Daniel Miessler's Blog, page 62
September 29, 2020
Cyber Pearl Harbor Is Happening Right Now — It’s Ransomware

Since 2007 the InfoSec industry has been talking about TheBigOne™—the event that would change cyber threats from annoyances to existential concerns.
They called it Cyber Pearl Harbor.
This doesn’t mean it can’t still happen.
The idea was that it’d be some massive blast that would take out the country’s power grid, or disable the entire internet, along with what they used to call e-commerce. That moment hasn’t happened (yet), but I think we’ve become the frog in the boiling cyber-water.
Ransomware is the Cyber Pearl Harbor we’ve been waiting for all along. It just looks different. Rather than being the one big blast, it’s more of a steady bombardment.
Ransomware is the new PCI.
— ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ (@DanielMiessler) September 19, 2020
1. It’s annoying
2. It’s not nearly the whole story
3. It’s forcing a lot of organizations to take security seriously
No catalyst for change compares to real-world consequences.
Business disruption is the ultimate argument.
Some stats:
At the time of this writing, Google News returns 7,460,000 results for the term Ransomware. More
SafetyDetectives reports the average cost of a ransomware-caused downtime incident has risen from $46,800 in 2018, to $141,000 in 2019, to $283,800 in 2020. More
The UHS hospital network, which is a Fortune 500 company with over 400 hospitals, has had multiple hospitals affected which required them to redirect patients to other options. More
According to Datto, Ransomware attacks are costing businesses more than $75 billion a year. More
Ransomware groups simply evolve too fast for small school districts with no IT staff.
She tried to reroute to another hospital and didn’t make it.
A woman recently died in Germany after she couldn’t receive critical care at her local hospital due to an attack. More
A ransomware attack against the New Orleans city government in early 2020 cost the city over $7 million dollars. More
New York City’s capital was hit with a ransomware attack in 2019 that took several key services offline. More
IBM says 1 in 4 of attacks its X-Force Team sees is caused by Ransomware. More
Ransom demands are increasing exponentially. In some cases, IBM Security X-Force is seeing ransom demands of more than $40 million. More
The skill and preparation asymmetry between attacker and defender is drastic.

My rough scribble of how ransomware sophistication surpassed our defensive capabilities somewhere around 2018
I think the only reason we survived this long without serious disruption to business—like we’re seeing now—is because attackers didn’t have their acts together. Their tooling wasn’t nearly as good as it is now, and they hadn’t linked their tooling with the business models.
Today there are multiple routes to make money from an insecure business. Once they get in—via RDP or Phishing or Drive-bys—they are not only extorting people who want to get their data back.

Google Trends Data for the term Cyber Peal Harbor
As a security person I sometimes have to admire their creativity.
Many groups have come to realize that some companies have good backups, so they start by stealing a copy of the data for themselves at the beginning of the attack. Then if someone doesn’t want to pay they can threaten to release the data and create a public incident.
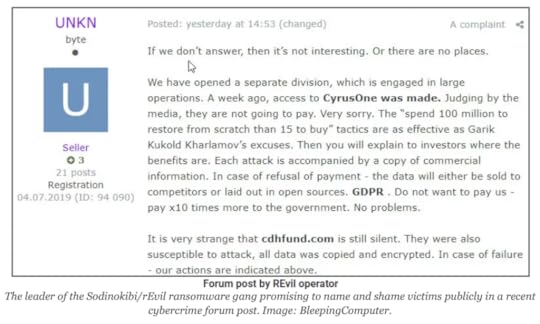
A threat to release data. Image from BrianKrebs.com.
These attacks don’t seem to be slowing down, and the attackers keep getting better at them. They’re improving their tools, they’re improving their business models, and they’re constantly evolving their techniques for getting companies to pay using social engineering.
The question is—how fast are our schools and hospitals and local governments improving our defenses to stay ahead of the attackers on all these fronts?
Nowhere near fast enough. That’s my answer.
Even medium and large businesses struggle to handle this threat, and that’s with dedicated security staff to help them. The small businesses, government orgs, and other entities that lack security talent and budgets are hopelessly outgunned.
If enterprises that spend millions on cybersecurity struggle with this, what hope is there for local governments?
I think the attackers are just now hitting their stride. I think they’re going to get more deadly, more efficient, and smarter about who to target at what times.
Schools have had to shut down over this. Hospitals. City governments and businesses. And as far as I can tell there’s no end in view here. We don’t have enough security people to cover the surface area, even if these targets had the budget to hire them.
We can stop waiting for Cyber Pearl Harbor. It’s here already, and we’re living it.
Notes
I think what’s going to happen before too long is the federal government will tap the endpoint vendors on the should and say: “Hey, the country needs you. Here’s several hundred million dollars: you now need to get Crowdstrike, Sentinel One, etc., installed on every school and government computer in the country. Go.”
I’d put BEC in the same conversation, but not the same sentence.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Cyber Pearl Harbor Finally Happened, and it’s Ransomware

Since 2007 the InfoSec industry has been talking about TheBigOne™—the event that would change cyber threats from annoyances to existential concerns.
They called it Cyber Pearl Harbor.
This doesn’t mean it can’t still happen.
The idea was that it’d be some massive blast that would take out the country’s power grid, or disable the entire internet, along with what they used to call e-commerce. That moment hasn’t happened (yet), but I think we’ve become the frog in the boiling cyber-water.
Ransomware is the Cyber Pearl Harbor we’ve been waiting for all along. It just looks different. Rather than being the one big blast, it’s more of a steady bombardment.
Ransomware is the new PCI.
— ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ (@DanielMiessler) September 19, 2020
1. It’s annoying
2. It’s not nearly the whole story
3. It’s forcing a lot of organizations to take security seriously
No catalyst for change compares to real-world consequences.
Business disruption is the ultimate argument.
Some stats:
At the time of this writing, Google News returns 7,460,000 results for the term Ransomware. More
SafetyDetectives reports the average cost of a ransomware-caused downtime incident has risen from $46,800 in 2018, to $141,000 in 2019, to $283,800 in 2020. More
The UHS hospital network, which is a Fortune 500 company with over 400 hospitals, has had multiple hospitals affected which required them to redirect patients to other options. More
According to Datto, Ransomware attacks are costing businesses more than $75 billion a year. More
Ransomware groups simply evolve too fast for small school districts with no IT staff.
She tried to reroute to another hospital and didn’t make it.
A woman recently died in Germany after she couldn’t receive critical care at her local hospital due to an attack. More
A ransomware attack against the New Orleans city government in early 2020 cost the city over $7 million dollars. More
New York City’s capital was hit with a ransomware attack in 2019 that took several key services offline. More
IBM says 1 in 4 of attacks its X-Force Team sees is caused by Ransomware. More
Ransom demands are increasing exponentially. In some cases, IBM Security X-Force is seeing ransom demands of more than $40 million. More
The skill and preparation asymmetry between attacker and defender is drastic.

My rough scribble of how ransomware sophistication surpassed our defensive capabilities somewhere around 2018
I think the only reason we survived this long without serious disruption to business—like we’re seeing now—is because attackers didn’t have their acts together. Their tooling wasn’t nearly as good as it is now, and they hadn’t linked their tooling with the business models.
Today there are multiple routes to make money from an insecure business. Once they get in—via RDP or Phishing or Drive-bys—they are not only extorting people who want to get their data back.

Google Trends Data for the term Cyber Peal Harbor
As a security person I sometimes have to admire their creativity.
Many groups have come to realize that some companies have good backups, so they start by stealing a copy of the data for themselves at the beginning of the attack. Then if someone doesn’t want to pay they can threaten to release the data and create a public incident.

A threat to release data. Image from BrianKrebs.com.
These attacks don’t seem to be slowing down, and the attackers keep getting better at them. They’re improving their tools, they’re improving their business models, and they’re constantly evolving their techniques for getting companies to pay using social engineering.
The question is—how fast are our schools and hospitals and local governments improving our defenses to stay ahead of the attackers on all these fronts?
Nowhere near fast enough. That’s my answer.
Even medium and large businesses struggle to handle this threat, and that’s with dedicated security staff to help them. The small businesses, government orgs, and other entities that lack security talent and budgets are hopelessly outgunned.
If enterprises that spend millions on cybersecurity struggle with this, what hope is there for local governments?
I think the attackers are just now hitting their stride. I think they’re going to get more deadly, more efficient, and smarter about who to target at what times. As far as I can tell there’s no end in view here. We don’t have enough security people to cover the surface area, even if these targets had the budget to hire them.
We can stop waiting for Cyber Pearl Harbor. It’s here already, and we’re living it.
Notes
I think what’s going to happen before too long is the federal government will tap the endpoint vendors on the should and say: “Hey, the country needs you. Here’s several hundred million dollars: you now need to get Crowdstrike, Sentinel One, etc., installed on every school and government computer in the country. Go.”
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


September 28, 2020
News & Analysis | No. 248

Welcome to the member area of the site. This is where you can see all the member-only content in one place.
or…
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


You Can Subscribe to Newsletters in Feedly
I think RSS is spectacular, and Feedly is my client of choice. But lately, newsletters have become the big thing. It really is a case of the old becoming new, with people leaving the internet and going back to email.
Weird.
Anyway, I love the newsletter trend for the content, but I don’t like the email medium. I want all my content in my RSS reader, and luckily Feedly can handle it.
All you do is click the plus icon on the far left of Feedly (to add content), and type in the name or the URL of the Substack or other newsletter you are interested in, and the suggestion pops up just like a regular website.
They even have an option for subscribing to pure email newsletters by subscribing to that newsletter with a Feedly address. You just create a new, custom address, subscribe to the newsletter using that address, and then all your new newsletters will show up in Feedly!
Anyway, hope this helps someone who’s trying to benefit from newsletters while keeping an RSS-centered life.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


September 27, 2020
Everyday Threat Modeling

Threat modeling is a superpower. When done correctly it gives you the ability to adjust your defensive behaviors based on what you’re facing in real-world scenarios. And not just for applications, or networks, or a business—but for life.
The Difference Between Threats and Risks
This type of threat modeling is a life skill, not just a technical skill. It’s a way to make decisions when facing multiple stressful options—a universal tool for evaluating how you should respond to danger.
Threat Modeling is a way to think about any type of danger in an organized way.
The problem we have as humans is that opportunity is usually coupled with risk, so the question is one of which opportunities should you take and which should you pass on. And If you want to take a certain risk, which controls should you put in place to keep the risk at an acceptable level?
Most people are bad at responding to slow-effect danger because they don’t properly weigh the likelihood of the bad scenarios they’re facing. They’re too willing to put KGB poisoning and neighborhood-kid-theft in the same realm of likelihood. This grouping is likely to increase your stress level to astronomical levels as you imagine all the different things that could go wrong, which can lead to unwise defensive choices.
To see what I mean, let’s look at some common security questions.
This has nothing to do with politics.
Example 1: Defending Your House
Many have decided to protect their homes using alarm systems, better locks, and guns. Nothing wrong with that necessarily, but the question is how much? When do you stop? For someone who’s not thinking according to Everyday Threat Modeling, there is potential to get real extreme real fast.
Let’s say you live in a nice suburban neighborhood in North Austin. The crime rate is extremely low, and nobody can remember the last time a home was broken into.
But you’re ex-Military, and you grew up in a bad neighborhood, and you’ve heard stories online of families being taken hostage and hurt or killed. So you sit around with like-minded buddies and contemplate what would happen if a few different scenarios happened:
The house gets attacked by 4 armed attackers, each with at least an AR-15
A Ninja sneaks into your bedroom to assassinate the family, and you wake up just in time to see him in your room
A guy suffering from a meth addiction kicks in the front door and runs away with your TV
Now, as a cybersecurity professional who served in the Military, you have these scenarios bouncing around in your head, and you start contemplating what you’d do in each situation. And how you can be prepared.
Everyone knows under-preparation is bad, but over-preparation can be negative as well.
Well, looks like you might want a hidden knife under each table. At least one hidden gun in each room. Krav Maga training for all your kids starting at 10-years-old. And two modified AR-15’s in the bedroom—one for you and one for your wife.
Every control has a cost, and it’s not always financial.
But then you need to buy the cameras. And go to additional CQB courses for room to room combat. And you spend countless hours with your family drilling how to do room-to-room combat with an armed assailant. Also, you’ve been preparing like this for years, and you’ve spent 187K on this so far, which could have gone towards college.
Now. It’s not that it’s bad to be prepared. And if this stuff was all free, and safe, there would be fewer reasons not to do it. The question isn’t whether it’s a good idea. The question is whether it’s a good idea given:
The value of what you’re protecting (family, so a lot)
The chances of each of these scenarios given your current environment (low chances of Ninja in Suburbia)
The cost of the controls, financially, time-wise, and stress-wise (worth considering)
The key is being able to take each scenario and play it out as if it happened.
If you get attacked by 4 armed and trained people with Military weapons, what the hell has lead up to that? And should you not just move to somewhere safer? Or maybe work to make whoever hates you that much, hate you less? And are you and your wife really going to hold them off with your two weapons along with the kids in their pajamas?
Think about how irresponsible you’d feel if that thing happened, and perhaps stress less about it if it would be considered a freak event.
That and the Ninja in your bedroom are not realistic scenarios. Yes, they could happen, but would people really look down on you for being killed by a Ninja in your sleep. They’re Ninjas.
Think about it another way: what if Russian Mafia decided to kidnap your 4th grader while she was walking home from school. They showed up with a van full of commandos and snatched her off the street for ransom (whatever).
Would you feel bad that you didn’t make your child’s school route resistant to Russian Special Forces? You’d probably feel like that emotionally, of course, but it wouldn’t be logical.
Maybe your kids are allergic to bee stings and you just don’t know yet.
Again, your options for avoiding this kind of attack are possible but ridiculous. You could home-school out of fear of Special Forces attacking kids while walking home. You could move to a compound with guard towers and tripwires, and have your kids walk around in beekeeper protection while wearing a gas mask.
Being in a constant state of worry has its own cost.
If you made a list of everything bad that could happen to your family while you sleep, or to your kids while they go about their regular lives, you’d be in a mental institution and/or would spend all your money on weaponry and their Sarah Connor training regiment.
This is why Everyday Threat Modeling is important—you have to factor in the probability of threat scenarios and weigh the cost of the controls against the impact to daily life.
Example 2: Using a VPN
A lot of people are confused about VPNs. They think it’s giving them security that it isn’t because they haven’t properly understood the tech and haven’t considered the attack scenarios.
If you log in at the end website you’ve identified yourself to them, regardless of VPN.
VPNs encrypt the traffic between you and some endpoint on the internet, which is where your VPN is based. From there, your traffic then travels without the VPN to its ultimate destination. And then—and this is the part that a lot of people miss—it then lands in some application, like a website. At that point you start clicking and browsing and doing whatever you do, and all those events could be logged or tracked by that entity or anyone who has access to their systems.
It is not some stealth technology that makes you invisible online, because if invisible people type on a keyboard the letters still show up on the screen.
Now, let’s look at who we’re defending against if you use a VPN.
Your ISP. If your VPN includes all DNS requests and traffic then you could be hiding significantly from your ISP. This is true. They’d still see traffic amounts, and there are some technologies that allow people to infer the contents of encrypted connections, but in general this is a good control if you’re worried about your ISP.
The Government. If the government investigates you by only looking at your ISP, and you’ve been using your VPN 24-7, you’ll be in decent shape because it’ll just be encrypted traffic to a VPN provider. But now they’ll know that whatever you were doing was sensitive enough to use a VPN at all times. So, probably not a win. Besides, they’ll likely be looking at the places you’re actually visiting as well (the sites you’re going to on the VPN), and like I talked about above, that’s when your cloaking device is useless. You have to de-cloak to fire, basically.
Super Hackers Trying to Hack You. First, I don’t know who these super hackers are, or why they’re trying ot hack you. But if it’s a state-level hacking group (or similar elite level), and you are targeted, you’re going to get hacked unless you stop using the internet and email. It’s that simple. There are too many vulnerabilities in all systems, and these teams are too good, for you to be able to resist for long. You will eventually be hacked via phishing, social engineering, poisoning a site you already frequent, or some other technique. Focus instead on not being targeted.
Script Kiddies. If you are just trying to avoid general hacker-types trying to hack you, well, I don’t even know what that means. Again, the main advantage you get from a VPN is obscuring your traffic from your ISP. So unless this script kiddie had access to your ISP and nothing else, this doesn’t make a ton of sense.
Notice that in this example we looked at a control (the VPN) and then looked at likely attacks it would help with. This is the opposite of looking at the attacks (like in the house scenario) and then thinking about controls. Using Everyday Threat Modeling includes being able to do both.
Example 3: Using Smart Speakers in the House
This one is huge for a lot of people, and it shows the mistake I talked about when introducing the problem. Basically, many are imagining movie-plot scenarios when making the decision to use Alexa or not.
Let’s go through the negative scenarios:
Amazon gets hacked with all your data released
Amazon gets hacked with very little data stolen
A hacker taps into your Alexa and can listen to everything
A hacker uses Alexa to do something from outside your house, like open the garage
Someone inside the house buys something they shouldn’t

A quick threat model on using Alexa smart speakers (click for spreadsheet)
If you click on the spreadsheet above you can open it in Google Sheets to see the math. It’s not that complex. The only real nuance is that Impact is measured on a scale of 1-1000 instead of 1-100. The real challenge here is not the math. The challenges are:
Experts can argue on exact settings for all of these, but that doesn’t matter much.
Assigning the value of the feature
Determining the scenarios
Properly assigning probability to the scenarios
The first one is critical. You have to know how much risk you’re willing to tolerate based on how useful that thing is to you, your family, your career, your life. The second one requires a bit of a hacker/creative mind. And the third one requires that you understand the industry and the technology to some degree.
But the absolute most important thing here is not the exact ratings you give—it’s the fact that you’re thinking about this stuff in an organized way!
The Everyday Threat Modeling Methodology
Other versions of the methodology start with controls and go from there.
So, as you can see from the spreadsheet, here’s the methodology I recommend using for Everyday Threat Modeling when you’re asking the question:
Should I use this thing?
Out of 1-100, determine how much value or pleasure you get from the item/feature. That’s your Value.
Make a list of negative/attack scenarios that might make you not want to use it.
Determine how bad it would be if each one of those happened, from 1-1000. That’s your Impact.
Determine the chances of that realistically happening over the next, say, 10 years, as a percent chance. That’s your Likelihood.
Multiply the Impact by the Likelihood for each scenario. That’s your Risk.
Add up all your Risk scores. That’s your Total Risk.
Subtract your Total Risk from your Value. If that number is positive, you are good to go. If that number is negative, it might be too risky to use based on your risk tolerance and the value of the feature.
Note that lots of things affect this, such as you realizing you actually care about this thing a lot more than you thought. Or realizing that you can mitigate some of the risk of one of the attacks by—say—putting your Alexa only in certain rooms and not others (like the bedroom or office). Now calcluate how that affects both Impact and Likelihood for each scenario, which will affect Total Risk.
Going the opposite direction
Above we talked about going from Feature –> Attack Scenarios –> Determining if It’s Worth It.
But there’s another version of this where you start with a control question, such as:
What’s more secure, typing a password into my phone, using my fingerprint, or using facial recognition?
Here we’re not deciding whether or not to use a phone. Yes, we’re going to use one. Instead we’re figuring out what type of security is best. And that—just like above—requires us to think clearly about the scenarios we’re facing.
So let’s look at some attacks against your phone:
A Russian Spetztaz Ninja wants to gain access to your unlocked phone
Your 7-year old niece wants to play games on your work phone
Your boyfriend wants to spy on your DMs with other people
Someone in Starbucks is shoulder surfing and being nosy
You accidentally leave your phone in a public place
We won’t go through all the math on this, but the Russian Ninja scenario is really bad. And really unlikely. They’re more likely to steal you and the phone, and quickly find a way to make you unlock it for them. So your security measure isn’t going to help there.
For your niece, kids are super smart about watching you type your password, so she might be able to get into it easily just by watching you do it a couple of times. Same with someone shoulder surfing at Starbucks, but you have to ask yourself who’s going to risk stealing your phone and logging into it at Starbucks. Is this a stalker? A criminal? What type? You have to factor in all those probabilities.
First question, why are you with them?
If your significant other wants to spy on your DMs, well they most definitely have had an opportunity to shoulder surf a passcode. But could they also use your finger while you slept? Maybe face recognition could be the best because it’d be obvious to you?
For all of these, you want to assign values based on how often you’re in those situations. How often you’re in Starbucks, how often you have kids around, how stalkerish your soon-to-be-ex is. Etc.
Once again, the point is to think about this in an organized way, rather than as a mashup of scenarios with no probabilities assigned that you can’t keep straight in your head. Logic vs. emotion.
It’s a way of thinking about danger.
Other examples
Here are a few other examples that you might come across.
Should I put my address on my public website?
How bad is it to be a public figure (blog/YouTube) in 2020?
Do I really need to shred this bill when I throw it away?
Don’t ever think you’ve captured all the scenarios, or that you have a perfect model.
In each of these, and the hundreds of other similar scenarios, go through the methodology. Even if you don’t get to something perfect or precise, you will at least get some clarity in what the problem is and how to think about it.
Summary
Threat Modeling is about more than technical defenses—it’s a way of thinking about risk.
The main mistake people make when considering long-term danger is letting different bad outcomes produce confusion and anxiety.
When you think about defense, start with thinking about what you’re defending, and how valuable it is.
Then capture the exact scenarios you’re worried about, along with how bad it would be if they happened, and what you think the chances are of them happening.
You can then think about additional controls as modifiers to the Impact or Probability ratings within each scenario.
Know that your calculation will never be final; it changes based on your own preferences and the world around you.
The primary benefit of Everyday Threat Modeling is having a semi-formal way of thinking about danger.
Don’t worry about the specifics of your methodology; as long as you capture feature value, scenarios, and impact/probability…you’re on the right path. It’s the exercise that’s valuable.
Notes
I know Threat Modeling is a religion with many denominations. The version of threat modeling I am discussing here is a general approach that can be used for anything from whether to move out of the country due to a failing government, or what appsec controls to use on a web application.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


September 23, 2020
Why I Like TikTok So Much
I get that I’m a security guy, and thus am not supposed to like China stealing the personality traits of tens of millions of people through the use of a virally popular mobile app—especially mine. I get that.
Yes, I did a threat model of my own usage.
But I really like TikTok, and I want to talk about why.
First, I think I like it more because of COVID. How much I don’t know, but ultimately the reason I like the app is that it provides highly-creative short-form positivity. It’s like a massive cannon that shoots positivity.
That’s for my feed, of course—which is based on a whole lot of ML training. Other people’s feeds might be angry, or sad. But mine is full of amazing. Stuff like:
Dance moves & dance-offs
Proposals
Military Homecomings
Beat Boxing
DJing
Lip-synching
Cute Pets
Skateboarding
Great Dads Being Presented Adoption Papers
Happy Couple Pranks
If you’re a TikTok user you know exactly what I’m talking about. If you’re not, you should check it out.
This app—as I have it trained—is a phenomenal cure for the 2020’s.
It’s a marvel at multiple levels—culturally and technically. Culturally it’s taken off like nothing I can remember. This thing is big. Of course as tech permeates society every new big thing will get bigger, so that’s part of it. But still. This thing is massive.
Technologically and design-wise, just wow. This thing is unbelievably brilliant. For one, the way they’ve integrated music clips is pure genius. They’ve created this ecosystem where certain clips of songs become universally understood soundtracks to certain types of sweet and happy scenes, like reunions and proposals.
And the way different personalities can come through is quite powerful. People can produce a certain feel in their content, much like hanging out with someone in person. And that’s probably another COVID-related appeal.
But the main feature is how good the algorithm is at finding you new content. You can open the app and suddenly wake up hours later with a stomach ache and the sun in a vastly different position.
It’s that good.
So, downsides.
Well there is the fact that it’s a brain personality scanner for an entire generation of youth, powered by a Chinese company government who’s probably using it for this project. So that’s bad.
The other downsides are more common to any app that basically becomes a teenager’s life. I don’t have kids but I’m sure there are plenty of parents struggling with that right now. But to be fair, it’s hard time for parents and teenagers right now regardless.
Anyway, that’s it for now. I just wanted to admonish anyone who’s got a decently high Openness rating to experiment with this thing. If you’re paranoid about security, use a burner phone run through a VPN that links to Tor through a foreign nation. And fake all your clicks.
Nah, don’t do that. Maybe use a different phone and a non-identifying account if you’re seriously worried. I don’t have a tied identity and I don’t communicate with anyone on it, so I’m not concerned.
Again, know your threat model. Don’t use it if you’re a working spy with strange fetishes. Unless you’re a CI agent looking to write a book later.
Summary
TikTok is a cultural and technical phenomenon.
If you’re a curious person who cares about what humans are doing, you owe it to yourself to dabble a bit.
The app is most likely harvesting immutable things from your personality and giving them to the Chinese military, so if you’re not into that maybe don’t. Just kidding, it should be fine. Probably.
For an individual the actual risk is that you reveal something as a user, or your kids do, that can be used against them in a year or fifty from now. Like 23andMe data being turned into a biological weapon that can only target people like you, or you specifically, it’s technically possible in the future, but it shouldn’t stop you from being 37% more happy during COVID. That’s my risk analysis, not yours. YMMV.
Bottom line, you should try to find a way to check it out—safely—based on your risk tolerance.
There really is a there there.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


September 21, 2020
News & Analysis | No. 247
SSH Port Obscurity, The TikTok Deal, Ransomware Death, Chinese Espionage CRM, Amazon Bribery, Instant Domain Admin, Technology News, Human News, Ideas Trends & Analysis, Discovery, Recommendations, and the Weekly Aphorism…

Security, technology, and society…
I spend 5-20 hours a week consuming books, articles, and podcasts, and every Monday morning I send out the best of what I found.
MY ESSAYS
No, Moving Your SSH Port Isn’t Security by Obscurity More
I’ve Been Too Sloppy in the Past More
SECURITY NEWS
A TikTok deal has evidently been approved in the US, with the contract going to Oracle and Walmart right before the app was set to be banned. The contract supposedly includes the standing up of a new company called TikTok Global, which both companies will have a combined 20% share of. The deal includes both US hosting and access to TikTok’s source code, but given how fast this happened, and how close to the deadline, I expect a lot to change in the next few days. More
A (likely-Maze-based) ransomware attack on a hospital in Germany has lead to the death of woman. She tried to get immediate help at a hospital that was currently disabled due to ransomware, and she had to go to another hospital about an hour away. She never made it. More
An anti-China activist leaked a Chinese database full of personal data from tens of thousands of VIPs from around the world. The total list was around 2.4 million people, which included politicians, royalty, etc. The database was created by a Chinese company called Zhenhua Data, and seems to be exactly what I wrote about here, where I postulated that China is probably building a massive Leverage CRM for the future. Basically, gather as much information as you can, about everyone, including kids, so that you can use that data as leverage years or decades in the future. More
Six people selling products on Amazon have been indicted for bribing Amazon employees to help them gain an unfair advantage. This included bribing them to do things like reinstate their banned accounts, or banning rival accounts. They were able to earn one-hundred million dollars using these techniques. More
Congress has passed a bipartisan IoT Security Bill that will require (if it becomes law) that all devices acquired by Federal agencies comply with a new set of NIST security standards for IoT. More
Credit card fraud has risen 104% in the last quarter according to the FTC. More
Vulnerabilities:
There’s a wicked vulnerability in Microsoft Netlogon (445 TCP or a Random RPC port) that gives an attacker instant Domain Admin. Patch immediately. More
There’s a vulnerability in Bluetooth affecting billions of devices. More
The ZDI September Security Update Review More
Ransomware:
Ransomware lead to the death of a woman in Germany because she needed immediate help and had to go to a further hospital and never made it. More
APT:
The US has imposed sanctions on an Iran-based APT39, which is known for targeting dissidents, journalists as well as global enterprises. More
TECHNOLOGY NEWS
Anime avatars are getting big on Twitch and YouTube. It’s where you’re basically looking at a video stream of a cartoon character, but it’s being controlled by a real person, in real-time. The technology is just now getting really good, but I think this is going to open the doors for millions more streamers who didn’t want to stream live because of their voice or their appearance. They will be able to emote as themselves, or as a character, and have people see them as they wish they were. More
Amazon is hiring another 100,000 employees in the US and Canada. More
It looks like Zoom might be coming after Slack with new messaging features. More
Facebook is introducing a new feature where you can watch videos together, called Watch Together. More
Elon Musk has almost completed his tunnel under Las Vegas that will transport self-driving cars. More
Starting on October 1st, all new repos on Github will be called “main” instead of “master”. More
The X-1 credit card gives you a limit based on your income, not your credit. More
Companies:
Snowflake just had the largest software IPO in history, at $3.4 billion dollars. More
Affirm just raised a $500 million dollar series G to help their ‘buy now pay later’ business. More
Tonal has raised another $110 million to continue doing connected home fitness. More
Observe.ai has raised $54 million to analyze call center conversations. More
RapidAI has raised $25 million to analyze medical scans using AI. More
SOCIETY NEWS
Another doctor and a fairly large study has found that Vitamin D can significantly help against Coronavirus. As I’ve said before here, I think the science is still early on COVID, but it looks like getting your D-levels to the high-normal range is probably a really good idea. Again, normal ranges. Don’t go crazy with it. The problem seems to be a deficiency in D, not a need for super-high levels. More
Spiking gun sales are overwhelming our background check infrastructure. More
Israel is doing another lockdown because their cases are spiking. More
The study of Ancient DNA (it’s a whole field now) has revealed that Vikings weren’t all Scandanavians with blonde hair. There was significant mixing with groups from Asia and Southern Europe. More
Scientists figured out how to create a disassociation, Ketamine-like effect using brain waves instead of drugs. More
IDEAS, TRENDS, & ANALYSIS
Ransomware is the New PCI, and both seem more effective than anything else we’ve tried at getting people to take security seriously. More
UPDATES
My friend John Japuntich just released his new novel, ATROPOS, on Amazon, and it’s currently sitting at #44 in new hard Sci-fi!. I’m going to read it first, and if it’s great I might recommend it for our book club. More
I’ve been doing a bunch of work on the site lately, basically making it look more like a modern website and less like a blog. Whatever that means.
DISCOVERY
The Ultimate Guide to FFUF, by my friend Codingo. More
Generative Bad Handwriting More
A brilliant and hilarious walkthrough of someone finding Tony Abbott’s passport number using a discarded airplane ticket. More
How to send files using nothing but SSH, Tee, and Base64 More
How the Air Quality Index Works More
I am loving these one-liner bug-bounty tips on Twitter. More
Mental Models More
Marc Andreessen on Productivity, Scheduling, Reading Habits, Work, and More More
Hash.ai — Build multi-agent simulations in minutes. More
Darkshot — A multi-threaded screenshot scraper. More
Onefuzz — A self-hosted Fuzzing-as-a-Service Platform More
RECOMMENDATIONS
You should watch—and get your loved ones to watch—The Social Dilemma. It’s a documentary about how social media is attacking our mental health and our democracy. Extremely well done. More
APHORISMS
“Simplicity is the extreme degree of sophistication.”
~ Leonardo da Vinci
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


No, Moving Your SSH Port Isn’t Security by Obscurity

I just came across another post on Hacker News talking about why you shouldn’t move your SSH port off of 22 because it’s Security by Obscurity.
There are some good reasons not to move SSH ports in certain environments, such as usability.
People absolutely love to invoke the “Security by Obscurity” boogeyman, and it makes them feel super smart when they do. It’s a conversation ender.
Oh man, that’s nothing but Security by Obscurity… (Ryu Fireball)
(The victim covers their face, packs, and leaves town)
It’s true that Security by Obscurity is bad; the problem is many people have no idea when it applies. Including most of the people being loudest about it. Let me tell you the secret to this debate that will permanently solve it for you.
Security by Obscurity is when you hide how a security measure works, not when you keep some part of it a secret.
Let me repeat that a few different ways, with examples.
Certain types of security controls (like encryption) have two components: the mechanism, and the key. In encryption, the mechanism is the algorithm, and the key is, well…the key.
The question is whether you’re hiding the mechanism or the key.
If you hide how the algorithm works, you’re using Security by Obscurity. And that’s bad. We all agree there. But how about these examples?
These are all well-known by attacker and defender.
Frequency hopping on a radio system to avoid eavesdropping
A dead-drop mechanism used by spies to exchange notes and packages
The use of camouflage on tanks and planes in war
The use of decoy limos for heads of state in dangerous areas
Here we have something that’s clearly being hidden. We’re hiding the frequency we’re using. We’re hiding the location of the dead-drop. We’re hiding the location of the tank in the desert by making it look like sand. And we’re hiding which limo the President is actually in so it’ll be harder to attack him.
Is that Obscurity?
No. It’s not. And here’s why. Nobody is hiding the mechanism.
Even if your enemy knows you’re camouflaged somewhere in the dessert all their work is still ahead of them.
Everyone knows what’s going on. Everyone knows that the tank is somewhere in the desert, they just can’t see it to shoot it. Everyone knows the President is in one of those three helicopters, but it’s way more dangerous and expensive to guess which one and fire. And with the dead-drop, you know the package is somewhere in Central Park, but you don’t know where.
Increasing attacker effort is invaluable.
Importantly, it’s very expensive to take the time to check all the places the target could be. For a package. For a President. For a camouflaged tank.
And yes—for an SSH port.
It’s fine that people know you changed your SSH port. But now they have to scan all the ports and find the new one. Sure, that’s not too difficult, but many people are actually going to do that? Not many, because it’s costly in terms of time and effort.
I did an experiment one weekend and got ~10,000 probes on port 22 and 4 on some random high port.
In short, you just made it harder for the enemy to successfully attack you by giving them a resource problem. Sure, they can check under every rock in Central Park and eventually find the package, but you’ll be done with the mission by then.
Obscurity doesn’t apply if people know the mechanism you’re using and they simply have a resource problem. Having a known defense but a hidden key is a well-established part of good security, and it has been for millennia.
Summary
Yes, Security by Obscurity is bad.
But most people don’t know what it actually is.
It’s where you keep the mechanism secret, not the key.
As long as you have a good key, it’s ok for people to know the mechanism.
Don’t let people term-shame you who don’t grasp the underlying concepts.
Notes
Changing an SSH port is a lot like a dead-drop or camouflage. It’s not good security by itself. The tank still needs armor. The message should still be encrypted. But it’s a layer.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


September 20, 2020
Subscribe Complete
Annual $59.00/year
Monthly $120.00/year
None
6 Months Free
Weekly Newsletter
Slack Community Access
Book Club Access
Newsletter Archives
Essays, Tutorials, Podcasts
Bi-weekly newsletter
Subscribe
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Subscribe

I spend 5-20 hours a week consuming books, articles, and podcasts, and every Monday morning I send out the best of what I found.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers





