Daniel Miessler's Blog, page 110
November 12, 2017
Moving Application Authentication to the Operating System
For the best reading experience, I recommend you view this content natively at: Moving Application Authentication to the Operating System.
—

Benedict Evans said something on Twitter the other day that got me thinking a lot about the future of app authentication.
He’s highlighting a pain that we all experience but that we accept as necessary, like a barbed wire watch band. And it absolutely does feel like something we will eventually fix. The question is when.
I’ve been talking for a while about how good applications become OS features. I argue that new tech features follow this timeline:
The feature starts as a standalone application.
If it’s popular it’ll be adopted by social media platforms.
If it’s really compelling then it’ll eventually make it into the operating system.
There are multiple examples of this: location sharing, heart rate monitoring, workout tracking, weather, stopwatches, calculators, voice assistants, etc. It’d be enough to scare me out of being an application developer: the better your app does the faster it’ll become part of iOS and Android.
Anyway, Benedict’s point was about authentication. Why do we have all these separate logins for every application when it’s one of the worst user experiences in all of tech?
As I was thinking about it I realized that we’ve already gone through two of the phases in the App/Social/OS evolution. Password applications solve this problem by saving your passwords for you to make it easier to enter them. And Facebook and Google provide OAuth functionality so you can register and log in using your social credentials in a more transparent way.
Having an app to do it is easier than manual (step 1), and having your social network do it is easier than using an application (step 2). Now we’re just waiting for the final step, which is having the OS do it for us automatically.
And who better to know about us than our operating system? As digital assistants become more prominent, along with constant and often passive IoT interactions that will be made on our behalf, we’re going to be authenticating to services constantly. Manual interaction (and credential management) will not be an option.
Future authentication
I think the only option for us is to solve authentication’s last mile problem, which will allow us to prove not just that a device made a request, but that the right person was using that device. This is the link that must occur in order for our operating system to be able to represent us.
As I talk about in that piece, this means constantly taking multiple authentication points from us, from our gait, to our voice, to our typing patterns, ambient noise, motion sensors, and dozens of other inputs—and then using that to maintain a constantly updating authentication score.
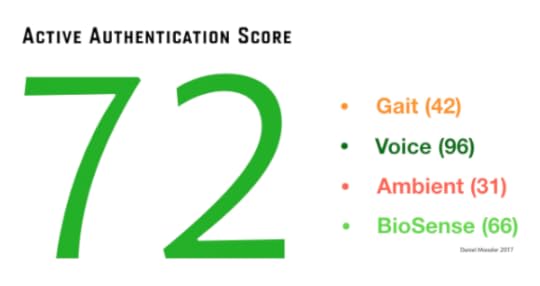
An Active Authentication Mock-up
This score updates every few seconds, and it’s a representation of how sure the OS is that you are you.
Then, when it comes time to authenticate to a service—say to open the door to your hotel just by touching the handle, or to log you in to Facebook without an extra step—your OS will do the following:
Form a request to the authentication API for what you’re trying to do (hotel door or Facebook).
Attach the current—up to the second—security score.
Sign that request, combined with your score, with the private keys of the device and user.
Send that request to a third-party Identity Validation Service, which validates that people really are who they say they are. They in turn have their own Active Authentication Score, similar to that of the OS, but they can also see where all this user has tried to authenticate recently, so they know if this particular request is likely to be fraudulent.
The Identity Validation Service then looks to see the security level required for this action—say a 65 is required to get into Facebook, but a 70 is required to open the hotel door—and if the current AAS is higher than the requirement for the service, it will sign that signed request with its own keys and send that to the service in question.
The hotel door, or Facebook, or whatever will then see a request from the device, signed by the IVS that it trusts, with a sufficient AAS score, and it allows the request.
There are a lot of steps there, and hence a lot of requests. And it doesn’t address what happens when the IVS service goes down, or is slow, or gets DDoS’d. But you get the idea. Those are engineering and security challenges, and their existence will require optimization and resilience, but they likely won’t stop something like this design from happening.
Anyway, I wish I had thought of Benedict’s point. Application authentication really is just another feature that will eventually end up being handled by the OS. And for me it can’t come fast enough.
Read or comment at Moving Application Authentication to the Operating System.
Maybe the Best Application for Blockchain is Democracy
For the best reading experience, I recommend you view this content natively at: Maybe the Best Application for Blockchain is Democracy.
—

Image from PCMag UK
There are lots of possibly great applications for blockchain technology. The one that’s mentioned most is usually finance, where people can more easily send money without no (or less) middle-entity involvement.
I think Democracy might be the killer app, though. Voting, in particular.
Two of the core concepts of the blockchain’s distributed ledger are the fact that it can’t be changed, and that every transaction can be verified by everyone else. It seems, conceptually, like a perfect fit of a technology to a human need.
But I also see challenges.
First, you need ubiquitous adoption, or close to it. You can’t roll it out for Silicon Valley and other tech-focused places and call that a victory. And it also can’t be a gate that keeps the less fortunate from voting.
There’s also the issue of tampering with Blockchains by controlling a certain percentage of the network.
Finally, there is the issue that the security of the system is based on cryptography, and attacks against that cryptography—either through traditional means or more likely through quantum computers—could cause serious issues.
Of all of these, I think adoption is the primary issue. We seem incapable of doing what we should when it requires a joint effort. Until we fix that the idea will probably be dominant only in blog posts.
Read or comment at Maybe the Best Application for Blockchain is Democracy.
November 11, 2017
Author’s Recommendations
For the best reading experience, I recommend you view this content natively at: Author’s Recommendations.
—
This is my own list of my favorite pieces I’ve written throughout the years. They’re not always the most popular, but one can hope and pretend that this is due to insufficient exposure. They tend to be more discreet ideas, or particularly heartfelt explorations of a given topic. I hope you find something you enjoy.
InfoSec
 Authentication’s Last MileHow authentication will be performed in the future of IoT.
Authentication’s Last MileHow authentication will be performed in the future of IoT.Obscurity is a Valid Security Layer
Why Biometric Data Breaches Won’t Require You to Change Your Body
IoT Functionality and Personal Privacy Are Inversely Correlated
Technology
 With Facebook and Google You Literally Are the ProductHow to tell if you’re the product or the customer.
With Facebook and Google You Literally Are the ProductHow to tell if you’re the product or the customer.The InfoSec Community is Wrong About AI Being Hype
Humans
 The Bay Area is Separating Into Red and Green ZonesHow class separation is impacting the San Francisco Bay Area.
The Bay Area is Separating Into Red and Green ZonesHow class separation is impacting the San Francisco Bay Area.How Russia is Helping America Destroy Itself
Read or comment at Author’s Recommendations.
November 10, 2017
Notes and Analysis on the 2017 Verizon DBIR Report
For the best reading experience, I recommend you view this content natively at: Notes and Analysis on the 2017 Verizon DBIR Report.
—

Verizon just released the 10th edition of their Data Breach Investigations Report, and this is one that I always look forward to. Here are the things that stood out to me, along with some comments on them.
Verizon classifies an Incident as a security event that compromises the integrity, confidentiality or availability of an information asset. It defines a breach as an incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
75% of breaches were perpetrated by outsiders.
25% involved internal actors.
I wonder what “involved” means there. Used their access, or there was collusion?
62% featured hacking.
51% included malware.
81% involved stolen or weak passwords.
Not surprising at all. The number is quite high, though.
Around 40% of victims were either financial or healthcare.
66% of malware was installed via email attachment.
This points to phishing as being an extremely powerful vector, which we knew but it’s good to see it reflected here.
Crazy idea: what if people use malware in hacking? Not trying to be snarky, just think we might be able to find better words to make this distinction.
73% of breaches were financially motivated. 21% espionage.
27% discovered by third parties.
21% espionage is interesting. Feels higher than I would have guessed just based on how much cybercrime there is.

This is some great analysis on median click rates for phishing, by industry. The high numbers for manufacturing doesn’t look good for supply chain security.
Finance and retail look to be the primary targets for DDoS.
Healthcare had a massive number of breaches that came from insider misuse.
Ransomware accounted for 72% of malware incidents in the Healthcare industry.
Cyber-espionage was the top motive for attacks against manufacturing
Espionage is also the top motive in attacks against Public Administration.
The vast majority of breaches in Public Administration were state affiliated (90 out of 113).
Retail’s biggest problems are DDoS and POS compromise.
93% of social incidents were Phishing.

Ransom notes are the most profitable form of writing. ~ 2017 DBIR
Web App Attacks resulted in the most breaches, which is expected since they’re facing the internet the most.
Makes sense, right? Web attacks and phishing—both of the things that external entities can touch you with.

Telephone DDoS is becoming more of an issue, evidently.
Summary & Analysis
Another strong report by Verizon. I especially love the industry breakdowns towards the end of the report.
What I’d really like to see a report on is the reasons for the failures. It’s great to know how broken we are, but why are we broken in this way?
We have budgets. We have security teams. I hardly ever go into a company with over 1,000 people who 1) don’t have have a security team, and 2) aren’t massively focusing on the wrong things. As someone said recently, it’s not that we have a talent shortage (necessarily), but instead that we’re mismanaging the resources that we have.
I know many security teams of 10 or 50 or more who are intensely busy—and who could remain that busy for years—but aren’t getting their company’s risk level anywhere near the acceptable level.
Our priority should be figuring out how that’s possible. What forces inside an organization can keep a large security team simultaneously busy and ineffective?
That’s the enemy we must name and face.
Read or comment at Notes and Analysis on the 2017 Verizon DBIR Report.
November 7, 2017
Summary: Coming Apart
For the best reading experience, I recommend you view this content natively at: Summary: Coming Apart.
—
Basic Concept
The basic idea of this book is that there’s a new elite class in this country, and that it’s largely separated from the middle and lower classes in many ways.
These book summaries are designed as captures for what I’ve read, and aren’t necessarily great standalone resources for those who have not read the book. Their purpose is to ensure that I capture what I learn from any given text, so as to avoid realizing years later that I have no idea what it was about or how I benefited from it.
Key Points
Geographically the new upper class lives in clustered areas in and around big cities.
The upper class is largely separated by education and income, and the people with lots of education and high incomes tend to marry others like them, so the effect keeps getting stronger.
Pretty much every social dynamic is better in the upper class areas when compared to the lower classes.
He argues that there are core upper class values that are being maintained to some degree in upper class areas, but not in lower class ones. But he says it’s declining everywhere.
He touches on the IQ differences (on average) between the classes.
He calls out the major difference in parenting styles, where the lower classes basically have kids and assume everything will work out, whereas the rich plan every last detail for their children, starting before conception and lasting all the way until college graduation.
He argues that ultimately it comes down to culture, and that higher culture is the only thing that can save America, and that the lower classes have abandoned the five key values.
These are values that used to be taught in school, to everyone, but now only the rich have them.
He says that the country used to be FAR more similar than it is now.
He says that Europe wants a life of leisure at all times, whereas America understood that life was all about taking on responsibility, having the ability to fail, and constantly striving for more.
This point reminded me of Bertrand Russell, where he talked about struggle and success as the center of happiness.
Read or comment at Summary: Coming Apart.
How to Record a Table Tennis Workout Using the Apple Watch
For the best reading experience, I recommend you view this content natively at: How to Record a Table Tennis Workout Using the Apple Watch.
—
The table tennis option on Apple Watch
I’m an Apple Watch user who loves table tennis, and merging these two is not super intuitive. When you first start the Workout app there is no table tennis option available. Here’s how to make the app more table tennis friendly.
Start a workout type of “Other”.
Play table tennis like normal.
When you finish your workout, end it and then choose the “Name Workout” option.
Select the table tennis option.
You will now have a workout saved as table tennis.
Once you do this once or twice, when you go to do a workout the next time you’ll see the table tennis option available to you as a top choice, so you can select it just like one of the more common workout types.
Enjoy!
Read or comment at How to Record a Table Tennis Workout Using the Apple Watch.
Doing a Table Tennis Workout Using the Apple Watch
For the best reading experience, I recommend you view this content natively at: Doing a Table Tennis Workout Using the Apple Watch.
—

The table tennis option on Apple Watch
I’m an Apple Watch user who loves table tennis, and merging these two is not super intuitive. When you first start the Workout app there is no table tennis option available. Here’s how to make the app more table tennis friendly.
Start a workout type of “Other”.
Play table tennis like normal.
When you finish your workout, end it and then choose the “Name Workout” option.
Select the table tennis option.
You will now have a workout saved as table tennis.
Once you do this once or twice, when you go to do a workout the next time you’ll see the table tennis option available to you as a top choice, so you can select it just like one of the more common workout types.
Enjoy!
Read or comment at Doing a Table Tennis Workout Using the Apple Watch.
I Can’t Do iPhone Cases
For the best reading experience, I recommend you view this content natively at: I Can’t Do iPhone Cases.
—

My Not-yet-broken iPhone X
I really, really tried to keep a case on my iPhone X. Just like the other 9 I’ve tried it with, I lasted 2 days. I just can’t do it. It’s like going to a fine restaurant and putting Vicks under your nose while you eat. What’s the point?
Some good things are just fragile, and I’m ok with that. If I drop it, and it breaks, I’ll pay the fee to fix it or replace it. What I won’t do is only experience half of the enjoyment of the device—permanently—just to keep it safe.
It’d be like moving to San Francisco, paying crazy rent, and then not go outside to avoid getting sick.
On an unrelated note, I need to go outside more. With my unprotected iPhone. That I’ll probably drop.
Read or comment at I Can’t Do iPhone Cases.
November 6, 2017
Unsupervised Learning: No. 100
For the best reading experience, I recommend you view this content natively at: Unsupervised Learning: No. 100.
—
This is episode No. 100 of Unsupervised Learning—a weekly show where I curate 3-5 hours of reading in infosec, technology, and humans into a 30 minute summary. The goal is to catch you up on current events, tell you about the best content from the week, and hopefully give you something to think about as well…
This week’s topics: Russian IW memes, POTUS Twitter, Texas Attack, Silence Trojan, NotPetya Damages, tech news, human news, ideas, discovery, recommendations, aphorism, and more…
Listen and subscribe via…



Read below for this episode’s show notes & newsletter, and get previous editions…
Security news
We're finally seeing a clear picture of the various influence campaigns that Russia are using against the United States. Note that I said "are using", not "were using". This is ongoing. A number of researchers have identified the social media accounts being used and are tracking the memes that they're putting out. The content is brilliant in its ability to capture American identity politics, our various social pressure points, and then use that content to make us fight amongst ourselves. This is literally a state-funded attack against America designed to make us hate each other and destroy ourselves from within. Utter genius on their part. Link
The president's Twitter account was deactivated by a rogue employee as their last action before leaving the company. This raises a number of important questions about the ability for Twitter employees to change things within the platform, e.g., could they tweet as someone else? It's an interesting question when you have people like the president using the product, and there's an assumption that he's actually the one writing the tweets. Imagine reading "I've just declared war on North Korea.", from his account. Would it really be that unbelievable? And what response could the tweet product on its own? Link
A white, former Air Force man went into a church on Sunday near where he grew up and killed 26 people with an AR-15. When he left the church an armed citizen fired on and injured the attacker, who was found dead in his crashed vehicle later. There are myriad issues to discuss here, but the one I'll mention is that many will want to label this terrorism just like they did in the New York attack last week. The difference (so far in a developing story) is that in the New York attack there was a clear modus operandi linked to terror, and the proclaiming of Allahu Akbar during the attack, whereas with this situation we appear to simply have another mentally ill person with no obvious motive. Mental illness based violence is not terrorism because it has no political goal it's trying to achieve. Link
Researchers have discovered a new trojan called Silence in some banking institutions. The MO is to stay silent for some extended period of time to learn more about the network, and then to start stealing money once they believe they can do it successfully. Link
Merck told financial analysts last Friday that NotPetya cost them at least $310 million dollars in Q3, and likely that much again Q4. Maersk lost around $300 million as well, as did FedEx. This makes NotPetya probably the largest cybersecurity incident of its kind. Link
The Trump Organization appears to have been compromised by some Russian hackers in 2013. Multiple subdomains were registered under domains it owned, and many redirected to IP addresses in St. Petersburg, Russia. This could have simply been a Russian criminal group, however, and not anything state or politics related. Either way, it's not good. Link
A fake version of WhatsApp has been installed by over a million Android users. Link
Code signing of malware is evidently more common than we thought. Link
Patching: WordPress, Tor
Technology news
Bitcoin crossed $7,000. Link
HP is selling its main headquarters in Palo Alto and moving to Santa Clara, San Jose, and Milpitas. Not sure exactly what it means, but it definitely means change. Link
Cisco is bringing AI to its conference room meeting hardware. Link
Human news
A massive new study of 600,000 people shows that long-term aspirin use significantly reduces many types of cancer risk. The reduction numbers are staggering: 47% for liver, 47% for esophageal, 35% for lung, 38% for gastric, etc. I really want to see this study get reproduced or otherwise validated. Link
You can now order CRISPR kits through the mail, and hack DNA at home for around $100. Experts say there are way easier ways to do harm to someone, and it'd be pretty hard to modify pathogens to become more dangerous. But my problem with this is that it only takes one. And there seems to be no shortage of people willing to harm thousands or millions. Link
China has opened 516 Confucious Institutes around the world, where they teach the world to speak Mandarin. They are in 142 countries, 42 of which are in Africa. Link
The New York Times is on pace to become a $900 million dollar digital business by 2020 thanks to a major surge in its subscribers in recent years. Much of the increase is being attributed to people being willing to pay for high quality news in a world where it's hard to tell good information from bad. They currently have around 2.5 million paid subscribers. Link
Ideas
November 5, 2017
How Russia is Helping America Destroy Itself
For the best reading experience, I recommend you view this content natively at: How Russia is Helping America Destroy Itself.
—

by Andy Denzler
Maybe Putin is trying to get Trump elected so that he’ll be able to play the role of international savior from the (then obviously evil) US. And in order to do that, he’s collecting as much as possible that he (or someone else) can use to harm Clinton during the election.
Source: Why is Russia Trying to Get Trump Elected?
This is what I wrote back in August of 2016—before all this Russian conspiracy stuff was being taken seriously by anyone but those with some intelligence training. The InfoSec community was particularly bad—perhaps because they were rather Trmp leaning behind closed doors—and essentially saying that only stupid people blame Russia for anything. The argument is that Russia and North Korea are catch-alls for incompetence. So if you got hacked because you don’t know how to defend your organization, but you don’t want to take blame, just say it was Russia!
This is no doubt happening, and the community is right to oppose that mentality, but the problem is that the feeble-minded are extending that somehow to mean that Russia is never to blame for anything. Which is a curious position to have when the country’s basically being run by experts in information warfare.
Anyway, coming back to the present, last week we just learned an extraordinary amount about the nature of Russia’s involvement. A number of anonymous researchers have identified some key social media accounts and then mapped those accounts to the campaigns they have created and disseminated through various social media networks.
The ads they created are staggering in their genius. They jab stiff fingers into the exact pressure points that can turn America into an enraged and unthinking animal bent on self-destruction.
It’s like Russia has mastered the art of Social Lupus, and they’re spreading it within America until it destroys itself. But there’s no way to understand the depth of what I’m talking about until you see the types of campaigns they’ve created.










