Daniel Miessler's Blog, page 68
May 25, 2020
Unsupervised Learning: No. 230

THIS WEEK’S TOPICS: Twitter Bots, Face Recognition Headsets, Chrome Bug Memories, Virtual Currency, White House OPSEC, Realtime Language Translation, Technology News, Human News, Ideas Trends & Analysis, Discovery, Recommendations, and the Weekly Aphorism…
The newsletter serves as the show notes for the podcast.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


May 24, 2020
An Information Security Glossary of Terms

I’ve been writing about Information Security for around 20 years now, and I’ve written a lot about the definitions of various terms. A number of people have asked me to assemble those definitions into a single location, and that’s what we’ve done below.
These terms are active works in progress, so if you can improve them please let me know.
Each term has a link to more discussion around each definition.
Threat
A negative event that can lead to an undesired outcome, such as damage to, or loss of, an asset. Threats can use—or become more dangerous because of—a vulnerability in a system. MORE
Risk
A risk, in plain language, is a chance of something bad happening combined with how bad it would be if it did happen. MORE
Threat Actors
The person, actor, entity, or organization that is initiating the given (Threat) scenario. This is generally reserved for human-driven scenarios, such as hack attempts. It doesn’t usually make sense to talk about threat actors when the event is a flood or an earthquake, for example. MORE
Vulnerability
Vulnerabilities are weaknesses in a system. They make threats possible and/or more significant. MORE
Programmer
A Programmer is someone who can solve problems by by manipulating computer code. They can have a wide range of skill levels—from just being “ok” with basic scripting to being an absolute sorcerer with any language. MORE
Hacker
A Hacker is someone who makes things. In this context, it’s someone who makes things by programming computers. This is the original, and purest definition of the term, i.e., that you have an idea and you “hack” something together to make it work. It also applies to people who modify things to significantly change their functionality, but less so. MORE
Developer
A Developer is a formally trained programmer. They don’t just solve problems or create things, but do so in accordance with a set of design and implementation principles. These include things like performance, maintainability, scale, robustness, and (ideally) security. MORE
Event
An event is an observed change to the normal behavior of a system, environment, process, workflow or person. Examples: router ACLs were updated, firewall policy was pushed. MORE
Alert
An alert is a notification that a particular event (or series of events) has occurred, which is sent to responsible parties for the purpose of spawning action. Examples: the events above sent to on-call personnel. MORE
Incident
An incident is an event that negatively affects the confidentiality, integrity, and/or availability (CIA) at an organization in a way that impacts the business. Examples: attacker posts company credentials online, attacker steals customer credit card database, worm spreads through network. MORE
Breach
A Breach is an Incident that results in the confirmed disclosure——not just potential exposure—of data to an unauthorized party. MORE
Penetration Test
A Penetration Test is a time-boxed technical assessment designed to achieve a specific goal, e.g., to steal customer data, to gain domain administrator, or to modify sensitive salary information. MORE
Red Team Engagement
A Red Team Engagement is a long-term or continuous campaign-based assessment that emulates the target’s real-world adversaries to improve the quality of the corporate information security defenses, which—if one exists—would be the company’s Blue Team. MORE
Vulnerability Assessment
A vulnerability assessment is a technical assessment designed to yield as many vulnerabilities as possible in an environment, along with severity and remediation priority information. MORE
Audit
An audit can be technical and/or documentation-based, and focuses on how an existing configuration compares to a desired standard. This is an important point. It doesn’t prove or validate security; it validates conformance with a given perspective on what security means. These two things should not be confused. MORE
White/Grey/Black-Box Testing
The white/grey/black assessment parlance is used to indicate how much internal information a tester will get to know or use during a given technical assessment. The levels map light to internal transparency, so a white-box assessment is where the tester has full access to all internal information available, such as network diagrams, source code, etc. A grey-box assessment is the next level of opacity down from white, meaning that the tester has some information but not all. The amount varies. A black-box assessment—as you’re hopefully guessing—is an assessment where the tester has zero internal knowledge about the environment, i.e. it’s performed from the attacker perspective. MORE
Risk Assessment
Risk Assessments, like threat models, are extremely broad in both how they’re understood and how they’re carried out. At the highest level, a risk assessment should involve determining what the current level of acceptable risk is, measuring the current risk level, and then determining what can be done to bring these two in line where there are mismatches. Risk Assessments commonly involve the rating of risks in two dimensions: probability, and impact, and both quantitative and qualitative models are used. In many ways, risk assessments and threat modeling are similar exercises, as the goal of each is to determine a course of action that will bring risk to an acceptable level. MORE
Threat Assessment
A threat assessment is a type of security review that’s somewhat different than the others mentioned. In general it pertains more to physical attacks than technology, but the lines are blurring. The primary focus of a threat assessment is to determine whether a threat (think bomb threat or violence threat) that was made, or that was detected some other way, is credible. The driver for the assessment is to determine how many resources—if any—should be spent on addressing the issue in question. MORE
Threat Modeling
Threat Modeling is not a well-understood type of security assessment to most organizations, and part of the problem is that it means many different things to many different people. At the most basic level, threat modeling is the process of capturing, documenting, and (often) visualizing how threat-agents, vulnerabilities, attacks, countermeasures, and impacts to the business are related for a given environment. As the name suggests, the focus often starts with the threat agent and a given attack scenario, but the subsequent workflow then captures what vulnerabilities may be taken advantage of, what exploits may be used, what countermeasures may exist to stop/diminish such an attack, and what business impact may result. MORE
Bug Bounty
A Bug Bounty is a type of technical security assessment that leverages crowdsourcing to find vulnerabilities in a system. The central concept is simple: security testers, regardless of quality, have their own set of strengths, weaknesses, experiences, biases, and preferences, and these combine to yield different findings for the same system when tested by different people. In other words, you can give 100 experienced security testers the exact same testing methodology and they’re likely to find widely different vulnerabilities. The bug bounty concept is to embrace this difference instead of fighting it by harnessing multiple testers on a single assessment. MORE
Red Team
Red Teams are internal or external entities dedicated to testing the effectiveness of a security program by emulating the tools and techniques of likely attackers in the most realistic way possible. The practice is similar, but not identical to, penetration testing, and involves the pursuit of one or more objectives—usually executed as a campaign. MORE
Blue Team
Blue Teams refer to the internal security team that defends against both real attackers and Red Teams. Blue Teams should be distinguished from standard security teams in most organizations, as most security operations teams do not have a mentality of constant vigilance against attack, which is the mission and perspective of a true Blue Team. MORE
Purple Team
Purple Teams exist to ensure and maximize the effectiveness of the Red and Blue teams. They do this by integrating the defensive tactics and controls from the Blue Team with the threats and vulnerabilities found by the Red Team into a single narrative that maximizes both. Ideally Purple shouldn’t be a team at all, but rather a permanent dynamic between Red and Blue. MORE
Green Team
An offensively-trained and defensively-focused security team dedicated to working with development and infrastructure groups to address issues discovered using offensive security techniques systemically and at scale across an organization. MORE MORE
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


May 23, 2020
Why I Believe Trump Will Win in 2020

I think Trump will win due to an unprecedented use of information warfare by our adversaries that will simultaneously activate and deactivate different voting groups within our country.
Faction 1 (Woke Liberals): The extreme left who need to believe in a candidate’s morality before they can support them, and I think they’re easy to convince not to vote
Faction 2 (Anyone But Trump): Those who hate Trump and will vote for anyone to get him out. They can more easily be convinced not to vote
Faction 3 (Independents): Are undecided, and will either be swayed by disgust for Trump or disgust for the Left. They are easy to convince not to vote
Faction 4 (Trump Devotees): Adore Trump, and they will vote in extremely high percentages
This is not a formal analysis, and I am neither a pollster nor a political scientist. This is simply how I see the factions that will be in play leading up to the election.
I believe November’s outcome will pivot on information campaigns that push and pull on these various groups—specifically, the Woke Liberal faction and the Anyone But Trump Faction.
For the Woke Liberals, it’s fairly easy to get them not to vote. You simply have to convince them that Biden is an antiquated sexist who acted inappropriately to women in the past—possibly up to the point of rape. That’s probably going to be easy to do, so the only remaining question will be how many of these voters move to the Never Trump camp.
The Never Trump camp is harder to dissuade because they’re already holding their noses. They’ve already told themselves they don’t need to like the Democrat, and that they just have to do their duty and get Trump out.
My problem with them is the reasoning seems shabby. It feels hard to vote someone out when you don’t believe in the alternative. In that scenario, any complications around voting are magnified. If you’re busy at work that day, if there are fewer polling places, etc., etc. There are a million small reasons that can add up to stop you from voting someone out.
So now let’s look at various pieces on the board.
There is a massive backlash against the Woke Left in this country. The country is far less left than the left thinks it is, and those who are moderately conservative have been aggravated by extreme left views. This is a huge activating function for turning Independents either towards Trump, or against voting altogether.
Forget the fact that it was he who completely failed to respond back in January/February.
If Trump can convince Independents that the left hurt the economy, many of them will vote for him. The longer the lockdown goes on in various forms, which continues to cause additional damage to the economy, the more Trump will be able to point at someone’s pain and say, “See! That’s what they did to you!” If this becomes a battle of narratives and emotions around economic pain, I don’t think Biden and the left will have a chance. Trump is remarkably good at blaming other people for his mistakes and getting people to believe him.
Biden can do extraordinary damage to himself during the next several months. Trump cannot. If there are to be any gaffes, revelations, or bombshells that surface before November, they will most likely harm Biden, which will influence the Independents, Wokers, and Never Trumpers to abstain or switch to Trump.
Inaction favors Trump. If things were to be so convoluted and distorted that people didn’t know which way was up, the result is most likely to be people staying home and not voting. That means that the dedicated Trump fans—which are guaranteed to vote in extreme numbers—will be the strongest force on the field.
There are, of course, some trends that hurt Trump.
People generally hate him as a person—even many conservatives
If the economy continues to worsen (which seems inevitable), any clear-headed person is likely to place at least some of that blame at Trump’s feet
I simply worry it won’t be enough.
I think disgust for the left will be too strong a force—combined with Trump’s ability to point blame at that same left for the economic damage caused by the lockdown.
That, combined with Biden being such a horrible candidate, will cause independents to either not vote or vote for Trump.
The surfacing of non-Woken-approved behavior on the part of Biden—combined with his likely collection of fresh gaffes—will take the extreme left off the board.
So that really leaves the Trump Acolytes vs. the Never Trumpers. How much can the left rally to produce a white-hot hatred for Trump that knocks down all other considerations, and actually motivates people to go out and get the job done?
I think they’re shit at it. They can’t rally anyone for anything. Whenever they open their mouths to name an enemy and march against it, they end up choosing Christmas songs, which further alienates the center of the country.
The left sucks at narrative. And the narrative is going to matter more than ever in this one.
We have all this division. We have all this chaos. We have all this anger. We have all this pain.
Those things are crying out for a story, and the left doesn’t have one. Their story is Trump is bad.
Trump’s story is that everything was fine before China started a virus and the liberals broke the economy.
And far, far too many people will take that story, because, at least it’s an answer. It’s an answer with handles. It’s easy to follow.
To me that wins the undecided vote, or at least a significant portion of it.
And then Biden and the DNC will combine their powers to kick as many balls into their own goal as possible, resulting in much of the left being paralyzed into apathy.
Activate the center and right with a clear narrative blaming China and the left
Move more independents to the right by highlighting the stupidity of the left
De-activate the left by highlighting Biden’s flaws
Mobilize a pro-Trump voting block that’s even bigger than last time
That’s the move that will win it for them, and I fear it could actually be taken by a wider margin than last time.
And finally—as a magnifier to all of this—I believe Russia will exacerbate every single aspect of this in the favor of Trump. I think they could easily spend more than a billion dollars to move the population as much as possible as I’ve described above.
Based on all the polling, it seems like Trump only needs 3-8 percentage points to win.
Unfortunately, I think between the narrative advantage they have, the massive backlash against the left from the middle, the large number of people who are actually pro-Trump and not telling anyone, and the help from Russia—they will easily move things by that amount.
I really hope I’m wrong, and that would be really easy as well.
The economy continues to crash and it’s so glaringly obvious that it’s Trump’s fault
The Russian influence on social media has a small to medium effect, but not nearly enough to change things
The never-Trumpers come out in massive force and easily win
I really can see that happening as well, but it seems more logical and positive, which brings me to my last point.
Every single thing that’s happened with Trump has been unexpected. It’s inconceivable that he won. It’s inconceivable that he wasn’t removed from office. It’s plainly astounding that he’s sitting in the White House right now at all.
So it just seems patently stupid to think—oh, don’t worry, the never-Trumpers are going to win this for us! Case closed!
That’s exactly the hubris that has us in this position now.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


May 21, 2020
Is China Making a Major Strategy Mistake?

I’ve been thinking a lot about China’s new strategy of rising to prominence, which is covered in a number of recent articles.
For the last several months I’ve been thinking about how China is just winning in all these areas.
They’re silently colonizing Africa
They’re about to take full control over Hong Kong
They’re getting even more aggressive in the South China Sea
They’re becoming even more hostile towards Taiwan
They continue to hack and conduct espionage against the US with impunity for the purpose of stealing intellectual property
They’re ramping up intimidation tactics against anyone who speaks out against them, even outside of China
At first I was thinking that this was guaranteed to work, and that we need to raise the alarm so we can counter it. But now I think China might be making a serious strategic error.
They’re being so blatant about these tactics that they’re likely to label themselves as hostile—in the minds of other countries—for decades to come.
So they might get extraordinary gains for the first 5-10 years, as they no doubt already have, but once the whole world figures out how predatory and self-centered they’re behaving they’ll make policy decisions that will exclude China for decades.
Most importantly, that includes finding other countries to produce their goods. Japan just did that, which seems largely prompted by COVID, but is likely also related to China’s action in the local theater over the last few years.
I don’t see China as inherently evil; I see them as reacting in a toxic way to past trauma.
It just seems to me like China would be far more effective if they played the long game here, i.e., being nicer to the rest of the world and at least pretending to be cooperative. I mean, even if they had full Mr. Burns level goals in mind (which I’m not convinced of), it’d still be most effective to play nice and spread the tentacles.
As it stands now, they’re going to expand those tentacles at maximum range and speed, and they’ll be cut off quickly once the world realizes they’re an overt enemy.
This is not the sort of strategic error I would expect them to make. Although, it could be that they already thought about this, and they’re 1) either in a major rush for some reason, or 2) they believe that the gains they will get in the beginning (before everyone turns against them) will be enough to keep them dominant even after the world turns against them.
That bet seems risky to me.
We’ll see.
Notes
Image by Johnathan Bartlett.
I received a very nice letter from a Chinese gentleman who agreed with my analysis, but who—like some of my other Chinese friends—was reticent to grant China’s innocence the way I was. He was worried that China is actually more broken even than I was describing. But it was a very nice email from a fellow human hoping for a better world.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


May 20, 2020
Frame: Defining My Life Theme

I have been thinking for the last couple of years about how to capture the underlying theme for all my intellectual pursuits.
I like to read, sure. But why? I like to learn stuff. I’m curious. But what is the goal? And I like to describe things and then share those descriptions.
All great, but what’s the point?
I think I might have it.
I think my primary, long-term interest is: the capture and articulation of goals for a given entity, combined with the building of frameworks that allow one to realize those goals.
And Federations of Planets.
This is critical for individuals trying to make their way in life. It’s critical for families. Businesses. Towns. Cities. Countries. Planets.
Capture what you’re trying to achieve
Build a system that will let you do so
Each of these steps can be broken into many pieces, of course, and it’s possible to go one level higher as well.
Building frameworks for achieving the goals of any given entity.
That actually captures both. So the one breaks into two, and from there they both break into many.
In my book, The Real Internet of Things, I wrote about this as Desired Outcome Management (DOM).
For the time being, I’m going to call this idea, Frame. First, it’s short and simple. Second, it implies structure, framework, and foundation. All good things.
I intend to write a book about this specifically, although I’m not in any particular rush to do so. For now I’ll settle for updating my about page, which I’m not looking forward to.
Like I say in that about page, if you’ve not written one for yourself, you absolutely should. It’s remarkably enlightening and difficult.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Frame

I have been thinking for the last couple of years about how to capture the underlying theme for all my intellectual pursuits.
I like to read, sure. But why? I like to learn stuff. I’m curious. But what is the goal? And I like to describe things and then share those descriptions.
All great, but what’s the point?
I think I might have it.
I think my primary, long-term interest is: the capture and articulation of goals for a given entity, combined with the building of frameworks that allow one to realize those goals.
And Federations of Planets.
This is critical for individuals trying to make their way in life. It’s critical for families. Businesses. Towns. Cities. Countries. Planets.
Capture what you’re trying to achieve
Build a system that will let you do so
Each of these steps can be broken into many pieces, of course, and it’s possible to go one level higher as well.
Building frameworks for achieving the goals of any given entity.
That actually captures both. So the one breaks into two, and from there they both break into many.
In my book, The Real Internet of Things, I wrote about this as Desired Outcome Management (DOM).
For the time being, I’m going to call this idea, Frame. First, it’s short and simple. Second, it implies structure, framework, and foundation. All good things.
I intend to write a book about this specifically, although I’m not in any particular rush to do so. For now I’ll settle for updating my about page, which I’m not looking forward to.
Like I say in that about page, if you’ve not written one for yourself, you absolutely should. It’s remarkably enlightening and difficult.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


May 19, 2020
Analysis of the 2020 Verizon Data Breach Report


TOPIC: In this episode, Daniel takes a look at the 2020 Verizon Data Breach Investigations Report. He looks at the key findings and talks about what they might mean to us going forward.
The newsletter serves as the show notes for the podcast.

The Dataviz Game on Point
Verizon’s Breach Report is one of the best infosec reports out there, and I’m always excited when I hear it’s been released. This year—with the lockdown—that’s even more the case. So I decided to do a dedicated edition of show for it.
I have to say, the report started strong with the very first thing I see being a super clean data visualization like we see above.
You can download the full report here.
So let’s get into it.
Key definitions
There’s lots of religion around definitions (trust me, I have my own church), so it’s important to lock that down in the beginning. These are the three that I see the most disagreement on when people talk about this report.
Incident
A security event that compromises the integrity, confidentiality or availability of an information asset.
Breach
An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
Hacking
1) Utilizing stolen or brute- forced credentials; 2) exploiting vulnerabilities; and 3) using backdoors and Command and Control (C2) functionality.
Key numbers

Top tactics utilized
This year, they looked at 3,950 breaches and 157,525 incidents—32,002 of which qualified to be analyzed by them
45% of breaches involved Hacking
Errors were causal events in 22% of breaches
72% involved large business victims
58% had personal data compromised
70% were perpetrated by external actors (30% involved insiders)
Organized crime was behind 55% of breaches
86% were financially motivated
Web Apps were involved in 43%
37% stole or used credentials
22% involved phishing
Phishing is usually going after credentials, but stealing money is continues to rise in popularity
Verizon’s analysis

Top actions for incidents vs. breaches
They say external actors have always been the majority, and that the rise of internal breaches is from better reporting, not increased frequency
The top actor was by far Organized Crime, at 55%
Nation-state, end-user, and system admins each took around 10% of the actor pool
The Error incident type continues to increase, with most other types falling
Hacking, social, and malware have fallen the most
The top 2 incident threat actions were DoS, and Phishing
The top 2 breach threat actions were Phishing and Use of Stolen Creds
Errors are now as common as social attacks, and more common than malware attacks
The top malware type is Password Dumper, because it really is about getting those creds

Hacking types and vectors
The top three ways of getting the malware are email link, direct install, and download by other malware
Within hacking, web applications accounted for over 95% of breaches
Over 80% involved using brute force or stolen creds
There was relatively little vuln exploitation or use of backdoors/C2
Social actions arrived via email over 96% of the time
Breaches that take days or less are rising, while those taking months or more are declining
They’re showing cyber-espionage as being down, which is surprising to me
DDoS is way up, both in numbers of attacks and the weight of them
My analysis
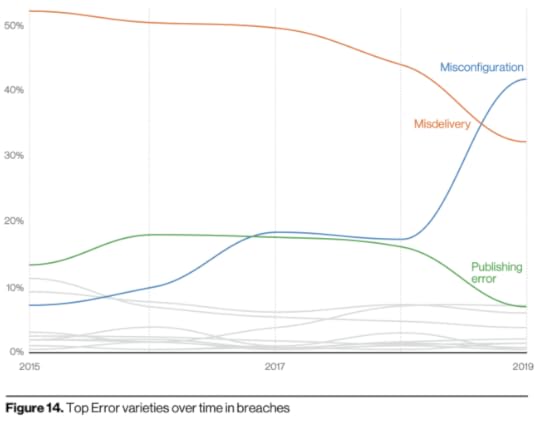
Misconfiguration is becoming a huge issue
I find it really interesting that in the top threat actions for breaches—so, successful incidents—the top 5 included: phishing, stolen creds, misdelivery (error), and misconfiguration (error).
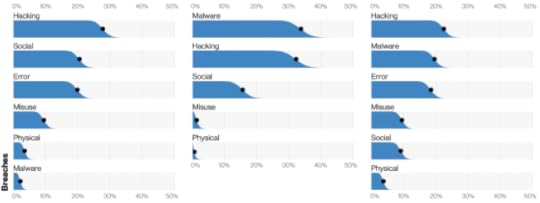
Different techniques used in different phases of the attack
On page 101 they mention that they’re standardizing their recommended controls on the CIS 20, which I think is smart.
So it seems like the major themes are:
Phishing (which is usually used to steal credentials)
Email security (because phishing)
Web applications (which are used to extract and input stolen credentials)
Stolen Creds (which are usually used against web apps)
In short, credentials.
And the second big theme seems to be misconfiguration, which I’ve always been on about, and is also why I’m so obsessed with recon.
All summed, this is another phenomenal report by the team at Verizon. I think I liked the structure and visuals of this report more than any other so far, so happy to see them constantly innovating on how they present their data.
Tons of data is useless if you can’t find compelling ways to display it, and I commend them for their work in that regard.
Remember, what you see above is just some highlights that jumped at me, but different readers will notice different things. So I definitely recommend you read the report yourself.
See you next year for the 2021 version.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


A Massive Collection of Zoom (Virtual Meeting) Backgrounds

We’re all doing more virtual meetings now, and virtual backgrounds have become a way to add some individuality to your visage.
Yes, you can use videos as your background in most applications.
When COVID first started, a ton of places started offering interesting backgrounds. It turns out that you can use pretty much anything you want for one. All you need is a quality image or video.
A lot of professional studios and artists released some of their own backgrounds as well, and after I saw like 10 of these collections on the internet I vowed to make a collection of the collections. So here it is:
How to change your background in Zoom
Images
Unsplash’s List
Studio Ghibli’s Backgrounds
Anime Backgrounds
Pocket Lint
The Good Housekeeping Collection
GotYourBack’s Optimism List
Den of Geek’s Geek Backgrounds
Canava’s List

Fine Art / Corbis Historical / Getty Images
TechRepublic’s Collection
Tom’s Guide List of Pop Culture Backgrounds
The Dad’s Nerd Backgrounds
Art Backgrounds from Modernmet
PC Mag’s Geeky List

Famous Paintings
Variety’s List of Movie/TV Backgrounds
Videos

Coverr’s Videos
Wibbitz Video Backgrounds
Kapwing’s Videos
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Are There Such Things as Anti-Fragile Stocks?

I was thinking recently about COVID-19, and stocks, and the concept of antifragility, which was coined by Nassim Taleb.
Here’s how he introduces it in his book with that title:
Some things benefit from shocks; they thrive and grow when exposed to volatility, randomness, disorder, and stressors and love adventure, risk, and uncertainty. Yet, in spite of the ubiquity of the phenomenon, there is no word for the exact opposite of fragile. Let us call it antifragile. Antifragility is beyond resilience or robustness. The resilient resists shocks and stays the same; the antifragile gets better.
Using that, let’s say that something is Antifragile when it improves from adversity. Not just survives. Improves.
So I was thinking about all these factors that we’re facing—many of which I talk about in my recent piece called COVID Will Accelerated Trends That Were Already Coming. Some of these include:
A move to automation, resulting in lost jobs
A move to remote work
A push for basic income
Consolidation of fewer winners
A rise in surveillance
Esports
Escapism
Etc.
At first I tried to imagine what stocks could survive in this situation. And I think it’s fairly easy to do that, although the question always has to be: survive at what timescale? Maybe the airlines will be fine eventually, but when exactly is eventually? I’m not willing to find out.
So here’s a more interesting question: when it comes to pandemics and economic slowdown, which stocks improve the most if things go poorly, yet still do fairly well if things don’t get that bad?
I came up with three.
AAPL Chart by TradingView
Amazon. They’re becoming planetary infrastructure, and they have a CEO who appears to be interested in everything from movie theaters to pharmacies to education. He basically wants to become what the government should have been. And while that’s scary and exciting, it’s also going to make their stock one of the best picks for a long time. If things go poorly, they’ll be there to keep things running. And if things go well, they’ll be there to expand into new spaces. Win, win.
Zoom. They seem to have captured the space of doing things remotely. Of course there will be competitors, but the way they’ve set themselves up to succeed is pretty impressive. If things go horribly regarding pandemics and declines, we’ll all need them more. And if things go well, they’ll still do fine. Win, win.
Facebook. Regardless of what you think about their effect on humanity, it’s clear that Zuckerberg is a voracious businessman. His purchases of Instagram and WeChat were phenomenal, and once again we have the dual benefit. If the world craters for a bit, everyone will be on Facebook. And if the world shakes it off quickly, the world will still be on Facebook. Win, win.
The internet (and the unemployment line) is full of people who think they “figured something out” about the stock market, right before they lost it all.
I have very little faith in my stock picks above because they’re stock picks, in the stock market. There’s also another whole line of thinking from smart people that say the NASDAQ is going to get pummelled in the next few months or years.
I honestly don’t know enough about this space to even tell who’s an expert and who isn’t. So I have very little money invested in this, and I’m doing it mostly for fun.
I’m basing my picks on what I think I know about human psychology, sociology, and what people are likely to do if things crash or if we recover quickly.
I honestly think these three stocks could do well either way. Hence, antifragile.
I’m marking this post as unalterable, because I want to measure just how lucky/unlucky/stupid/brilliant I am going forward in time. All edits to this post will be in the notes below, not in the prediction text above.
We’ll see how it goes.
Notes
You know how some people try to actually make you listen even more to them by prefacing things with, “I’m not an expert but…”? Well, this isn’t one of those situations. I’m seriously not qualified to give stock purchasing advice. Hell I made my first stock purchase like 5 years ago. I’m a noob. And even worse, I don’t even think being an expert makes you safe. So, seriously. Consider this post to be a thought exercise and nothing more.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


May 18, 2020
Unsupervised Learning: No. 229

THIS WEEK’S TOPICS: Feds Release Top Vulns, China Brainwave Tracking, Europe CISSP Masters, Army Electronic Warfare, Microsoft Third-largest Patch Tuesday, Technology News, Human News, Ideas Trends & Analysis, Discovery, Recommendations, and the Weekly Aphorism…
The newsletter serves as the show notes for the podcast.
—
If you get value from this content, you can support it directly for less than a latte a month ($50/year) which also gets you the Unsupervised Learning podcast and newsletter every week instead of just twice a month.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers







