Daniel Miessler's Blog, page 69
May 17, 2020
Responding to Questions About Hard Determinism

I just received this email from a reader about free will, and I actually get a lot of these because of my numerous articles on the topic.
I thought his email was so well put together that I should answer publicly. So here are his questions, along with my answers inline.
If everything has been predetermined, how come we can make rational, informed, choices?
The same way a computer can. Computers can be smart and rational when it comes to solving problems, and nobody would argue that they have free will.
Would it also not be silly to think about things because of no matter what it was predetermined for you to do it?
I’m releasing a full video essay on this topic soon.
The answer to this is that we’re human and we can’t live without behaving as if we have free will, and as if our “choices” matter. That is how we must function in a moment-to-moment, day-by-day basis because that’s how we’re built. But it doesn’t mean we have to accept that perception as truth. There are many situations where our senses lie to us in ways that we can prove objectively.
For example, when you touch your nose, the sensation of your nose and finger arrive at different times in the brain, but the brain groups them together to make it feel simultaneous. Even with this knowledge, we live in the reality of our senses, not in raw truth.
The longer answer is something I call General Absurdism, which is the universal distance between human experience and underlying reality. This gap applies to so many things. In Absurdism (proper), it applies to the search for inherent meaning in this chaotic universe. And it also applies to our perception of agency and free will.
We experience one thing (making choices) while another thing is true (we cannot affect outcomes if our actions are the result of previous inputs). Those things are in conflict, but that’s ok. Ice cream is a bunch of atoms bumping into each other, but that doesn’t make it any less glorious.
Do you think that even if we can’t control the present or the future we can at the very least chose how we deal with it or our mindset of the situation? Or is that all determined to?
Determined here really just means out of our control. If there is true randomness that goes against determinism, but doesn’t give us any control.
Yes, it’s all determined. Even how we choose to deal with things that we contemplate.
Again, computers can do that. They can see a chess move is made, contemplate the future, and make a choice that seems best for their goals. That’s not free will.
Do you believe we exist or are we just illusions? If we can’t chose what we do, how can we as a concept exist?
Well, we all have a collective perception that we exist. And everyone seems to mostly have the same perception. And there is a strong argument that the only possible thing we can be sure of, is that we are conscious. Because feeling conscious is itself the proof.
As far as whether we really exist, well, that depends on what you think qualifies? If we’re running in a simulation but we’re still here doing these things, and still conscious, do you think that’s reality? I do. Is it as much reality as another kind? I don’t know.
At what point do we consider something real?
When a whole bunch of individuals in the collective develop the scientific method, and we can independently verify truths about the environment. Again, that doesn’t tell us how real it is. Maybe we’re in a virtual reality engine somewhere. Maybe we’re in one of a trillion universes. Whatever.
The question is what you consider to be the cutoff for real. I personally think whatever this is definitely qualifies.
Is there a possibility that we could be wrong? I have been accused of using circular logic when trying to convince people they don’t make choices and are mindless cause and effect machines even though all the science says otherwise. Is it just a copout? Because no matter what they do we are right because it was determined to do so?
Yes, it’s possible that we’re wrong.
If we live in a world with true, Libertarian Free Will, like the kind given by a god, then we would be wrong.
As an atheist I don’t see any evidence for this, but it could absolutely be true. It’s just very, very unlikely.
If free will is a lie is self-control not real? Does that mean it does not matter how hard a person tries to change they never will of their own?
I wrote a whole piece about this, called Free Will’s Absurdist Paradox.
This is where the paradox comes in.
Yes, self-control is ultimately an illusion. But as a human, living this human life, it’s quite real. It’s real from our perspective as these weird, complex animals that we are.
Answer me this. Do people love their romantic partners? Do they love their children? Does ice cream taste good? Yes. Of course they do. Those things are true because they’re about perception. They’re interpretations of reality from a human point of view.
If you are an unfeeling, super-evolved AI life form from the other side of the multiverse, and I show you the atoms of an ice cream cone, does those atoms taste good? The question doesn’t even make sense, because both “taste” and “good” require a perspective.
When you wake up every morning you have to try to be a better person. You have to try to help your friends and loved ones live better lives. That’s human truth. That’s human reality.
At the same time, it’s not really possible to do anything other than what you’re going to do. So maybe you did improve yourself. Or maybe you stayed in bed. You don’t know and nobody else does either.
As humans, all you can do is lean into the illusion and be the best possible version of yourself. Absurdism is about embracing that paradox and living on despite it.
Sam Harris thinks that morality is objective and be scientifically deduced. I want to agree. But how does that work if we have no free will? How can people make good choices or make the world better if they have no choice at all?
He sees the world the way I’ve described above. He knows it’s all an illusion.
When he talks about trying to make good or bad choices, and trying to maximize well-being, he’s talking about doing so from within the illusion. As he’s talked about in his books, the alternative is laying in bed paralyzed, without ambition and without purpose.
We are humans, and we have to operate most of our lives within the human framework. That means behaving “as if” we were free agents.
Our intellects allow us to simultaneously see the paradox.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
May 16, 2020
It’s Time to Get Back Into RSS

A lot of people who were on the internet in the early 2000’s remember something called RSS. It stands for Really Simple Syndication, and it allowed content creators to publish updates to the world in a well-understood format.
The idea—which seems strange to type out—is that millions of people in the world could create and publish ideas, thoughts, and content…and then people who enjoyed that content would collect sources into a reader, which was called, well, an RSS Reader.
I often wonder if Google could revive democracy by bringing back Reader.
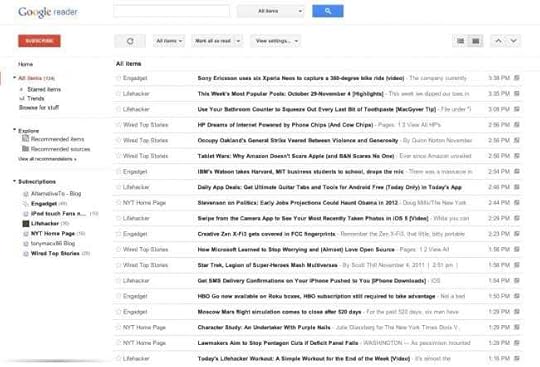
Google Reader, the most missed product in Google’s extensive graveyard
Google Reader was the reader of choice, and it was glorious. People took pride in their curated set of sources, and we wrote a lot about how to best organize your feeds for maximum efficiency.
It was a direct connection between creators and consumers. By adding someone’s feed to your RSS reader you were saying, “Yes, I’d like to subscribe to your interpretation of reality.”
By curating the feeds in your reader, you were curating your view of the world. And that was made up of hundreds or thousands of individual voices.
We’re not sure who struck first—us or them—but we know it was us that scorched the sky.
Morpheus
It’s unclear what exactly destroyed RSS, but Google closing Google Reader definitely didn’t help. Another factor was the rise of aggregation sites like Slashdot, Digg, and Reddit, which seductively took on the burden of surfacing the best content.
So rather than having to curate your own feeds, you just land on a single site and have the “best” content presented to you.

A picture of me getting a story off of Digg in 2005
Reddit is awesome, for sure. And so were the other aggregators. But I think they stole something from us. First, they broke the direct connection between the reader and the creator, making it so that Digg showed you a story, not Kristen—who you’ve been following for years. And second, it removed the need to tend to one’s own input garden.
The less effort it takes to acquire something, the less value it will have to you.
I’m sure social media sites had an effect too, because—like aggregators—they were singular watering holes that guaranteed something exciting when you showed up. The common denominator is the move from more effort to less. It’s like in WALL-E, where we turn into morbidly obese people on hoverchairs being shuttled between stimuli.
Well, it’s time to garden again. It’s time to return to RSS.
Google Reader is still dead, but if I remove my nostalgia glasses, Feedly is probably better now than Reader ever was. It’s what I’ve been using for years now.

Be sure to follow lots of stuff you agree with, and stuff you don’t
I mean cooking as a passion, not as a cheaper alternative to eating out.
I see RSS curation like the practice of cooking one’s own meals. There’s something magical about picking specific ingredients, using custom tools to prepare them, and then consuming the output.
Or—perhaps an even better metaphor—cultivating a bookshelf. With the only difference being that bookshelves are usually constructed using only one’s favorite books, while I think an RSS reader should be designed for “exposure to other” as well.
Just as with any hobby, the effort adds meaning to the output.
The point is that curation of an RSS reader forces one to think about their inputs, and to exercise their values in doing so. Are you building a list of inputs that agree with you? Are you including people who you respect but disagree with? What about people you can’t stand at all?
What you choose to include will not just define how you see the world, but how well you understand other peoples’ perspectives as well.
So I challenge you.
Go sign up for Feedly
Add your favorite news sites
Add your favorite aggregators’ feeds (best of both worlds!)
Add your favorite thinkers and creators’ individual sites
Add every one of your friends’ sites
Add the top news sites of your political opponents
Add the sites from your various hobbies (cooking, cars, electronics, etc.)
Then, as the most important step, stop visiting the New York Times, CNN, Reddit, Hacker News, Lobsters, and every other site you rotate through all day.
Feedly also uses AI to highlight critical sections of the article.
Instead, just open your reader and get the content from there.
A story within Feedly
Not only will this reduce your anxiety and churn from constantly opening and closing various sites, but RSS also shows the content in a standard format, with less to distract you.
If you add .rss to the end of any Reddit URL you get its RSS feed.
Remember, you don’t have to give anything up. You can still have Hacker News, Lobsters, and yes—even Reddit—all in one place.
Summary
Ok, to sum up.
We lost something when we stopped following individual content sources
While Reader is gone, Feedly (and others) have done a good job replacing it
You don’t have to give up the power of the aggregators; just add them as sources
RSS is clutter-free consumption, with fewer ads, no popups, etc
Curating your input garden is a meaningful part of the consumption experience
It’s relaxing to know you only have to check one place rather than N places
Long live RSS.
Notes
Ideally, the return to RSS would be accompanied by the return to blogging. More
Here’s a write-up on the various RSS Reader options out there. More
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
May 15, 2020
On the Science and Philosophy of DEVS

I think DEVS is probably the best show I’ve seen since Game of Bad Endings. And DEVS had a great ending, so that puts it on top.
This piece contains spoilers.
I am particularly excited when a project can combine great ideas, story, and acting in a single effort. Upload is a great show, for example, but it wants for two of the three.
DEVS hits all three for me. But rather than talk about how great it is, which is kind of boring, I’m going to talk about what I took issue with.
1. They never talk about how to get around the complexity of simulating that many variables
I get that the God in the Machine is the secret-sauce quantum tech they developed, but I didn’t see them address how that’s supposed to allow them to simulate entire universes.
The complexity is mind-blowing for doing such a thing for a single moment in time. Even if the processing were possible using something magically quantum, I can’t fathom the memory and storage that’d be required.
They seemed to perform a magician’s trick by talking about whether the universe is singular vs. the multiverse model, but that doesn’t do it for me. It’s a clear distraction from the level of resources that would be required—even if you could somehow run the computations (because quantum).
That must be some compression algorithm.
Perhaps I simply don’t grok enough of the relevant science here.
In short, this doesn’t get around the problem of needing a universe to store a universe. Sure, maybe you have an amazing compression algorithm (space is full of space, afterall), but still…
We’re talking about storing a universe for every instant in the universe, which, even if you were only saving changes would be colossal.
Again, it’s sci-fi. And they did show us the one artifact/idea that we’re supposed to accept and move on from. But because they were so technical with many parts of the science I would have loved to hear a theoretical explanation for how they solved the problem of saving that much state data.
2. They messed up the hard determinism bit when they showed people what they’d do in multiple seconds, minutes, or days in the future
The scene where the guy was seeing himself react like a second in the future was spectacular. The reason it worked, and was realistic, is because he didn’t have time to review the prediction and adjust.
This doesn’t work—even in hard determinism—where you show someone what they’ll do an hour from now. Let’s look at why.
Even if you take away true, absolute free will from the equation, humans are processing engines capable of arriving at a desired path of execution.
If you show me that I’ll pick heads 10 times in a row when you flip a coin, and you offer to pay me $1,000 dollars if I pick tails, my brain can calculate that I want to defy your prediction, or that I want the money. So I can easily end up saying the word “tails” while the coin is next in the air.
That’s not breaking determinism. That’s processing a flow of inputs that includes you giving me a reason to not say heads. That flow is deterministic, but it doesn’t look like it unless you 1) can see all the variables, or 2) can look backward at the choice that was made.
Second order chaos is chaos that responds to prediction.
It’s like first and second-order chaos. We can predict the weather even though it’s extremely complex—to the point of being pseudo-random. But we can’t predict the stock market because it depends on how people react to chaos.
Weather is predictable because it doesn’t change its behavior when the prediction has been made. Humans can. And that doesn’t require us to break determinism for that to work. It’s just a stream of inputs that we react to.
The real issue here is another sci-fi concept that wasn’t explored, which is that of the paradox. John Connor sending someone back to protect him, which resulted in him being born, for example.
If time is determined, and you go back and change the inputs at some point in the stream, that changes everything after that point. As soon as the inputs change, the outputs do as well. That’s determinism.
Showing a rational agent an outcome they want to avoid in the future—which is the result of choosing option A—allows them to take option B instead. That’s not free will, that’s just processing based on what you think will happen vs. what you want to happen, based on modeling various scenarios.
Change the information you have and your processing might “choose” a different path. And that’s what showing the future does: it changes the inputs. Second-Order Chaos.
3. The breaking of determinism by having the hero make a “true choice” was the weakest part of the whole show
This was super annoying. You either have a show based on hard determinism or you don’t.
The magic was the quantum computer that made this all possible. You can’t add new magic in the last episode. It’s against the sci-fi rules.
She’s the first human to make a free choice? Really?
How? Why?
I would have preferred her doing something innovative based on her knowledge that everything is determined, combined with the fact that we can run simulations that are essentially alternative realities.
Work within the rules you’ve established. There’s tons of room for creativity there.
It doesn’t require true choice.
In fact, that’s kind of the whole point.
Summary
These points did bother me, but they only brought the show from a 10/10 to 9/10 in my opinion.
There is still expansive ground to cover with the maintaining of those various realities, and the fact that you can simply select a branch and drop people into it.
I hope there’s a second season.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
May 14, 2020
Summary: Capital and Ideology
8/10
My One-Sentence Summary
Content Extraction
Takeaways
My book summaries are designed as captures for what I’ve read, and aren’t necessarily great standalone resources for those who have not read the book.
Their purpose is to ensure that I capture what I learn from any given text, so as to avoid realizing years later that I have no idea what it was about or how I benefited from it.
My One-Sentence Summary
Inequality manifests itself in identifiable patterns throughout history, and it’s possible to identify those patterns, and to counter the forces that lead to them by creating a political system that’s inclusive and participatory by design.
Content extraction
We used to be heavily focused on three basic levels of society: workers, soldiers, thinkers, and these three can be seen repeating for millennia throughout history
At some point we became obsessed with ownership of property, which is bad for society. The obsession, not the concept itself
This obsession with ownership continues to stratify society
The educated used to vote purely republican, now they vote mostly democrat
The left used to be the party of the worker (which is why they used to be racist), and now they’re the party of the educated
There is hope for centrism because there are factions within the left and the right that lean in that direction
The problem is that there are extreme left types who want to do dramatic redistribution of wealth, and there are radical right types who want radical isolationism and othering
It is possible to make society more equitable, and we’ve done it in the past (like after WWII)
It takes active effort to engineer a society that is more just
We cannot simply give up and accept dramatic differences in education, income, and wealth, because they will ultimately destroy everyone, not just the poor
That’s the irony: it’s self-defeating for the rich to care only about themselves. All they do is prolong a guaranteed reset of society at some point in the future
There are a series of representation and taxation policies that can be used to improve things, but they require the vision and courage to carry them out
Takeaways
It takes active effort—and extreme courage—to counter the natural tendency to stratify
It’s incumbent on the less extreme people in the left and right to form a new, logical center
I learned more about colonialism and American slavery from this Frenchman than I ever did in school
After reading this book, combined with hearing Scott Galloway on the PIVOT podcast, I’m extremely pessimistic. The will doesn’t seem to be there. Everyone is out for themselves. Which means the only path back to baseline will be revolution and/or war. Turns out the pandemic will only accelerate the inequality. So we’ll wait for the catastrophic reset, at which point the clock starts again. Build up, tear down. Yay humans.
You can find my other book summaries here.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
Unsupervised Learning: No. 228

The podcast and newsletter are the same content in different mediums.
THIS WEEK’S TOPICS: Thunderbolt Attack, Celebrity Ransomware, ClearView Government, Blackhat DEFCON Virtual, War Thunder, 5G Bio Attacks, PC Game Cheating, Zoom Keybase, Technology News, Human News, Ideas Trends & Analysis, Discovery, Recommendations, and the Weekly Aphorism…
The newsletter serves as the show notes for the podcast.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
10 Behaviors That Will Reduce Your Risk Online
I wrote an article recently on how to secure your home network in three different tiers of protection. In that piece I wanted to link to some safe internet practices—which some used to call Safe Hex—but I couldn’t find anything newer than nine years old.
These are the diet and exercise of the computer safety world.
So, I decided to update the advice myself. What follows is a set of basic security hygiene steps that will significantly reduce your risk online.
1. Use unique, strong passwords, and store them in a password manager
Automatic Logins Using Lastpass
Many people get hacked from having guessable or previously compromised passwords. Good passwords are long, random, and unique to each account, which means it’s impossible for a human to manage them on their own. A password manager is a piece of software that creates all these for you, keeps them stored safely, and then fills them in for you automatically when you need to log in.
Don’t overthink the choice between the two: they’re both solid options.
Using any of the top password managers is far better than using passwords alone.
Pick either 1Password or LastPass, go through all your accounts, and for each one…reset the password to something created by (and stored in) your password manager.
2. Keep your firmware and software updated
Keep all of your software and hardware religiously updated. Turn on automatic updates, install updates from the operating system when you’re asked to, and make a regular habit of updating everything in your technology ecosystem.
That means your computers, laptops, phones, gaming systems, smart home appliances, etc. Everything.
3. Enable two-factor authentication on all critical accounts
Setting up Google 2FA
Your email and phone accounts are critical because they’re used to reset passwords on most of your other accounts.
For your most important accounts—such as those controlling your email account, your bank, and your mobile phone account—you should enable two-factor authentication. This means even if you have the password, an attacker would still need an additional thing to be able to get into your account, such as your phone.
Text-based two-factor is not ideal, but it’s far better than having nothing.
Go to each of those high-priority accounts and ensure two-factor authentication (often called strong authentication) is turned on. If you have the option between using a 2-factor authentication application or using SMS (text messaging) for the second factor, the app option is more secure—but not enough to worry about. Text-based two-factor is still far better than having a password by itself.
4. Don’t click links or attachments in emails, text messages, or any other media—especially from untrusted sources
It’s hard to say what’s worse—re-using weak passwords across multiple important accounts, or being too click-happy when it comes to incoming content.
For example, instead of sending a link to a picture, ask them to send the picture itself.
Even if you are using good passwords and have all the updates installed, it’s still possible to get compromised by clicking on links.
Your best possible bet is to get in the habit of not clicking on things.
Read emails, don’t click links in them. Read text messages, don’t click links in them. Try to get in the habit of telling people not to send you links, because you won’t click them.
This one behavior will massively reduce your chance of being infected!
5. Use your operating system’s antimalware capabilities, keep them updated, and (optionally) use MalwareBytes in addition
Built-in security in Windows 10
It’s a little-known fact that Windows and Mac anti-malware systems are catching up to the dedicated offerings by third-parties. They are, and you should be taking advantage of that functionality.
Some say these tools are already redundant, but there’s no harm in having both.
In addition to turning on the native anti-malware and firewall features in your operating system, also consider installing MalwareBytes as an extra layer of protection.
6. Stay on reputable websites. The more fringe the site, the higher the risk of bad things happening while you’re there

Live footage of someone visiting a random website
When you visit a website, you are agreeing to have your computer execute thousands of lines of code from that site. They are dropping cookies on your computer, they’re serving you ads, and yes—you’re executing computer code written by them as well. It’s like being blindfolded and forced to eat random things put in your mouth.
Browsing random websites is like having someone blindfold you, put something in your hand, and say, “Eat this.”
You unfortunately have little choice about the blindfold when navigating the web, because it’s not possible for most people to inspect the thousands of lines of code on every page you visit. But you can choose to walk in friendly places as much as possible.
Try to stay on reputable sites, and be more cautious as you venture into bad web neighborhoods. Landing on a webpage is agreeing to eat whatever they feed you. Be careful who you do that with.
7. Don’t use filesharing sites to gain access to free content
A typical view when browsing filesharing sites
Filesharing sites are notorious for malware, and the reputation is deserved.
It’s remarkably easy to take a movie—or any type of media—wrap it up with ransomware, and share it to one of these sites. Then all the attackers have to do is wait for victims to show up, and collect their money.
Don’t be one of their victims. Don’t use filesharing sites.
8. Don’t install things like plugins, toolbars, extensions, or download managers when prompted online
don’t install software from random places on the internet
Don’t randomly install software, and definitely not while browsing some website. If something seems worthwhile, stop, open a different browser window, and investigate it by going to the official source.
If browsing a website is taking food from a stranger, then installing software is like taking medicine from one.
Try to only install software using your operating system’s official mechanism, such as its app store.
9. Don’t trust incoming offers; disconnect and go through the official channel instead
Now we’re getting into the more powerful and overarching advice.
Being able to sense what’s out of the ordinary comes with time.
We’ve learned to avoid clicking and installing things, and even browsing to sites that seem shady. We’re basically training ourselves to be extremely cautious in everything we do, and that’s a good thing.
But sometimes you are actually sent something interesting, and you’re really curious. Well, here’s what you do.
Stop.
If it’s a link, don’t click it.
If it’s a phone offer, don’t say yes.
Disconnect from that email/text/phone call.
Open a separate window and investigate from the orginal source.
Example 1: Someone calls you and says they work for AT&T and they can give you 30% off your bill if you give your credit card right now. No. Ask them the name of the promotion and where you can find it online. If they tell you it’s only a phone offer, they’re lying. That’s not how legitimate businesses work. Get off the phone and investigate yourself by going to the AT&T site directly.
Example 2: Someone emails or texts you a link for a buy-1-get-one-free promotion for your favorite spa. Do not click it. Close and/or delete that message, and go to the spa website directly. If there’s a coupon code in the email/text, and you think it might be legitimate, write it down. And if you find it’s a real promotion when you look at the site directly, you can type the code in manually.
In both cases here, we STOPPED the flow that was happening. If you feel pressured to click, or pressure to say yes on the phone, you should sense danger. Break contact and do your own research!
When a trained security professional accidentally clicks a phishing link, they often tell me afterwards that they knew the whole time they were doing it that they had a bad feeling.
10. If you get a bad feeling, or something seems out of the ordinary, don’t give into curiosity

Respect your spider sense, and work to improve it using the behaviors above
And finally, as a general rule to number 9 above—never give in to curiosity, don’t let yourself supress warning signs, and never allow yourself to feel rushed.
If something feels strange, or smells bad, or you find yourself getting overly excited about how great a deal something seems to be—STOP! That’s dangerous.
Don’t click. Don’t accept. Don’t proceed.
Trust your Spidey-sense.
Summary
If you follow these 10 rules, and turn them into habits, you will quickly become one of the safest people on the internet. and here’s an infographic to help you remember them.
Stay safe out there!

An infographic of the 10 Safe Hex rules
Notes
I didn’t include WiFi security in the list because it’s not an internet-based threat. Someone has to be near your house to take advantage, which is a completely different threat model. But all the same, you should have a long, strong, and unique password for your WiFi, which you store in a password manager. And for extra security, consider hiding your SSID so that people don’t even try to connect to you in the first place.
The most important two things to take away from this article are: 1) the better you are at the basics, the safer you will be against 99.99% of threats you’ll face online, and 2) if you are truly targeted by someone with skill, these measures will only serve as an annoying speedbump.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
How to Practice Safe Hex and Reduce Your Risk Online

I wrote an article recently on how to secure your home network in three different tiers of protection. In that piece I wanted to link to some safe internet practices—which some used to call Safe Hex—but I couldn’t find anything newer than nine years old.
These are the diet and exercise of the computer safety world.
So, I decided to update the advice myself. What follows is a set of basic security hygiene steps that will significantly reduce your risk online.
1. Use unique, strong passwords, and store them in a password manager

Automatic Logins Using Lastpass
Many people get hacked from having guessable or previously compromised passwords. Good passwords are long, random, and unique to each account, which means it’s impossible for a human to manage them on their own. A password manager is a piece of software that creates all these for you, keeps them stored safely, and then fills them in for you automatically when you need to log in.
Don’t overthink the choice between the two: they’re both solid options.
Using any of the top password managers is far better than using passwords alone.
Pick either 1Password or LastPass, go through all your accounts, and for each one…reset the password to something created by (and stored in) your password manager.
2. Keep your firmware and software updated
Keep all of your software and hardware religiously updated. Turn on automatic updates, install updates from the operating system when you’re asked to, and make a regular habit of updating everything in your technology ecosystem.
That means your computers, laptops, phones, gaming systems, smart home appliances, etc. Everything.
3. Enable two-factor authentication on all critical accounts

Setting up Google 2FA
Your email and phone accounts are critical because they’re used to reset passwords on most of your other accounts.
For your most important accounts—such as those controlling your email account, your bank, and your mobile phone account—you should enable two-factor authentication. This means even if you have the password, an attacker would still need an additional thing to be able to get into your account, such as your phone.
Text-based two-factor is not ideal, but it’s far better than having nothing.
Go to each of those high-priority accounts and ensure two-factor authentication (often called strong authentication) is turned on. If you have the option between using a 2-factor authentication application or using SMS (text messaging) for the second factor, the app option is more secure—but not enough to worry about. Text-based two-factor is still far better than having a password by itself.
4. Don’t click links or attachments in emails, text messages, or any other media—especially from untrusted sources
It’s hard to say what’s worse—re-using weak passwords across multiple important accounts, or being too click-happy when it comes to incoming content.
For example, instead of sending a link to a picture, ask them to send the picture itself.
Even if you are using good passwords and have all the updates installed, it’s still possible to get compromised by clicking on links.
Your best possible bet is to get in the habit of not clicking on things.
Read emails, don’t click links in them. Read text messages, don’t click links in them. Try to get in the habit of telling people not to send you links, because you won’t click them.
This one behavior will massively reduce your chance of being infected!
5. Use your operating system’s antimalware capabilities, keep them updated, and (optionally) use MalwareBytes in addition

Built-in security in Windows 10
It’s a little-known fact that Windows and Mac anti-malware systems are catching up to the dedicated offerings by third-parties. They are, and you should be taking advantage of that functionality.
Some say these tools are already redundant, but there’s no harm in having both.
In addition to turning on the native anti-malware and firewall features in your operating system, also consider installing MalwareBytes as an extra layer of protection.
6. Stay on reputable websites. The more fringe the site, the higher the risk of bad things happening while you’re there

Life footage of someone visiting a random website
When you visit a website, you are agreeing to have your computer execute thousands of lines of code from that site. They are dropping cookies on your computer, they’re serving you ads, and yes—you’re executing computer code written by them as well. It’s like being blindfolded and forced to eat random things put in your mouth.
Browsing random websites is like having someone blindfold you, put something in your hand, and say, “Eat this.”
You unfortunately have little choice about the blindfold when navigating the web, because it’s not possible for most people to inspect the thousands of lines of code on every page you visit. But you can choose to walk in friendly places as much as possible.
Try to stay on reputable sites, and be more cautious as you venture into bad web neighborhoods. Landing on a webpage is agreeing to eat whatever they feed you. Be careful who you do that with.
7. Don’t use filesharing sites to gain access to free content

A typical view when browsing filesharing sites
Filesharing sites are notorious for malware, and the reputation is deserved.
It’s remarkably easy to take a movie—or any type of media—wrap it up with ransomware, and share it to one of these sites. Then all the attackers have to do is wait for victims to show up, and collect their money.
Don’t be one of their victims. Don’t use filesharing sites.
8. Don’t install things like plugins, toolbars, extensions, or download managers when prompted online.

don’t install software from random places on the internet
Don’t randomly install software, and definitely not while browsing some website. If something seems worthwhile, stop, open a different browser window, and investigate it by going to the official source.
If browsing a website is taking food from a stranger, then installing software is like taking medicine from one.
Try to only install software using your operating system’s official mechanism, such as its app store.
9. Don’t trust incoming offers; disconnect and go through the official channel instead
Now we’re getting into the more powerful and overarching advice.
Being able to sense what’s out of the ordinary comes with time.
We’ve learned to avoid clicking and installing things, and even browsing to sites that seem shady. We’re basically training ourselves to be extremely cautious in everything we do, and that’s a good thing.
But sometimes you are actually sent something interesting, and you’re really curious. Well, here’s what you do.
Stop.
If it’s a link, don’t click it.
If it’s a phone offer, don’t say yes.
Disconnect from that email/text/phone call.
Open a separate window and investigate from the orginal source.
Example 1: Someone calls you and says they work for AT&T and they can give you 30% off your bill if you give your credit card right now. No. Ask them the name of the promotion and where you can find it online. If they tell you it’s only a phone offer, they’re lying. That’s not how legitimate businesses work. Get off the phone and investigate yourself by going to the AT&T site directly.
Example 2: Someone emails or texts you a link for a buy-1-get-one-free promotion for your favorite spa. Do not click it. Close and/or delete that message, and go to the spa website directly. If there’s a coupon code in the email/text, and you think it might be legitimate, write it down. And if you find it’s a real promotion when you look at the site directly, you can type the code in manually.
In both cases here, we STOPPED the flow that was happening. If you feel pressured to click, or pressure to say yes on the phone, you should sense danger. Break contact and do your own research!
When a trained security professional accidentally clicks a phishing link, they often tell me afterwards that they knew the whole time they were doing it that they had a bad feeling.
10. If you get a bad feeling, or something seems out of the ordinary, don’t give into curiosity

Respect your spider sense, and work to improve it using the behaviors above
And finally, as a general rule to number 9 above—never give in to curiosity, don’t let yourself supress warning signs, and never allow yourself to feel rushed.
If something feels strange, or smells bad, or you find yourself getting overly excited about how great a deal something seems to be—STOP! That’s dangerous.
Don’t click. Don’t accept. Don’t proceed.
Trust your Spidey-sense.
Summary
If you follow these 10 rules, and turn them into habits, you will quickly become one of the safest people on the internet. and here’s an infographic to help you remember them.
Stay safe out there!

An infographic of the 10 Safe Hex rules
Notes
I didn’t include WiFi security in the list because it’s not an internet-based threat. Someone has to be near your house to take advantage, which is a completely different threat model. But all the same, you should have a long, strong, and unique password for your WiFi, which you store in a password manager. And for extra security, consider hiding your SSID so that people don’t even try to connect to you in the first place.
The most important two things to take away from this article are: 1) the better you are at the basics, the safer you will be against 99.99% of threats you’ll face online, and 2) if you are truly targeted by someone with skill, these measures will only serve as an annoying speedbump.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
May 8, 2020
A 3-Tiered Approach to Securing Your Home Network

A lot of people are thinking about the security of their home network right now, and as one of the project leaders on the OWASP Internet of Things Security Project, I wanted to provide three levels of security you can do at home.
The most important thing to realize about this list is that it’s top-heavy. The first one is far more important than the second, and the first three are far more important than the second three. Etc.
Let’s start with Level 1.

There are security/hacker types that maintain massive repositories of passwords.
Change all default passwords to something unique and strong. This is the most important thing in this article. Most home networks get broken into through either phishing or some random device they have with a bad password. It’s usually a password that was never configured or never changed from the default. Use a password manager to make and store good passwords that are different for every account/device.
Patch all computers, routers, and other devices on the network. The second most important thing to do is make sure you keep all your computers and devices updated with security fixes. You should enable automatic updates if available, and try to update at least weekly if not.
Install MalwareBytes on all laptop and desktop computers. MalwareBytes has somehow won the battle of the best consumer anti-malware offering. And although it is a paid product, it serves as an extra layer of protection for users that aren’t the most educated or careful when it comes to practicing Safe Hex. Which is most people.
95% is a guess, but it’s probably closer to 99%.
If you did just those two things you’d be more secure than 95% of home users out there. But let’s look at Level 2.

Enable 2FA for high-risk systems. Most peoples’ highest risk systems are their primary email account and their mobile phone account. These are the keys that open all doors into every other account you have (because they’re how you do account recovery). Next come your social media accounts, and then any accounts that control IoT systems in your house. Do you have internet-connected lights, appliances, gaming systems, media systems, etc? Get their passwords changed (see above), and enable two-factor authentication.
Segment your high-risk devices onto a separate network. The next strong control to consider is segmenting your network. This is where you take your higher-risk systems, like your IoT devices, your entertainment systems, gaming systems, etc., and place them on their own network—separate from your personal computers, laptops, phones, etc.
One could argue putting this in the basic section.
Change your DNS to 1.1.1.2, or 1.1.1.3 to get privacy and malicious domain filtering.Next, you can consider changing your DNS settings on all your devices to use those by Cloudflare. There are plenty of good options, actually; I’m just trying to be prescriptive. 1.1.1.2 blocks just malware, and 1.1.1.3 blocks malware and adult content. Make sure to set these on not just your router, but on your other devices as well.

So if you’ve done all that, you can now move into the tasty stuff at Level 3. This section requires some pretty significant technical knowledge to implement, and is probably far more than most people need. But it’s fun!
Use Rumble to inventory your home network’s assets. Anyone serious about security starts with understanding what they’re defending, and that’s where Rumble comes in. It’s a tool created by H.D. Moore that creates a continuously-updated inventory of your local network, and there’s a free version for home networks! Install that, run regular scans, and investigate anything out of the ordinary.
Use CanaryTools to monitor for malicious tampering on your network. After you have your inventory, you can move into looking for actual signs of trickery on the network. The most efficient way to do that is with Canary Tokens, and once again, there’s a free version! Create some, sprinkle them around, and look for hits.
The Dream Machine even has a built-in honeypot and port scanner.
Upgrade to a prosumer router like a Ubiquiti Dream Machine to get enterprise security features. Next you might want to look at a higher-end router. The Ubiquiti stuff has been getting better and better over the years, and as someone who started in firewall engineering, I’m starting to see tons of enterprise features in these things. Enterprise Auth, Geo-based Black/Whitelisting, MAC-based controls, IDS/IPS, Signal Optimization, Logging Capabilities, etc. Another option is an Astaro Security Gateway, by Sophos.
This should get you going.
Remember, doing the first few properly will massively improve your security. And for the best results, get as many people that you know and care about to do the first 2!
Here’s the full list as an infographic.
Notes
Many security professionals stopped using antivirus many years ago, and more and more are doing so as native offerings from operating systems improve. The native protections are actually quite good, and combined with practicing Safe Hex, most professionals can get away with not running anything.
I personally also run MalwareBytes, which I consider to be excellent, and I do recommend it to some when I think they need it. But the fact is that I’ve never had a hit on it in the several years that I’ve run it, and it’s also a paid product. So I often ask myself why I run it at all. Again, Safe Hex and an updated operating system are your best protections against mundane stuff. And for super-targeted and/or custom attacks, neither of those will help you anyway.
A previous version of the advanced section included running Suricata from a tap on your network, which is still a lot of fun and offers great additional security. But it requires quite a bit of knowledge, setup, and time to do properly. More
Another great option for the advanced section is the use of a PiHole. It’s more in the spaces of blocking ads and providing privacy, but it’s definitely worth a look. More
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
A 3-tiered Approach to Securing Your Home Network

A lot of people are thinking about the security of their home network right now, and as one of the project leaders on the OWASP Internet of Things Security Project, I wanted to provide three levels of security you can do at home.
The most important thing to realize about this list is that it’s top-heavy. The first one is far more important than the second, and the first three are far more important than the second three. Etc.
Let’s start with Level 1.

There are security/hacker types that maintain massive repositories of passwords.
Change all default passwords to something unique and strong. This is the most important thing in this article. Most home networks get broken into through either phishing or some random device they have with a bad password. It’s usually a password that was never configured or never changed from the default. Use a password manager to make and store good passwords that are different for every account/device.
Patch all computers, routers, and other devices on the network. The second most important thing to do is make sure you keep all your computers and devices updated with security fixes. You should enable automatic updates if available, and try to update at least weekly if not.
95% is a guess, but it’s probably closer to 99%.
If you did just those two things you’d be more secure than 95% of home users out there. But let’s look at Level 2.

Enable 2FA for high-risk systems. Most peoples’ highest risk systems are their primary email account and their mobile phone account. These are the keys that open all doors into every other account you have (because they’re how you do account recovery). Next come your social media accounts, and then any accounts that control IoT systems in your house. Do you have internet-connected lights, appliances, gaming systems, media systems, etc? Get their passwords changed (see above), and enable two-factor authentication.
Segment your high-risk devices onto a separate network. The next strong control to consider is segmenting your network. This is where you take your higher-risk systems, like your IoT devices, your entertainment systems, gaming systems, etc., and place them on their own network—separate from your personal computers, laptops, phones, etc.
One could argue putting this in the basic section.
Change your DNS to 1.1.1.2, or 1.1.1.3 to get privacy and malicious domain filtering.Next, you can consider changing your DNS settings on all your devices to use those by CloudFlare. There are plenty of good options, actually; I’m just trying to be prescriptive. 1.1.1.2 blocks just malware, and 1.1.1.3 blocks malware and adult content. Make sure to set these on not just your router, but on your other devices as well.

So if you’ve done all that, you can now move into the tasty stuff at Level 3. This section requires some pretty significant technical knowledge to implement, and is probably far more than most people need. But it’s fun!

a ubiquity dashboard
Use Rumble to inventory your home network’s assets. Anyone serious about security starts with understanding what they’re defending, and that’s where Rumble comes in. It’s a tool created by H.D. Moore that creates a continuously-updated inventory of your local network, and there’s a free version for home networks! Install that, run regular scans, and investigate anything out of the ordinary.
Use CanaryTools to monitor for malicious tampering on your network. After you have your inventory, you can move into looking for actual signs of trickery on the network. The most efficient way to do that is with Canary Tokens, and once again, there’s a free version! Create some, sprinkle them around, and look for hits.
Upgrade to a prosumer router like a Ubiquity Dream Machine to get enterprise security features. Next you might want to look at a higher-end router. The Ubiquity stuff has been getting better and better over the years, and as someone who started in firewall engineering, I’m starting to see tons of enterprise features in these things. Enterprise Auth, Geo-based Black/Whitelisting, MAC-based controls, IDS/IPS, Signal Optimization, Logging Capabilities, etc. Another option is an Astaro Security Gateway, by Sophos.
Tap your network and implement Suricata’s Emerging Threat rules to detect malicious activity. And finally, if you’re seriously into this stuff, you should look at getting into a real IDS. Suricata is based on Snort, and it’s what I’ve used for the last few forevers, and I recommend using the ET Signatures.
Ok, so this should get you going.
Remember, doing the first few well will massively improve your security. And for the best results, get as many people that you know and care about to do the first two!
Here’s the full list as an infographic.

—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
May 6, 2020
Why Aspiring Influencers Should Build Their Brands on Their Own Domains

I’ve been blogging consistently since 1999 and I’m often asked my top advice for someone starting out. My answer is easy—and it’s not even close—build everything on your own domain.
The title says “influencers”, which, nobody actually knows the definition of. I’m using that term because it’s common, but if forced my definition would be: “Anyone looking to grow an audience around their creative output.”
That’s broad enough to encompass makers, artists, musicians, hackers, writers, gamers, journalists, photographers, chefs, moms, poets, and everything in between. Really, it’s anyone producing something useful to someone else, and who plans on sharing that with a wider audience.
YouTube is an exception, because YouTube.
So, with that out of the way, here’s why you should only do this on your own domain, and not using one that belongs to a third-party platform.
1. Your domain is your brand
As a creator, your domain stays with you for life.
I’m not sure John Gruber would have chosen Daring Fireball to be his permanent home. Or that Dave Winer would have chosen scripting.com. But they did, and that’s them now. It’s their identity.
Ideally you’d have something more tied to your name, but that’s not necessary. What’s necessary is that you have something you’ll like in 20 years. Try to avoid androidupdates.com, for example. Because if you want to start writing about nature photography it’ll be a little weird.
But your domain is the center of your internet creator life, and you want to dilute that as little as possible by referring to other places.
2. Controlling your future means controlling your traffic
Whoever controls your traffic, controls your audience.
If you’re on Medium, or Nuzzle, they have traffic. They have followers. You are largely abstracted from that equation as a faceless author on their amazing platform. The platform is the star, not you. You’re lucky to be there. You should be honored.
Screw that. You are the one writing. You’re the one making stuff. If someone likes your content, you shouldn’t be sharing that incoming positivity with a greedy, rent-seeking landlord.
When you own the traffic you can redirect it how you want to. You can launch new services and ask your fans to try them out. You can set up new subdomains and branch out from there. You have control.
yourdomain.com/newsletter is infinitely better than somesite.com/yourname.
3. Platforms have conflicting incentives
A platform is out for itself, not for you.
They might start “with the user in mind”, and many do. And they might have great people in charge in the beginning, who are truly trying to make the internet a better place.
That’s all nice, but when a couple of years have passed, and they have lots of users, and lots of bills, and lots of employees—there will be hard questions.
They will need to monetize somehow. They’ll need to show a profit. They’ll be competing against other platforms. And under that kind of pressure, decisions will be made that don’t necessarily align with your interests.
When some random management team is called in to increase profits, they won’t be considering how it’ll affect you as a creator. They will make the decision that is best for them, which is completely fine.
But if you’re not there you can’t get hit with the shrapnel of those decisions.
4. Platforms come and go, your domain is forever
In my twenty years blogging I’ve probably used at least 10 different platforms—mostly very early on, and for very short periods of time.
Some of them were tech stacks, where I kept my own domain, but I’ve also flirted with writing on other domains as well.
It’s never taken me long to see the mistake I made. One time I showed up and saw my URLs were all changed.
I’ve seen blogging platforms crumble and blow away in a matter of a few years. I’ve seen goliaths like Moveable Type—which seemed invulnerable—get completely supplanted by a newer, shinier platform.
Live Journal
Blogger
TypePad
Tumblr
Moveable Type
Etc.
They all came and (mostly) went. And now we have a host of newcomers. Wix, Medium, Squarespace, etc. Some of these are pretty cool, but the odds of them surviving another five years aren’t great.
WordPress is the longest standing and most powerful platform right now (and this site runs the software), but even it will eventually evolve and/or die.
There’s one good bet though, and that’s DNS. Your domain.
As long as you’re on good software, which allows portability of your content, you can take all your hard work with you to any platform—just as I have all these times.
5. It’s cohesive and convenient to have a single home
And finally, it’s just nice to have a single handle to refer people to.
You have Instagram and YouTube? No problem, just send them to your site where you have links to all that stuff.
You have a newsletter and a podcast? No problem, just send them to /newsletter and /podcast off your same domain.
You can feel free to experiment with whatever other platforms you want, which basically serve as syndication for your content, but to avoid giving someone 13 different usernames and locations, you can just give them your site.
It’s your home.
Summary
I would spare you that pain.
Ramirez to MacLeod
Trust me on this. Consolidate on your domain, and try to avoid third-party platforms as much as possible.
Your domain is your brand
Control your traffic
Platforms put you second
Platforms are ephemeral
It’s nice to have a single home
Notes
There are certain platforms that you might not be able to avoid using, like YouTube and Instagram in 2020. That’s fine, just try to keep as much of your content focused around your own domain as possible given that reality, and still use your site as home base.
There’s another nuance here for backend platforms, such as MailChimp. I use MailChimp when I could theoretically build my own email infrastructure and do it myself. In this case, that would be a cost not worth paying for a few reasons: 1) it’s hard to send that many emails, so relying on someone who’s good at it has its advantages, and 2) they largely allow themselves to disappear into the background. The platforms to avoid are those that try to interject themselves between you and your audience.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers








