Daniel Miessler's Blog, page 61
October 20, 2020
Retroactive Mindfulness

Is it possible to rescue mindfulness from the past?
One of the most interesting lessons I’ve ever had in mindfulness came from Sam Harris in his Waking Up app.
He made the argument that it’s not actually time that gives you life, because if you live 90 years on the planet but never pay attention, it’ll be as if you only lived a very short time. Alternatively, you could pay attention closely, only live for 30 years, and your life could feel very full.
He argues that attention is the currency of life quality—not time.
To that end, he warns people not to just drift through life, lest they waste their lives essentially sleeping.
That waste part is what’s interesting to me. For those who didn’t pay enough attention early in their lives, is it possible to get any of that back?
I wonder if we can replay our past as memories, and attempt to be mindful of both the stimuli and the sensations they caused.
As observers. Not judges. Not victims. Not victors. Not someone enjoying fond or bitter memories. But as someone being present for the moment this time—as we weren’t the first time.
I think there are problems with the idea. First off, raw sensations aren’t fully recorded—or at least it’s not easy to retrieve them if they were recorded. So we won’t be experiencing the entire raw situation when we invoke a memory. We’re instead experiencing only very specific parts of the experience, and of course how they made us feel.
So it won’t be full-bandwidth. It’ll be lossy, compressed, and likely altered by our multiple recollections of the memory in the past.
But I can’t shake the idea that we could spend considerable effort, perhaps with a sherpa, to attempt to experience as much as possible, even if your creative subconscious has to construct some of the details, in order to be in the present—in the past.
If you have spent a quarter or half of your life not paying attention, would you like to get some of that time back?
If attention is the real measure of meaningful time, I think it might be possible to do do just that.
We can navigate our memories, in as pure a form as possible, and just be there. Experience them. Be present. Accept what happens without becoming the event. Just observing it and letting it pass—like we would today with the present.
Retroactive Mindfulness. A way to harvest meaning from our past.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 19, 2020
News & Analysis | No. 251
I spend my time reading 3-6 books a month on security, technology, and society—and thinking about what might be coming next. Every Monday I send out a list of the best content I’ve found in the last week to around 40,000 people. It’ll save you tons of time.
MY ESSAYS
The Content Value Hierarchy (CVH) — How to protect your podcast or newsletter from being cut when people hit content overload More
The Relationship Between Hardship, Struggle, and Meaning More
A CrowdSec Primer — A modern replacement for Fail2Ban More
SECURITY NEWS
Multiple law enforcement groups are preparing for election-related unrest by limiting the ability to take time off in the weeks before and after the election. More
China is working on swarms of so-called “suicide drones”, which are relatively inexpensive and can be launched from mobile platforms including trucks and helicopters. More
Projecting objects, such as stop signs, cars, and other obstacles, can make Teslas see those object as real, causing them to swerve or apply the brakes. More
Sweden is growing its military spending by 40% due to tensions with Russia. More
Atlanta police used a drone to make an arrest in the murder investigation of Thomas Jefferson Byrd, and they released the video. More Video
Vulnerabilities:
CVE-2020-16898 — There’s an RCE in the Windows TCP/IP stack related to the handling of ICMPv6 Router Advertisements More
800,000 SonicWall VPNs are vulnerable to an RCE. More
There’s a bad NULL Pointer Dereference error in Flash. By the way, dereference just means “read”, i.e., trying to read something that isn’t there. More My Primer
Someone found an RCE in the desktop app for Discord. More
Multiple vulnerabilities have been found in Magento. More
Breaches:
Barnes & Noble warns customers of a breach that may have resulted in data loss. More
TECHNOLOGY NEWS
The 2021 Tesla Model 3’s are getting some major upgrades, including longer range, a bit more speed, and double-paned glass. More
You can now hum or sing songs to search for them using Google. More
Google Analytics is rolling out a new upgrade—Google Analytics 4—which is nicer looking, gives more data, and uses AI to provide insights—but as per Google the rollout doesn’t seem well-documented or complete. There’s supposed to be an “Upgrade to GA4” button in existing properties, but many are reporting it’s not there for them. More
Companies:
Clear, the company that helps air travelers get through line faster, looks to be pivoting into a larger identify verification play. More
98point6 raises $118M to do remote healthcare, including text-based interactions with doctors and automatic prescription sending to your local pharmacy. More Video
Balto raises $10 million to analyze call center conversations using AI. More
BlackSwan (who just raised $28 million) is an Israeli company that’s looking to enable any company to leverage AI for operational efficiency and data-driven decision making. More
Augury is a company that uses AI to predict machine faults based on vibration and sound, and they just raised another $55 million. Evidently they’re about to have competition from Amazon as well. More
Danon is a company that scans construction sites using AI and can tell you if they are behind schedule or if errors have been made. More
Alkira is a multi-cloud networking startup that helps people get their services onto multiple cloud services very quickly. More
HUMAN NEWS
China’s economy grew 4.9% in the third quarter of 2020. The surge is partly due to its lead at containing COVID. Construction and consumer spending are both up. Caveat: These are China-reported numbers. More More
China has rolled out pilot of its new, digital version of the Yuan in Shenzhen. It’s not a cryptocurrency, just a digital version of the official, state currency. More
Nearly 900,000 people applied for unemployment in the US last week. More
Amazon has launched a payday loan program for its warehouse workers. This seems gross. It’s like they’re creating both the supply and the demand for a new business that shouldn’t have to exist. More
California has a $54 billion dollar budget deficit and over 340,000 government employees drawing more than $100K in salary. That seems, well…unsustainable. More
Rents in San Francisco have crashed the most in the country: up to 31%. More
IDEAS, TRENDS, & ANALYSIS
How to Reverse 50 Years of Social Decline and Actually Make America Great More
I’m starting to worry, as are others, that there is a big COVID shoe that still needs to drop regarding COVID and the economy. There’s a very real chance that we’ve just sort of been going on fumes for the last few months, i.e., stimulus, strong tech performance, etc., but that at some point the millions of unemployed people and all the unpaid loans are going to have an impact. Then there’s the election of course. We could see some strange times in the next several months. Maybe things stabilize and a Biden presidency brings a big optimism push for years. Or maybe he gets elected and all the Trump-fueled distractions get reduced, and people realize there are actually problems with the economy. Or maybe Trump wins and the cocaine-fueled optimism continues (but for how long), or maybe his crazy optimism carries things through to a longer-term recovery. I don’t know, and nobody else does either. But the one thing to say is that it might not be a good bet to assume that the recovery will continue the way it has for the last few months, because it could be that the real impact of the bad economy simply hasn’t landed yet.
Is Maslow’s Hierarchy the Only Pyramid Scheme That Works? More
How Substack Became Milquetoast More
A Unified Theory for Coming Up With New Ideas More
UPDATES
As you probably noticed, I changed and shortened the intro to the podcast a bit, and I also trimmed the outro. David, who’s one of our original UL members, noticed that the outro was quite long and it prevented a quick transition into the next podcast. So I took that feedback and cut the intro/outro time by around 70% to make it easier to get into and out of UL content.
Just a reminder on product shoutouts, this show is very anti-ad, yet I am also very pro-product-discovery, and I’m trying to forge a new path that balances these two things. I’m still investigating ways to find and recommend more products on the site in the discovery section (if anyone knows a service I can use for that let me know!) Like I talked about here, my goal there is to bring extremely cool products to your attention that I find on Facebook, get recommended from friends, etc. One example is the RESOLUTE TOOLS everyday carry blade, which is actually the only knife I carry now. I’m also starting to reach out to some of those product companies that I find and want to recommend, to ask if they want to support the show. To date I’ve only found two products that have been 1) good enough to bring to your attention, 2) that I actually use, and 3) that I reached out to and asked to support the show. Those two products are Thinkst Canary Tokens, and now CrowdSec, which is in today’s show. I’ve recommended the RESOLUTE TOOLS blade multiple times but they’ve never been a show supporter, for example. More
I think I’ve been neglecting a certain type of writing on the site, which is essentially short-form ideas. In the past Google really hated seeing short posts, and in the past that mattered to me. But now I think 1) I care less, and 2) Google probably values people who post more often more than long posts. Either way, I’m looking to do more short essays on the site, and some of those I’ll also turn into short podcast episodes as well. The lesson here is to never impose limits on your own writing. If you have an idea, do it. Google—or whoever—will come around eventually.
DISCOVERY
CrowdSec — A Go-based, modern replacement for Fail2ban that leverages crowdsourcing to manage ban lists. I run this on all my public-facing servers, and I’m super happy to finally have a replacement for Fail2ban after all these years. If you run a web or SSH server, you should definitely check it out. Download My Tutorial My Metrics
I just ordered a new microphone arm from Gator Frameworks, which I recently saw on the Joe Rogan show and also saw my friend Phillip Wylie talk about as well. I currently have the one from Blue, which replaced my old one from Rode, and I’m hoping this will be even better since it’s Joe’s new preferred arm in his new Austin studio. I’ll let you know how much I like it. More
I’m trying a mechanical keyboard for the first time in over a decade, and I went with the Keychron K2 based on seeing it in an MKHD video. Not sure if it’ll stick or not. Very different from what I’ve been using. More
I went on Ashish Rajan’s Cloud Security Podcast this weekend and really enjoyed the conversation! Thanks to Ashish for having me on. Podcast Video
The Next World | Dark Techno / Cyberpunk / Dark Electro Playlist — A cyber-ish EDM playlist I love to hack/create to. More
How to Invent Everything — A new book that shows you how to invent everything if you get sent backward in time. More
An interesting set of metrics for gauging the health of your team. More
Lobsters’ Q4 Hiring Thread More
How to Read and Why — A new book recommended by a member the UL Slack channel. More
A collection of Tech Landscape maps. More
Among-sus — A text-based multiplayer version of Among Us. More
The Hedonometer — A project that takes a 10% sampling of the daily Twitter firehose, and does bag-of-words analysis on the English words it sees. It then maps that as an indication of happiness/pleasure in the world. More
JWT Heartbreaker — A Burp extension that finds weak secrets automatically. More
VulnHub — Prebuilt vulnerable environments built on Docker. More
RECOMMENDATIONS
How to Read and Why — A new book on reading that I am so excited to get to. Yes, I haven’t read it yet, so it’s a weird recommendation. But it’s a highly-rated book about why you should read, so I’m recommending it sight unread. More
APHORISMS
“To avoid criticism, do nothing, say nothing, be nothing.”
~ Elbert Hubbard
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 16, 2020
The Content Value Hierarchy (CVH)

The four tiers of content value hierarchy
It’s important for content creators—especially those in the newsletter and podcast spaces—to know what level of content they’re bringing to their audience.
I highly recommend Clint’s newsletter, TL;DR Sec.
In a recent conversation with a creator friend of mine, Clint Gibler, I came up with this 4-tier hierarchy. It breaks content into four levels:
Discovery: You’re just surfacing random, interesting stuff for your audience.
Curation: You’re being extremely conscientious about the quality of what you surface.
Analysis: You don’t show them content; you’re also telling them why it matters.
Vision: You’re creating original ideas that help them navigate the world.
The context of the conversation was him asking me what part of his most recent newsletter I liked most, and I responded by telling him it was this section.
Top tier newsletters are heavy in levels 3 and 4.

An analysis section of a TL;DR Sec newsletter
When he asked why, I told him it was because it was Analysis, which is the second-highest form of newsletter content—with Vision being the top.
This quoted piece doesn’t just tell us that exploits come out faster than CVEs: it tells us how many exploits, and how much faster, and what percentage were zero-days. That’s valuable!
People are going to start unsubscribing from newsletters that don’t have level 3 or level 4 content.
In my own newsletter, I make this distinction clear with clearly labeled sections—although I don’t have a “Vision” one because that sounds ridiculous.

The Unsupervised Learning Discovery Section
It’s natural to combine Levels 1 & 2 into a single section.
This is a Level 1 and 2 (heads-up this is interesting content!) section, and it’s aptly labeled “Discovery”.
In my IDEAS, TRENDS, & ANALYSIS section, I try to combine Level 3 and Level 4 content by both commenting on what’s happening right there in the section—with a paragraph of commentary—or by linking out to full essays of original content.

Analysis (and hopefully vision) in a single section of UL
Why this matters
I think this is already happening, actually.
You should know where your podcast or newsletter content fits in this hierarchy because as those mediums continue to go mainstream people are going to tire—or become overwhelmed by—too many shows that offer only the first two levels.
Even if you have decent discovery and curation, people only have so much time.
“Prediction is hard, especially about the future.”
My prediction is that people will drop most of their first and second-level content and hold onto content that hits levels three and four.
Summary
There has been a massive adoption trend around newsletters and podcasts, with people signing up for tons of them.
Content moves through a value progression of Discovery, Curation, Analysis, and Vision.
As people get overwhelmed with all the content they’ve signed up for, they’re likely to drop most of the newsletters and podcasts at the first and second levels.
The highest chance you have of remaining on someone’s list after they cut 90% of their subscriptions is to provide analysis of what’s going on, and/or vision around what might be coming.
Notes
There could be an exception to this rule for self-help oriented content, e.g., James Clear, where he basically tells you how to be a happier or better person in very short little snippets. I think that’s producing impact at a 3-4 level, but on a completely different axis.
Entertainment value is a magnifier of all four levels, so if you only do discovery but you’re super funny while you do it, you could still hold onto an audience that likes your lens for seeing the world.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 14, 2020
The Relationship Between Hardship, Struggle, and Meaning

I think the best thing to happen to America was a massive influx of people with The Immigrant Mentality™. A lot of people say immigrants are great—especially near San Francisco where I live—but they rarely complete the sentence with ane explanation.
I’m not an expert on immigration, so this is really just a thought exercise.
I’m sure there’s a literature on this with some formal designations, but based on what I’ve read and experienced there are a few key attributes of the immigrant mentality that I’ll try to capture here.
They are thankful to be in the receiving country, because they acknowledge that it’s offering something not found where they came from
They’re extremely hard workers, and assume that it’ll be hard to get jobs and are willing to compete for them by working even harder
They’re extremely resilient to hardship, and simply get back up when they get knocked down
They tend not to complain about how hard things are, usually because they’ve seen much harder situations where they came from
As we’ve gone through this pandemic I’ve been thinking a lot about mental toughness. Not just for people during this very strange 2020, because yeah—there’s a lot going on—but even before then, with Americans in general.
According to the American Psychological Association, the rate of individuals reporting symptoms consistent with major depression in the last 12 months (as of March 2019) increased 52 percent in adolescents from 2005 to 2017 (from 8.7 percent to 13.2 percent) and 63 percent in young adults age 18 to 25 from 2009 to 2017 (from 8.1 percent to 13.2 percent). And again, that’s before the pandemic.
This claim could benefit from research, of course.
I have known a lot of immigrants in my life, and while I know the plural of anecdotes is not data, I generally don’t see or hear of too many depressed immigrants. Sad immigrants? Yes. They’re often separated from their families and lonely. Overworked? Absolutely. Stressed? Absolutely. But those feelings—while negative—are not the same as depression.
My loose hypothesis is that people with the immigrant mentality are resistant to depression because hardship and drive function as a depression vaccine. I think this is why so many Americans are depressed: because they have not experienced hardship and therefore lack any drive.
We can see something like this by looking at the attainment levels of immigrants vs. their children and grandchildren.
This generational gap is covered extensively in many books, but I think this New Republic piece captures it well:
The longer immigrant children live in this country, the worse, on average, their health, their attitude, and their school performance. What’s more, with each subsequent generation, immigrant children do worse and worse.
On average, first-generation children function at significantly higher levels than do typical American-born children. But, by the third generation, that advantage is gone.
Why Do Immigrant Children Struggle More Than Their Parents Did?
I think people who have purpose, or drive, naturally produce meaning when they face adversity. Or perhaps meaning is the natural exhaust of drive colliding with adversity and low-level suffering.
And the flip side of that is that depression could be the exhaust of a lack of drive colliding with nearly limitless options.
I imagine a tiny trickle of water being weekly pushed down a 10-foot pipe, vs. a massive stream of water being forced at high pressure through a tiny nozzle. The first stream of water is barely noticable as a dribble, where the second can cut through metal.
So it’s not only the water pressure that propels the water at high speed: it’s also the clear and restricted path that it must take.
Immigrants are that high-pressure water nozzle. They know what they want—or need to achieve—which is usually a steady job, shelter, and the stability to safely start a family. That’s the pressure. That’s the drive. And the restricted nozzle is the fact that many immigrants have only one trade.
Perhaps they build things, or they cook, or they clean houses, or they know information technology. But it’s not as if they can open an art gallery and explore themselves. They have a trade and they are driven to get work doing that thing as quickly as possible.
60% of gun deaths in the US are from suicide.
The reasons so many people in America are upset, depressed, angry, and are overdosing on drugs are obviously numerous. It’s not like it’s one thing.
But I think a big part of it comes down to the lack of hardship, the lack of struggle, and the lack of appreciation for how easy it is to live in the US compared to most of the world.
Perhaps everyday meaning comes from something like this equation:
Hardship/Struggle (Produces-->)
Drive/Goals (Combines with-->)
Struggle/Adversity (Results in-->)
Meaning
In this model, hardship and struggle would come from serious things, like not having a place to live in your previous country, or having seen your parents go hungry so you can eat, or having experienced hunger yourself.
Drive and goals could be anything from a determination to never feel that hunger again, or to make sure your kids never experience it, to wanting to become a famous musician, or a lawyer.
Adversity is similar to hardship, except it’s the constant grind. It’s not the hardship you faced in the past that gave you your drive, but rather the opposing force that makes you have to push everyday to avoid being crushed.
US immigrants—especially from Mexico—have this. It’s neverending. Many of them had rough lives back home, and they’re here to better themselves and their families through hard work. They have the origin story that gave them the fire, and they have the daily and mandatory grind that keeps them afloat. This is why they can experience meaning in a good meal, a good beer, and spending time with friends.
I think many multi-generational Americans have simply had it too good for too long. It’s not their fault. And it’s not their parents’ fault. It’s hard to impose hardship on children when you went through it yourself. The inclination is to do the exact opposite. To shield them from that and make things easier for them.
Think about the slow water and the giant pipe again. That’s what so many American teens seem like to me today.
They’ve had an easy path their whole lives. They’ve never been cold. They’ve never been hungry. They’ve never felt deeply or consistently unsafe. They’ve never been denied education. They’ve had it good.
That produces the slow trickle of a small amount of water (drive).
Then, they’re told by everyone, and the media, that “they can be anything.” Oh, great. Thanks. So I have no interest in anything. No passion for anything. No idea what I should feel passionate about. And your wisdom is to tell me that my options are limitless?
For someone with no direction, being told they can go anywhere just makes it worse.
This is why so many Americans are struggling with a lack of meaning. It’s not the driven people who are grinding through long days and nights to get their masters degree so they can become an archaeologist—which they’ve always wanted to do—that are hurting. They’re sleep-deprived, and exhausted, and stressed about money, etc. But they’re not as likely to be depressed.
It’s the directionless that we need to worry about. Especially the ones with “lots of options”.
Far too many of them are unable to produce a steady flow of water at useful pressure level. Instead you end up with a giant, abandoned water pipe that’s a bit swampy to walk through.
People like that are open to anything that will get the water moving. Anything to either increase their passion and drive, or to focus it into a tight stream.
People like that are easy to control.
I think if we are to have any long-lasting civilization we must learn how to imbue our youth with the memory of hardship. We must teach kids—somehow—what it’s like to struggle so that they can develop their own drive and therefore their own potential for meaning.
If we don’t learn this lesson we will end up repeating massive cycles of:
War
A couple generations of great people who now appreciate life
2-3 generations of people increasingly taking the good life for granted
War
Enough already.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 13, 2020
Civil War Would Look Different This Time

A lot of people are talking about another American Civil War.
A number of white nationalist groups are even hoping for one, and the boogaloo movement is based completely around the idea.
Nobody obviously knows if that’ll happen, or what it would look like, but there’s a deeper problem with even defining it. What does it mean to have a Civil War in a country where people aren’t separated geographically?
I’m sure there are many examples we can look at throughout the world, where there are internal conflicts between peoples, and I’m curious where the line is between internal strife, internal violence, and civil war.
As a layperson on the topic my first inclination is that you’d need the warring factions to be separated from each other, and that’s what makes it seem strange in the US today.
There are some neighborhoods that are somewhat homogenous, obviously.
If the reason for the war is race, what are the sides? Crazy white people on one side and everyone else on the other? White people against Black people? The problem there, of course, is that there are white and Black people all over the place. They’re interspersed within states, cities, and even neighborhoods, so it’d be pretty difficult to group people on one “side” vs. another.
Or maybe the idea is not race but class. But that’s the same problem. Every state and most cities have rich and poorer areas, and the forming of sides once again seems like a logistical problem that would have difficulty reaching critical mass.
But perhaps the standard is just different now. Maybe it’s not a matter of clear sides, per say, but rather just the reaching X level of unrest over Y number of distinct areas.
Civil War can’t look the same this time because there aren’t clear sides separated by geography.
Throw in some anti-Government for good measure.
So whether it’s anti-white, anti-non-white, anti-rich, or anti-elite—it’s really all the same. It’s people deciding that they don’t like the current system, going outside and getting violent. And then when those various groups meet, then you get the clashes.
As we saw from the protests and riots earlier in 2020, it’s pretty easy to have confusion at a riot or protest. People aren’t exactly wearing color-coordinated team uniforms that are associated with mission statements.
I’ve witnessed—and even been in a couple of situations—where someone tries to break up a fight among people on the same side, and they suddenly get attacked by someone thinking they’re part of the other side, which spawns a violent response.
So, yeah, I think that’s really the standard at this point—basically a certain level of unrest, spread over a certain number of cities, that lasts a certain amount of time. Whether it’s 1%-based, or race-based—I’m not sure that matters as much.
There are lots of reasons people could erupt at this point. The real question is how widespread it is, how intense, and how long-lasting.
I think that’s what Civil War means at this stage of America’s lifespan.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 12, 2020
News & Analysis | No. 250
You’ve reached a piece of member-only content.
If you’re already a subscriber, please login here.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 9, 2020
A CrowdSec Primer: A Modern Replacement for Fail2Ban

If you’ve been around security for a while you’ve probably used—or are still using—Fail2Ban. It reminds me of Nikto or Netcat in a way in that it’ll always have a place of respect in my heart, but while Nikto and Netcat were supplanted in many ways by other tools, Fail2Ban still seems like the best tool out there for managing abusive users on services like SSH.
With CrowdSec that appears to be changing.
Introduction
CrowdSec is more than just a Fail2Ban replacement though, and makes it a bit confusing. It calls itself:
Their team reached out to me after I featured them on Unsupervised Learning.
An open-source and crowd-powered software enabling you to detect & block attacks.
…which is definite in the Fail2Ban space, but when I had a call with their team they were thinking much bigger than that. Here are some of their described features:
From their site…
allows you to detect attacks and respond at all required levels (detect where your logs are, block at CDN or application level)
is easy to install and maintain with no technical requirement. The installer even comes with a wizard duh!
is designed to be integrated with other solutions and components (ie. use CrowdSec to read your mod_security logs and automatically block attackers at your CDN level)
is about sharing : meta-data about the attack/attacker you detect is sent to a central API, and malevolent IPs are shared with all users.
is a lightweight : it runs standalone, doesn’t require much ram or CPU
can work with cold logs: you can run it on “cold” logs and see what could have happened
comes with out of the box dashboards, because we know visualisation is key
Some other features I liked were:
They’re a French company, so privacy is a huge focus. According to them, the only three things that leave your box are: a timestamp, the offending IP, and the policy they violated, and
Their tool is built on Go.
Download and install
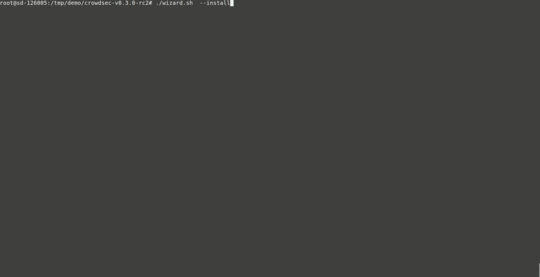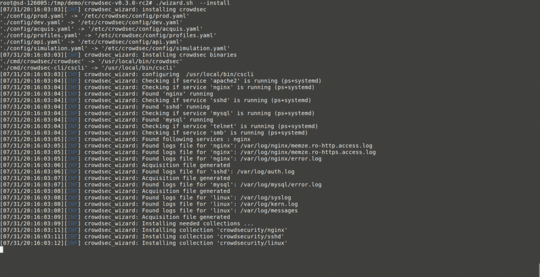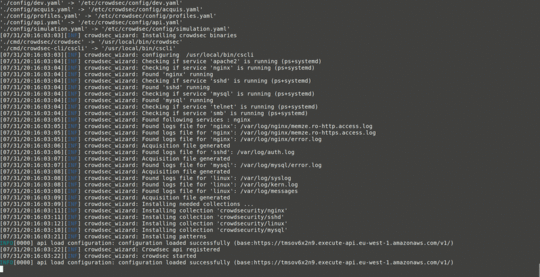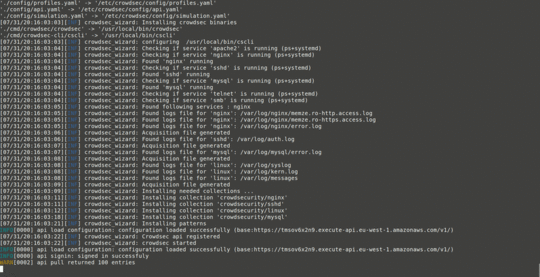
You can install this and be up and running in like two minutes.
Download
git clone https://github.com/crowdsecurity/crow...
Install
sudo ./wizard.sh -i
As the GIF shows above, it basically walks you through a wizard to select what types of daemons/logs you want to monitor—which it also auto-detects—and you’re done.
Components
The system consists of three main components:
The CrowdSec Service, which is basically the persistent service that monitors logs, tracks attacks, etc.
The Command Line Tool, which is the cli interface for interacting with the service.
Bouncers, which are the integrations with other tools that allow actions to take place.
You can also do configuration by editing files, which we’ll talk about later.
So basically the service does all the monitoring, the cscli tool is how you do configuration, ban stuff, get metrics, etc., and the bouncers are how the system interacts with other tools to actually do things, like blocking someone in SSH or Cloudflare, etc.
Usage
So there are a few different ways you can interact with the tool. My favorite is through the cscli command, which has these options:
cscli metrics
This gives you the primary outputs of what’s been seen and acted upon within the system.
cscli metrics

The output of the ‘cscli metrics’ command
This shows you all kinds of stuff, like the number of attacks within the various collections (modules), such as—in this box’s case:
http-backdoors-attempts
http-bad-user-agent
http-crawl-non_statistics
http-path-tranversal-probing
http-probing
http-sensitive-files
http-xss-probing
ssh-bf
ssh-bf-user-enum
You also get to see which logs are being looked at, plus the metrics on how those logs were parsed.
cscli ban list
This command shows you the current contents of who’s been banned, along with what got them banned.
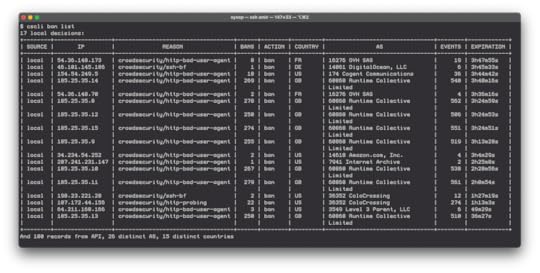
A look at a hosts current banned IPs
This shows you things like the IP that got banned, the number of events that were seen from them, the number of times they’ve been banned, the country they came from, as well as the IP their IP belongs to.
Configuration
In addition to the cscli method of making changes to configuration, you can also do so old-school Linux style. The main config for editing scenarios, for example, is in:
vi /etc/crowdsec/config/profiles.yaml

Editing the YAML config files for detection scenarios
The bad thing is also that it’s YAML.
The good thing about this is it’s just YAML. And you get to create your own scenarios as well.
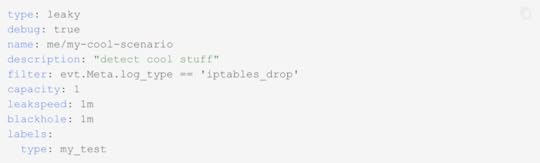
An example of a custom configuration.
Integrations
What makes this tool more like a platform than a utility is its numerous integrations with other tools.

Some of the integrations you can do with other technologies
So the system doesn’t just detect attacks using its view into your logs, it can also trigger various actions once something is detected, such as:
Blocking people in Cloudflare
Running your own arbitrary scripts
Executing a block in netfilter/iptables
Denying an IP in Nginx
Blocking in WordPress
Etc.
This tells me they’re thinking big and long-term with this thing, and not just as a replacement for a local banning tool.
Summary
So the bottom line—at the very miniumum—is that we seem to have a modern replacement for Fail2Ban, and over time that may turn into something more.
Notes
Oct 9, 2020 — Because I mentioned them in my newsletter, and I’m super enthused about them, I’m pursuing a sponsorship engagement with them for Unsupervised Learning. But I don’t really do sponsorships like other places. I consider it more like “bi-directional positivity”, i.e., I’m going to say what I’m going to say about them regardless, and if I can get them to support the show then that’s great. They get zero creative control, and I don’t even promise to mention them any number of times, or in any format. That is 100% up to me, based on what I think is the best experience for readers and listeners. It’s completely up to me if and how I choose to raise them in the show, and they get no input into what’s said. I feel strongly that this is the only type of paid product discovery that works well with a direct-support monetization model, and with a show that’s free from outside influences. You can read more about my approach here. More
The other thing about this whole sponsorship/money business is that I tend to feature a product for around 6-12 months, so if you’re reading this after 2021 they likely won’t be a sponsor anymore.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 5, 2020
News & Analysis | No. 249
I spend 5-20 hours a week consuming books, articles, and podcasts that explore the intersection of security, technology, and society. Then every Monday morning I send out the best of what I found. Sign up here >. Get the weekly version >.
MY ESSAYS
Operation Fortify: A US Ransomware Plan More
Cyber Pearl Harbor is Happening Right Now — It’s Ransomware More
Ransomware Groups Add a Third Threat Vector: DDoS More
SECURITY NEWS
The President of the United States, his wife, and several members of his inner circle have contracted Coronavirus. This adds an additional layer of uncertainty to US elections that are in less than a month. More
Github has rolled out its code scanning feature to all its users, which lets people know if they’ve added code with known security flaws. More
Right after Trump said he had COVID, some people on Twitter noticed some E-6B’s taking off and landing, which are used to manage US missile defense operations. They started speculating, which turned into a major Twitter event. Turns out, they fly all the time, so nothing had really changed. This is a great example of why it’s important to ask questions when you hear about something new. Questions like, “Is this new because we’re just now learning about it, or because it’s truly rare?” “When was the last time this happened, and what were the circumstances?” Etc. More
After saying for months that their breach did not affect customers’ bank details, Blackbaud has now revealed that this in fact did happen, including unencrypted versions of account numbers, social security numbers, and username/password combinations. More
Vulnerabilities:
Grinder had a serious vulnerability that allowed you to reset anyone’s password just by having their registered email address. More
QNAP continues to tell their users to update and to be vigilant for ransomware. They seem to be in this position quite often. More
Companies:
Cloudflare has launched a free API security tool called Cloudflare API Shield. This is super smart given how much trouble people have with API security. More
Axis Security raises $32 million to help secure remote workers. More
Cisco has purchased PortShift to get into the DevOps and Kubernetes spaces. More
TECHNOLOGY NEWS
Google Assistant has an awesome new feature called “Hold For Me”, which will wait on hold for you while you do other things. I love the innovation Google is doing around phone calls. More
Amazon has launched a new product called Amazon One, which lets you scan into a location using your palm. They’re demoing it at a couple of Amazon Go stores in Washington, but hope to sell it to lots of other places. More
Tesla crushed predictions and shipped nearly 140,000 vehicles last quarter. More
Cloudflare has rolled out a web analytics offering to compete with Google that stresses privacy by not gathering information on site visitors. More
Unscreen is a new product that can remove backgrounds not just from images, but from videos. More
Twitter is continuing to roll out voice tweets to more users. More
Facebook has launched an app called Forecast, which does “crowdsourced predictions”. It lets you make predictions about things, which are then scored over time. Kind of reminds me of the book, Superforecasting. More
Companies:
Amazon’s Prime Day is October 13th and 14th. More
Golden is a company that wants to ‘map all human knowledge’, and it just raised $14.5 million in a Series A from Andreessen Horowitz, DCVC, and Gigafund.
PandaScore has raised €5 million for its AI-powered eSports data dashboards. More
HUMAN NEWS
Xi Jinping has shocked the climate change community by saying he will have his country’s carbon emissions peak before 2030, and that he expects to reach carbon neutrality by 2060. More
Morgan Stanley is buying E*Trade. More
New York City thinks half of its restaurants will close permanently. More
Publishers are getting worried because digital book borrowing rates have increased by 52% since March. More
Undergraduate degree enrollment has fallen significantly during COVID, but post-grad enrollment is up. This seems like part of the disturbing trend of the marketable (those with degrees) seeking to become more so, while those who are less marketable (those without college) are giving up. More
Girls Who Code says half of young women will leave their tech jobs by age 35. More
Actively speaking multiple languages reduces the chances of cognitive impairment, with locales that speak more than one language experiencing dementia prevalence that’s 50% lower. More
Mars is as close to the Earth this week as it will be for another 15 years. More
IDEAS, TRENDS, & ANALYSIS
Do Things That Don’t Require Scale More
An argument that a better way to think about China and Taiwan is not “will they invade or not”, but rather as a Civil War that was put on pause during WWII and has never ended. More
UPDATES
I’m in the process of redoing my RSS feeds in Feedly. I used to have my tags, or categories, listed fairly generally, e.g., security, technology, etc. But now, with so many feeds, it’s hard for me to get through all the titles while still filtering for context and quality. In other words, I need to be able to adjust how skeptical I am of something based on the source, and this is hard to do when I’m looking at 797 articles. So what I’m doing now is breaking my categories into smaller pieces, like, “news-high-quality, news-political-analysis, security-disinformation, tech-social-discovery”, etc. This tells me the level of caution I should employ, and the frame of mind I should be in, when parsing content. As part of that, I’m also pruning a lot of sources and focusing on fewer, higher-quality sources. We’ll see how it goes. Early Screenshot
DISCOVERY
Thinkst Canary — Three minutes of setup and nearly zero false positives in detecting threats on your network. More
ASMRION — A generator of soothing sounds. More
INTEZER — Track the use of libraries with offensive capabilities by threat actors. More
You can now use IPINFO to resolve IPs to hostnames very quickly. IPINFO is absolutely one of my favorite recon tools! More
GHunt — A tool that gathers lots of Google-based information on someone based on just their Gmail address. More
RECOMMENDATIONS
Enjoy the Best—Not the Latest—Media. “Go by the average rating, not popularity. It’s better to watch something a million people love than something 10 million people watched and consider okay.” More
APHORISMS
“The difference between successful people and really successful people is that really successful people say no to almost everything.”
~ Warren Buffet
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


October 4, 2020
Ransomware Groups Add a Third Threat Vector: DDoS
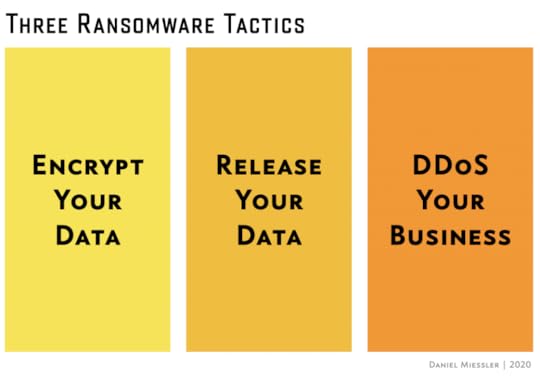
I’ve been writing a lot on ransomware recently, and wanted to comment on an interesting new development in attackers’ toolchests.
At first they started with:
If you don’t pay, you won’t get your data back.
This is the original ransomware tactic. It’s a denial of service against your data. You pay, and you (sometimes) get your data back.
Then, within the last year or two, they started adding a second technique, which is stealing the data before they encrypt it—and then if you don’t pay they threaten to release that data and embarrass your business.
If you don’t pay, we’ll release this data to the public.
And now they’re adding a third tactic, which is a denial of service again, but at the business/network level. They threaten to DDoS your company so customers can’t use your service.
If you don’t pay, we’ll knock your business offline.
This is a brilliant set of options for an attacker, and they seem to be moving from left to right, which is the order in which they became popular. So they start by asking if people want their data back. If they have good backups, or don’t need the data, they threaten to release that data to the public, and if that doesn’t work they now seem to be pivoting to a threat to take the business offline using a DDoS attack.
All three cases target the business’s ability to make money. The first and third are direct hits to the ability to do business itself, and in the case of embarrassment, it’s an attack on reputation, finances, and resources via lost customers, fines, etc.
They also get to point to real-world examples in their threats, such as the situation in Las Vegas where student information was just leaked because a school declined to pay a ransom.
The thing that makes these groups so dangerous is their ability to evolve their attack techniques. And that’s not just the quality of their malware, but the effectiveness of their approaches to victims.
Some groups play the sympathy card, and apologize for asking for the ransom. Others pretend their threats are “findings” that are part of a bug bounty program, which gives the company the out of paying security researchers instead of hackers.
Whatever the tactic, the problem is that the attackers are evolving a lot faster than defender defenses. And we should expect that gap to continue and even widen in the coming months and years.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Operation Fortify: A US Ransomware Plan

The US is currently being ravaged by ransomware.
Google News Results for US Ransomware
Our schools are being disabled, our small businesses are being pilfered, our cities are being taken offline, and now our hospitals are being attacked as well.
I talk about the reasons here, but in short, we have long had a horrible state of security in our local governments, our small businesses, our schools, and our hospitals. But until recently, attackers were using less-advanced malware in an unorganized way.
Now they’ve not only started perfecting the tooling they’re using, but they’ve figured out how to monetize the entire operation. They’ve married the tech with the business side, and the combination has caused an epidemic.
The problem is that we’re figuratively out-staffed and out-gunned. In low-security environments, attack is infinitely easier than defense. These soft targets not only lack the defensive technology to protect themselves, they don’t even know what that tech is. And even if they did they wouldn’t have the people to do a basic security assessment, implement basic security practices, and to install and maintain some basic defensive technology.
So I have a proposal: Operation Fortify.
Free to attendees.
The Pentagon starts a new program called Operation Fortify, which allocates multiple billions to hardening our essential infrastructure of governments, schools, SMBs, and hospitals.
This is accomplished by activating millions of people into the US workforce via a new, standardized security course that takes people new to the industry or who are already working in it—and teaches them how to secure an organization.
These are the top 20 NCC and Optiv-type companies in the country.
Those people are then hired as supplemental staff to the US’s existing security services companies that do consulting like this already.
I know many of the best people in the industry for making this course content.
We create a free, instructor-lead, 2-week (virtual) security training course available to anyone in the US who wants to get into security (or move into this area). The course is trade-focused in that it teaches how to do very specific tasks that will help attendees lock down organizations.
Those tasks are: Security Fundamentals (Security+), Networking Basics, Sysadmin Basics, Security Assessment Basics (Nmap, OWASP Zap, etc.), Security Hardening Basics (Patching, Disabling Services, etc.), Ransomware Basics (Common Features, Common Variants, etc.), Endpoint Tool Basics (SentinelOne and Crowdstrike).
We then create a concise Fortify Hardening Methodology (FHM) that serves as an infographic and Top-10 list of items to be done for every entity in the country we want to protect.
Maybe add a Cyber to the name. People love some Cyber.
After people go through the course and pass the exam, they become Fortify Certified. They are now part of the National Fortify Task Force, and are eligible for hire at these existing US security companies.
The Fortify Project then goes to SentinelOne and Crowdstrike, taps them on the shoulder, and says, “You’ve been drafted. We’re securing the entire country using your software. Here’s a lump sum, so make us a free version to be used in all these organization types.
We then divide up the country into regions and verticals. So we’ll have like Southwestern Hospitals, for example, and Northeastern Governments. Every government, school, hospital, and SMB in the country will be accounted for and entered into our National Attack Surface Map (NASM).
Then we execute.
Project Fortify deputizes all these security services companies to carry out the hardening procedures in the Fortify Hardening Methodology.
Fortify-certified people are added to the ranks of the branch of NCC/Optiv/Etc. company where they live as they graduate the course.
Each new recruit then gets virtually deployed (via Zoom, et al) to their assigned “customer” based on where they’re needed most in the NASM.
If you’re some random county government in upstate New York, for example, Julie will show up one day and say, “Hi, I’m with Project Fortify, and I’m here to help.” She’ll then proceed to follow the Fortify Hardening Methodology for that customer. Figuring out what they have, getting it patched, locking down credentials for key systems, getting the security software installed and configured, etc.
If your objection is that it’ll be a nightmare to put partially-trained people onsite doing work like this, I have two responses. First, you should have more faith in American industriousness. And second, we’re already living a nightmare. It’s actually pretty hard to go into one of these places and MESS UP their security.
If your objection is that this will be hard, or that it’ll cost a lot of money, well, yeah. The only thing that will cost more is doing what we’re doing now. And given the state of military budgets, what’s a few billion among friends?
To be clear, it’s not that I think this is a good idea. There are many challenges with it. I simply think it’s the best option we have.
It activates Americans. It puts them in play against a serious threat. And it simultaneously functions as an infrastructure enhancement project—kind of like Roads and Bridges—and a national training program that addresses the cybersecurity skills gap.
Notes
We could also have a massive network of technical support, using people in infosec who already have jobs. So basically the Fortify Operatives? who are deployed onsite can ask questions about installations, configs, etc. For specific product support, the company itself can potentially offer help with a dedicated support line just for Fortify assistance.
A major, positive side-effect will be that we’ll have trained somewhere between tens of thousands and a few million Americans with some basic security knowledge. Some significant percentage of them are likely to transition into careers in the field using that jumpstart.
This is not the logo I recommend. It’s just a placeholder graphic from the internet that I added the Fortify project name to. But—even more than most projects—this definitely needs a great logo.
The practical nature of the training is likely to help with both the effectiveness of the people onsite during Project Fortify, but also in their marketability afterward.
—
If you get value from this content, you can support it directly by becoming a member. Being a member gets you access to the newsletter every week instead of just twice a month, access to the UL Slack Channel, the UL Book Club, the UL Archives, and access to future member-only content.


Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers






