Gennaro Cuofano's Blog, page 119
January 28, 2022
What Is Pre-seed Funding? Pre-seed Funding In A Nutshell


In a startup, external funding from angel investors and then venture capitalists progresses in a series of stages including seed, Series A, Series B, Series C, and so forth. By definition, any round of funding that occurs before the seed round is called pre-seed funding. Pre-seed funding, therefore, is an early funding round in the life of a startup and is used to fund product development in exchange for equity in the company.
Understanding pre-seed fundingSince pre-seed funding is provided in the very early stages of a startup’s journey, the idea of acquiring it is to sustain the launch of the business and, ideally, take it to the next milestone.
Capital is normally provided by the founders themselves or by friends and family members and may range anywhere between $10,000 and $250,000. However, some startups also secure funding from angel investors, accelerator programs, incubator programs, and venture capital funds. Once the capital has been secured, entrepreneurs seek to make it last as long as possible.
Irrespective of the funding source, however, it is important the founders remain accountable to their investors at all times. In most cases, the pre-seed investment will last around 12 months or up to 18 months if there are unforeseen circumstances. Extensions beyond 18 months usually indicate that the startup has set goals that were too ambitious.
When should a startup raise pre-seed funding?While there are no concrete conditions for raising pre-seed funding, most startups will share some of the following characteristics:
A minimum viable product (MVP) has been developed and is displaying tentative signs of traction with users.Data or proof of product-market fit has been identified.There is a need or readiness to recruit critical additional staff.The presence of a capable founding team with relevant skills and expertise.Cash is required to build a prototype.The start-up has made its first revenue.How can a business attract pre-seed funding?Most startups will find the process of attracting pre-seed funding easier if they are already generating sales. However, for those that don’t have a working product, it can be helpful to consider the following pointers:
Secure an introduction – to connect with an investor who isn’t a friend or family member, entrepreneurs can connect with a potential investor by seeking an introduction from an individual they trust. For best results, this should be someone the investor has worked with in the past.Personality – investors want to see certain personality traits in the startup’s founders. These include a propensity for risk-taking and the passion and motivation to make their dreams a reality.Relevant qualifications – similarly, investors look for startups with a founder who is surrounded by a qualified team that complements their skillset. A solo entrepreneur with a background in accountancy, for example, will have trouble attracting pre-seed funding since they lack product development experience. First-time entrepreneurs can also bolster their resumes if they hold a relevant Bachelor’s degree or previously worked at a tech company.Detailed funding pitch – this is a chance for the entrepreneurs to tell the story of their startup and where they see it heading in the future. The pitch must detail the problem the company is solving and how it intends to solve it. It must also provide detail on the estimated market size, business model, competitive advantage, key milestones, and projected revenue and customer growth.Key takeaways:Pre-seed funding is an early funding round in the life of a startup. It is used to fund product development in exchange for equity in the company.Pre-seed investment lasts approximately 12 months or up to 18 months if there are unforeseen circumstances. Extensions beyond this timeframe usually indicate overly ambitious entrepreneurs.Pre-seed funding can be obtained by securing an introduction from an individual known to the investor and crafting a funding pitch that gives an overview of the company’s goals and visions. It is also important that entrepreneurs have the personality and relevant qualifications to drive the company forward.Main Free Guides:
Business ModelsBusiness CompetitionBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkConnected ConceptsAngel Investing
Venture Capital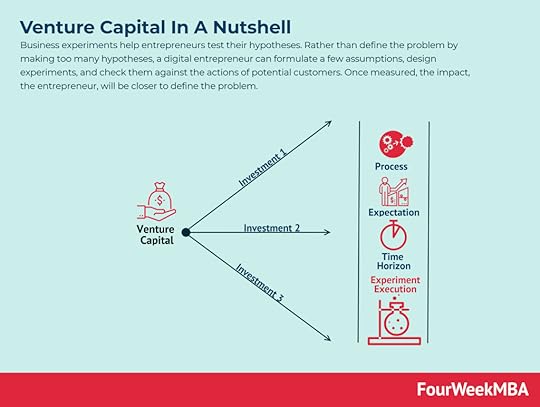 A venture capitalist generally invests in companies and startups which are still in a stage where their business model needs to be proved viable, or they need resources to scale up. Thus, those companies present high risks, but the potential for exponential growth. Therefore, venture capitalists look for startups that can bring a high ROI and high valuation multiples.Economic Moat
A venture capitalist generally invests in companies and startups which are still in a stage where their business model needs to be proved viable, or they need resources to scale up. Thus, those companies present high risks, but the potential for exponential growth. Therefore, venture capitalists look for startups that can bring a high ROI and high valuation multiples.Economic Moat Economic or market moats represent the long-term business defensibility. Or how long a business can retain its competitive advantage in the marketplace over the years. Warren Buffet who popularized the term “moat” referred to it as a share of mind, opposite to market share, as such it is the characteristic that all valuable brands have.Meme Investing
Economic or market moats represent the long-term business defensibility. Or how long a business can retain its competitive advantage in the marketplace over the years. Warren Buffet who popularized the term “moat” referred to it as a share of mind, opposite to market share, as such it is the characteristic that all valuable brands have.Meme Investing Meme stocks are securities that go viral online and attract the attention of the younger generation of retail investors. Meme investing, therefore, is a bottom-up, community-driven approach to investing that positions itself as the antonym to Wall Street investing. Also, meme investing often looks at attractive opportunities with lower liquidity that might be easier to overtake, thus enabling wide speculation, as “meme investors” often look for disproportionate short-term returns.Payment for Order Flow
Meme stocks are securities that go viral online and attract the attention of the younger generation of retail investors. Meme investing, therefore, is a bottom-up, community-driven approach to investing that positions itself as the antonym to Wall Street investing. Also, meme investing often looks at attractive opportunities with lower liquidity that might be easier to overtake, thus enabling wide speculation, as “meme investors” often look for disproportionate short-term returns.Payment for Order Flow Payment for order flow consists of a “kickback” or commission that the broker routing customers to a market maker (in charge of enabling the bid and ask price) will pay a commission to the broker as a sort of market-making fee.What is a SPAC
Payment for order flow consists of a “kickback” or commission that the broker routing customers to a market maker (in charge of enabling the bid and ask price) will pay a commission to the broker as a sort of market-making fee.What is a SPAC A special purpose acquisition company (SPAC) is a company with no commercial operations that are created to raise capital through an IPO to acquire another company. The SPAC is also called for that reason a “blank check company” as it will use the money provided by investors to enable private companies to go public via the SPAC.
A special purpose acquisition company (SPAC) is a company with no commercial operations that are created to raise capital through an IPO to acquire another company. The SPAC is also called for that reason a “blank check company” as it will use the money provided by investors to enable private companies to go public via the SPAC.The post What Is Pre-seed Funding? Pre-seed Funding In A Nutshell appeared first on FourWeekMBA.
January 27, 2022
What Are Hard Skills And Soft Skills? Hard skills vs. Soft Skills In A Nutshell


Hard skills describe teachable or technical abilities that are learned in an educational institution, book, or in the workplace. Soft skills, on the other hand, are those that are used to interact with other people. For this reason, they are sometimes referred to as interpersonal skills or people skills.
Understanding hard skillsHard skills describe the technical abilities an interview candidate may list on their resume. These skills demonstrate competency in a specific job, career, or industry and must be learned in a formal or informal education setting. In other words, no one is born with hard skills.
For example, a restaurant worker will need to possess formal barista and point-of-sale system training as part of their role. An international sales representative may need to be fluent in the language of the country where their most important clients reside.
Hard skills tend to be measurable, easily quantified, and can be described using numerical or yes/no criteria. Examples include:
SEO marketing.User interface design.Statistical analysis.Database management.Forklift operation.Phlebotomy. Blockchain. Cash flow management.Coding.With business now dominated by technology, it can be easy to assume that most roles emphasize hard skills and technical proficiency. However, there are some skills that technology cannot reproduce. We will take a look at these in the next section.
Understanding soft skillsSoft skills are harder to quantify than hard skills because they refer to how we interact with others. Many of these skills are innate to our personalities, but we can also learn soft skills to bolster our job prospects or improve the quality of our relationships with others.
In the workplace, soft skills are desirable because they can be used in any context irrespective of the industry or the organization itself. What’s more, employers look for candidates with soft skills because they are essential to creating a harmonious and positive company culture.
Some positions may also place a greater emphasis on soft skills than on hard skills. For example, it is more important for a human resources manager to be empathetic and a great communicator than it is for them to be able to analyze data or use specialized software.
Examples of soft skills include:
Communication.Collaboration.Problem-solving.Leadership.Active listening.Critical thinking.A willingness to learn.Self-motivation or organization.Creativity.Dependability.Key takeaways:Hard skills describe teachable or technical abilities that are learned in an educational institution, book, or in the workplace. Conversely, soft skills are those that are used to interact with other people and can be more difficult to quantify.Hard skills are increasingly important in many technology-based roles where technical proficiency is key. Examples include coding, blockchain, and forklift operation. Many individuals possess innate soft skills that allow them to relate to others positively, but the good news is that most soft skills can be learned to bolster a resume. Examples include communication, creativity, critical thinking, leadership, and active listening.Main Free Guides:
Business ModelsBusiness CompetitionBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkThe post What Are Hard Skills And Soft Skills? Hard skills vs. Soft Skills In A Nutshell appeared first on FourWeekMBA.
7 Types of companies You Must Know
There are various types of companies operating in the United States today. These range from simple sole proprietorships to more complex and involved corporations. Since nearly every company once existed as a small business, entrepreneurs need to determine which company structure is most suitable for their circumstances as the business grows. Each comes with various legal implications that pertain to personal liability protection and tax exemptions, among other things.
Sole proprietorshipsSole proprietorships consist of one individual and are the simplest business structure in North America. Since there is no distinction between the person behind the business and the business itself, a sole proprietor is financially liable for any debts or damages that are incurred.
Sole proprietors are not required to take any formal action to form this type of company. However, they will still need to obtain licenses and permits that are state and industry-specific. What’s more, they will also have to file what is known as a fictitious name if they wish to do business under a name that is not their personal or given name.
Limited liability companies (LLCs)Limited liability companies are business entities characterized by the separation of the founders of the business and their personal liability. In more specific terms, the personal assets of the founders are protected in the event the business suffers any kind of financial damage.
The individual has flexibility when incorporating an LLC and can choose any business structure they want. They may elect to choose a general partnership or a board of directors structure – or another structure that falls somewhere in between.
There are also various perks to the limited liability company, including simpler taxation at the personal level and taxes that can be reduced if the founder owns multiple real estate properties under different LLCs.
Limited liability partnerships (LLPs)Limited liability partnerships are similar to limited liability companies in that the founders can structure the company as they see fit. LLPs are characterized by perpetual succession. This means the existence of the company does not change if one partner resigns, for example.
In a limited liability partnership, each founder has rights and responsibilities that are laid out in a formal agreement according to the particular state jurisdiction. Each is liable for any financial problems the company experiences in proportion to their investment in the company itself. They are not responsible for the harmful behavior of other partners, such as negligence or fraud.
S CorporationsS Corporations are those that choose to pass corporate income, deductions, losses, and credits to their shareholders. Shareholders complete their personal tax returns by reporting the flow-through of income and losses, which allows the S Corporation to avoid double taxation on its corporate income.
To qualify as an S Corporation, the company needs to satisfy these criteria:
Consist of no more than 100 allowable shareholders. Here, this refers to individuals, certain trusts, and estates. Possess only one class of stock. Be a corporation that operates domestically.Not be an ineligible corporation. These include insurance companies, some sales corporations, and certain financial institutions.C CorporationsC Corporations are one of the more common types of corporations in the United States. Unlike the S Corporation, the shareholders of a C Corporation are taxed separately and the corporation itself cannot avoid paying income tax.
C Corporations offer unlimited growth potential through the sale of shares and there is no limit to the number of individual shareholders it can have. However, these corporations are expensive to register and they are subject to increased government scrutiny. This is due to complicated tax rules and the presence of limited liability for the owners of the firm and its investors.
B CorporationsB Corporations are for-profit companies that are certified to meet high standards of transparency, accountability, and social and environmental stewardship. While turning a profit is important for a B Corp, it also prioritises other factors such as workers, customers, community, and governance.
B Corp certification is a highly selective and rigorous process, with corporations required to prove their worthiness every three years to maintain their status.
Non-profit corporationsNon-profit corporations share structural similarities to traditional corporations. They tend to have a board of directors in addition to financial backers or donors. But, as the name implies, non-profit corporations do not generate any profit and must only be created in support of a specific, public cause.
These corporations do not pay corporate or federal taxes and are allowed to receive funding from a diverse range of sources, including other corporations, philanthropists, and grants.
Key takeaways:There are various types of companies operating in the United States today. These range from simple sole proprietorships to more complex and regulated corporations.In a sole proprietorship, there is no distinction between the founder and the business itself. This means the sole proprietor is financially liable for any debts or damages that are incurred. Limited liability companies (LLCs) and limited liability partnerships (LLPs) provide varying degrees of liability protection for companies with two or more members.Various corporation types also exist in the United States. Some examples include S Corporations, C Corporations, B Corporations, and non-profit corporations.Main Free Guides:
Business ModelsBusiness CompetitionBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkThe post 7 Types of companies You Must Know appeared first on FourWeekMBA.
What is Brand Dilution? Brand Dilution In A Nutshell


According to inbound marketing platform HubSpot, brand dilution occurs “when a company’s brand equity diminishes due to an unsuccessful brand extension, which is a new product the company develops in an industry that they don’t have any market share in.” Brand dilution, therefore, occurs when a brand decreases in value after the company releases a product that does not align with its vision, mission, or skillset.
Understanding brand dilutionBrand dilution occurs when a business releases a product that is closely related to the product consumers most associate it with. When the new product does not live up to the brand promise of the original product – perhaps because of poor quality or unrelatedness – the brand becomes devalued among consumers.
What causes brand dilution?Here are the top four reasons for a brand becoming diluted:
Licensing – this describes a trademark or copyrighted asset that is rented or leased for use in a product or service. Brand dilution occurs when the product in the licensing agreement does not reflect the image or expected quality of the brand itself.Experimentation – brand dilution also occurs when a business enters a market where it has no presence or expertise. Some businesses release unrelated products that have no connection to their core products. Others release incompetent products because they lack the required industry experience. While expansion is a necessary evil to some extent, businesses that stray too far from what they know best run the risk of dilution.Lack of brand control – sizeable companies with hundreds or even thousands of employees representing the brand may also experience dilution. This can be reflected in outdated logos or slogans, inconsistent social media messaging, and other activities that are not representative of the brand.Inconsistency – if, for example, consumers associate a brand with premium, hand-made products, dilution will occur if the company decides to release mass-produced products that are of poorer quality.Brand dilution examplesSome of the more famous examples of brand dilution include:
CadburyEnglish chocolatier Cadbury is a brand most consumers associate with premium quality chocolate and candy products. However, for over 20 years, the company sold instant mashed potato mix. While the product was reasonably successful, it diluted the perceived quality of the Cadbury brand.
Harley-DavidsonWhile motorcycle manufacturer Harley-Davidson also sells helmets, bandanas, shirts, and jackets, the company went too far when it released a perfume and cologne range in the 1990s. The products were attractively packaged but did not reflect the values the brand had cultivated over many decades.
WindowsMicrosoft released the Windows Phone in 2010 at a time when the market was oversaturated with similar products. The move, which involved the creation of new teams and partnerships with mobile brands, took important resources away from Microsoft’s software development and was abandoned a few years later.
Michael JordanWhen NBA superstar Michael Jordan decided to retire from basketball and play baseball instead, his brand suffered. Jordan was for the most part unsuccessful as a baseballer and returned to the NBA to restore his brand image.
Key takeaways:Brand dilution occurs when a brand decreases in value after the company releases a product that does not respect its mission, vision, or skillset.Brand dilution is caused by improper licensing agreements, experimentation, a lack of brand control, and inconsistency.Real-world examples of brand dilution can be seen in companies such as Cadbury, Harley-Davidson, and Microsoft. NBA star Michael Jordan also damaged his brand when he retired from the sport and started playing baseball.Main Free Guides:
Business ModelsBusiness CompetitionBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkThe post What is Brand Dilution? Brand Dilution In A Nutshell appeared first on FourWeekMBA.
What Is Field Marketing? Field Marketing In A Nutshell


Field marketing is a general term that encompasses face-to-face marketing activities carried out in the field. These activities may include street promotions, conferences, sales, and various forms of experiential marketing. Field marketing, therefore, refers to any marketing activity that is performed in the field.
Understanding field marketingField marketing is used to increase brand awareness, generate leads, and build customer relationships. It is the domain of experienced and well-trained marketers who are tasked with interacting with the brand’s target audience to encourage them to make a purchase decision.
These marketers may work in the B2B context and as a result, possess marketing and sales expertise to meet with prospects across multiple touchpoints. They may also work in the B2C context and present themselves in locations where the ideal buyer tends to congregate.
Field marketing campaign typesIn truth, there are many different settings in which a field marketing campaign can be run. Some of these include:
Experiential marketing – a face-to-face strategy where the consumer is immersed in a product or service to engage them with a brand.Product demonstrations – this is a common approach that many consumers are now averse to. However, free samples and giveaways are still effective in some situations if the consumer is also able to experience the brand hands-on.Conferences – for B2B campaigns, it can be useful to offer educational experiences at conferences to build brand awareness.Tradeshows – another approach well suited to B2B brands. In this case, businesses demonstrate their products and services to prospective customers at industry-specific tradeshows.VIP dinners – for a more intimate form of field marketing, exclusive restaurant dinners for very important prospects can also be effective in turning them into customers.Direct selling – where brand representatives make sales at the point where the interaction is made. This is sometimes used in combination with demos if the prospect has expressed interest in the product or service.Retail audits – not every field marketing strategy must be customer-facing. Retail audits involve companies visiting retail stores to collect data on the way their products are displayed, signed, and promoted. This allows them to determine the effectiveness of in-store marketing and adjust the strategy if necessary.Field marketer responsibilitiesSome consider field marketers to be more like salespeople than marketers. As we noted earlier, however, the field marketer is a well-trained and specialist role that combines elements of both sales and marketing.
Here are some of the main responsibilities of a field marketer:
Researching, planning, and executing the delivery of field marketing campaigns.Ensuring they possess detailed knowledge of products and services.The monitoring of industry trends or the emergence of new competitors.Negotiate mutually beneficial deals with third-party retailers and partners with respect to merchandise and promotional display placement.Manage social media accounts for each campaign.Share important lead and customer intel with sales departments. Key takeaways:Field marketing refers to any marketing activity that is performed in the field to increase brand awareness, generate leads, and build customer relationships. It may occur in both a B2B and B2C context.Field marketing campaign types include tradeshows, conferences, VIP dinners, retail audits, direct selling, product demonstrations, and experiential marketing. Note that not all campaigns are necessarily customer-facing.Field marketers possess a blend of sales and marketing skills, which makes the role highly specialized. Some of their duties include the research, planning, and execution of campaigns and the monitoring of industry trends or the emergence of new players. They must also be able to negotiate beneficial outcomes with key stakeholders.Connected Business Concepts Content marketing is one of the most powerful commercial activities which focuses on leveraging content production (text, audio, video, or other formats) to attract a targeted audience. Content marketing focuses on building a strong brand, but also to convert part of that targeted audience into potential customers.
Content marketing is one of the most powerful commercial activities which focuses on leveraging content production (text, audio, video, or other formats) to attract a targeted audience. Content marketing focuses on building a strong brand, but also to convert part of that targeted audience into potential customers.
 Integrated marketing describes the process of delivering consistent and relevant content to a target audience across all marketing channels. It is a cohesive, unified, and immersive marketing strategy that is cost-effective and relies on brand identity and storytelling to amplify the brand to a wider and wider audience.
Integrated marketing describes the process of delivering consistent and relevant content to a target audience across all marketing channels. It is a cohesive, unified, and immersive marketing strategy that is cost-effective and relies on brand identity and storytelling to amplify the brand to a wider and wider audience.
 Grassroots marketing involves a brand creating highly targeted content for a particular niche or audience. When an organization engages in grassroots marketing, it focuses on a small group of people with the hope that its marketing message is shared with a progressively larger audience.
Grassroots marketing involves a brand creating highly targeted content for a particular niche or audience. When an organization engages in grassroots marketing, it focuses on a small group of people with the hope that its marketing message is shared with a progressively larger audience.
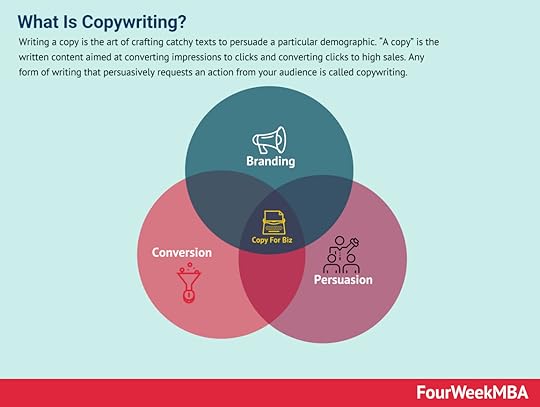 Writing a copy is the art of crafting catchy texts to persuade a particular demographic. “A copy” is the written content aimed at converting impressions to clicks and converting clicks to high sales. Any form of writing that persuasively requests an action from your audience is called copywriting.
Writing a copy is the art of crafting catchy texts to persuade a particular demographic. “A copy” is the written content aimed at converting impressions to clicks and converting clicks to high sales. Any form of writing that persuasively requests an action from your audience is called copywriting.
 Buzz marketing leverages the power of word-of-mouth advertising to create products or services with enough novelty that they go viral. In many cases, buzz marketing leverages on versatile content that can easily scale and be readapted to various contexts and fear of missing out (FOMO) to amplify the effect of word-of-mouth campaigns.
Buzz marketing leverages the power of word-of-mouth advertising to create products or services with enough novelty that they go viral. In many cases, buzz marketing leverages on versatile content that can easily scale and be readapted to various contexts and fear of missing out (FOMO) to amplify the effect of word-of-mouth campaigns.
 Inbound marketing is a marketing strategy designed to attract customers to a brand with content and experiences that they derive value from. Inbound marketing utilizes blogs, events, SEO, and social media to create brand awareness and attract targeted consumers. By attracting or “drawing in” a targeted audience, inbound marketing differs from outbound marketing which actively pushes a brand onto consumers who may have no interest in what is being offered.
Inbound marketing is a marketing strategy designed to attract customers to a brand with content and experiences that they derive value from. Inbound marketing utilizes blogs, events, SEO, and social media to create brand awareness and attract targeted consumers. By attracting or “drawing in” a targeted audience, inbound marketing differs from outbound marketing which actively pushes a brand onto consumers who may have no interest in what is being offered.The post What Is Field Marketing? Field Marketing In A Nutshell appeared first on FourWeekMBA.
What Is Instructor-led Training? Instructor-led training In A Nutshell


Instructor-led training is a more traditional, top-down, teacher-oriented approach to learning that occurs in online or offline classroom environments. The approach connects instructors with students to encourage discussion and interaction in a group or individual context, with many enjoying ILT over other methods as they can seek direct clarification on a topic from the source. Instructor-led training (ILT), therefore, encompasses any form of training provided by an instructor in an online or offline classroom setting.
Understanding instructor-led trainingFor companies, instructor-led training is also used to train employees on complex topics that require interactive, hands-on experience. Most favor instructor-led training because of its effectiveness in increasing knowledge retention among employees.
Relatively recent data on ILT shows that the method comprises 66% of all corporate training and development. This figure rises to 80% in high-stakes industries such as healthcare, finance, and utilities.
Three types of instructor-led trainingThere are three general types of instructor-led training available today. These include:
Location-dependent – or any form of training provided in a physical environment such as an office, workplace, training center, workshop, classroom, or in the field.Virtual – this describes instructor-led training that is provided in a real-time, virtual environment. Virtual training occurs on video conferencing platforms such as Zoom and has increased in popularity due to the coronavirus pandemic.Blended – a hybrid approach of location-dependent and virtual training that caters to a broader mix of learning styles and facilitates more collaboration and discussion. Education may occur via live webinars, podcasts, videos, quizzes, and in-field or practical exercises that supplement theory-based content.Advantages and disadvantages of instructor-led trainingAdvantagesOpen dialogue – as hinted at earlier, two-way communication between the instructor and student is a hallmark of instructor-led training. This allows the instructor to leverage student queries and ensure they understand the information presented. There is also value in face-to-face interaction and the ability for both parties to read the facial expressions and body language of the other.Less distraction – while remote learning is now extremely popular, it cannot compete with instructor-led training in terms of a distraction-free environment. In a classroom setting where the student is under direct supervision and has often paid to be there, there is a reduced likelihood they’ll be distracted by social media or other temptations.DisadvantagesCost – for companies who sell or utilise instructor-led training, the costs can be significant. Expenses include instructor fees, venue rental, travel expenses, training materials, and instructor-specific refresher courses.Reduced productivity – unlike some forms of virtual training that employees can do in their own time, instructor-led training is normally conducted in business hours and can take several days to complete. For the business, this means reduced productivity as employees undertake the training.Key takeaways:Instructor-led training (ILT) encompasses any form of training provided by an instructor in an online or offline classroom setting.There are three types of instructor-led training: location-dependent, virtual, and blended, which caters to a more diverse range of learning styles and situations.Instructor-led training increases knowledge retention as instructors can adapt their teaching style based on student queries and body language. There are also fewer distractions in a formal classroom setting. However, ILT tends to be costlier for companies, and productivity is reduced when employees are requisitioned for learning.Other Frameworks5E Instructional Model The 5E Instructional Model is a framework for improving teaching practices through discussion, observation, critique, and reflection. Teachers and students move through each phase linearly, but some may need to be repeated or cycled through several times to ensure effective learning. This is a form of inquiry-based learning where students are encouraged to discover information and formulate new insights themselves.Fishbone Diagram
The 5E Instructional Model is a framework for improving teaching practices through discussion, observation, critique, and reflection. Teachers and students move through each phase linearly, but some may need to be repeated or cycled through several times to ensure effective learning. This is a form of inquiry-based learning where students are encouraged to discover information and formulate new insights themselves.Fishbone Diagram The Fishbone Diagram is a diagram-based technique used in brainstorming to identify potential causes for a problem, thus it is a visual representation of cause and effect. The problem or effect serves as the head of the fish. Possible causes of the problem are listed on the individual “bones” of the fish. This encourages problem-solving teams to consider a wide range of alternatives.5 Whys Method
The Fishbone Diagram is a diagram-based technique used in brainstorming to identify potential causes for a problem, thus it is a visual representation of cause and effect. The problem or effect serves as the head of the fish. Possible causes of the problem are listed on the individual “bones” of the fish. This encourages problem-solving teams to consider a wide range of alternatives.5 Whys Method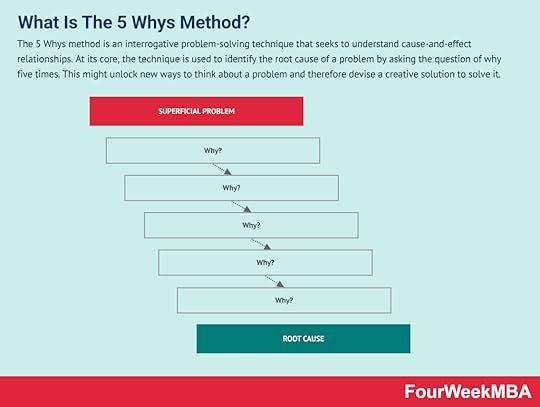 The 5 Whys method is an interrogative problem-solving technique that seeks to understand cause-and-effect relationships. At its core, the technique is used to identify the root cause of a problem by asking the question of why five times. This might unlock new ways to think about a problem and therefore devise a creative solution to solve it.Ansoff Matrix
The 5 Whys method is an interrogative problem-solving technique that seeks to understand cause-and-effect relationships. At its core, the technique is used to identify the root cause of a problem by asking the question of why five times. This might unlock new ways to think about a problem and therefore devise a creative solution to solve it.Ansoff Matrix You can use the Ansoff Matrix as a strategic framework to understand what growth strategy is more suited based on the market context. Developed by mathematician and business manager Igor Ansoff, it assumes a growth strategy can be derived by whether the market is new or existing, and the product is new or existing.Five Product Levels
You can use the Ansoff Matrix as a strategic framework to understand what growth strategy is more suited based on the market context. Developed by mathematician and business manager Igor Ansoff, it assumes a growth strategy can be derived by whether the market is new or existing, and the product is new or existing.Five Product Levels Marketing consultant Philip Kotler developed the Five Product Levels model. He asserted that a product was not just a physical object but also something that satisfied a wide range of consumer needs. According to that Kotler identified five types of products: core product, generic product, expected product, augmented product, and potential product.Growth-Share Matrix
Marketing consultant Philip Kotler developed the Five Product Levels model. He asserted that a product was not just a physical object but also something that satisfied a wide range of consumer needs. According to that Kotler identified five types of products: core product, generic product, expected product, augmented product, and potential product.Growth-Share Matrix In the 1970s, Bruce D. Henderson, founder of the Boston Consulting Group, came up with The Product Portfolio (aka BCG Matrix, or Growth-share Matrix), which would look at a successful business product portfolio based on potential growth and market shares. It divided products into four main categories: cash cows, pets (dogs), question marks, and stars.Read also: Business Strategy, Examples, Case Studies, And Tools
In the 1970s, Bruce D. Henderson, founder of the Boston Consulting Group, came up with The Product Portfolio (aka BCG Matrix, or Growth-share Matrix), which would look at a successful business product portfolio based on potential growth and market shares. It divided products into four main categories: cash cows, pets (dogs), question marks, and stars.Read also: Business Strategy, Examples, Case Studies, And ToolsMain Free Guides:
Business ModelsBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsTech Business ModelThe post What Is Instructor-led Training? Instructor-led training In A Nutshell appeared first on FourWeekMBA.
What is A Cog’s Ladder? The Cog’s ladder In A Nutshell


Cog’s ladder is a model of group development. The ladder was created in 1972 by Procter & Gamble employee George Charrier to help management at the company understand how teams worked to make them more efficient. Cog’s ladder is a model of group formation and behavior that is used to help businesses understand how a team can work to achieve its goals.
Understanding Cog’s ladderCog’s ladder is used by team leaders to provide direction and order in groups of people often characterized by personality clashes, disruptive behavior, and nervous individuals who are reluctant to contribute. It is important to note that Charrier’s approach does not eliminate these negative aspects entirely. Instead, leaders use the ladder to help their teams reach the most productive state as quickly as possible.
The model is quite similar to Bruce Tuckman’s 1965 team development model, which posits that as a team becomes more mature and competent, relationships form between individual team members, and the leader alters their management style to suit.
The five phases of Cog’s ladderCharrier found five phases described a group as it transitioned from the initial meeting to a high-performance team.
The five phases are as follows:
1 – The polite phaseWhen the team comes together for the first time, most individuals will be anxious and hesitant to reveal personal information about themselves.
Some do this because they are nervous, seek approval, or understand the importance of not making a bad first impression. Some prefer to sit back, as it were, and evaluate the personalities of others to predict future team dynamics.
2 – The “Why are we here?” phaseIn the second phase, formal introductions and acquaintances are made and the team leader clarifies what is expected of the group and how it will be achieved.
Roles and responsibilities are assigned and cliques may form as people with similar interests or skills coalesce. Communication becomes more natural as individuals become more comfortable with one another.
3 – The power phaseThe third phase describes the inevitable power struggles that will develop in the group. Dominant personalities may compete for authority and influence as criticism, tension, resistance, and refutation becomes more common.
The team leader must let this occur with only limited intervention as it is a crucial phase in the team’s hierarchical development. Assertive individuals in the group will describe how they think the goal can be achieved, with non-assertive individuals then deciding who to support.
4 – The cooperation phaseOnce a natural hierarchy has been established, increased cooperation between individuals builds momentum as each understands their role in helping the team reach its objectives. As a result, the focus shifts away from the individual and toward group cohesiveness.
Criticism becomes more constructive and a friendlier atmosphere develops as team members see others as their comrades. When conflict does arise, the group works to find a solution that is in the common interest.
5 – The esprit phaseIn the esprit phase, cliques that were formed in the second phase disappear as the group solidifies its collective identity. Strong informal relationships develop between individuals, with mutual feelings of trust, respect, and appreciation.
With all individuals making a concerted and unified effort, significant process toward the goal is made. Since this phase is associated with the highest level of team development, there is typically less reliance on instruction and task delegation from the team leader. Instead, the leader should focus on maintaining efficiency to ensure the work is completed on time and budget without sacrificing quality.
Key takeaways:Cog’s ladder is a model of group formation and behavior that is used to help businesses understand how teams can work to achieve their goals. The ladder was created in 1972 by Procter & Gamble employee George Charrier.Cog’s ladder provides direction and order in groups of people that are often characterized by personality clashes, disruptive behavior, and nervous individuals who are passive and avoid contribution. The ladder does not seek to eliminate these aspects. Rather, it is intended to help team leaders guide subordinates to an efficient state as quickly as possible.Charrier explained Cog’s ladder in terms of five phases: the polite phase, the “Why are we here?” phase, the power phase, the cooperation phase, and the esprit phase.Other Frameworks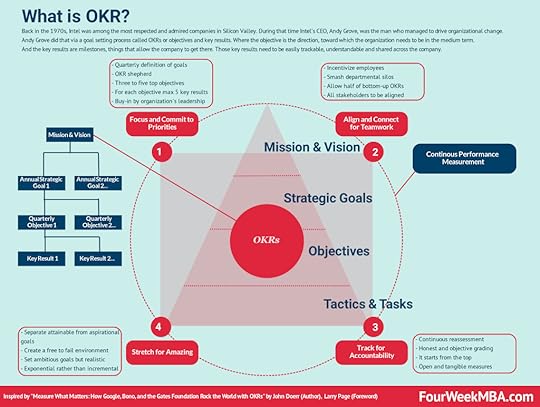 Andy Grove, helped Intel become among the most valuable companies by 1997. In his years at Intel, he conceived a management and goal-setting system, called OKR, standing for “objectives and key results.” Venture capitalist and early investor in Google, John Doerr, systematized in the book “Measure What Matters.”
Andy Grove, helped Intel become among the most valuable companies by 1997. In his years at Intel, he conceived a management and goal-setting system, called OKR, standing for “objectives and key results.” Venture capitalist and early investor in Google, John Doerr, systematized in the book “Measure What Matters.” First proposed by accounting academic Robert Kaplan, the balanced scorecard is a management system that allows an organization to focus on big-picture strategic goals. The four perspectives of the balanced scorecard include financial, customer, business process, and organizational capacity. From there, according to the balanced scorecard, it’s possible to have a holistic view of the business.
First proposed by accounting academic Robert Kaplan, the balanced scorecard is a management system that allows an organization to focus on big-picture strategic goals. The four perspectives of the balanced scorecard include financial, customer, business process, and organizational capacity. From there, according to the balanced scorecard, it’s possible to have a holistic view of the business. The theory was developed by psychologist Edwin Locke who also has a background in motivation and leadership research. Locke’s goal-setting theory of motivation provides a framework for setting effective and motivating goals. Locke was able to demonstrate that goal setting was linked to performance.
The theory was developed by psychologist Edwin Locke who also has a background in motivation and leadership research. Locke’s goal-setting theory of motivation provides a framework for setting effective and motivating goals. Locke was able to demonstrate that goal setting was linked to performance. A SMART goal is any goal with a carefully planned, concise, and trackable objective. To be such a goal needs to be specific, measurable, achievable, relevant, and time-based. Bringing structure and trackability to goal setting increases the chances goals will be achieved, and it helps align the organization around those goals.
A SMART goal is any goal with a carefully planned, concise, and trackable objective. To be such a goal needs to be specific, measurable, achievable, relevant, and time-based. Bringing structure and trackability to goal setting increases the chances goals will be achieved, and it helps align the organization around those goals. Businesses use backcasting to plan for a desired future by determining the steps required to achieve that future. Backcasting is the opposite of forecasting, where a business sets future goals and works toward them by maintaining the status quo.
Businesses use backcasting to plan for a desired future by determining the steps required to achieve that future. Backcasting is the opposite of forecasting, where a business sets future goals and works toward them by maintaining the status quo. Moonshot thinking is an approach to innovation, and it can be applied to business or any other discipline where you target at least 10X goals. That shifts the mindset, and it empowers a team of people to look for unconventional solutions, thus starting from first principles, by leveraging on fast-paced experimentation.
Moonshot thinking is an approach to innovation, and it can be applied to business or any other discipline where you target at least 10X goals. That shifts the mindset, and it empowers a team of people to look for unconventional solutions, thus starting from first principles, by leveraging on fast-paced experimentation.Related Strategy Concepts: Go-To-Market Strategy, Marketing Strategy, Business Models, Tech Business Models, Jobs-To-Be Done, Design Thinking, Lean Startup Canvas, Value Chain, Value Proposition Canvas, Balanced Scorecard, Business Model Canvas, SWOT Analysis, Growth Hacking, Bundling, Unbundling, Bootstrapping, Venture Capital, Porter’s Five Forces, Porter’s Generic Strategies, Porter’s Five Forces, PESTEL Analysis, SWOT, Porter’s Diamond Model, Ansoff, Technology Adoption Curve, TOWS, SOAR, Balanced Scorecard, OKR, Agile Methodology, Value Proposition, VTDF Framework, BCG Matrix, GE McKinsey Matrix, Kotter’s 8-Step Change Model.
Main Guides:
Business ModelsBusiness StrategyMarketing StrategyBusiness Model InnovationPlatform Business ModelsNetwork Effects In A NutshellDigital Business ModelsThe post What is A Cog’s Ladder? The Cog’s ladder In A Nutshell appeared first on FourWeekMBA.
Ethereum: The History of Ethereum

Ethereum is the second-largest blockchain protocol and the first protocol to think about blockchain as a potential world’s computer. Indeed, over the years Ethereum has spurred various applications, from decentralized finance to NFTs, decentralized organizations, and more. Founded by Vitalik Buterin, it launched in 2014 with its ICO, the core development team behind Ethereum helped kick things off, and the crowd sale turned out to be one of the most successful ones in the blockchain ecosystem.
The history of Ethereum is part of the Blockchain Business Models, you find the detailed references in the book:
 The beginnings of Ethereum
The beginnings of Ethereum In a 2014 message from Vitalik Buterin that read “Welcome to the New Beginning,” Buterin explained “When the grand experiment that is bitcoin began, the anonymous wizard desired to test two parameters – a trustless, decentralized database enjoying security enforced by the austere relentlessness of cryptography and a robust transaction system capable of sending value across the world without intermediaries. Yet the past five years have painfully demonstrated a third missing feature: a sufficiently powerful Turing-complete scripting language.”
And Vitalik Buterin continued listing the innovations that Bitcoin had brought but then got to the point of what Ethereum would be for “Ethereum is a modular, stateful, Turing-complete contract scripting system* married to a blockchain and developed with a philosophy of simplicity, universal accessibility, and generalization.”
Vitalik Buterin also highlighted the main goal of such a Blockchain model “to provide a platform for decentralized applications – an android of the cryptocurrency world, where all efforts can share a common set of APIs, trustless interactions and no compromises.”
This message alone well explains the whole foundation of Blockchain. A general-purpose Blockchain, working more like a programming language able to accommodate an infinite number of use cases on top of it. Indeed, as Vitalik Buterin has highlighted in many of his interviews, initially he had thought of a Blockchain that could be used for a few dozens of use cases. But then he realized that the strength of a modular, general-purpose Blockchain would have been unlimited.
This apparently mad project turned into one of the most successful Blockchain protocols, that enabled various use cases (from decentralized applications and finance to decentralized autonomous organizations, non-fungible tokens, and more).
The core developers behind the initial launch of Ethereum were Vitalik Buterin (who would become the leading person for the whole project), Gavin Wood (who later went on to found other successful protocols like Polkadot and Kusama), and Jeffrey Wilcke.
Where did this name come from?In a forum discussion in 2014, Vitalik Buterin explained the reasoning of Ethereum’s name “I was browsing a list of elements from science fiction on Wikipedia when I came across the name. I immediately realized that I liked it better than all of the other alternatives that I had seen; I suppose it was the fact that sounded nice and it had the word “ether”, referring to the hypothetical invisible medium that permeates the universe and allows light to travel.”
The name choice wasn’t that casual, as it stood for the mission that Ethereum had as a Blockchain protocol. Become the “gas” or the primary element that fueled transactions of any time on top of its modular, general-purpose Blockchain.
*In simple terms that means a general-purpose computer language.
The $18 million-dollar launchAs Ethereum got into the world as a project, it started its journey as a decentralized organization, busy in building up the key components of the protocol that would lay out the foundation of the work to do in the coming years.
By January 2014, as Vitalik Buterin got ready to announce the “Ether Sale” which would officially mark the beginning of Ethereum as a cryptocurrency he reminded the cold day in San Francisco, back in November 2013, when he was drafting the White Paper, after months of reflection on what would determine the evolution of the blockchain.
This phase would be called among the insiders “cryptocurrency 2.0” or the phase in which finally crypto would move beyond the application that Bitcoin had brought around money. In short, it wouldn’t be just about money, as a use case, but rather about applications, decentralized applications, that could potentially be built on top of this new infrastructure.
The journey to get through this realization wasn’t a simple one and as Vitalik Buterin highlighted that was quite frustrating. As Buterin explained in his own words:
“Eventually, I realized that the key to solving the problem once and for all was a simple insight that the field of computer science first conceived in 1935: there is no need to construct a separate infrastructure for each individual feature and implementation; rather, it is possible to create a Turing-complete programming language, and allow everyone to use that language to implement any feature that can be mathematically defined. This is how our computers work, and this is how our web browsers work; and, with Ethereum, this is how our cryptocurrencies can work. ”
This would become his approach and strategy in developing the Ethereum protocol. Rather than thinking in simple use cases and potential applications, Vitalik Buterin started to think in terms of a programming language that could accommodate an unlimited number of use cases.
From there lead code developers Gavin Wood (who would later depart to found two major Blockchain protocols like Polkadot and Kusama) and Jeffrey Wilcke (who later went on to found games development studio, Grid Games) but also other lead developers like Charles Hoskinson (who would, later on, support the hard fork of Ethereum, Ethereum Classic, and in 2016 he also found another successful protocol, Cardano), Anthony Di Iorio and Mihai Alisie (who would serve as vice-president of the Ethereum Foundation until 2015).
In short, the founding team that would bring the core Ethereum protocol to life (and that later on would be the protagonist of the first “Ethereum War”) was formed.
Vitalik Buterin at the time described Ethereum as “a next-generation cryptographic ledger that intends to support numerous advanced features, including user-issued currencies, smart contracts, decentralized exchange and even what we think is the first proper implementation of decentralized autonomous organizations (DAOs) or companies (DACs)” (those would stick as some of the core use cases for Ethereum).
Buterin also explained that even though decentralization was the great promise of Ethereum what made it special was “the way that it does this – referring to the various applications. Instead of attempting to specifically support each individual type of functionality as a feature, Ethereum includes a built-in Turing-complete scripting language, which allows you to code the features yourself through a mechanism known as “contracts”.
Indeed, contracts (or smart contracts) would become the killer application for Ethereum. Those contracts represented ‘agents’ running specific pieces of code every time a transaction is sent to it and even more interestingly more advanced versions of these agents would be even able to modify their own code (thus becoming autonomous agents).
Over the course of the months as Ethereum moved from its White Paper to becoming a real-world project, more and more challenges came to be overcome. From the problems related to the proof of stake algorithm to mining and more.
Yet the founding team was focused and capable.
In a post to review the work done on the project just prior to the Ether sale, one of the leaders from the development team, Mihai Alisie, highlighted:
“The project started as an idea in Vitalik’s mind. Ethereum has now expanded into thousands and thousands of other minds around the world, thanks to this interconnected digital mesh called the Internet. A sea of minds brought together by the idea of a Turing complete general-purpose blockchain is creating, as you’re reading these lines, the Minecraft of blockchain tech.”
One of the key discussions that went on in these months, and that indeed represented the foundation of Ethereum from an organizational point of view, was whether to be a for-profit or not-for-profit organization. And the latter was the conclusion, as Mihai Alisie explained:
“After researching a number of models and organizations, we arrived at the conclusion that in order to keep the protocol and the software as pure as possible the only real option was to build a non-profit structure with a declared mission to develop, maintain, nurture and explore the potential of this new technology. Motivated not by money but radiant passion for this crazy idea of a free, open, and decentralized world. That’s what make us happy in the end and most importantly what makes us get up and work on this project, proudly saying today we’re building tomorrow.”
Finally, after months of intense work, the day of the sale came, and in a blog post on July 22, 2014, entitled “Launching the Ether Sale*” Vitalik Buterin announced the sale of what would become the major player in the Blockchain space, only behind Bitcoin (even though at the time very few people expected the success of such a project).
As Vitalik Buterin explained in the same post “First of all, I would like to thank the community, and especially those close to the project who have in many cases abandoned their jobs to dedicate their time to it, for their extreme patience regarding the launch of the ether sale.”
In the blog post Vitalik Buterin laid down the work that had been done in the previous months to get to the sale (that included the development of the first version of the Ethereum protocol). The sale would fix the initial price at “2000 ETH per BTC” until declining to a final rate of 1337 ETH per BTC and it concluded on September 2.
By the first two weeks from the sale over 50 million ETH had been sold pushing Ethereum among the top eight coins for a market cap for a value of the initial sale of $17.3M USD beating out also the initial sale of Dogecoin (at $15.5M).
Keeping it open: The first year and the discussion around governance and visionIn a post highlighting the work done in the first year of the Ethereum project, Mihai Alisie, one of the co-founders who would stay on board as vice-president of the Ethereum Foundation until 2015 explained:
“During the last couple of weeks, I started to think about how far we’ve come and how many things we have accomplished since this project started. From idea to implementation and everything in between, it was (and continues to be) the most intense ride of my life.”
Mihai remembered the early days of the Ethereum project when in the autumn of 2013, Vitalik Buterin had drafted the first version of the Ethereum White Paper, which he had addressed to a few selected ones, among these there was Mihai.
As Mihai Alisie recalled “Ethereum felt different from anything else he’d sent me before. The same rush I felt when I first understood the implications of Bitcoin was returning, this time with thousands of new multi-dimensional rabbit holes to explore.”
In fact, Mihai together with Vitalik back in 2011, when Bitcoin was just gaining traction, started Bitcoin Magazine, a project that was meant to narrate all the aspects of the Bitcoin ecosystem. By May 2012 the first issue came out.
From the magazine, Vitalik Buterin started to draft the vision for Ethereum. As the project got set up, along the way, in 2014, the Peter Thiel Foundation awarded $100K fo Vitalik Buterin for his Ehtereum’s project:
 Image Source: blog.ethereum.org/2015/03/14/ethereum...
Image Source: blog.ethereum.org/2015/03/14/ethereum...This $100K would set the stage for a project worth billions of dollars only a couple of years later and potentially a trillion of dollars in a decade or two.
The early years: $50 million Ether hack, the hard fork and the Web 3.0In a blog post on January 2016 entitled “The last Blog Post,” Gavin Wood explained how his departure was going to mark the beginning of a few new projects. And in another article on his personal blog, he asked “So Ethereum is released. How come the dream of an open, transparent, jurisdiction-neutral techno-legal system hasn’t arrived?!”
Finally in an article entitled “Why We Need Web 3.0” of September 2018 (over two years from his departure from Ethereum) Gavin Wood emphasized his vision for the future by also announcing Polkadot:
“From a user’s point of view, Web 3.0 will look barely different from Web 2.0, at least initially. We’ll see the same display technologies: HTML5, CSS, and so on. On the back-end, technologies like Polkadot — Parity’s inter-chain blockchain protocol — will connect different technological threads into a single economy and “movement.”
Polkadot and Kusama would all become blockchain protocols springing up from the “Ethereum’s war.”
But how did we get there?
The years from 2014 to 2016 marked the beginning of Ethereum beyond its White Paper. Not just a paper project, but a real-world one, that had shown its capabilities. Yet, the question here still remained on the whole project’s viability.
The development of the Ethereum Blockchain protocol had continued at full speed and the community grew exponentially.
Until one of the greatest heists on the Blockchain took place, and that happened right on the Ethereum Blockchain.
It all happened in the first part of June 2016, when the Ethereum community found a flaw in the DAO’s code. In an article entitled “More Ethereum Attacks: Race-To-Empty is the Real Deal” on June 9, 2016, Peter Vessenes opened by saying “Chriseth at github casually pointed out a terrible, terrible attack on wallet contracts that I had not considered. If there were a responsible disclosure avenue for ethereum contract developers, I would use it, but there doesn’t seem to be. Not only that, this code has been out and published on github for long enough that I wanted to get the news out there quickly.”
In short, a flaw in the smart contract’s code enabled potential hackers to exploit the fact that several withdrawals could be done, before the smart contract eventually records the final balance, thus enabling hackers to potentially steal millions of dollars from these smart contracts. This vulnerability not only was now visible for anyone, and up for grabs by hackers, but that posed a threat to the whole existence of Ethereum as a Blockchain.
Indeed, if one of the core values of Ethereum was security and an “unhackable cryptographed blockchain” how could this be possible in the first place?
The way the community would answer it would determine not only whether Ethereum survived but also if it could thrive going forward.
Initially, the bug in the code was undervalued by the community, but as of June 17th, it became clear this was something serious. In a blog post entitled “CRITICAL UPDATE Re: DAO Vulnerability” Vitalik Buterin explained “An attack has been found and exploited in the DAO, and the attacker is currently in the process of draining the ether contained in the DAO into a child DAO. The attack is a recursive calling vulnerability, where an attacker called the “split” function, and then calls the split function recursively inside of the split, thereby collecting ether many times over in a single transaction.”
Therefore, this “split function” was used to withdraw ether out of the smart contract many times over in a single transaction. Similar to a broken cash machine where the robber is able to take the same amount of cash many times while the machine records it only once, the hackers started to take advantage of this vulnerability, thus draining millions of dollars worth of Ethereum’s from the DAO’s smart contracts.
Indeed, imagine a cash machine that records only a transaction of $100 but while the drawer is closing the robber is able to take many times over banknotes of $100, while the cash machine only records one transaction of $100. This is the extent to which hackers were draining out money from smart contracts.
From an analysis done by Phil Daian the next day revealed some of these flaws and explained: “this exploit in the DAO is clearly not trivial; the exact programming pattern that made the DAO vulnerable was not only known but fixed by the DAO creators themselves in an earlier intended update to the framework’s code. Ironically, as they were writing their blog posts and claiming victory, the hacker was preparing and deploying an exploit that targeted the same function they had just fixed to drain the DAO of all its funds.”
As it turned out the core bug was part of the language program developed to deal with DAO and smart contracts. In fact, within the language program, Solidity (which was invented by Gavin Wood).
Gavin Wood, interviewed for the Dutch Blockchain Conference, on June 21, 2016, explained in his own words, what was going on and how to fix this next:
“What happened so there are a few things to explain about this. The first thing is that the problem isn’t with the Ethereum itself but the problem is with one of these applications, with one of these smart contracts so the smart contracts are not built into Ethereum. Ethereum exists sort of on a lower level and these software run on the higher level so it’s like saying well these websites are broken and it’s not saying the same thing as the Internet’s broken right. So Ethereum is like the Internet it just sort of works but yes one of the websites as it were that the work that sits on if they’re on the on ethereum and broke this website was called the DAO. Now the Dow was envisioned as some sort of mechanism so that people could pay in ether and this either could be used to sponsor projects and if the project’s ended up becoming profitable people would be able to make some of the new profits back and what happened was due to a technical flaw in this the DAO in this piece of software, this website that sits on top of Ethereum someone was able to attack it and to drain about a third of the money that the DAO had managed to collect into a child DAO. So into a kind of an offspring of the same the same sort of thing but an offspring. Now the reality is that the mayor is still sitting there so we know precisely where as we can see in the system there’s a balance it’s big it’s bigger than it should be but there’s a different owner but a different owner and at the moment the owner is unable to withdraw it. So due to safeguards in the DAO it’s at about thirty nine days before the owner can withdraw it and so we have this time in order to determine whether we’re going to do something about it or whether we’re just going to let it go.”
Further asked by the interviewer, if that was terrible as an attack for the whole system’s trustability, Gavin Wood replied:
“It’s an attack on the DAO. It’s an attack on the on the integrity of the DAO and it’s using the fact that the DAO is a smart contract that nobody can alter how it’s interpreted and if the interpretate if this software is wrong then the interpretation is wrong and people are understandably annoyed and the sound ugly concerned that you know yeah hold on where is this money being going now the question really is what can we do about it “
As the presenter asked “what to do” next, Gavin Wood, made clear to underline he had nothing to do with the DAO and as the interviewer asked Gavin Wood, whether Ethereum would survive that, Gavin Wood remarked an important point about the future of consensus and decision-making underlying Ethereum:
“The community manages this problem hopefully of how to form governments consensus even in the face of a widespread concern that what happened wasn’t the expectation.”
This passage is critical, as would emphasize something the many people getting to know Blockchain protocols for the first time undervalue. The Blockchain protocol is not just a trustless entity that executes orders automatically. But, it’s also (and this is one of the main points of that) a distributed consensus platform, where important decisions can be taken as a group, rather than single individuals. This is a critical difference also between traditional governance (which is also how major tech players’ companies are run) and the new way of managing blockchain-based companies.
Yet the Reddit user by the screen name of ydtm explained back at the time “Yes, I realize the OP is a bit harsh. I do think Vitalik is a smart guy. But I also think that tens of millions of dollars almost evaporated here, and I would like to provide a perspective based on language design – which might be somewhat different from what we’ve already heard from Emin Gün Sirer in his post mortem which also appeared recently.”
Things got very bad when the flaw was found to be draining dozens of millions and it could get even worse. In the meantime, the developer’s community was frantically trying to find various solutions to the problem. Yet, whichever solution was potentially threatening for the network.
At this point, it’s critical to understand that Blockchain-based business models living on these protocols are made of rules expressed in the form of code that can’t be changed so easily. A change in the code could mean either a soft or hard fork.
And none of these options was a simple one. Forking the blockchain is something that needs to be done carefully and only to reach critical decisions, and this indeed was a survival threat. However, that also opened up the discussion of how blockchain protocols were really immutable. They are not. Indeed, forking enables the underlying rules of a blockchain to be changed. Even though extremely difficult and still based on the consensus of the majority that could be done.
Among the Ethereum community, the leader, Vitalik Buterin also was extremely preoccupied. In a chat between Vitalik Buterin and Exchanges, recorded on Steemit we can feel Vitalik’s concerns:
[3:09:03 AM] George Hallam [ETH] : Ping
[3:09:19 AM] Bill Shihara: Pong
[3:09:57 AM] Bill Shihara: Is the reported issue with the DAO real?
[3:10:17 AM] Vitalik Buterin: as far as we can tell yes
[3:10:33 AM] Mike Li: Where can I find the report?
[3:10:54 AM] Vitalik Buterin: https://www.reddit.com/r/ethereum/comments/4oi2ta/i_think_thedao_is_getting_drained_right_now/
[3:10:55 AM] Vitalik Buterin: active thread
[3:11:06 AM] Alex Hanin: https://thedao.slack.com/messages/general/
[3:11:07 AM] Mike Li: Thank you VB
[3:11:19 AM] Vitalik Buterin: possible mitigation strategies are:
[3:11:21 AM] Bill Shihara: Thanks. There is a lot of panic so a clear statement from the DAO and ETH team’s would be extremely helpful. At this point, people are speculating that griff’s account was hacked.
[3:11:29 AM] Vitalik Buterin: 1. seizing any stolen either that goes through exchanges
[3:11:38 AM] Vitalik Buterin: 2. there is one person who will split within 2 hours
A few minutes later in the conversation, Vitalik Buterin said:
[3:43:01 AM] Vitalik Buterin: ok can you guys stop trading
Asking exchanges to stop trading was a huge deal, as it also meant other legitimate people couldn’t freely trade Ethereum. Thus, this signals perfectly the concern Vitalik Buterin had at the time.
To make things even worse, on June 18th 2016, on “An Open Letter” a guest claimed to be the attacker (this might have only been an attempt to distract the Ethereum’s community), and explained:
“I have carefully examined the code of The DAO and decided to participate after finding the feature where splitting is rewarded with additional ether. I have made use of this feature and have rightfully claimed 3,641,694 ether, and would like to thank the DAO for this reward. It is my understanding that the DAO code contains this feature to promote decentralization and encourage the creation of “child DAOs”.
And at the end of it he went on:
“A soft or hard fork would amount to seizure of my legitimate and rightful ether, claimed legally through the terms of a smart contract. Such fork would permanently and irrevocably ruin all confidence in not only Ethereum but also the in the field of smart contracts and blockchain technology. Many large Ethereum holders will dump their ether, and developers, researchers, and companies will leave Ethereum. Make no mistake: any fork, soft or hard, will further damage Ethereum and destroy its reputation and appeal.
I reserve all rights to take any and all legal action against any accomplices of illegitimate theft, freezing, or seizure of my legitimate ether, and am actively working with my law firm. Those accomplices will be receiving Cease and Desist notices in the mail shortly.
I hope this event becomes an valuable learning experience for the Ethereum community and wish you all the best of luck.
Yours truly,
The Attacker”
Hard-forking the protocol to win the warIt had become clear by that point that this was a war, a “DAO War.” On June 24, 2016, on a blog post entitled “DAO Wars: Your voice on the soft-fork dilemma” Péter Szilágyi, from Ethereum’s core development team (that had been frantically trying to solve this major flaw in the last weeks), explained:
“The last week was quite hectic for all of us in the Ethereum ecosystem. The DAO has shown us that it takes much more effort to write smart contracts than we originally anticipated; but also that it takes a surprising amount of debate to reach a consensus on issues of this scale.”
One thing that strikes quickly from this event, is now going through this survival threat, there was no single person in charge. Sure, the community still relied a lot on Vitalik Buterin’s ability to respond to this. Yet the decision on how to end this over was in the hands of the developer’s community and even there, the developer’s community alone wasn’t the only stakeholder. In order to align the whole ecosystem, any decision needed to be debated over and made publicly available, to enable people using, exchanging, or building applications on top of Ethereum to understand what was happening there.
This event is at the heart of what it means to do business on a Blockchain.
As Vitalik Buterin went on aligning the community around the two courses of actions possible (soft-fork which would have been less invasive of the protocol, and hard-fork) as he emphasized in the same “as there is no clear, best course of action that will satisfy all community members equally, we’ve decided to give the power to the people running Ethereum to decide whether they support this decision or not.”
Vitalik Buterin also explained the consequences going forward, “miners who do not update by definition vote against the soft-fork as they will continue the current logic of keeping the gas limit above the vote threshold. If the soft-fork is accepted by the majority, non-updating miners will still accept blocked transactions. In that case, non-updating miners will either fork off their own Ethereum network, diverging from the majority, or will forfeit any blocks they mined (since it’s not accepted by the majority, overruling the minority blocks)”
And as an epilogue “This release implements a soft-fork. A soft-fork is perfectly compatible with all protocol rules and requires only the consensus of the majority of miners to enact. It is temporary and can be removed/amended at any point in time upon miner consensus. It does not break protocol rules; it does not roll back any executed transactions/blocks; and it does change not any blockchain state outside of the original protocol capabilities.”
As time went by, the dilemma on how to permanently fix the issue was highlighted in the blog post “To fork or not to fork” on July 15, 2016, Ethereum’s core developer Jeffrey Wilcke explained “The DAO, though not a product developed by the Ethereum Foundation, has been a hot topic as of late, both internally in the organisation as well as within our community. The Hard Fork is a delicate topic and the way we see it, no decision is the right one. As this is not a decision that can be made by the foundation or any other single entity, we again turn towards the community to assess its wishes in order to provide the most appropriate protocol change.”
By July 20, 2016, the hard fork had been completed. This time Vitalik Buterin took the lead in explaining the process. As Ethereum’s blockchain moved toward block 1920000 (the one that would execute the hard fork) we can only imagine Buterin’s state of mind. As the process completed Buterin acclaimed “we would like to congratulate the Ethereum community on a successfully completed hard fork. Block 1920000 contained the execution of an irregular state change which transferred ~12 million ETH from the “Dark DAO” and “Whitehat DAO” contracts into the WithdrawDAO recovery contract. The fork itself took place smoothly, with roughly 85% of miners mining on the fork.”
This is what the hard fork looked like in practice. This simple move in codes determined hundreds of millions to move to the new fork in a few seconds.
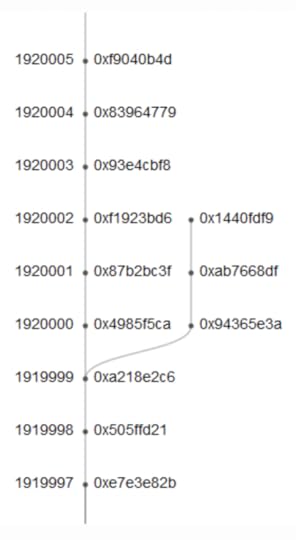 Image Credit: blog.ethereum.org/2016/07/20/hard-for...
Image Credit: blog.ethereum.org/2016/07/20/hard-for...Vitalik Buterin closed the post by highlighting “we thank our developers and the community for working together to make the transition as smooth as it has been, and look forward to working together to continue to make the Ethereum ecosystem and protocol a success.”
In a final post “Onward from the Hard Fork” Vitalik Buterin explained “The foundation has committed to support the community consensus on the admittedly difficult hard fork decision. Seeing the results of various metrics, including carbonvote, dapp and ecosystem infrastructure adoption, this means that we will focus our resources and attention on the chain which is now called ETH (ie. the fork chain). That said, we recognize that the Ethereum code can be used to instantiate other blockchains with the same consensus rules, including testnets, consortium and private chains, clones and spinoffs, and have never been opposed to such instantiations.”
Therefore, going forward two Ethereum protocols would come out from this hard fork. The new ETH, which would be rebranded as the “official” Ethereum protocol, contained the altered history (by removing the hacked tokens) and the old Ethereum protocol, named now ETC, or Ethereum Classic that contained the unaltered history (together with the theft of millions of dollars).
Thus, the hard-forked Ethereum protocol would continue its existence afresh, with a very hard-learned lesson, dozens of million dollars missing, and yet a community that had responded with maximum support.
And all of this paradoxically highlighted one of blockchain’s most important promises, the unknowability of the holder.
Everyone knows the address:
0xF35e2cC8E6523d683eD44870f5B7cC785051a77D
Misplaced millions of ethers, and yet none knows who that is (having passed on the Ethereum Classic blockchain we don’t know for sure whether these tokens were eventually sold and to whom). Just like Satoshi Nakamoto remained a mystery after years from the Bitcoin’s White Paper (together with a pool of 1.1 million Bitcoins worth billions). So Ethereum’s stolen token was never traced back.
Solving for Scale: Making Ethereum from 100x to 1000x more efficientWhen Ethereum was first created as a project, the first question that popped to mind to investors was whether it would become a viable project. However, as it showed it was viable (and it survived the “DAO War”), the next question was about scalability. Indeed, as more and more applications (dApps) got built on top of the Ethereum blockchain, its fees to execute transactions got higher and higher.
In part, these “gas fees” have helped as a disincentive to the system to execute transactions or applications that might be less relevant to the whole ecosystem. Yet, in the long run, the Ethereum ecosystem depends upon its ability to accommodate as many use cases as possible.
This poses a major challenge, which is scalability. How does Ethereum tackle that? In two main ways.
Layer 1 Scaling: Getting 100x BetterIn layer 1 scaling the underneath Ethereum-based Blockchain, the protocol is made more efficient, thus enabling 10 to 100x growth of the ecosystem.
Core examples of Layer 1 scaling comprise proof of stake and sharding. Indeed, as Ethereum rolls out what’s now called Eth2 (the upgrades that will make the whole protocol more scalable), eventually, as and if the roll-out comes out successfully, Eth2 will merge into Ethereum, thus becoming a more effective whole.
It’s important to highlight that Ethereum started primarily as a proof of work-based protocol (like Bitcoin). While this delivered the project’s viability; as Ethereum grew to support new use cases like decentralized finance and decentralized applications a new consensus algorithm needed to be introduced. That is why Ethereum started to move toward proof of stake and sharding (these changes will be coordinated by the Beacon Chain).
As Vitalik Buterin highlighted in “Why sharding is great: demystifying the technical properties” “sharding is the future of Ethereum scalability, and it will be key to helping the ecosystem support many thousands of transactions per second and allowing large portions of the world to regularly use the platform at an affordable cost. However, it is also one of the more misunderstood concepts in the Ethereum ecosystem and in blockchain ecosystems more broadly. It refers to a very specific set of ideas with very specific properties, but it often gets conflated with techniques that have very different and often much weaker security properties. The purpose of this post will be to explain exactly what specific properties sharding provides, how it differs from other technologies that are not sharding, and what sacrifices a sharded system has to make to achieve these properties.”
He also explained that when it comes to Blockchain protocols the Scalability Trilemma (or the ability to keep the public blockchain scalable, decentralized, and secure) can be achieved via more complex mechanisms like sharding*.
As Vitalik Buterin highlighted “a sharded blockchain is:
Scalable : it can process far more transactions than a single node Decentralized : it can survive entirely on consumer laptops, with no dependency on “supernodes” whatsoever Secure : an attacker can’t target a small part of the system with a small amount of resources; they can only try to dominate and attack the whole thing”Blockchain companies use sharding to partition databases and increase scalability, allowing them to process more transactions per second. Sharding is a key mechanism underneath the Ethereum Blockchain and one of its critical components. Indeed, sharding enables Blockchain protocols to overcome the Scalability Trilemma (as a Blockchain grows, it stays scalable, secure, and decentralized).
 The Scalability Trilemma (Image Credit: vitalik.ca).
Layer 2 Scaling: Getting 1000x Better
The Scalability Trilemma (Image Credit: vitalik.ca).
Layer 2 Scaling: Getting 1000x Better
When it comes to layer 2 scaling, this has the potential to make the whole ecosystem much more effective. This consists of enabling smarter protocols on top of the main Ethereum protocol. Thus expanding exponentially the capabilities and use cases available on the main protocol. A very basic example of layer 2 scaling are payment channels which “allow for practically unlimited, bidirectional transfers between two participants, as long as the net sum of their transfers does not exceed the deposited tokens.”
As Vitalik Buterin explained “This technique – referring to payment channels – is powerful: it can be adjusted to handle bidirectional payments, smart contract relationships (eg. Alice and Bob making a financial contract inside the channel), and composition (if Alice and Bob have an open channel and so do Bob and Charlie, Alice can trustlessly interact with Charlie). But there are limits to what channels can do. Channels cannot be used to send funds off-chain to people who are not yet participants. Channels cannot be used to represent objects that do not have a clear logical owner (eg. Uniswap). And channels, especially if used to do things more complex than simple recurring payments, require a large amount of capital to be locked up.”
However, the main problem with these schemes is the fact that transactions are pushed off-chain (where the value is moved outside the blockchain), which can pose security risks, thus comprising the whole purpose of the blockchain.
However, for Vitalik Buterin, one of the most exciting examples of layer 2 scaling are the so-called “roll-ups.” As an example, let’s consider the case of optimistic rollups, which “use a side chain that sits in parallel to the main Ethereum chain. They can offer improvements in scalability because they don’t do any computation by default. Instead, after a transaction they propose the new state to mainnet. Or “notarise” the transaction.”
This is critical because roll-ups will reduce the congestion on top of the main blockchain, as they take place on a “sidechain” thus potentially reaching a transaction speed of 2,000-3000 per second.
Therefore, all these transactions would be processed through the rollups on the sidechain and the reports on top of layer 1, or the main Ethereum’s blockchain, de facto increasing speed, and reducing gas fees.
And the key advantage is that these transactions would still be on-chain. This passage is critical to understand as Vitalik Buterin himself highlights:
“The fact that data is on-chain is key. Putting data on-chain and having consensus on that fact allows anyone to locally process all the operations in the rollup if they wish to, allowing them to detect fraud, initiate withdrawals, or personally start producing transaction batches. The lack of data availability issues means that a malicious or offline operator can do even less harm (eg. they cannot cause a 1 week delay), opening up a much larger design space for who has the right to publish batches and making rollups vastly easier to reason about. And most importantly, the lack of data availability issues means that there is no longer any need to map assets to owners, leading to the key reason why the Ethereum community is so much more excited about rollups than previous forms of layer 2 scaling: rollups are fully general-purpose, and one can even run an EVM inside a rollup, allowing existing Ethereum applications to migrate to rollups with almost no need to write any new code. ”
Toward Ethereum 2.0, Staking, Sharding, Proof of Stake* and ScalingAs a quick recap so far, Ethereum was born in 2014 out of Vitalik Buterin’s White Paper, and the core development team has been extremely successful since the start. By 2016 a critical flaw in the DAO smart contract made it possible for hackers to steal millions of dollars worth of Ethereum, thus posing a serious threat to its survival. The solution to it was a hard-fork, to which most of the Ethereum community joined in and that determined the split of the protocol. From there two protocols were formed, Ethereum Classic (ETC) Containing the unaltered history of the protocol (comprising the stolen tokens) and ETH, which would be rebranded as Ethereum, which contained the altered history (the protocol from which the stolen tokens had been removed).
As Ethereum showed its viability, it started to scale quickly and by 2017 it also showed its potential. However, a problem of scalability arose, especially in light of massive “gas fees” (the fees to process transactions on top of Ethereum’s Blockchain). To solve this problem, Ethereum started to move toward Eth2 – scheduled between 2022-2024 – which once successfully rolled out would be rebranded as Ethereum. This upgraded protocol will primarily address scaling through two layers. With Layer 1 Scaling, the main protocol might get potentially 100x more efficient.
This will consist of integrating new mechanisms such as proof of stake, and sharding. In the process, Ethereum holders can also stake their coins (those would be locked into the blockchain until the transition to Eth2 has been completed) and earn interest as a result of that. Layer 2 Scaling instead will consist of integrating mechanisms such as roll-ups that might make the whole blockchain 1000x more efficient, by enabling transactions to be processed at scale on sidechains, that can be reconducted back to the main protocol (thus still be on-chain and therefore secure).
Main Free Guides:
Business ModelsBusiness CompetitionBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkThe post Ethereum: The History of Ethereum appeared first on FourWeekMBA.
Pre-Seed Funding In A Nutshell


For a start-up, pre-seed funding an initial round of development funding designed to help the business grow. Pre-seed funding tends to be in amounts between $10,000 and $250,000, and usually, these funds come primarily from family, friends, or the own funders, as this can help them develop a first MVP and access to the seed funding.
Understanding pre-seed fundingPre-seed funding is a relatively recent concept. Traditionally, new companies would look for Series A funding right away and then worry about developing a viable product.
Seed investors have since come to fill a critical role in this process. Instead of looking for companies focused on getting to market as quickly as possible, they look for start-ups who have the following characteristics:
They have an extremely basic product showing some functionality or are working on a minimum viable product (MVP).They have identified a clear market opportunity.They are in the process of making new hires or expect to advertise imminently.They have increasing operational expenses.Pre-seed funding tends to be in amounts between $10,000 and $250,000. It typically comes from friends, family members, ardent supporters, or the start-up founders themselves.
Some basic features and requirements of pre-seed fundingThe idea of pre-seed funding is to enable the launch of the business and get it to the next level of funding. The start-up founder is typically responsible for making the capital last as long as possible. They must also make the business attractive enough for subsequent investment.
Here are some other general features and requirements:
Pre-seed funding should last up to 12 months to set a good rhythm. Delays beyond a year portray an unprepared or underdeveloped business.Funds are typically extended to a start-up based on the credibility of the founder, and not so much on the viability of an idea.Investors must not expect quick returns and be cognizant of the risk at this early stage of development.The founder(s) must be accountable to investors. Personal relationships must not cloud accountability.As a matter of priority, funds must be directed to clarifying a value proposition, milestones, and a financial road map.How pre-seed funding is raisedFor a start-up requiring pre-seed capital, there are several options:
Pre-seeding platforms – these are host companies or entrepreneurs willing to invest in fresh ideas. Sping is a popular Dutch service for those developing web applications and other online platforms.Crowdfunding – this allows friends, family, and passionate supporters the chance to financially support a growing business by using the crowdfunding model. Kickstarter and Indiegogo are two of the more popular options.Early-stage accelerator programs – these are ideal for start-ups who require assistance in developing a product and honing their business model. Ultimately, these programs connect businesses with investors and provide critical support in the form of mentoring and education. Startup Boost is one such company with a focus on moving pre-seed stage start-ups towards accelerators, investment, and/or revenue.Key takeaways:Pre-seed funding is an initial round of funding designed to help a start-up commence operations. It is typically funded by friends, family, and the founder of the start-up itself.Pre-seed funding tends to be in amounts under $250,000. Start-ups who have identified a clear market opportunity can use the funding to build a simple but functional product or recruit extra staff.Pre-seed funding can be raised in several ways, including specialized pre-seeding platforms, crowdfunding platforms, and early-stage accelerator programs.Main Free Guides:
Business ModelsBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkConnected ConceptsVenture Capital A venture capitalist generally invests in companies and startups which are still in a stage where their business model needs to be proved viable, or they need resources to scale up. Thus, those companies present high risks, but the potential for exponential growth. Therefore, venture capitalists look for startups that can bring a high ROI and high valuation multiples.Economic Moat
A venture capitalist generally invests in companies and startups which are still in a stage where their business model needs to be proved viable, or they need resources to scale up. Thus, those companies present high risks, but the potential for exponential growth. Therefore, venture capitalists look for startups that can bring a high ROI and high valuation multiples.Economic Moat Economic or market moats represent the long-term business defensibility. Or how long a business can retain its competitive advantage in the marketplace over the years. Warren Buffet who popularized the term “moat” referred to it as a share of mind, opposite to market share, as such it is the characteristic that all valuable brands have.Meme Investing
Economic or market moats represent the long-term business defensibility. Or how long a business can retain its competitive advantage in the marketplace over the years. Warren Buffet who popularized the term “moat” referred to it as a share of mind, opposite to market share, as such it is the characteristic that all valuable brands have.Meme Investing Meme stocks are securities that go viral online and attract the attention of the younger generation of retail investors. Meme investing, therefore, is a bottom-up, community-driven approach to investing that positions itself as the antonym to Wall Street investing. Also, meme investing often looks at attractive opportunities with lower liquidity that might be easier to overtake, thus enabling wide speculation, as “meme investors” often look for disproportionate short-term returns.Payment for Order Flow
Meme stocks are securities that go viral online and attract the attention of the younger generation of retail investors. Meme investing, therefore, is a bottom-up, community-driven approach to investing that positions itself as the antonym to Wall Street investing. Also, meme investing often looks at attractive opportunities with lower liquidity that might be easier to overtake, thus enabling wide speculation, as “meme investors” often look for disproportionate short-term returns.Payment for Order Flow Payment for order flow consists of a “kickback” or commission that the broker routing customers to a market maker (in charge of enabling the bid and ask price) will pay a commission to the broker as a sort of market-making fee.What is a SPAC
Payment for order flow consists of a “kickback” or commission that the broker routing customers to a market maker (in charge of enabling the bid and ask price) will pay a commission to the broker as a sort of market-making fee.What is a SPAC A special purpose acquisition company (SPAC) is a company with no commercial operations that are created to raise capital through an IPO to acquire another company. The SPAC is also called for that reason a “blank check company” as it will use the money provided by investors to enable private companies to go public via the SPAC.
A special purpose acquisition company (SPAC) is a company with no commercial operations that are created to raise capital through an IPO to acquire another company. The SPAC is also called for that reason a “blank check company” as it will use the money provided by investors to enable private companies to go public via the SPAC.The post Pre-Seed Funding In A Nutshell appeared first on FourWeekMBA.
January 26, 2022
What Is Market Validation? Market Validation In A Nutshell

In simple terms, market validation is the process of showing a concept to a prospective buyer and collecting feedback to determine whether it is worth persisting with. To that end, market validation requires the business to conduct multiple customer interviews before it has made a significant investment of time or money. A transitional business model is an example of market validation that helps the company secure the needed capital while having a market reality check. It helps shape the long-term vision and a scalable business model.
Understanding market validationMarket validation, therefore, is used to determine whether there is a need for a product or service in a business’s target market.
Market validation can be used in several different contexts. Some entrepreneurs use it when they are founding a new startup based around an innovative product idea. More established businesses may also use market validation when considering whether to launch a new product or add new features to an existing product.
Market validation is important for two main reasons:
Failure avoidance – the sunk costs associated with a product that fails when presented to the market are significant. Market validation is a way to validate an idea for viability before committing substantial resources.Funding procurement – when an idea is deemed to be viable, this validation is used to convince key stakeholders to commit to funding the rest of the project. This is particularly crucial for early-stage startups where time is of the essence and funding tends to be more difficult to obtain.How to perform market validationThere is no set market validation framework, with many of the framework components dependent on the nature of the industry, project, and the way project managers like to work.
Nevertheless, we have provided a basic outline of the process below.
Start with an assumptionTo validate an assumption about the market, the business must first define a list of assumptions that it wants to test. These may be related to market demand, the ability of a product to solve consumer problems, or whether the product price will be suitable.
Define the testThe most prevalent market validation methods are those we mentioned earlier: customer interviews and surveys. However, some businesses will build an MVP while others will conduct prototype, usability, or SEO-based tests.
It is important to construct the tests with questions that provide clarification on the assumptions made in step one. Consider, for example, the following survey questions:
Does this feature help solve your problem? How would you explain what this product does? How often do you estimate you’d use the new feature? What tools or products, if any, were you using to solve the problem previously?Recruit participantsWhile an obvious point to make, the business must recruit participants that represent the actual end-user or buyer. People tend to be averse to studies as a general rule, so it may be wise to provide various incentives to ensure the data set collected is sufficiently large.
For instance, the business may opt to cover travel costs of each participant or provide them with a voucher to use in-store.
Conduct the experiment and reviewOnce everything is in place, run the experiment and evaluate the results. Remember that proving an assumption wrong is not the same as failing; it is simply a matter of repeating the process until the assumptions are correct.
If nothing else, this keeps the product team humble and serves as a reminder to never assume they know exactly what the consumer wants before asking them.
Transitional Business Models A transitional business model is used by companies to enter a market (usually a niche) to gain initial traction and prove the idea is sound. The transitional business model helps the company secure the needed capital while having a reality check. It helps shape the long-term vision and a scalable business model.Key takeaways:Market validation is used to determine whether there is a need for a product or service in a business’s target market.Market validation is important for two main reasons: failure avoidance and funding procurement. Each reason is related to the other and enables product development teams to move forward with viable ideas that do not prove to be fruitless.Market validation can be performed in four basic steps: start with the assumption, define the test, recruit participants, and conduct the experiment and review.
A transitional business model is used by companies to enter a market (usually a niche) to gain initial traction and prove the idea is sound. The transitional business model helps the company secure the needed capital while having a reality check. It helps shape the long-term vision and a scalable business model.Key takeaways:Market validation is used to determine whether there is a need for a product or service in a business’s target market.Market validation is important for two main reasons: failure avoidance and funding procurement. Each reason is related to the other and enables product development teams to move forward with viable ideas that do not prove to be fruitless.Market validation can be performed in four basic steps: start with the assumption, define the test, recruit participants, and conduct the experiment and review.Main Free Guides:
Business ModelsBusiness CompetitionBusiness StrategyBusiness DevelopmentDigital Business ModelsDistribution ChannelsMarketing StrategyPlatform Business ModelsRevenue ModelsTech Business ModelsBlockchain Business Models FrameworkThe post What Is Market Validation? Market Validation In A Nutshell appeared first on FourWeekMBA.



