LOW (1) = 3
Shoulder-surfing (2) x LOW (1) = 2
Law enforcement (1) x HIGH (3) = 3
3 + 2 + 3 = 8.
TouchID
So, considering just the TouchID control
Convenience (3) x HIGH (3) = 9
Shoulder-surfing (2) x MAX (4) = 8
Law enforcement (1) x MED (2) = 2
9 + 8 + 2 = 19.
FaceID
So, considering just the FaceID control
Convenience (3) x MAX (4) = 12
Shoulder-surfing (2) x MAX (4) = 8
Law enforcement (1) x LOW (1) = 1
12 + 8 + 1 = 21.
So we end up with the relative strength—for this set of scenarios—being: Passwords (8), TouchID (19), and FaceID (21). So with the highest score, FaceID wins.
What’s important here is that these numbers represent a combination of both your most important scenarios (the weighting of the multiplier) AND the effectiveness of the controls across those various situations.
Given as an English sentence we’d basically be saying:
Based on me valuing these scenarios the most, and the effectiveness of each authentication system in those situations, FaceID seems best match for me, with TouchID being pretty close and passwords lagging pretty far behind.
And here’s the key: I only spent a few moments coming up with those ratings, and there are more scenarios that could be added. And as you update the data in the model, your recommended authentication method (the highest score) might change along with it.
Hopefully this will help some folks understand Threat Modeling a bit more—at least at a basic level—and thus enable clearer thinking about how various security measures can be rated for practical effectiveness.
Notes
We could obviously debate pretty much every rating for every scenario, but the chance of getting security material means the ease of stealing someone’s fingerprint, stealing someone’s face, or stealing their password. And there’s obviously a difference between getting an image of a face vs. getting something that will unlock a device. So keep that all in mind.
For the law enforcement stuff I assumed you didn’t have time, or didn’t remember, to enable the Cop Mode feature that then requires a password be used instead of TouchID or FaceID
I think it’s interesting that if someone grabs your phone from you or in front of you, the first reaction is to look at them, which is precisely what will unlock it. I think we’re about to have to train people to look away, or close their eyes, when this happens.
I also think there should be an Apple Watch or Mac-based way to lock the phone remotely if someone does this trick to take and then unlock your device using your own face.
__
September 13, 2017
Whitelisting Cloudflare With IPTABLES
Many people use Cloudflare to protect their website but don’t restrict access to the web server to Cloudflare IPs. This means that whatever protection Cloudflare provides can easily be bypassed by hitting your IP directly.
That’s why you should have a firewall. And if you’re cool, you’re probably using iptables. So here’s how to make sure only Cloudflare can talk to your web ports.
1. Install ipset, which is a utility that lets you create text hashes that can be used with firewall rules.
apt install ipset
2. Create the firewall object “cf4”
ipset create cf4 hash:net
3. Populate that object with Cloudflare’s list of IPv4 addresses.
for x in $(curl https://www.cloudflare.com/ips-v4);
do
ipset add cf4 $x;
done
4. Insert the rule into your firewall.
iptables -A INPUT -m set –match-set cf4
src -p tcp -m multiport –dports http,https -j ACCEPT
5. Regularly pull down the list and reintegrate it with the firewall
ipset destroy cf4
ipset create cf4 hash:net
iptables -A INPUT -m set --match-set cf4 src -p tcp -m
multiport --dports http,https -j ACCEPT
Load your rules.
iptables-save
[ NOTE: I assumed you are on Ubuntu here, because I (once again) assume you’re cool. I can’t get into the way CentOS does things. ]
I recommend putting this into /etc/cron.daily/ as a script, or perhaps doing it weekly or monthly. I do it more often because I don’t like the idea of dropping packets from my proxy.
Finally—and I hope this is obvious—you need to have a DENY ALL rule at the bottom of your ruleset, otherwise it’s not a whitelist!
iptables -A INPUT -d $YOURHOST -j DROP
And don’t forget to log it as well!
Hope this helps.
__
I do a weekly show called Unsupervised Learning, where I curate the most interesting stories in infosec, technology, and humans, and talk about why they matter. You can subscribe here.
Building a Professional Firewall with Linux and Iptables
An IPTABLES Primer
Visualizing Interesting Log Events Using Splunk’s Google Maps Application
Building a Wicked Fast CentOS Web Server with Nginx, PHP, and MySQL
Getting Real IP Addresses Using CloudFlare, Nginx, and Varnish
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers