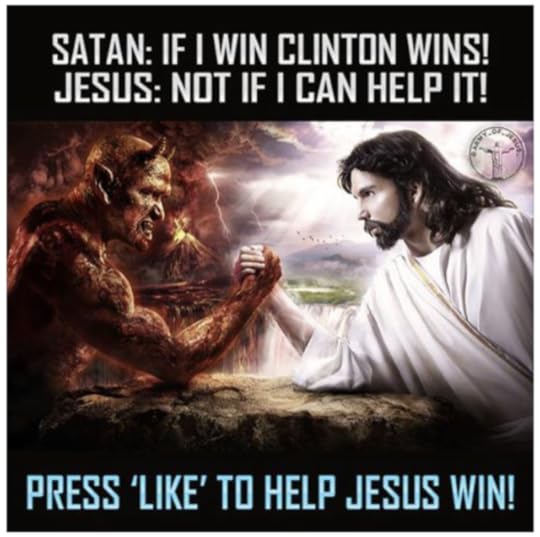





These are the pressure points for internal strife in America. They already have people angry. All the Russian campaigns are doing is identifying them, capturing them in short and sharable memes, and then spending money to make sure they get injected and magnified among the population.
As someone who’s been a student of this type of thing in the past, I cannot help but admire it. It’s seriously great work.
I’d go so far as to say the election of Trump had to be the one of the most effective intelligence campaigns in modern history.
But, as I’ve said multiple times here, Russia isn’t starting this problem: they’re just magnifying it. Exacerbating. Poking the bear. Instigating.
Hey, did you hear what they said about your mom?
That’s the technique. And wow, it worked. Not trying to disrespect the negative effects that have come from this, but I honestly can’t help but appreciate the perfection of this campaign.
But unrelated to Russia, but very much related to the fragmentation of America, I’ve been reading a few books about how America used to be unified in the 60’s, and how it’s becoming more and more soloed now—especially in terms of how the new upper class is breaking away from the middle and working classes.
The books I’m reading are Coming Apart, The New Urban Crisis, and BoBos In Paradise. They all walk through the relatively recent changes in America that are taking us from a single group with a unified set of goals and ideals, to a massive set of peoples who have very little in common.
What fascinates me is how this fragmentation and the Russian instigation of strife internally are very much related. Not tactically, but at the narrative level of disintegration of America.
Basically, we all used to be Americans. Different. Some rich, some less rich. But all were industrious. We valued honesty. We valued morality. There were major social issues with race to be sure. But we were (mostly) one America.
And now we’re just fragmenting. Busting into pieces along the lines of surgical identity politics. That’s what the campaigns above are: they’re sets of things that appeal to specific identity politics groups. They explicitly create the feeling of us and them.
And it’s not just America. The same thing is happening in Europe. In Canada. All over.
As I wrote about in Maybe the Current Trend for Society is Fragmentation, I think this is just the current mode the world is in. Thomas Piketty said in his book that the natural tendency is towards income separation, and that the only things that bring the classes together are major events like wars.
So which are we hoping for? More income disparity or a war to fix it?
Summary
Russia executed the move of the century in helping to get Trump elected. It was sheer genius on their part.
The strife they took advantage of was already there; they just magnified it.
I highly recommend you take a look at some of these campaigns and that you read these books that talk more about the class separation that’s been happening for decades.
Notes
Coming Apart is the book by Charles Murray mentioned above.
The New Urban Crisis talks about how big cities are shutting everyone else out.
BoBos In Paradise talks about the new upper class.
Capital in the 21st Century is about how wealth distribution has moved over time, and how we can expect it to keep separating until we have a war.
This resource collected the various Russian accounts and campaigns in one place.
Hamilton 68 tracks Russian influence on Twitter.
This NYT piece takes a nice sampling of these campaigns as well.
Read or comment at How Russia is Helping America Destroy Itself.
Daniel Miessler's Blog
- Daniel Miessler's profile
- 18 followers





