Daniel Miessler's Blog, page 49
June 11, 2021
How I Knew Stadia (And Similar Products) Would Fail
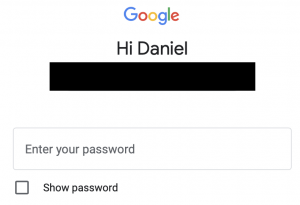
As soon as I heard about Stadia I started predicting the day it would enter the Google Graveyard.
Why?
Because for almost a decade I’ve been forced to scream at my monitor—along with many others—around completely useless user experiences.
One of the worst ones is hinted at above in the login process.
If you have multiple Google logins you get to play a fun game when you try to authenticate: it presents you a random one of your accounts as if that’s the one you’re trying to use.
But there’s no pulldown. No. Instead, you have to hit Next.
Then you get a pulldown.
Now, let’s say you have accounts A, B, and C. Your main account is A. You sometimes use B. And very rarely do you log into C.
As it turns out, if you ever do decide to use C, it might magically become the default for logins for the next several days or weeks—even if you have gone through the idiotic “Next” process to log into account A a dozen times since.
So you’re like:
Me: “Hey, let me authenticate to account A.”
Them: “Sure, here’s a login to account C.”
Me: “Nah, that’s ok, where’s account A?”
Them: “Just pretend you really want to go into account C and hit Next.”
Me: “Ok, well just know that I hate you.” clicks Next.
Me: pulls down the login for account A, logs in.
Now it’s later in the day, or maybe the next day. And I’ve not logged into account B or C in days at this point…
Me: “Hey, I need to authenticate to account A again, you know because it’s my main account.”
Them: “No problem, I completely understand. So it looks like you’re trying to log into account C. Here’s a password field.”
Me: “Are you fucking kidding me? You make me want to buy a cabin in the mountains. Not account C. My main account.”
Them: “No problem, you can change that.”
Me: “Cool, how do I do that?”
Them: “Hit next.”
Me: “To log into account C?”
Them: “Yeah.”
tables flip and cuss words are combined like new Taco Bell offerings
Me: “Seriously? Again?”
Them: “Yeah.”
repeat this process for days or weeks
—
Now, here’s the fun part.
This hasn’t been broken since March. Or since 2020. Or since 2015.
This is like a major design flaw that’s probably killed thousands from strokes at this point, and it’s existed for YEARS.
And the same thing exists for logging into tons of interfaces all over Google. Admin panels. Configuration screens. Etc.
Like the functionality is great, but how do you actually find it and use it?
This is why Google Wave Plus Meetover Outhangs never took off either. Random fucking interface, which isn’t intuitive, and which changes constantly.
So they announce Stadia. An interface and technology for gamers.
I know instantly it’ll fail. Not because of the gaming stuff, but because nobody can stand to use a Google interface for more than a few attempts before they call a fucking suicide hotline.
Google isn’t at fault for making this mistake.
They’re at fault for making it constantly, over and over, for over a decade—if not longer.
RIP Stadia, and most products that come after it.
Until Google figures out a workflow for self-improvement, their technology will basically transition from cradle to graveyard.
Here’s How I Know Stadia (And Similar Products) Will Fail

As soon as I heard about Stadia I started predicting the day it would enter the Google Graveyard.
Why?
Because for almost a decade I’ve been forced to scream at my monitor—along with many others—around completely useless user experiences.
One of the worst ones is hinted at above in the login process.
If you have multiple Google logins you get to play a fun game when you try to authenticate: it presents you a random one of your accounts as if that’s the one you’re trying to use.
But there’s no pulldown. No. Instead, you have to hit Next.
Then you get a pulldown.
Now, let’s say you have accounts A, B, and C. Your main account is A. You sometimes use B. And very rarely do you log into C.
As it turns out, if you ever do decide to use C, it might magically become the default for logins for the next several days or weeks—even if you have gone through the idiotic “Next” process to log into account A a dozen times since.
So you’re like:
Me: “Hey, let me authenticate to account A.”
Them: “Sure, here’s a login to account C.”
Me: “Nah, that’s ok, where’s account A?”
Them: “Just pretend you really want to go into account C and hit Next.”
Me: “Ok, well just know that I hate you.” clicks Next.
Me: pulls down the login for account A, logs in.
Now it’s later in the day, or maybe the next day. And I’ve not logged into account B or C in days at this point…
Me: “Hey, I need to authenticate to account A again, you know because it’s my main account.”
Them: “No problem, I completely understand. So it looks like you’re trying to log into account C. Here’s a password field.”
Me: “Are you fucking kidding me? You make me want to buy a cabin in the mountains. Not account C. My main account.”
Them: “No problem, you can change that.”
Me: “Cool, how do I do that?”
Them: “Hit next.”
Me: “To log into account C?”
Them: “Yeah.”
tables flip and cuss words are combined like new Taco Bell offerings
Me: “Seriously? Again?”
Them: “Yeah.”
repeat this process for days or weeks
—
Now, here’s the fun part.
This hasn’t been broken since March. Or since 2020. Or since 2015.
This is like a major design flaw that’s probably killed thousands from strokes at this point, and it’s existed for YEARS.
And the same thing exists for logging into tons of interfaces all over Google. Admin panels. Configuration screens. Etc.
Like the functionality is great, but how do you actually find it and use it?
This is why Google Wave Plus Meetover Outhangs never took off either. Random fucking interface, which isn’t intuitive, and which changes constantly.
So they announce Stadia. An interface and technology for gamers.
I know instantly it’ll fail. Not because of the gaming stuff, but because nobody can stand to use a Google interface for more than a few attempts before they call a fucking suicide hotline.
Google isn’t at fault for making this mistake.
They’re at fault for making it constantly, over and over, for over a decade—if not longer.
RIP Stadia, and most products that come after it.
Until Google figures out a workflow for self-improvement, their technology will basically transition from cradle to graveyard.
June 7, 2021
News & Analysis | No. 284
June 1, 2021
News & Analysis: No. 283
[ Sponsorship — If you’re a company interested in appearing in the UL Discovery Section as a Sponsored Discovery, you can now reserve a spot for Summer/Fall 2021! Reserve ]
SECURITY NEWSThe FBI says the Conti ransomware gang, which disabled the Irish healthcare system, has also gone after healthcare and first responder networks in the United States. They say they’ve hit over 400 organizations worldwide, and at least 290 in the US, including police departments, 911 dispatch centers, and more. More
Researchers at Georgetown University used GPT-3 to generate disinformation on climate change and foreign affairs, and they were able to tangibly sway real peoples’ opinions. They showed people GPT-3 generated content on Afghanistan troop withdrawals and US sanctions in China, for example, and were able to double the number of people against a given policy. More
The SolarWinds group is going after think tanks with a new backdoor called “NativeZone”. More
Have I Been Pwned has gone open source, and the project is getting help from the FBI in pulling in known-compromised passwords. More
New flaws in Bluetooth allow attackers to impersonate legitimate devices, allowing MiTM attacks. A series of CVEs have been released around the flaws. Impacted vendors, including Android, Cisco, and others are working on patches. More
Microsoft released a tool called Counterfit for testing the effectiveness of AI-based security systems. More
Facebook says Russia is still the biggest player in disinformation on its platform. More
Continuous Attack Surface Management (CASM) is becoming a real space now. There are tons of players getting in, from vulnerability management companies to small startups that come from the bug bounty community. More My Analysis
A UN report says a drone may have carried out the first known autonomous attack that killed a human last year. The attack was in Libya, and was made possible by an object recognition system that does not require connectivity once it’s received a target. This allows it to travel, hunt, and carry out an attack without being given explicit instruction once the target is found. Daniel Suarez warned us about this in his book, Kill Decision. More
Danish media is saying that Denmark helped the US spy on European politicians, including Angela Merkel. More
Vulnerabilities: HPE fixes an 0-day in Systems Insight Manager. More Siemens PLCs have some newly discovered vulnerabilities. More Drupal has released security updates. More VMware vCenter has a critical RCE. MoreIncidents: JBS Foods, the world’s largest beef and poultry producer with 245,000 employees around the world, has shut down production due to what they’re calling a cyberattack. MoreCompanies: Crowdstrike and EY are uniting to work on Organizational Resiliency. More Salt Security raises $70 million to do API security. More Material Security raises $40 million to address email hacks through integration with identity-protection services like Duo and Okta. More
TECHNOLOGY NEWSMicrosoft is teasing a new version of Windows, and the announcement could be soon. Supposedly there will be major UI changes, and updates to the app store. I’d like it to have fewer ads. That’s my ask. More
Microsoft has released a tool that lets you write basic code using the power of GPT-3. More
An AI system looked at 40 years of scientific papers and predicted 19 out of the 20 most impactful publications. It then looked at current work and picked 50 recent papers that it thinks will be among the top 5% of biotech papers in the future. Sounds like a dream tool for investors. More
Twitter appears poised to release Twitter Blue, its $2.99 monthly subscription tier. Features will supposedly include the ability to undo a tweet, among others. More
The world’s fastest AI supercomputer came online at Lawrence Berkeley National Lab. It’s an HP-built Cray computer with 6,159 NVidia A100 Tensor Core GPUs, and they intend to use it to build a massive 3D map of the universe. More
Peloton is building a new $400 million dollar factory in Ohio. More
Tesla has turned on its in-car camera so that it can monitor drivers while they’re using autopilot. It’s designed to monitor the driver for inattention, and the data is not supposed to leave the car. More
Tesla is being fined in Europe for throttling charging speeds. More
Tesla is now shipping cars without radar sensors, going instead with camera-based detection. More
HUMAN NEWSChina is now allowing citizens to have up to three kids. Just to be clear, it was illegal to do so before now, because the government can tell you how big your family can be. So I guess…thanks? What’s next? Freedom of expression? Reminds me of Saudi Arabia allowing women to drive. What do you want, a cookie? You’re not supposed to get credit for returning rights that weren’t yours to take away. More
A study by Public Health India says two doses of COVID vaccine (Pfizer or AstraZeneca) are effective against the India variant, but it said you’re significantly more vulnerable with only one dose. No word on Moderna, but I’m hoping it has similar efficacy against that strain. More
China has maintained an artificial sun at 120 million degrees Celsius for over 100 seconds, which is a new world record. I’m impressed, but I wish this wasn’t the country that shrugs when their satellites fall out of the sky. More
Housing inventory is down 37% over year to a record low. Only San Francisco and New York have a bump in inventory. Lumber prices are up 300% and 63% of one sample had bid on houses they’ve never seen. More
Median home prices are up 19% over a year ago, and are at the highest point since 1999. More
We’re at an all-time high number of smokers, at 1.1 billion. Rates are dropping, especially in the west, but population growth in China and India has lead to overall numbers being higher than ever. An estimated 8 million died from smoking in 2019. More
CONTENT, IDEAS & ANALYSISConvincing and Belonging — I think people’s opinions are often tied to their identity, which is why it’s so hard to change people’s minds. When you’re arguing with someone, think about what’s at stake for them if they were to see things your way. It’s often more than they’re willing to pay. And ask the same about yourself as well. Would you lose a sense of belonging to a group if you were to change your mind about certain topics?
Lab Leak Theory Insanity — This lab leak theory stuff is just insane. Walk with me here. There are many labs (I counted around 50) that deal with extremely dangerous pathogens, and it’s widely known within the space that we have—internationally—a problem with safety. Not only have we had many leaks and accidents all over the world in the last couple of decades, but experts in the space have been blowing the whistle about the issue for years. They’re screaming at full volume that this is a problem. They write papers. They give interviews. They give talks. They were before COVID, and they still are. So if this thing actually came out of a lab in China, that would be bad, but it’s not the news most people think it is. Similar leaks have happened in the US and UK. And the supposed news that Fauci may have funded the lab that the leak might have come from? Um, he’s been involved in virus research for decades, and is closely tied to how money gets distributed for research. This is like finding out that a plane crashed somewhere, yet some guy sent money to a related place to research air travel safety. You can still have accidents even if the point of the research is safety. Another analogy would be testing of bullet-proof vests. If you donate money to a place that does that research it’s not a conspiracy if someone gets injured during live testing of one of the vests. Instead, just like a plane crash, it’s another instance of what we’re trying to avoid, and a call to double down on safety. So, yeah, big conspiracy—the guy who’s famous for virus research sent some of his virus research organization’s money to (among others) one of the labs that does—wait for it—virus research. Riveting.
NOTESI just got done re-reading Practical Vim, by Drew Neil, and redoing my entire (Neo)Vim config. I started this journey by learning a ton more while writing a new Vim article, so I decided to re-parse Drew’s book and take notes, which lead to me redoing everything. Somehow I ended up changing my Zsh config in the process, basically going from zpresto back to ohmyzsh. This is my tech version of a meditation retreat, or spring cleaning. I absolutely LOVE optimizing my shell and Vim configs. Reminds me of walking into a book store. Endless self-enhancement. Vim Config Screenshot Shell Screenshot
The Vim tutorial I’m working on is going to be based on gradual steps. I’m basically taking Vim’s functionality and breaking it into chunks, and then ordering them by difficulty. So it might end up having like 15 or 20 levels, with each having a very small amount to learn. I’m excited about revealing the depth of Vim in an approachable, tiered sort of way.
Currently going through this free online course at MIT called The Missing Semester of Your CS Education. More
I just renewed my Audible Annual (24 books) subscription for the third time in less than a year. Pretty sure I’m way over 60 books read so far.
One of our UL Community members, Tim Leonard, built himself a Dogebago and is currently driving it across the country. More
DISCOVERY [ Sponsored Discovery ] Thinkst Canary Tokens — Most companies discover they’ve been breached way too late. Canary fixes this: just 3 minutes of setup; no ongoing overhead; nearly 0 false positives, and you can detect attackers long before they dig in. Check out why our Physical, VM, and Cloud-based Canaries are deployed and loved on all 7 continents. Explore
Is This a Cyberattack? — A public service website that indicates whether something they’ve heard about in the news was an actual cyberattack. Teaser: the Colonial attack wasn’t. More
A privacy tech worker explains how being at his mom’s house for a week resulted in him receiving ads for her toothpaste. More
SecLists 2021.2 Release — This release includes multiple updates from the community. Thanks to g0tmi1k for all the hard work on maintaining updates! More
Synthesia.io — Create your own AI video by writing a script and picking a model to perform it. More
Pentesting Mindmaps More
The Feynman Lectures Audio Collection More
What Cybersecurity Can Learn From Video Games. More
Deepfakes, but for Maps More
A new-ish technique allows pentesters to use captured NT hashes in attacks even if they’ve not been cracked. More
FindAReddit — Find Subreddits for your favorite niche. More
How Well Can You Distinguish High-res Audio? More
Public Pentesting Reports More
Drunk Post: Things I’ve Learned as a Sr. Engineer — Someone gets drunk and gets way too honest about the life of a programmer. More
A Writing Tip I Learned at Oxford More
RECOMMENDATIONSDavid Perell has compiled a great list of paradoxes in modern life. More
APHORISMS“Nothing is more persuasive than the opinion you desperately want to believe is true.”
~ Morgan Housel
May 31, 2021
Unsupervised Learning Sponsorship
Unsupervised Learning is both a podcast and a newsletter, and it takes an integrated approach to sponsorships. We believe the traditional ad model disrupts the reader/listener experience, so our approach is to integrate supporting products and services into our popular Discovery section.
We believe this is better for both the audience and the sponsor.
This is an area of the show where we surface products, services, tools, articles, etc.—that we think our audience would enjoy and find valuable. This section is embedded naturally within the content rather than presented as interruptions before, during, or after.
We believe this serves the primary purpose of exposing the audience to stuff they want to hear about—which is a core part of the show’s brand—while also avoiding the jarring and offputting nature of advertising.
Most mentioned products and services are not supporters/sponsors.
How are sponsors featured?
How a sponsored discovery looks within the newsletter
Featured products and services appear at the top of the Discovery section and are tagged as a Sponsored Discovery, with a description of what the product/service does and the value it brings.
Because the newsletter is the text version of the podcast, a Sponsored Discovery will feature both in the newsletter and on the podcast (text and audio). Each episode is also then presented on danielmiessler.com (my personal site), which is in the Alexa Top 100K and receives over 200K views per month.
Unsupervised Learning releases two (2) public newsletters per month, and two (2) paid newsletters per month—for a total of four (4) News & Analysis episodes per month.
What type of audience does Unsupervised Learning have?The Unsupervised Learning audience is heavily weighted towards senior-level Information Security and Technology professionals based out of the United States, Europe, Canada, and Australia.
There is also significant representation among creatives, international travelers, and lifestyle-focused subscribers.
What is the reach for Unsupervised Learning?This doesn’t include standalone content that can be released in addition to scheduled News & Analysis episodes.
Each episode goes out over the following four channels:
Email (Reach: ~42,000/~1,000 subscribers in May 2021)Podcast (Reach: ~29,000 downloads for May 2021)Website (Reach: Alexa top 100K, ~238K views for May 2021)Twitter (Reach: Verified, ~116K followers in May 2021)Great, how do we sign up?We are currently scheduling slots for the Summer and Fall of 2021.
To reserve slots, reach out to us at:
sponsorship@unsupervised-learning.com
We look forward to working with you!
Additional InformationHere are some additional frequently asked questions.
What can we expect for engagement?Newsletter open rates are 25-35% for public episodes, with a 7-12% click rate.Newsletter open rates are 60-80% for subscriber episodes, with a 35-50% click rate.Promoted links generate anywhere from dozens to hundreds of links, depending on the epsiode.What else do we need to know about working with you?We accept sponsors based on how well they fit with our audience, and reserve the right to refuse sponsors for any reason.Sponsorships can include products, services, job openings, other calls to action, or general awareness.We feature one sponsor per episode. We accept multiple bookings, but prefer a gap of two episodes.We try to limit copy to ~400 characters.What data can we get from our campaign?What we are able to share:
How many people opened your emailHow many people clicked the sponsored linkWhat we will never share:
Any information about our subscribers, including those who engaged with your campaign.May 26, 2021
How I Organize my RSS Feeds, 2021 Edition

I’ve been writing about RSS feed organization since at least 2007, and it seems to be a recurring topic for me.
This post will describe my latest iteration based on two factors:
A partial resurgence of RSS as a preferred news consumption mediumFeedly as my tool of choicePrevious iterationsMy most recent attempt to organize my feeds was the “tag everything” approach, so I had dozens of subcategories within Feedly.
It was cool until it wasn’t. The cognitive overhead of needing to check so many hyper-specific feeds simply overwhelmed any advantage they provided.
The current systemMy latest approach is based around content collection for my show, Unsupervised Learning.
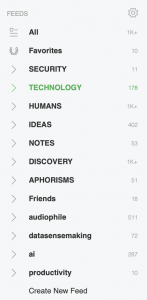
Feeds organized by show sections
The show is focused on how security and technology affect humans and society, so the top categories are:
I also subscribe to aggregator feeds like Hacker News, Lobsters, and Reddit.
NewsThese sections focus on current events.
Security (information security, cybersecurity, national security)Technology (new tech, tech trends, innovation)Humans (society/government/trends/future)Section Feeds: Sites for individual security thinkers, quality security blogs, quality security product blogs, threat intel blogs, new gadget blogs, tech review sites, science journals, science journalism,
IdeasThen I have an Ideas, Content, and Analysis section that focuses on my own ideas and/or thoughts about existing trends. This includes any type of creative thinking, new technical projects, or analysis of patterns that I see or that are being discussed elsewhere.
Section Feeds: My own new work, other thinkers, think tanks, policy groups, statistics, polling organizations, etc.
NotesThen there’s a Notes section that captures different stuff I’ve been working on I think are worth mentioning in a personal capacity.
Section Feeds: Feeds of what I’m reading, watching, testing, etc. Reminders of stuff I’ve shipped, discussions online about something I’ve shipped recently.
DiscoveryMy Discovery section is where I put non-news projects, tools, and articles that I didn’t create. It’s the curation portion of the show.
Section Feeds: New gadgets, new art, quality analysis articles, new security tools, etc.
I also have a Recommendations and Aphorisms Section, but they’re pretty simple. The weekly recommendation is really like the best thing or idea I’ve had/seen all week that I think you should check out. And the Aphorism section I populate with feeds on quotes and wisdom, plus I do my own parsing of quote sites for that one.
TakeawaysOk, so where does this leave us? My takeaway here is that you should orient your RSS reader around your current lifestyle.
My current vibe is security, tech, and society, which is why I have this show. And it’s a weekly show, so that’s why I benefit from consuming news and ideas in a certain way. And my newsreader reflects that.
You should do the same.
Are you a mood-focused consumer of news? Maybe you could do CURIOUS, DOWN, UPLIFTING, TECHNICAL, or something like that.
Or maybe you’re purely subject-based, so you’d benefit from a more traditional APPSEC, NATSEC, INFOSEC, BREACHES, etc.
Be willing to tinker with different systems.
RIP Google Reader, never forget.
SummaryI optimize my RSS feed structure at least every 2 yearsGoing hyper-specialized didn’t work for me: too many sub-feedsMy current system is oriented around my show because that’s how I’m processing contentCustomize yours based on your desired perspective when consuming, e.g., Mood, Subject, etc.Be willing to try out different systemsMay 23, 2021
News & Analysis | No. 282
May 22, 2021
Why an NTSB Wouldn’t Be Helpful For Ransomware

Twitter is great for quick ideas that may or may not be useful. I had one the other day:
An NTSB, but for ransomware.
— ᴅᴀɴɪᴇʟ ᴍɪᴇssʟᴇʀ (@DanielMiessler) May 22, 2021
After posting it and reading a few comments I realized why the analogy of plane crashes and ransomware events don’t really match. At least not yet. I thought the reason they don’t match was worth a short piece.
Basically, the reason the NTSB is so effective at its job comes down to 2 things:
The number of variables it’s looking at are relatively known and finiteThey have the influence to actually affect change in the airline industryTaking the first one, planes haven’t changed all that much in the last four decades. They’re getting bigger and more technologically advanced, of course, but a plane from the 1980s largely functions the same way as a plane in the 2020s. The plane is controlled the same way, i.e., by adjusting thrust combined with flaps on the wings and the tail.
The other area for fault is even more similar: humans—namely the pilots. So the knowledge largely accumulates when it comes to stopping crashes, and when something goes wrong we have a good idea of where to look.
And secondly, if the NTSB or any similar agency were to find a fault in a technical system, or in the procedures that humans use to fly planes, they could write a scathing report and people are likely to listen. Especially if they have evidence that an accident was caused by this issue.
Not so with ransomware.
First, the number of variables in IT is overwhelming. Business IT systems are not tubular fuselages with wings, a tail, and flaps that haven’t changed much since the 1960s. Sales and accounting could be analogs to those things, but they’re not represented physically anymore like on a plane.
If anything, modern IT systems are a virtual airplane that can be changed—or even deleted—via code. So while modern airplanes might have computer control systems, they at least still have actual wings and flaps, which interact with actual air outside the plane.
Even more different are the humans involved. In air travel, humans are locked down to specific behaviors that are strictly controlled by internationally approved checklists. Pilots used to bring their raw training and talent into the cockpit, and planes crashed a lot. Now everything is checklists and they crash very rarely.
So if a plane does crash, one of the first things the NTSB looks at is whether the pilots deviated from standard operating procedure. And that procedure is extremely specific. Everyone takes off the same. Everyone lands the same. Etc.
Plus they have massive amounts of data from all the systems on the plane to be able to find deviations from baseline.
And that’s the key right there. With flying there is a normal. There’s a standard—both for the tech of the airplane and for the humans that are running it.
With IT it’s a wonder anything works at all. It’s a Mad Max scene on a rock floating in a magma river.
All the tech is virtual, not actual metal interacting with air. If Salesforce goes down you no longer have a plane. You’re just people sitting in the sky. In chairs.
And people running business tech don’t generally have unified checklists. Or more specifically (and horrifically), there are lots of unified checklists. If things were standardized we wouldn’t a constant migration of collaboration tools in the industry, with today’s documentation Valhalla being tomorrow’s graveyard.
Basically, the average business running day-to-day on IT systems is a dumpster fire inside of a wood chipper—but all inside of Minecraft.
So if you called a Cyber NTSB into a business that had been hit with ransomware, they wouldn’t be able to help much.
They couldn’t ask for logs because they may or may not exist. They couldn’t ask for deviations of protocol because the protocol is YOLO. And there’s no physical black box or plane to inspect because that was all code that may have been changed or deleted during the incident.
In short, we don’t have an industry that’s serious and adult enough to get use out of an NTSB. They need a haystack to look for needles in, and we’re not mature enough to provide one.
I think we’re going to see a big market for “Assumption of Total Loss” solutions in the SME space. ATL Solutions.
Basically a unified solution for everything across CRM, Finances, Scheduling, Computing Environment, etc., all of which is being constantly saved offline.
So if the business ever gets disrupted you just zap the whole thing and get a fresh image. New machines, an up-to-date instance of your books, calendars, data, etc.
Of course these systems will also be attacked by ransomware.
Fire? Earthquake? Ransomare? Remote employees? Onsite employees? Doesn’t matter. Zap and restore.
This will only work for relatively new businesses that are small enough to have everything in such a system, or companies that are willing to go through the hard process of migrating into that kind of solution, but I think the ransomware threat might actually push us in this direction.
Anyway, back to the NTSB.
It’d be nice to have one for cyber, but it’s not realistic right now and probably won’t be for a very long time.
If the only thing they could do is show up and tell you that you’re a soup sandwich, that’s not providing much value.
NotesI thought of this old post of mine while I was writing this, and it came up in my Related Posts plugin as well. Worth the read if you’re willing to be even more depressed: Technical Professions Progress from Magical to BoringMay 19, 2021
Analysis of the 2021 Verizon Data Breach Report (DBIR)

Every year I like to look at Verizon’s DBIR report and see what kind of wisdom I can extract. This year they appear to have put in even more effort, so let’s get into it.
The format is simple: a series of content extraction bullets, some analysis and commentary along the way, and then a quick summary of what I saw as the main takeaways.
Content extractionMy Definitions of Event, Alert, and Incident
A definitions reminder:
Incident: A security event that compromises the integrity, confidentiality or availability of an information asset.
Breach: An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
This year they analyzed 79,635 incidents, 29,207 met their quality standards, and 5,258 were confirmed data breachesThey covered 11 main industries across 88 countriesThey map to the CIS controls for recommendationsTop three patterns in breaches were: social engineering, basic web application attacks, and system intrusionTop three patterns in incidents were: denial of service, basic web application attacks, and social engineeringInteresting that social engineering and basic web application attacks were in the top three for both breaches and incidents.
85% of breaches involved a human element61% of breaches involved credentialsFor breaches, the breakdown of External vs. Internal actors moved significantly towards External in 2020Similarly, the top threat actor motive moved away from Espionage and towards FinancialOrganized crime made up over 80% of threat actors, with other categories—including State Actor—having very little showingTop actions in breaches were: phishing (social), use of stolen credentials (hacking), other, ransomware (malware), pretexting (social), misconfiguration (error), misdelivery (error), brute force (hacking), C2 (malware), and backdoor (malware)The top two (phishing and credential stuffing) were disproportionately represented in the dataFor incidents, the breakdown was: dos (hacking), phishing (social), other, and then ransomware (malware)So phishing and ransomware are the categories most shared among incidents and breachesRansomware doubled from 5% of breaches to 10% in 2020As in past years, financially motivated attacks continue to be the most common, and actors categorized as Organized Crime continues to be number one.
They break down actions at the beginning, middle, and end of breachesTop three for beginning: hacking, error, and socialTop three for middle: malware, hacking, socialTop three for end: malware, hacking, errorTop assets in incidents: server, person, user devTop assets in breaches: server, person, user devThe major change this year with regard to action types was Ransomware coming out like a champ and grabbing third place in breaches (appearing in 10% of them, more than doubling its frequency from last year).
So those match perfectly, at least for the top three.
Top asseet varieties: web application (server), email (server), desktop or laptop (user dev), mobile phone (user dev)Interesting to see mobile phone in there. It’s number 4, and behind desktop/laptop, but not by much. But it turns out, most of that data is from lost phones, so it doesn’t appear major afterall.
Even the median random organization with an internet presence has 17 internet-facing assetsEven the median random organization with an internet presence has 17 internet-facing assets.
Most of those systems had no vulnerabilities, but among those that are attacked it’s mostly the older ones that matter, not the newer onesAs far as what type of data is lost, the top 4 for breaches are: credentials, personal, medical, and bankI think they mean direct financial loss.
There is massive variation in the impact of an incident. First of all, 42% of BEC incidents didn’t involve any financial loss. 76% of Computer Data Breaches didn’t involve any financial loss. And 90% of ransomware incidents didn’t have any financial loss.
The range of financial losses was pretty extraordinary:
CDB ranges had 95% falling between $148 and $1.6 million, with the same median of $30,000Ransomware’s median loss was $11,150, with a range between $70 and $1.2 million95% of BECs fell between $250 and $985,000 dollars with $30,000 being the median.
The takeaway here is that there really is a market scaling based on the size of the organization and their ability to pay, and the minimums start very low/cheap.
They also did analysis on total cost of breach estimates, which I found fascinating.
The top hacking varieties in Basic Web Application Attacks were: use of stolen credentials, brute force, and exploit vuln—with stolen creds being over 80% and brute force and exploit vuln being around 10% a pieceSummaryWeb application attacks continue to dominate, with credential stuffing being the main way to attackBrute force is also key for web app attacks, and both are handled well by 2FAWe already knew this, but ransomware massively jumped in prominence, and organized crime grew as an actor type along with itErrors keep featuring at the top of these lists across industries; we have to figure out a way to reduce own-goalsThe top CIS controls are still: Enterprise Asset Inventory and Software Inventory. Never forget.While you could plan for the median breach of $21,659, a better option might be to plan for the middle 80% of breach impacts, $2,038 to $194,035. Or better yet, be prepared for the most common 95% of impacts, between $826 and $653,587. If you add to that an organizational devaluation of around 5%, then you just may have yourself a tangible figure you can plan around.
May 17, 2021
News & Analysis | No. 281
Biden signed an executive order on cybersecurity, with three top highlights: 1) multifactor authentication for all federal agencies within 6 months, 2) breach disclosure requirements based on the severity of the incident, and 3) a star rating system for the security of software sold to the government. More Analysis
Verizon DBIR 2021: The primary trends for this year’s DBIR report were web application attacks, ransomware, and credential stuffing. 85% of breaches involved a human element. Ransomware doubled to 10% of breaches. And external cloud assets were compromised more than on-prem assets. More
A security researcher has found a collection of major vulnerabilities in WiFi that affect most products that are in use today. Practical attacks don’t appear trivial to carry out yet, but that could change as the bugs are better understood and people have time to make tooling. Patches have started to come out from some vendors, but it will take time due to the fact that the bugs affect so many products over multiple decades. More
Microsoft has released a free tool called Counterfit for testing AI-based security systems. It automates the launching of different types of attacks to see how AI-based systems respond, and they partnered with MITRE to release an ATT&CK style Adversarial ML Threat Matrix. More
OpenSSH 8.2 now works extremely well with U2F/FIDO2 security keys, meaning you can easily create a hardware-based keypair using ssh-keygen -t ecdsa-sk and have things work well without elaborate hacks of your SSH configs. More
Insurer AXA recently decided not to pay out for ransomware payments, and they are now dealing with a ransomware attack of their own. A ransomware group called Avaddon says they’ve stolen 3TB of data from AXA’s Asian operations. More
The Pentagon is thinking about shutting down the JEDI cloud project due to all the legal drama around who it was awarded to. Amazon has been fighting the situation ever since the contract ever since it was awarded to Microsoft. More
The DHS is now monitoring public social media posts for signs of extremist beliefs and behaviors in an attempt to prevent situations like January 6, 2020. They appear to be focusing less on finding people, but rather on specific themes, narratives, and related plots. More
Vizio makes nearly as much from selling your data and selling ads as it does from selling the actual hardware. This is yet another example of where ‘cheap’ often equates to ‘subsidized by selling your data’. More
A report from the Center for Countering Digital Hate says only 12 people are responsible for 65% of COVID-related misinformation being shared online. More
Cloudflare is looking to replace CAPTCHAs with physical security keys. It’s a cool idea, but requires that websites adopt it. More More
Arlington Research says 85% of customers running Microsoft 365 have suffered email data breaches. More
Brian Krebs says adding Russian or Ukrainian as a virtual keyboard language will stop a lot of malware. More
Vulnerabilities: Microsoft Patch Tuesday Analysis: .NET, Exchange, NNI, and more. More SAP patches major flaws in Business One and Netweaver. More Magecart hackers are hiding PHP backdoors in favicons. MoreIncidents: Ireland’s publicly funded healthcare systems had to shut down all its IT systems after it was infected by ransomware. More Insurance company CNA has finally recovered from their ransomware incident. More Rapid7 says their source code was accessed as part of the Codecov supply chain hack. MoreCompanies: SecurityScorecard has partnered with HackerOne to bring vulnerability data to its security ratings. More Cisco has purchased Kenna Security. More Panaseer has raised $26.5 million to monitor the state of security controls across company assets. More
TECHNOLOGY NEWSGPT-Neo is a new, free version of GPT-3. The biggest difference between GPT-3, which is not free, and GPT-Neo is that GPT-3 has much larger models. GPT-Neo has 2.7 billion parameters while GPT-3 goes up to 175 billion. More
STADIA, Google’s video gaming service, looks to already be in major trouble. Google seems completely unable to make a cohesively good product anymore (functionality + usability). I don’t understand how their product people are allowed to constantly fail, for like a decade, without anyone catching on that there’s a problem. Someone said they’ve become the Oracle of the tech world, and I am starting to agree. More
Esports seems to be moving away from teams and leagues and towards influencers and streaming. A big reason for this is that the athletes themselves were prohibited from promoting themselves over their teams, which wasn’t sustainable. I think the more sustainable model is individual first—connected through looser and more temporary affiliations. More
Companies Kin raises $64 million for data-driven home insurance. More
HUMAN NEWSTop industry experts are now saying that the lab leak theory of how COVID initially spread is not conspiracy thinking, and that it needs to be taken seriously. This is something we’ve talked about here at Unsupervised Learning multiple times. Basically there were legitimate political sensitivities around being anti-China that were stopping this from being explored, but the fact is that this exact type of research has been going on for a very long time, and similar leaks have happened multiple times both in the US and in Asia. So it’s quite possible that it simply happened again in the case of COVID-19. More
Consumer prices (see inflation) rose the most since 2009 in April, and it caused a major disturbance in the stock market. More
McDonald’s, Chipotle, and others are raising wages to address the lack of applications to open positions. More
China has landed its Zhurong rover on Mars. More
It’s really hard to sell a book. The New York Times says 98% of books sold in 2020 sold fewer than 5,000 copies. And Bookstat says 96% of online books sold fewer than 1,000 copies. Only 11 books sold more than 500,000. More
Consumer Reports says Tesla Model 3 owners are the happiest car owners. As one such owner, I can say I’m definitely part of that cohort. More
Target has stopped selling Pokemon cards in physical stores because of the risk of violence between people trying to attain them. More
California has a $75 billion dollar budget surplus due to higher than anticipated tax revenue. More
The University of California is dropping the SAT for admission consideration. More
The firefighter community has a problem with arsonists. One expert says around 100 serial arsonists, working as firefighters, are convicted every year. More
CONTENT, IDEAS & ANALYSISThe Ultimate Drug is Belonging — I think Belonging is at the bottom of most conspiracy thinking and truth denial we see today. Facts can and will be ignored if they’re coming from a group that people think has abandoned them. Namely, “the elites”. We must understand this if we want to make progress in any given conversation, and it shows us very clearly why “the deplorables” narrative does nothing but make things worse. More
NOTESCurrently re-reading How Innovation Works by Matt Ridley. More
DISCOVERY The Purpose of Purpose More
43 years and 14 billion miles later, Voyager 1 is still sending us valuable data. More
Game Developer Salary Comparisons More
Ten Rules for Negotiating a Job Offer More
An EFF Threat Modeling Lesson More
Why Israel and Palestine Are Fighting More
FireEye’s DARKSIDE gang analysis. More
RECOMMENDATIONSI’m really enjoying this hilarious, improv-based podcast called A Mission to ZYXX. It’s basically a bunch of voice actors doing a sci-fi adventure. Really good. More
APHORISMS
“Freedom is nothing else but a chance to be better.”
~ Albert Camus
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers





