Febin John James's Blog, page 5
May 21, 2018
The Curious Programmer’s LightSpeed Guide to Building Applications on Ethereum
 JumpStart Blockchain Application Development
JumpStart Blockchain Application DevelopmentI had a lot of questions on my quest to understand how Blockchain works. The important one was “How do I build applications on it?”. It took a few weeks of digging up, reading and experimenting to finally get it. I couldn’t find a short but comprehensive guide. Now, that I have some decent understanding, I thought of writing one that could help others. This is a light speed guide, I have kept only the important parts in order to reduce the learning curve.
 ChaptersThe Purpose of BlockchainHow was the Blockchain invented?Introduction to Ethereum & Smart ContractsProgramming Smart Contracts on EthereumThe Way AheadThe Purpose of Blockchain
ChaptersThe Purpose of BlockchainHow was the Blockchain invented?Introduction to Ethereum & Smart ContractsProgramming Smart Contracts on EthereumThe Way AheadThe Purpose of Blockchain
Roopa lives in one of the remote areas of Delhi. The government of India has allocated her few resources of food every month. Since she belongs to the BPL(Below Poverty Line) category. The government uses a middleman to distribute these food resources. Only one-third of the allocated food resources reach people like Roopa, the rest is sold by the middleman for profit.
Sara writes fiction books, she publishes them on Amazon. She’s upset because Amazon takes 50% of the sale as commission. That’s unfair because she alone has put in the efforts of writing and marketing.

The problem is middleman is hungry for power and money. Their motto has become “profit at any cost”, to support producers and to empower the poor, we need middlemen to act ethically. That’s almost impossible to achieve, but what if we can replace middleman with an autonomous system?

Since computers don’t have biases they neither need money or power. This could have been Satoshi Namakato’s thought when he invented bitcoin using the blockchain technology in 2008.
How was the Blockchain Invented?
Money has evolved over time, each evolution reduced its cost of production and made their transactions more convenient. Gold coins were costly to produce. The invention of paper currency solved this problem. But, after the invention of computers and internet, people found a better way to make transactions convenient and faster.
To safe keep our lifetime’s earnings and to facilitate digital transactions we need a middleman(bank). This made banks powerful, they can impose a heavy fee on our withdrawals /transactions, sell our private information, etc

Banks hunger for money caused the financial crisis in 2008. Banks failed to respect their customer’s privacy. Their weak security systems gave rise to digital fraud.
The next evolution of money had to solve the following problems.
It shouldn’t be stored with a central entity.It needs to be highly secure.It should ensure privacy.Since fiat currency is controlled by the government, Satoshi had no option but to invent a new currency (Bitcoin). He solved these problems with the help of peer-to-peer networks and cryptography.
Decentralisation Credits : xkcd
Credits : xkcdTorrents use peer-to-peer technology to share files. The torrent app doesn’t download the file from a central server or a single computer, instead, it connects to the people in its network, finds out who has the file and download it from their computers.
You get the pieces of a file from different computers around the world. If one person in the network goes away, your download isn’t affected because there are other people who can share the file.
Satoshi adopted this technology since it stores money in a decentralized way. No single entity will have control over it.
Cryptography Credits : xkcd
Credits : xkcdIn cryptography, one can digitally sign a message. In order to do this we need three things a public key, private key, and message.
The public key and private key are a set of long characters that are mathematically connected. A public key is public like your username, and the private key is a secret like your password.
A message is an information you want to authorise, ex: “I authorise you to pay John $100”.
If you input the algorithm with a public key, private key and message. The cryptographic algorithm will produce a signature. That is another set of characters unique to the contents of that message.
Public Key-----BEGIN EC PUBLIC KEY----- MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAE50uE+YSxqDgMkFByhpcgTVqXCqHO h68Ljt1z0jklDff/WV7xo+U6o3REBtK/C0/LM+Ef3FB3wR9aXMGNMLb9EA== -----END EC PUBLIC KEY-----Private Key
-----BEGIN EC PRIVATE KEY----- MIGHAgEAMBMGByqGSM49AgEGCCqGSM49AwEHBG0wawIBAQQgwqIsXl9FqsgrzMdx axI6flBwWIev0Z7i+WF4j8BGnrKhRANCAATnS4T5hLGoOAyQUHKGlyBNWpcKoc6H rwuO3XPSOSUN9/9ZXvGj5TqjdEQG0r8LT8sz4R/cUHfBH1pcwY0wtv0Q -----END EC PRIVATE KEY-----Message
Hello WorldSignature
B0A9A4F641D3A2E3A65576B7311DCD62ABE78BBF4D3F5FE856598508E24FCB2E6F0277C2F8D57E9E2E108B7C493986E783F5316B8046597019951669B4EE6922
To verify the message, one has to input the public key, the message, and the signature. The cryptographic algorithm can verify if the message was signed by the owner of the public key.
It would take 1000’s of years to break the cryptographic algorithm. This cannot be done faster because of the computational limits we have. Quantum computers in the future might challenge this. But, the Bitcoin system can be upgraded to ensure security.
Satoshi incorporated cryptography in his system to help people authorise bitcoin transactions from their wallets.
Privacy Credits : xkcd
Credits : xkcdYou register to bitcoin by generating a wallet (public key/private key). The systems collect no information such as email id, full name, etc. Hence you are anonymous unless you announce your public key.
Putting it TogetherSatoshi built a shared ledger using cryptography and peer-to-peer networks. When someone sends bitcoins to someone, a message is cryptographically signed and broadcasted to the entire people in the network. They update their ledger, hence everyone in the network knows who owns what.
Blockchain
Every ten minutes transactions are grouped together into a block and linked back to the previous blocks. This process makes a continuous blockchain. Mining is a process by which a block is confirmed, this involves computers in the network to solve a mathematical problem. The first computer/miner who solves the problem gets rewarded in bitcoins made out of thin air.
Once the block is confirmed and added to the network, it is replicated across the entire network. Blockchain was invented in the process of making the autonomous Bitcoin system which confirmed transactions without human intervention. If you are looking for a simplified explanation for blockchain, here’s a story.
A Beginner’s Guide to Blockchain
Introduction to Ethereum & Smart Contracts
Earlier we talked about replacing middleman with autonomous systems. This can be done through programming. Bitcoin’s system was difficult for people to code autonomous systems.
Hence Vitalik Buterin built a new cryptocurrency called Ethereum. It was not only a decentralised cryptocurrency but a network of computers which can host code in the form of smart contracts.
In smart contracts, we can program conditions. If you want to build a decentralised bookstore. You write instructions to help authors add new books, send the download link to an ebook once the customer makes a transaction etc.
Smart contracts not only store conditions but also data. A smart contract of a decentralised bookstore in itself stores the book listing, purchases, etc.

However, we should admit the limitations of the smart contract. Some systems need human support, computers can’t handle it. In the real world implementing smart contracts isn’t easy. Smart contracts once published cannot be altered, silly mistakes can be costly.
Programming Smart Contracts on Ethereum Credits : xkcd
Credits : xkcdWe will build a simple smart contract that stores and retrieves grades of students. We will be coding the contract in solidity. Here’s the github repo.
pragma solidity ^0.4.18;contract Grades{}The first line tells the compiler which version of solidity we are using. Then we define the contract grades.

We need to store two things in our contract, names of students and their grades. Hence we will create an array to store student names and an associative array to store their grades.
pragma solidity ^0.4.18;contract Grades{mapping (bytes32 => string) public grades;bytes32[] public studentList;}
Now, we will create a way through which we can send the contract, a list of student names. We will do that in the constructor.
pragma solidity ^0.4.18;contract Grades{mapping (bytes32 => string) public grades;bytes32[] public studentList;function Grades(bytes32[] studentNames) public {
studentList = studentNames;
}}
In Solidity we would be calling the constructor only once. We will pass student names as an argument, which would be stored in the studentList array we declared earlier.
Now, we need to write a function to assign students their grade. We also need another function to check if the student is valid.
pragma solidity ^0.4.18;contract Grades{mapping (bytes32 => string) public grades;bytes32[] public studentList;function Grades(bytes32[] studentNames) public {
studentList = studentNames;
}function giveGradeToStudent(bytes32 student, string grade) public {
require(validStudent(student));
grades[student] = grade;
}function validStudent(bytes32 student) view public returns (bool) {
for(uint i = 0; i < studentList.length; i++) {
if (studentList[i] == student) {
return true;
}
}
return false;
}}
The “giveGradeToStudent” function takes two arguments, student name, and grade. The require function checks if the “validStudent” function returns true or false. If it returns false, the execution is canceled.
Finally, we need to write a function to fetch the grade of a student. The “getGradeForStudent” function takes student name as an argument, return the respective grade from the associative array.
pragma solidity ^0.4.18;contract Grades{mapping (bytes32 => string) public grades;bytes32[] public studentList;function Grades(bytes32[] studentNames) public {
studentList = studentNames;
}function giveGradeToStudent(bytes32 student, string grade) public {
require(validStudent(student));
grades[student] = grade;
}function validStudent(bytes32 student) view public returns (bool) {
for(uint i = 0; i < studentList.length; i++) {
if (studentList[i] == student) {
return true;
}
}
return false;
}function getGradeForStudent(bytes32 student) view public returns (string) {
require(validStudent(student));
return grades[student];
}}
For the sake of this tutorial, you can deploy this on a personal blockchain. You can create with Ganache. Here are the commands to install and run ganache.
npm install ganache-cli web3@0.20.3 solcnode_modules/.bin/ganache-cli
Keep ganache running, on a new terminal we will deploy our smart contract. Please save the smart contract as ‘Grades.sol’.
Let’s compile the code.
nodecode = fs.readFileSync('Grades.sol').toString()
solc = require('solc')
compiledCode = solc.compile(code)
Now let’s deploy the smart contract. Deploying contract on a blockchain will cost you gas, this is to reward people who rent their computational power to you. So we have to specify the amount of gas which you are willing to allocate. You can estimate that using a gas calculator. But, you don’t have to pay now because you are deploying on a personal blockchain and it’s your resources being used. You will have to pay when you deploy contracts on the public Ethereum blockchain.
Web3 = require('web3')web3 = new Web3(new Web3.providers.HttpProvider("http://localhost:8545"));abiDefi... = JSON.parse(compiledCode.contracts[':Grades'].interface)GradesContract = web3.eth.contract(abiDefinition)byteCode = compiledCode.contracts[':Grades'].bytecodedeployedContract = GradesContract.new(['John','James'],{data: byteCode, from: web3.eth.accounts[0], gas: 4700000})Now let’s call our functions to give grade ‘A+’ to our student John. Later, we will check if it has been updated using our ‘getGradeForStudent’ function.
deployedContract.giveGradeToStudent('John', 'A+', {from: web3.eth.accounts[0]})deployedContract.getGradeForStudent.call('John')'A+'
Congrats, you have deployed your smart contract. If you have questions/doubts please comment on this story, I will either comment back or update this story.
The Way AheadYou can get in-depth understanding about writing Ethereum smart contracts in the following websites.
CryptoZombiesYou don’t have to download anything, you can write code on their interactive compiler. You will learn the concepts of solidity programming by building a game. It’s free of cost.
CryptoZombies - Learn to code games on Ethereum. Powered by Loom Network
ZastrinZastrin has both free and paid courses. Mahesh Murthy covers all the important aspects. They even teach you to build a decentralised marketplace similar to eBay.
Zastrin | Learn Ethereum programming by doing real-world projects
Claps Please
May 20, 2018
A Silly Mistake Most Crypto Traders Make
 Do Not Store Tokens In Exchanges
Do Not Store Tokens In Exchanges
“You are given a gun, one of the six chambers is loaded with a bullet. The game is to point the weapon at yourself and pull the trigger. If you come out alive, you will be rewarded with $1 Million. Would you take a chance?”

There is one in six chances of losing your life. Now, Imagine the case where there are thousand chambers and five of them are loaded. You are still at risk, storing your crypto assets on exchanges has similar risks. Here is a list of popular attacks.

In most centralised exchanges you don’t get a real wallet, but an illusion of a wallet is created. Because it’s inefficient to have separate wallets for a huge user base. They store the map of “who owns what assets” in a database, crypto assets are collectively stored(irrespective of ownership) in a few real wallets. When users trade with each other, trades are updated in the database and account balances are updated, real crypto transfers don’t happen.

If an exchange store all the Bitcoins in a single wallet and if it gets compromised, everything is lost. This has occurred several times in the past.
Though many exchanges claim to store it on cold/physical wallets, this process is not easy. A cold wallet is usually a paper wallet or a USB thumb drive where wallet credentials (private/public key) is stored.
Paper wallets are prone to fire/water damages. If one loses his thumb drive, there are no means of recovery.
 Poor Guy Lost His Cold Wallet
Poor Guy Lost His Cold WalletThe other problem is because of exchanges are not regulated, chances of fraud are higher. It’s easy for exchanges to disappear with people’s money. There is also a possibility of governments forcing exchanges to hand over their wallets.
Storing crypto assets on centeralised exchanges doesn’t make sense because the key concept of cryptocurrencies is decentralisation. But, since it stored in centralised exchanges, they can increase their trade/withdrawal fee as they wish. Users have no option, but to bear it.
Storing your crypto assets in exchanges is a bad idea. This is not practical for people who trade in high volumes because storing on their own wallets is time-consuming and costly.
It’s better to identify one’s trade volumes and keep only what is required in exchanges. Only store assets on exchanges you can afford to lose, storing everything should be avoided. Blockchain projects have started warning people about holding their tokens in exchanges, it applies to all type of crypto assets, not just Bitcoin or Ethereum.
I hope this problem won’t last long, exchanges should adopt a mechanism to enable trade without holding their user’s assets.
Claps Please
May 15, 2018
A Silly Mistake Most Crypto Traders Make
 Do Not Store Tokens In Exchanges
Do Not Store Tokens In Exchanges
“You are given a gun, one of the six chambers is loaded with a bullet. The game is to point the weapon at yourself and pull the trigger. If you come out alive, you will be rewarded with $1 Million. Would you take a chance?”

There is one in six chances of losing your life. Now, Imagine the case where there are thousand chambers and five of them are loaded. You are still at risk, storing your crypto assets on exchanges has similar risks. Here is a list of popular attacks.

In most centralised exchanges you don’t get a real wallet, but an illusion of a wallet is created. Because it’s inefficient to have separate wallets for a huge user base. They store the map of “who owns what assets” in a database, crypto assets are collectively stored(irrespective of ownership) in a few real wallets. When users trade with each other, trades are updated in the database and account balances are updated, real crypto transfers don’t happen.

If an exchange store all the Bitcoins in a single wallet and if it gets compromised, everything is lost. This has occurred several times in the past.
Though many exchanges claim to store it on cold/physical wallets, this process is not easy. A cold wallet is usually a paper wallet or a USB thumb drive where wallet credentials (private/public key) is stored.
Paper wallets are prone to fire/water damages. If one loses his thumb drive, there are no means of recovery.
 Poor Guy Lost His Cold Wallet
Poor Guy Lost His Cold WalletThe other problem is because of exchanges are not regulated, chances of fraud are higher. It’s easy for exchanges to disappear with people’s money. There is also a possibility of governments forcing exchanges to hand over their wallets.
Storing crypto assets on centeralised exchanges doesn’t make sense because the key concept of cryptocurrencies is decentralisation. But, since it stored in centralised exchanges, they can increase their trade/withdrawal fee as they wish. Users have no option, but to bear it.
Storing your crypto assets in exchanges is a bad idea. This is not practical for people who trade in high volumes because storing on their own wallets is time-consuming and costly.
It’s better to identify one’s trade volumes and keep only what is required in exchanges. Only store assets on exchanges you can afford to lose, storing everything should be avoided. Blockchain projects have started warning people about holding their tokens in exchanges, it applies to all type of crypto assets, not just Bitcoin or Ethereum.
I hope this problem won’t last long, exchanges should adopt a mechanism to enable trade without holding their user’s assets.
Claps Please
April 22, 2018
Can Technology Help You Declare Your Work Independence?
 This Paid Story is Brought to You by WeMark
This Paid Story is Brought to You by WeMarkI still remember my dad’s expression when I expressed my interest in being a blogger and a photographer eleven years ago. He didn’t encourage it, I moved on. After a couple of career switches here I am again with writing.
I worked as a consultant in a tech company for few months. I unknowingly inclined towards politics, gossiping, etc. I noticed I am becoming one of them. I was supposed to follow biased thoughts of my boss, I felt caged. The cage was weak for the inner zeal I had, and I broke free. I risked only guaranteed income, which luckily I was able to handle.
I have worked as a freelancer earlier, I earned by undertaking work in web and mobile development projects. I don’t like when programming gets serious, I love coding when it is fun. I wanted to figure out a way to earn through my passion, writing. I wish I knew about blockchain based communities that paid its creators for contributing content. If you are a photographer, checkout WeMark.
I started writing on Medium, few of my posts went popular (It didn’t happen overnight, it happened over a period of few months). Companies approached me for sponsored stories via LinkedIn.
This job is perfect for me since it allows me to work on my own phase. People value my work and are willing to pay more when I give my best. The important thing was my creativity was encouraged and appreciated.
Working independently comes at a cost, you won’t get guaranteed work. Later, I started researching about passive income. I experimented with publishing books. Amazon takes 50% of your book as commission. Publishing on Amazon itself didn’t give me visibility, I had to do marketing myself. It’s really hard to watch Amazon taking a substantial amount as commission, It’s not fair.
Producers in almost every industry are exploited by the middleman. This is a problem blockchain can solve. Innovators around the world are working on projects based on blockchain technology to help producers earn a fair income for their work.
WeMark is one among such innovators based on Ethereum blockchain.
https://medium.com/media/8e1453135d562008b2b4a65c6f594c0f/hrefIt is a decentralized marketplace where photographers can earn money by licensing their photos. Stock photography is a super-centralized $4B industry, with agencies like Shutterstock and Getty Images controlling much of the market.
Centralised vs Decentralised MarketplacesCentralised is the approach of traditional companies. They have leverage because they have all the control.
As a seller on Amazon, I have no option but to follow policies made by Amazon. They can change their commission rates as they wish, they can ban me for no reason. (This has happened with a lot of Amazon affiliates.)
In the case of decentralized marketplaces, the power is with the community. This is because decentralized marketplace deploys their program on computers of people around the world. Their program is transparent, anyone can even go through the code. They use smart contracts to guarantee trust. A smart contract is a computerized agreement which enforces itself.
Centralised marketplaces have a system that favours themselves whereas decentralised marketplaces have a system that favours the community.No More Broken Promises
A photographer can sign a smart contract with WeMark. Each agreement includes a price range for licensing the content, the terms of the agreement, the distribution fee to be paid to the platform, and the percentage of each sale to be paid for referrals.
When a customer buys a creator’s work, money is transferred to the photographer wallet without the consent of WeMark. Because they have already made a self-enforcing agreement on the smart contract.
Decentralised marketplaces are likely to be the future. Because it’s in the best interests of people and they are more trustworthy than centralized marketplaces.
Help with DistributionWeMark incentivizes affiliates who do the hard work of selling creator’s photos. Every sale is recorded on the transparent blockchain, nothing happens outside it, you can see the detailed revenue share by exploring the transactions.
Though centralized marketplaces have referrals, they ban people for no reason. It’s difficult to trust such centralized systems.
In a decentralized marketplace, referrals are trusting a computer program which is unchangeable and doesn’t have biased opinions as humans.
Automatic PaymentsIn centeralised marketplaces, you don’t get paid immediately when someone purchased your work. It usually ranges from 30-60 days, that’s a huge time spent waiting. Since WeMark uses smart contracts, once the sale is completed money is transferred to the photographer’s wallet.
Powered by EthereumEthereum is next to bitcoin, it’s powerful because it is built as a platform where anyone can deploy decentralised applications. Apple’s App Store changed how people consumed content and services. Similarly, Ethereum is likely to have a huge impact on online marketplaces.
WeMark made a great move by adopting Ethereum. It has a great community backing and given enough time Ethereum’s blockchain has a greater possibility to thrive.
Benefits for Photographers1.Photographers keep all the rights to their content The creator owns his work, WeMark only distributes it as on agreed terms.
2.Photographers control the pricing of their photos. The content needs creators approval on the price to license their work.
3.Photographers keep 85% of the revenue. It’s 5x when compared with the industry average, where the creator gets paid 15–20%
4.Photographers benefit from higher transparency. Since WeMark uses a public blockchain there is nothing done in secrecy. You can view the source code of smart contracts, transaction details on how the revenue is distributed,etc on the Blockchain.
5.Photographers will be able to trust the system. As discussed earlier, the creator is not trusting an entity but a system which favours them.
Benefits for CustomersCenteralised systems have the concept of expirng credits. If one change’s his/her mind later, the credit purchased cannot be refunded. WeMark issue you coins, you can use it to purchase licenses or you can trade/sell it.Since WeMark eliminates the middleman, they believe prices should reduce by 50%. This makes sense because in centralised marketplace photographer’s have to increase their price to have a decent income.WeMark curates modern and relevant photos, this helps you in finding the content you need much easier.WeMark is built on a system that is aligned with best interests of the community.Have a look at WeMark’s website, please feel to reach out to them with your questions and concerns on their telegram group. Follow WeMark’s publication for more updates from them.
The Internet has helped people to work independently in the last decades, Blockchain is likely to help much more people in the coming decades.
Claps Please
April 8, 2018
Hi Karen,
Hi Karen,
We are sheeps in the middle of wolves who are disguised as sheeps. Or we have wolves disguised as shepherds.

April 6, 2018
Things You Need to Know About Facebook and Mass Manipulation

As the number of websites increased on the internet, the registration process became redundant. You had to remember multiple usernames and passwords. This became a serious problem for users and websites. If the onboarding process is not convenient, user drop off rates would be higher.
Facebook and other social networks came up with the idea of sharing their login system. If you have a website, you can easily integrate “Login with Facebook”.
This was a win-win situation for everyone.
For the user because they don’t have to go through the hassle of registration and remembering passwords.For websites because they can easily onboard customers.For facebook because it’s free marketing, a growth hack that will enable them to reach more users.The problem is when they did more than just sharing their login system. Facebook collected a lot of information about the user. The biggest trick facebook ever pulled was users didn’t feel they were giving away so much information. They made a system that allowed users to share their information with applications outside of Facebook. This was done with the consent of the user.
There was a loophole, it not only allowed a user to share his information but it also allowed him to share his friend’s information. This would happen without the consent of their friends.
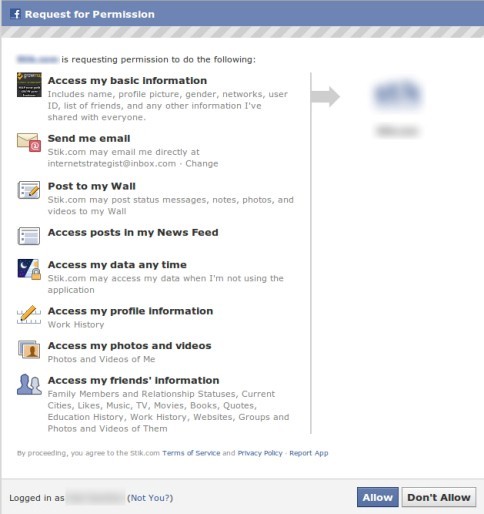
If Mary was using an app that uses Facebook’s login, she can permit that app to allow access to her friend’s information. They won’t even know about it.

Moving fast and breaking things came at the cost of user’s privacy. Something they should have put thought into. Facebook later fixed the loophole of allowing people to share information about his/her friends. It was too late though.
The shared login system gained massive adoption, there came a new category of apps called Social Apps. These apps simply used user’s or their friend’s information to accomplish tasks.
Social apps got data effortlessly, things you spoke to your networks since you joined Facebook were given away with a click of a button.

Cambridge Analytica used personality quiz apps to collect information about Facebook’s users. Cambridge Analytica was not the only app which collected such data. There are thousands of such apps and they still hold a lot of data.
These datasets were used to make predictive models.
Amazon uses predictive models to derive insights out of your past purchases and predict the probability of you buying a given product. They later email you with product recommendations.
Predictive models are no rocket science, it is simply based on patterns. Patterns are everywhere, there is a pattern in the way you write, talk, buy etc.
Target Figured Out A Teen Girl Was Pregnant Before Her Father Did. Here target had a massive dataset of purchases made by several people. People who were pregnant had a common pattern in the purchases they made. Simply put they bought the same kind of products. These models are not 100% accurate, but around 85%–95%, that’s good enough.
Here, the personality quiz contained information about the fears of the users. These fears were mapped to the kind of brands and products they like. Once a predictive model is built out of these massive datasets. This process can work two ways.
The brands and product you like can predict your fears. So even though a lot of people didn’t take a personality quiz, their fears could be predicted using their Facebook ‘likes’.
Using people’s fears to manipulate them is one of the tactics of persuasion. This is exploited by politicians and it is evident in their messaging. Read the book Win Bigly by Scott Adams, it is about the weapon-grade persuasive tactics used by Donald Trump.
So combining data science with the psychology of influence, tailored content were created that would make a mass influence for the United States Election, 2017. Facebook allows pinpoint targeting, they not only allow targeting based on age, gender location. But, also to a given set of user IDs.
This is extensively used in India by the political parties. Even trusted media, don’t verify the authenticity of such posts before publishing them.
Fact-Check: Photos Claiming Dalits Beat To Death A Jodhpur Policeman Are FakeImage Of The Youth Shared By India TV, Journalist Kanchan Gupta Is Not Of A Boy Named 'Abdul Jamal Khan'https://medium.com/media/154aca9375a30df5348df39651622aa7/hrefFacebook built a system to manipulate us. They apologised and are claiming to improve things. There is something even worse, you need to know.
When you browse through newsfeed, spend time on each post, make comments, send private messages to your friends, etc. You are likely to be tracked and your data is sent to algorithms. Later, tailor contented is pushed to hijack your time and money.

Along with the fight against Racism, Gender Inequality, etc. we need to fight such tech companies who have built evil systems to hijack people.
Don’t consume every content from media, remember its only someone’s opinion, sometimes a lie.
Claps Please
Things You Need to Know About Facebook and Mass Manipulation

As the number of websites increased on the internet, the registration process became redundant. You had to remember multiple usernames and passwords. This became a serious problem for users and websites. If on boarding process is not convenient, user drop off rates would be higher.
Facebook and other social networks came up with the idea of sharing their login system. If you are building a web app, you can easily integrate “Login with Facebook”.
This was a win-win situation for everyone.
For the user because they don’t have to go through the hassle of registration and remembering passwords.For websites because they can easily onboard customers.For facebook because it’s free marketing, a growth hack that will enable them to reach more users.The problem is when they did more than just sharing their login system. Facebook collected a lot of information about the user. The biggest trick facebook ever pulled was users didn’t feel they were giving away so much information. They made a system that allowed users to share their information to applications outside Facebook. This was however done with the consent of the user.
There was a loop hole, it not only allowed a user to share his information but it also allowed him to share his friend’s information. This would happen without the consent of their friends.

If Mary was using an app that uses Facebook login, she can permit that app to allow access to her friend’s information. Her friends won’t even know about it.

Moving fast and breaking things came at the cost of user’s privacy. Something they should have put thought into. Facebook later fixed the loophole of allowing people to share information about his/her friends. It was too late though.
The shared login system gained massive adoption, there came a new category of apps called Social Apps. These apps simply used user’s or their friend’s information to accomplish tasks.
Most social apps got data effortlessly, things you spoke to your networks since you joined Facebook were given away with a click of a button.

Cambridge Analytica used personality quiz apps to collect information about Facebook’s users. Cambridge Analytica was not the only app which collected such data. There are thousands of such apps and they still hold a lot of data.
These datasets were used to make predictive models.
Amazon uses predictive models to derive insights out of your past purchases and predict the probability of you buying a given product. They later email you with product recommendations.
Predictive models are no rocket science, it simply based on patterns. Patterns are everywhere, there is a pattern in the way your write, talk, walk, etc.
Target Figured Out A Teen Girl Was Pregnant Before Her Father Did. Here target had a massive dataset of purchases made by several people. People who were pregnant had a common pattern in the purchases they made. Simply put they bought the same kind of products. These models are not 100% accurate but around 85%–95%, that’s good enough.
Here, the personality quiz contained information about the fears of the users. These fears were mapped to the kind of brands and products they like. Once a predictive model is built out of these massive datasets. This process can work two ways.
The brands and product you like can predict your fears. So even though a lot of people didn’t take personality quiz, there fears could be predicted using their facebook ‘likes’.
Using people fears to manipulate them is one of the tactics of persuasion. This is exploited by politicians and it is evident in their messaging. Read the book Win Bigly by Scott Adams, it is about the weapon-grade persuasive tactics used by Donald Trump.
So combining data science with the psychology of influence, tailored content were created that would make mass influence for the United States Election, 2017. Facebook allows pinpoint targeting, they not only allow targeting based on age, gender location. But, also to a given set of user IDs.
This is extensively used in India by the political parties. Even trusted media, don’t verify the authenticity of such posts before publishing them.
Fact-Check: Photos Claiming Dalits Beat To Death A Jodhpur Policeman Are FakeImage Of The Youth Shared By India TV, Journalist Kanchan Gupta Is Not Of A Boy Named 'Abdul Jamal Khan'https://medium.com/media/154aca9375a30df5348df39651622aa7/hrefFacebook built a system to manipulate us. They apologised and are claiming to improve things. There is something even worse, you need to know.
When you browse through newsfeed, spend time on each post, make comments, send private messages to your friends, etc. You are likely to be tracked and your data is sent to algorithms. Then, tailor contented is pushed to hijack your time and money.

Along with the fight against Racism, Gender Inequality, etc. we need to fight such tech companies who have built evil systems to hijack people.
Don’t consume every content from media, remember its only someone’s opinion, sometimes even a lie.
Claps Please
April 5, 2018
A Beginner’s Guide to ICO
 A Short and Simple Guide for ICO Beginners
A Short and Simple Guide for ICO Beginners Mary ( Credits : Peony Bloom from the Noun Project)
Mary ( Credits : Peony Bloom from the Noun Project)Mary wants to start an apparel store online. She needs funding, around $5000. She’s young and still in college. She doesn’t have connections with big investors. She has some close friends but they can only make small investments.
Her friends are read to persuade their networks to invest if Mary can offer them something good.
Mary thought that was a great idea. She can use the investments to build her store and offer investors her products or discounts to apparels.
In order to do that, Mary needs to make a note of their contributions. Give them a receipt or a token that is a proof of their contribution. Investors can produce the token at a later date for apparels or discounts.
 Token (Credits : Dayan Yari from the Noun Project)
Token (Credits : Dayan Yari from the Noun Project)The token simply says Mary owes the token holder its value in the future.

This is the basic idea of an ICO(Initial Coin Offering). ICOs has some properties that make them incredible.
Solves The Problem of TrustMary’s friends might trust her with their investments. But its difficult for their networks to trust her. Let’s see how ICOs solve the problem of trust.
 Credits: Meaghan Hendricks from the Noun Project
Credits: Meaghan Hendricks from the Noun ProjectICO is a computer program that issues tokens for investment. The computer program is a set of instructions.
If the buyers pay x coins thenIssue him y coins
Like an agreement between Mary and the buyer. This computerised agreement is called a smart contract.
This computerised agreement once prepared cannot be altered. This is because unlike traditional internet services, the computer program or the smart contract doesn’t lie in a computer owned by Mary.
The program is replicated across thousands of computers in the network. Once the program is deployed, buyers will be able to buy tokens. The token transaction data is also replicated over the network.
 Credits : Priyanka from the Noun Project
Credits : Priyanka from the Noun ProjectThis information are stored in blocks and linked together, hence called “BlockChain”.
A Beginner’s Guide to Blockchain
Here the investor is not trusting Mary, instead computers. Mary cannot manipulate the transaction data. This doesn’t completely solve the problem of trust. Lot of scamsters have launched ICO, issued tokens and vanished. Be careful when you invest in an ICO.
Token ExchangeSeeing Mary’s success , Sara launched her ICO for an e-learning platform. You can exchange Mary’s tokens for Sara’s tokens.
 Credits : Guillaume Berry from the Noun ProjectThe Way Ahead
Credits : Guillaume Berry from the Noun ProjectThe Way AheadICOs in the future are likely to gain massive adoption. Because ICOs enable anyone living anywhere invest in an idea they believe. If you want to learn to program smart contracts, I recommend you to take a look at Zastrin.
Zastrin | Learn Ethereum programming by doing real-world projects
If you are a total beginner to Cryptocurrencies and Blockchain, I recommend you to have a look at CryptoManiaks.
Claps Please
April 4, 2018
A Beginner’s Guide to ICO
 A Short and Simple Guide for ICO Beginners
A Short and Simple Guide for ICO Beginners Mary ( Credits : Peony Bloom from the Noun Project)
Mary ( Credits : Peony Bloom from the Noun Project)Mary wants to start an apparel store online. She needs funding, around $5000. She’s young and still in college. She doesn’t have connections with big investors. She has some close friends but they can only make small investments.
Her friends are read to persuade their networks to invest if Mary can offer them something good.
Mary thought that was a great idea. She can use the investments to build her store and offer investors her products or discounts to apparels.
In order to do that, Mary needs to make a note of their contributions. Give them a receipt or a token that is a proof of their contribution. Investors can produce the token at a later date for apparels or discounts.
 Token (Credits : Dayan Yari from the Noun Project)
Token (Credits : Dayan Yari from the Noun Project)The token simply says Mary owes the token holder its value in the future.

This is the basic idea of an ICO(Initial Coin Offering). ICOs has some properties that make them incredible.
Solves The Problem of TrustMary’s friends might trust her with their investments. But its difficult for their networks to trust her. Let’s see how ICOs solve the problem of trust.
 Credits: Meaghan Hendricks from the Noun Project
Credits: Meaghan Hendricks from the Noun ProjectICO is a computer program that issues tokens for investment. The computer program is a set of instructions.
If the buyers pay x coins thenIssue him y coins
Like an agreement between Mary and the buyer. This computerised agreement is called a smart contract.
This computerised agreement once prepared cannot be altered. This is because unlike traditional internet services, the computer program or the smart contract doesn’t lie in a computer owned by Mary.
The program is replicated across thousands of computers in the network. Once the program is deployed, buyers will be able to buy tokens. The token transaction data is also replicated over the network.
 Credits : Priyanka from the Noun Project
Credits : Priyanka from the Noun ProjectThis information are stored in blocks and linked together, hence called “BlockChain”.
A Beginner’s Guide to Blockchain
Here the investor is not trusting Mary, instead computers. Mary cannot manipulate the transaction data. This doesn’t completely solve the problem of trust. Lot of scamsters have launched ICO, issued tokens and vanished. Be careful when you invest in an ICO.
Token ExchangeSeeing Mary’s success , Sara launched her ICO for an e-learning platform. You can exchange Mary’s tokens for Sara’s tokens.
 Credits : Guillaume Berry from the Noun ProjectThe Way Ahead
Credits : Guillaume Berry from the Noun ProjectThe Way AheadICOs in the future are likely to gain massive adoption. Because ICOs enable anyone living anywhere invest in an idea they believe. If you want to learn to program smart contracts, I recommend you to take a look at Zastrin.
Zastrin | Learn Ethereum programming by doing real-world projects
If you are a total beginner to Cryptocurrencies and Blockchain, I recommend you to have a look at CryptoManiaks.
Claps Please
March 29, 2018
Hear from the Techie Who Launched an ICO

I always wanted to contribute in the early stages of a startup. This is basically what ICO enables.
In my past stories, I have been writing content without practical knowledge. I don’t have experience in launching an ICO, I thought of interviewing someone who has experience in building and launching an ICO. Gilad was happy to help me out.
We have with us Gilad Menashe, CTO of Vanywhere.
Tell us a few words about yourself?I have over 15 years of experience in internet technologies, security, mobile, SAAS, Blockchain technologies, AWS, web applications and computer vision. I am managing development groups for 14 years and was a VP of R&D for the past 9 years where I developed a product which became the company’s flagship and a key factor in turning them into a technologically superior market leader.
My work has won multi-million dollar contracts with customers including NASA, Boeing, United Airlines, American Airlines, the Canadian Air Force, and Israel Defense Forces among others. I have also served in the Israeli Defense Forces Intelligence Corps (8200) as part of the development team creating (C / C++) embedded (Hardware) and desktop applications.Wow! When did you first hear about Blockchain and ICOs?
Two years ago I had the chance to see how smart contract looks like and I immediately fall in love with the idea.
Well, who wouldn’t? Smart Contrant is an ingenious idea. For those of you who don’t know smart contracts, Don’t worry, I can explain.
 Credits : xkcd
Credits : xkcdA normal contract is pretty dumb, It doesn’t enforce itself. You need first pay a lawyer to make a contract. Then if a party disagree on the agreement, you are supposed to again pay the lawyer to fight for you. This come at the expense of time and money.
Smart contracts are computerised contracts that enforce itself.
For Eg: Mark hasn’t paid his rent for five months. When Sara questions he promise to pay later. She is helpless and is unable to afford a lawyer. Courts take eight months to almost a year to enforce action. The only option is to persuade Mark.
If they made the agreement on a smart contract, the computer code will transfer money, from Mark’s account to Sara’s account on the agreed day of the month. It doesn’t require Mark’s consent the second time.
This would save a lot of Sara’s money and time. She doesn’t have to hire a lawyer and wait for months or years to get Justice.
 Credits : xkcd
Credits : xkcdSmart contracts don’t eliminate lawyers but it eliminates unnecessary lawsuits. Thus saving the money of honest people and precious time of the judiciary.
This is the idea Gilad fall in love with.
I agree with you Gilad, smart contracts are brilliant! Tell us about Vanywhere? How does it help people?As a user Vanywhere lets you connect live with someone. Someone who can guide you through a process, relate to you and give you his full attention and expertise. As a Skiller, Vanywhere allow you to share your skill with the world, help people, and monetise that process into cryptocurrency.Do you use smart contracts in Vanywhere?
Of course, the smart contract handles both payments and the rating system. When a call is initiated, the smart contract collects payment from the user and holds it for 48 hours, at which point it is released the Skiller.
The purpose of this 48 hour cooling period is to create a window for disputes to be raised and resolved, should they occur. If the user is satisfied with the service they received, the funds will automatically be released to the Skiller within 48 hours. If the user is dissatisfied, they can register a dispute which the Vanywhere team will investigate.
When resolving disputes, Vanywhere will consider the records of each party, and hold the tokens until the dispute is resolved. In the event that a Skiller gets a 5 star rating from a user, the tokens will be released to them immediately, without a cooling period.
 Credits : xkcdWhy did Vanywhere choose to launch an ICO?
Credits : xkcdWhy did Vanywhere choose to launch an ICO?ICOs enables anyone living anywhere who believes in our idea to easily participate in our token sale. Smart contracts ensure our contributors are issued VANY tokens seamlessly after payment. The other reason was the payment method in our platform is based on cryptocurrency. So it was just natural to raise funds via ICO. Moreover, cryptocurrency allows you to process micro-payments, without the high fees in centralised platforms.What are the challenges you faced in launching an ICO?
One of our technical challenges was how to use best all QTUM advantages and maximise the full potential of Vanywhere platform we also had to deal with a complex mechanism for handling disputes in the smart contract.
QTUM seems to be promising. It is like a cross-platform blockchain for smart contracts. In the earlier days of software development, you had to code separately for Windows OS, Mac, Linux, Mobile OS etc. Later, Java came up with cross-platform support, you can code once and deploy it on multiple platforms easily.
QTUM does something similar across different Blockchains like Bitcoin and Ethereum.This is technically not accurate, but I assume you get the idea. It basically supports interoperability. The benefit of using QTUM is if there is an advancement in Bitcoin or Ethereum (of course there will be). You would be able to make use of their features seamlessly.
 Credits : xkcdHow can one benefit by contributing in your ICO?
Credits : xkcdHow can one benefit by contributing in your ICO?They will have the chance to be part of a growing community where they can use their tokens to buy services and even get paid in tokens for providing service.
I understand, what I like about VANY tokens compared to other tokens is its frequent use case. I am presently looking for someone to teach me guitar remotely. I am sure this would apply to people from different backgrounds like art, music, programming, travel, cooking, marketing, etc
What’s advice can you offer who are in the process of launching their first ICO?From the technical perspective your top priority should be security and that the ease of use, we want to give the contributors a very clear process and try to reduce to minimum the chance of making mistakes while protecting him from all the predators out there, things to consider are: Phishing sites, DDOS, secure all the company and employee community accounts.How can we get in touch with you?
You are more than welcome to join visit our telegram (https://t.me/vanywhere) and visit our website: https://www.vanywhere.com
Thank you, Gilad Menashe.
Claps Please



