Febin John James's Blog, page 12
October 31, 2017
Publications by Dominic Dixon
 I’m a Teenager, plz understad me!
I’m a Teenager, plz understad me!Teenagers are the biggest casualties of the pressures of life. The Adolescent phase of life is the most critical phase in a human being. This is the time that they are in search for an identity and all that they gather in life — the philosophy, the worldviews, the moral values, will colour their attitude during young adulthood.
Adolescents are like glass: fragile and need to be handled with care. Teenagers have a special need. They need their parents with them to walk with them through this stage of life. If they miss out on the reassurance of parental love at this stage, it becomes very di cult to rectify their behavioural patterns later as this is the moulding period. They are in search of an identity.
“I’m a Teenager, plz understand me! is a cry from the recess of the heart of all today’s youth. What Dr. Dixon says is essential as this book focuses on the deepest human problems that challenge ‘Today’s Teens.’ Nothing is more moving or more enlightening than way the author has used his life experiences to open up new vistas of hope and healnig for the youth in the slave camps of despair…” Mrs. Wand Paul, Frist grade teacher of Dr. Dominic F Dixon
Can a Utilitarian respect rights?Utilitarianism plays fast and loose with God’s commandments by incting the Utility theory of “greater happiness for the greater number — GHGN”. If lying, stealing, or killing could lead to an increase of happiness for the greatest number, Act Utilitarianism says we should lie, steal or kill. Isn’t that a rejection of Gods commands? Utilitarianism is a secular alternative to Divine Command theory; therefore, the concept of Utilitarianism seems to be on borrowed ethics which is post facto, not rational or reasoning. According to classical utilitarianism, the sole moral obligation is to Maximize utility (= happiness = pleasure
PAPER TO THE HON’BLE PRIME MINISTER OF INDIAJust as any movie would have a script writer, a director and actors; it is the same with the pornographic industry. As there are genres in the media industry; the same exists in the adult entertainment industry too. One such type of audience and consumers are those with sexual fetishism to view child pornography. However, while our government prohibits and bans child pornography, the pornographic industry is currently beating the Indian system– simply by portraying young boys and girls as little children — consequently insinuating child pornography.
Pornogr@phy and its devastating consequences on the Youth & Women in the Nation of IndiaA research paper by Dr. Dominic Dixon, for the Government of India. This paper proves that pornographic use is addictive and has contributed to rape and molestation in India. This paper also proves that brain function deteriorates when watching porn.
MORAL ABSOLUTISMIn this world of sophisticated secular philosophy, we still debate on what is right and wrong and we debate on the metaphysics and the epistemology of morals. Perhaps our sophistication is not in line with ethics of the absolute thought but of a superficial and self knowledge, subjective and convenient understanding of morality.
DEALING WITH PORN ADDICTIONIn this eye-opening interview, Dr. Dixon shares his welath of knowledge in this area to help us understandthe addictive dangers of pornography and the devastating effects if has on us as a nation.
Theology of the body and sexual integrityA research paper by Dr. Dominic Dixon, presented to the Catholic Church for use of the Marriage Preparation Course in the Family Commissions and amoungst Youth Groups. It deals with the matiral fidelity and fidelity to the union of Church to Christ.
INDIA: A country of particular concernIS AN INEFFICIENT GOVERNMENT CONSIDERED CORRUPT?
To a civilian, it’s not about a political party but about the effectiveness of the “serving” government. Regrettably, in India an admirable statesman could morph into a questionable politician because of the unwritten corruptive dictum of the “ruling” party. India has seen almost a dozen former Chief Ministers either prosecuted or convicted for corruption.
This is injustice and injustice is an obstruction of justice according to the United Nations Convention Against Corruption (UNCAC). (UNODC Chapter III Articles 15–24): this act may not be considered as a criminal offence according to domestic legislation, but is “Quiet Corruption’ and is an act against human rights.
The Beautiful Christian mindDeliverance from mental illness.
This book is based on Biblical principles and values that Christ and His Apostles have imparted unto us. It is with the integrity of my understanding and experience as a deliverance minister of Biblical context I proclaim that we can be healed of our infirmities through the divine healing of Christ our Redeemer.
The Beautiful Christian Mind may be used as a tool that dwells on the healing touch of God based on Biblical principles. This book is about the mind and the matters of the mind. It explores the deepest, highest, grandest purpose of the mind. It explores the boulevards and depths of dealing with the ailing mind. The book presents the
effects of God’s mercy that produces a throb of the heart greater than you have ever experienced or have ever known — a reason so profound that no one and nothing else even comes close to — HIS UNFAILING LOVE!
Published by ATC Publications, endorsed by the Vice Chairma of Exorcism of the Vatican, realsed by Archbishop Bernard Moras and presented at the Asian Mission Congresss in Thailand.
Released by Auxiliary Bishop Sproxton of Perth, Western Australia.
Living for the Audience of One!Flawed. If there is one word that aptly describes the human race and human nature, this is it. Those of us who are given to introspection of even the remotest seriousness will attest to the truth of that statement, discovering as we do the numerous abrasions and inclusions in our psyches. Even those among us who shine with the brilliance of diamonds are like some of the stones: perfect to look at unless examined closely. Yet, perfection is what we are called to. “Be perfect,” Jesus said, “as your heavenly Father is perfect.” (Matthew 5:48) The question is: How does one attain perfection?
This book that you hold in your hand contains many such lessons. Dr. Dominic Dixon still has a long way to go to becoming a perfect saint, but he has made remarkable progress on his journey there thus far. It hasn’t been an easy journey — it never is — but his ourage and resilience in the face of difficulties is inspirational, and the insights that he has discovered along the way are profound. He shares many of these experiences and insights in this book, which is a wonderful combination of personal testimony, Scriptural reference and human psychology. It will be a useful guide, not only for those eager to grow spiritually, but also to those who want to pursue the Call in public ministry. Aneel Aranha, Founder — Holy Spirit Interactive
A Journey to Holiness!Dr. Dixon’s book on “A Journey to Holiness” is a reflection of his personal journey to holiness. Knowing him for over a decade and being his spiritual elder brother, I can say with confidence that he has been striving to walk with God and this walk has not been easy for him and it is never easy. The gate is narrow. On this journey that he has embarked on, he echo’s God’s voice to the Church as Prophet Elijah did. This book will surely help every Man and Woman on their journey to holiness. Simon Rodrigues — Chairman — Bangalore Catholic Charismatic Renewal Services (BCCRS)
“Suppose that God wishes to fill you with honey [a symbol of God’s tenderness and goodness]; but if you are full of vinegar, where will you put the honey?” The vessel, that is your heart, must first be enlarged and then cleansed, freed from the vinegar and its taste. This requires hard work and is painful, but in this way alone do we become suited to that for which we are destined”
POPE BENEDICT XVI — SPE SALVI

Publications by Dominic Dixon was originally published in Dominic Dixon on Medium, where people are continuing the conversation by highlighting and responding to this story.
October 4, 2017
How to Protect Your Password from Artificial Intelligence

In my previous story How Artificial Intelligence Can Be Used For Password Guessing I have explained how AI can outperform password guessing tools. In this story I will talk about how to make a strong password, that is AI proof.
Just to reiterate the story
Since humans are predictable , we can see patterns in leaked passwords. Hackers can write rules for password generation using these patterns. Later, performing a dictionary attack will help in cracking the password. Group of researchers recently used neural networks to find these patterns and generate passwords. Hence made the process completely automated. They outperformed traditional password guessing tools.
So how do we make a password that cannot be guessed by AI ?
Don’t use first name, last name, interests, etc
Whenever you use social media, you leave a digital footprint. AI can analyse your public posts to find your interests. If you have used names of celebrity crushes or the cars , bikes you like etc. There is a good possibility that you are vulnerable.
Don’t use common phrases as passwordsSome people use bible verses or commonly spoken phrases as their passwords. This will be a part of the dictionary and can be cracked easily.
Avoid Leet Speak PasswordsPeople try to substitute letters in a word with numbers or symbols to avoid dictionary attack (like I10v3f0rd). But neural networks can generate such passwords studying leaked dictionaries.
Use a password generator/managerI would suggest solutions like LastPass which can generate and store your passwords. Make sure you access such solutions with two-factor authentication.
Code a secret phraseI would still suggest using a password generator. However, if you want to make a password that can be remembered, then use this technique. Write a memorable event of your life in two sentences (Make sure no one knows’s about it).
“The year 2013 was hard. Luckily, I was supported by my good friends Anand and Naresh.”
Now take the first letter of every word, keep numbers or symbols as it is. Combine them. Here is the password Ty2013whL,IwsbmgfAaN.
Check the strength of your passwordUse password strength checker to find out how strong your password is. Make sure you do with tools that support offline mode like How Secure Is My Password.
Use different passwords for different accountsThe problem with using same passwords on multiple accounts is that. If one service gets hacked and the passwords are leaked. This would comprise your other account too.
Use two-factor authenticationTry using two-factor authentication as much as possible. So even if your password is compromised, the hacker won’t be able to log in. Though some suggest two-factor is insecure, this is still our best bet.
Follow Hacker Noon and me ( Febin John James ) for more stories.

How to Protect Your Password from Artificial Intelligence was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
September 24, 2017
Fight The Blue Whale

As you are aware, the deadly blue whale game has claimed lives of many teenagers. Cops suspect an active number of teenagers are still playing the game. During my recent interview at News9, I had the opportunity to connect with a few child rights activists and child psychologists. They mentioned their concern of lack of awareness among parents about the dark side of the web. I wrote a book( Fight The Blue Whale ) to raise awareness on the blue whale game. You have an option to purchase the book or read it for free. You can read the entire contents of the book here or optionally purchase it from Amazon .
A bunch of motivated people working together can accomplish great things. The Internet is a powerful medium which helps the same. It makes collaboration, communication, and distribution easy and fast. Unfortunately, the intent can be good or evil. The Blue whale game is a result of such evil intention, built and managed by a group of sociopaths or psychopaths.
“There are people, and there is biological waste. Those who do not represent any value for society. Who cause or will cause only harm to society, I was cleaning our society of such people. It was necessary to distinguish normal from biological rubbish.”
- Philipp Budeikin, Inventor of the Blue Whale game
Philipp Budeikin was a former psychology student who was expelled from his university. The game is psychologically designed to make the player suicidal as he/she progresses. It involves a list of 50 tasks like watching horror movies, cutting yourself, uploading a naked picture of yourself and finally taking your life.
The game is also known as
1. A quiet house
2. Silent house
3. A bunch of Wales
4. A bunch of Whales
5. Wake me up at 4.20 am
6. A sea
The game is not publically available. The administrators of the game strictly control the access to it. It is played using social media platforms, and teenagers with low self-esteem are the targets. The predators watch out for potential targets on social media and invite the player by sending him/her a link (In some cases the link is shared by peers of the victim on WhatsApp). When he opens the link he starts getting messages from an administrator of the game, who asks to give away his personal information, which is later used against him. They promise to ‘help’ them. They actively communicate with the victim during the game. At any point, if the user expresses the desire to quit, he is blackmailed. They threaten to kill his/her family or release their naked photos. The game originated in a Russian social media website in 2013. It claimed the first death in 2015. Based on a few reports the game is the reason for more than 200 suicides around the world.
Though the creator of the game was arrested, various groups have been formed and are taking the idea forward. This makes it difficult to stop. However, we can take action to ensure the safety of our loved ones. I will discuss these in detail in the upcoming chapters.
Questions & Answers
I am a victim; I am afraid if they will hurt my family?
Please contact suicide helpline of your respective country. If you are from India, Fortis Hospital has launched a 24x7 helpline (8376804102) for anxious parents and youngsters.
How do I protect my kids from such suicidal games?
Please turn to Chapter 4: Protecting Your Child.
What happens if someone doesn’t complete the blue whale challenge?
Nothing. They will scare you with continuous threats. Report to the cops / cyber crime cell.
Why can’t the government ban the game?
The word ‘game’ often makes us think it’s a graphical one or a software application that shows you a list of tasks to complete and credits you with badges and level ups. In the case of the Blue Whale, it is not. Instead, you are communicating with a person on the internet who gives you a list of tasks to complete. Now banning the game means eliminating the communication with such predators. These people mask their internet address and change them frequently. Out of the billions who use the internet finding and locating these predators who hid in the dark web is difficult. Even if few got caught, other psychopaths/sociopaths take the idea forward.
Why would someone play the deadly game?
Teenagers are the targets of the game. The rational part of a person’s brain is not fully developed until the age of 25. Their decision-making is a work in progress. Psychologists claim they often seek validation and have thoughts like “If I do something daring, people will respect me.” The predators of the game target such people and give them a fake sense of achievement for completing tasks involving self-harm.
How can we prevent from further Blue Whale tragedies?
Turn to chapter 5: Fight the Blue Whale.
What happens when you complete the Blue Whale Challenge?
You die.
What benefit do the predators get by taking so many lives?
A recent report mentioned broadcast videos of suicides are sold on the dark web for Bitcoin (A digital currency that supports anonymous transactions).
Around 1995, Ian Clarke from Edinburgh university created a new method of using the internet without detection for his thesis project. In the 90s, the internet could be monitored easily. He wanted to prevent such intentions. He got a B for his work.
In 2000, Clarke publically released his software. Now popularly known as Freenet. Millions of copies were downloaded and distributed around the world. In some countries, the website to download the software was blocked, but those users could get it from their friends. The software is so powerful that it not only hides the identity of the user using it but that anyone is using Freenet at all.
If you think Google gives you everything on the web, you are wrong. Search engines do not index a lot of web pages on the internet.
In other words, you can’t get access to these sites using conventional search engines like Google, Bing, etc. These pages lie in the deep web. Imagine an iceberg; you only find a part of it on the surface. Most of it lies below the surface of the water. Likewise, 90% of the information on the internet lies in the deep web. There is an attempt being made to plumb into the deep web. However, this would be impossible because there is too much data and it blocks an address if it tries to get too much information.
Dark web forms a part of the deep web. Dark web, unlike the deep web, requires you to have proprietary protocols or special software(like Freenet) for access. The websites hosted here are anonymous, so are the users who access it. The communication between the users of the dark web is highly encrypted which allows people to share information confidentially. Hence it’s the perfect place to carry out illegal activities such as drug trafficking, arms trade, child trade, etc. In 2013, a teenager died after consuming drugs purchased from Silk Road(Drug Trafficking Web Site). Everything you find on the dark web is not illegal.
So what is the connection between blue whale challenge and dark web? Self-harm groups long before blue whale came into existence. Blue whale game is the only one which has come to light. The administrators of the blue whale game are found selling the suicide videos of blue whale victims in the dark web.
On August 2017, a teenager got arrested who is accused of being one of the administrators. I suspect the administrators are trying to brainwash other teenagers to be criminals by being an administrator of the game. So even if they arrest a few people who are creators of the game, the idea they put outside is spreading like a virus infecting minds of other teenagers which makes it difficult to stop.
A teenager surfing the dark web is also vulnerable to be a prey of such criminals. In the dark web, criminal activity such as hacking is incentivized through Bitcoin. They can use the hacked information for crimes like trafficking or murder. Teens who find it easy to learn such things have a high possibility of accepting such tasks. This makes them a part of the criminal activity. The Internet is a powerful tool. Giving unrestricted access to your kid is dangerous.
Engineered to Be AddictiveIn the digital age, following are the types of addictions
1. Web Surfing Addiction
2. Device Addiction
3. Cyber-Sexual Addiction
4. Cyber-Relationship Addiction
5. Gambling or Shopping Addiction
Most apps and games on your phones are engineered to be addictive. Games nowadays have no end. Social Networking sites like Instagram, Facebook leads to an infinite feed when opened. They trigger a notification to pull you back into their app. Your time is their money. They have hacked your habits. The habit of brushing one’s teeth while waking up is changed to checking notifications.
Here are some signs to check if you are addicted
* When someone tells a joke, you say “lol”
* You use the phrase “hashtag” in your typical conversation like #FAIL.
* You experience phantom vibrations ( You feel the phone is ringing or vibrating when it is not)
* The first thing you do when you wake up is to reach out to your phone
* You make sure your followers ‘like’ the food before you taste it.
It’s mostly like you relate to at least one of these. Teenagers are more vulnerable because they feel pleasure or pain more intensely than other age groups. This is the reason why they seek for social approval. Their peers highly influence their decision. Social Media provides them with a constant supply of such social rewards from their peers. Blue Whale game utilized this to lure teenagers.
There were several games before Blue Whale by which teenagers tried to impress others
Pass-out Challenge
Youngsters choke themselves out to the point of passing; then they post these recording on social media.
The Aerosol Challenge
British teenagers filmed themselves holding the spray a few inches above the skin. They press and hold the aerosol as long as possible and try to outdo their peers to show who can endure it the longest.
Fire Challenge
People spray themselves with flammable liquid and then setting the liquids aflame. These acts are recorded and posted on social media.
Check if your child
* Is drowsy in the morning, because the challenge involves waking up at 4.20 AM
* Has any hurt marks on the body especially arms
* Started watching horror movies recently
* Updates social media with negative status
* Withdraws from friends and family
* Has drifted away from a hobby they liked before
Some of these signs are common in teenagers, so this can’t tell for sure if he/she is playing the blue whale game. But there is a possibility.
These are the two measures I suggest to prevent the child from playing such suicidal games.
1. Enforce positive habits
2. Enable Usage restrictions / Content Filters
Enforce positive habits
When I was 15, I used to play a lot of video games. One evening, my dad observed this and asked me “Why do you waste time playing this? Instead, can you learn to build the software I use?” This question changed my perception from the computer as a tool for playing video games to creating things that can solve people’s problems. This inspired me to become a programmer. You are reading this book because of the idea my dad put in my head years ago.
Your kid is undoubtedly gifted with one or the other skill. MBTI test will help in identifying them. Encourage them, more importantly help him/her add value to others. This way you will not just prevent them from playing suicidal games but shape them as a person of immense value to the society.
Kids are highly impacted by the kind of content they consume. Children who play violent video games are more likely to have aggressive thoughts and feelings. You should be gifting him/her a couple of good books instead of video games. Practically this seems impossible.
Enable Usage restrictions / Content Filters
The problem with giving restricted access to the device is, kids these days are smart. They will find a way to unlock them. Even if you keep the device away, he/she will easily find other means of access. I would suggest keeping a watch over the teenager while he uses the device. If that’s not possible, you can take the following measures.
On IOS
1. Tap Settings > General > Restrictions.
2. Scroll down and tap Restrictions, then tap Enable Restrictions.
3. Create a Restrictions passcode. You need your Restrictions passcode to change your settings or to turn off Restrictions.
Here you can restrict existing apps or enable download only for the content of selected rating.
4+ — Applications: No objectionable material.
9+ — Applications: May contain mild cartoon, fantasy or realistic violence, and infrequent or mild mature, suggestive, or horror-themed content
12+ — Applications: May contain infrequent mild language, frequent or intense cartoon, fantasy or realistic violence, and mild or infrequent mature or suggestive themes, and simulated gambling.
17+ — Applications: May contain frequent and intense offensive language; frequent and intense cartoon, fantasy or realistic violence; and frequent and intense mature, horror, and suggestive themes; plus sexual content, nudity, alcohol, tobacco, and drugs.
On Android
1. Open PlayStore
2. Pull the navigation drawer on the left
3. Scroll down, tap on settings.
4. Go to parental controls, turn it on by toggling the button
5. Set content restriction as per your requirement.
The Android Operating system is easy to hack around. Setting parental controls might not be enough. Here are a couple of tools which can give you more control and monitoring capabilities.
Qustodio
They give you a dashboard for social media monitoring, setting time limits for internet usage, games or apps and even the ability to track calls and messages.
Family Shield from OpenDNS
OpenDNS bans adult websites and sites with violence; they keep updating their list often. This tool can even ban proxy servers which kids use these days to get around parental controls.
Kidlogger
Instead of blocking sites, this helps you to keep an eye on what your child is doing.
In India, suicide is the leading cause of death among youngsters. There is evidence that social media and internet can influence suicidal behaviours. The quantity of content posted on the web every minute is enormous. Manually keeping a watch over what a billion users post online is impossible.
Facebook has developed an algorithm that finds warning signs in user’s post. It is then sent to a human review team who tries contact the post’s author and provide them a way to seek help. Presently, this is only available in the US.
Other social media services are working on such measures. But, they can only do that to a certain extent. For Ex: If the government asks messaging platforms to remove links on the blue whale. Searching messages between people, even though done by a machine is an act of invading user’s privacy. Privacy activists might have a problem with it. However, doing this in the dark web is impossible.
When you feel cold you wear a jacket; you don’t expect NASA to build a system that can regulate the temperature in the places you like to go. Likely, I would suggest installing safety software in the devices. Regulating the internet is not going to happen anytime soon.
The first step is to spread awareness. There are a few who still think that the blue whale game is a hoax. Most parents don’t even have a clue that parental control exist on their phone. The reach of this book is pretty limited. But I expect the reader to spread the message among his/her family and friends. You are free to use any content in this book, in any manner with no attributions necessary. Probably you should try explaining these over a video of few minutes in your native language and share it to among your friends on social media.
Schools must be enforced to educate kids and parents on the safe use of Internet. I have seen parents and teachers shouting at the kids with “Don’t do ____” statements. The problem with kids these days is they roam around with “Who are you to tell me?” attitude. Those don’t work on them. Instead, we should try to make them understand the “Why” of things. Make them conclude that some things are not meant for them.
Follow Hackernoon and me ( Febin John James ) for more stories.

Fight The Blue Whale was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
September 23, 2017
Normal programming languages have a strict syntax.
Normal programming languages have a strict syntax. Though community create libraries which does specific functions, that language itself hardly evolve.

September 22, 2017
Programming without coding

Computers have penetrated into almost every industry; shortly programming will become a mandatory skill in most industries. The new kind of jobs will require people to analyse and plot data, manipulate text, query database, and control internet of things or robots.
Currently, programmers build a layer on top of these systems; a user interface for non-programmers to interact. Since industries advance quickly, rapid changes must be made to these interfaces because they can only do things for which they are programmed. Making these changes is time-consuming and costly.
A better way is, people should be able to interact with the computer directly. Writing code is one way. But writing statements that have to be precise can be tedious, even for expert programmers. For non-programmers, this is not an easy task. Hence, we need an alternative.
Group of researchers from Stanford University may have come up with a way to solve this problem.
https://medium.com/media/2428fcdf926ab2e69919f07d99db3372/hrefVoxelurn allows you to program in the natural language. You can type in ‘add green monster’ to add a monster of color green. You can see the list of commands supported here. But, that is not the best part yet. You can make your definitions. Initially, you will need to know the core language to make things. After that, you can write your definitions. As the computer learns your definition the whole process of programming will become more natural.
I would have written a small tutorial here for your understanding. Unfortunately, their website is having issues. You can go through the above video for a demonstration.
Researchers recruited 70 users from Amazon Mechanical Turk. They were asked to make structures on voxel. The definitions created by these users were shared so that one could build from others definitions.
1.) User A creates a face structure and defines it as “Add a face.”
2.) User B uses the command “Add Face” and makes a hat on top of it. Say “Add a face with a hat.”
3.) User C can use the “Add a face with a hat” definition and probably add body, hands, legs, etc.
The idea is to evolve the language with a community of users over time. As the system learned researchers noticed that users tend use naturalised language more than 85% of the time.
This research is a good step towards a future without code. You can look into the technical details here. Here’s a link to their open source repo.
Follow Hackernoon and me (Febin John James) for more stories. I am also writing a book to raise awareness on the Blue Whale Challenge, which has claimed lives of many teenagers in several countries. It is intended to help parents understand the threat of the dark web and to take actions to ensure safety of their children. The book Fight The Blue Whale is available for pre-order on Amazon. The title will be released on 25th of this month.

Programming without coding was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
September 19, 2017
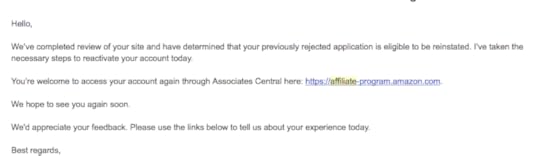
Guo Huang Actually I thought the same.
Guo Huang Actually I thought the same. But I wrote to them, they reinstated the account. Your earnings are preserved. Just write an email , you should be fine. Here is the email I got after it was reinstated.

How Artificial Intelligence Can Be Used For Password Guessing

Password guessing works because …
Humans are predictable
If you ask Mark to set a password. He will simply put it as ‘Mark’. Now the system tells him that his password must contain numbers. He makes it ‘Mark123’. Though you are smart enough not to put such insecure passwords, there are a good number of people who are like Mark.
 Leaked passwords from Rootkit
Leaked passwords from RootkitYou can see patterns in leaked passwords. Most of them might is a combination of one or more of first name, last name, birth date, or favorite entities (names of car, bike, actor, actress ,etc).
Password guessing tools like HashCat or John the Ripper commonly use dictionary attack with password generation rules to guess the password. Dictionary attack is simply trying the words in a dictionary one after the other as password inputs to see which works out.
Dictionary attack with password generation rules is done by manually going through a list of leaked password and making rules for password generation. For Ex: If leaked passwords are found to be a combination of an entity and 123 say ‘ford123’. Then concatenating 123 to the dictionary words is a generation rule.
In password guessing tools these these are defined manually or in other words they are human defined rules. The problem with such rules is human behaviours and interests change over time. So these rules must be updated often (As more leaks happen). Also when the list of leaked passwords is huge, finding patterns manually would be a difficult process. There are good chances some patterns go unnoticed.
This is where the role of Artificial Intelligence comes in. Few researchers recently trained neural networks with datasets of leaked password and were able to generate passwords that outperformed popular tools like HashCat and John the Ripper.
If the term neural network goes over your head, just think of it as computer process which can replicate how humans learn. Humans learn through modelling and observation. If I show you four photos of a person and tell him he is ‘Mark’. Next time you would easily recognise him. Neural Networks helps computer replicate the same .
Researchers used Generative Adversarial Neural Networks (GANs) to implement this. GANs consists of two neural networks. One neural network for generation and another one which gives feedback. Think of it as a master and student. A student tries to do something and the master gives feedback saying ‘You need to try more’ or ‘You are close’ etc. These neural networks run multiple iterations untill it get satisfactory results.
This makes the process completely automated. Researchers also observed that though in some cases the neural networks were unable to match the exact password, the generated one looked like the given password. For Ex: if the password was ‘AEF@123’ the generated one was ‘A3F@123’.
On the bright side, we can use this to make password based systems more secure by identifying weak or predictable passwords. If you would like to look into the technical details , here is the research paper A Deep Learning Approach for Password Guessing.
Follow Hackernoon and me (Febin John James) for more stories. I am also writing a book to raise awareness on the Blue Whale Challenge, which has claimed lives of many teenagers in several countries. It is intended to help parents understand the threat of the dark web and to take actions to ensure safety of their children. The book Fight The Blue Whale is available for pre-order on Amazon. The title will be released on 25th of this month.

How Artificial Intelligence Can Be Used For Password Guessing was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
September 18, 2017
This could be ads, however do check if you have the same issue while browsing with browser…
This could be ads, however do check if you have the same issue while browsing with browser extensions disabled (Incognito mode). This could be an issue with an extension. Not sure though.

CCleaner compromised, your computer could be infected

Group of researchers from Cisco Talos recently reported that CCleaner App v5.33 which was available for download between August and September came with the Floxif malware.
The Floxif malware collects information such as computer name, installed softwares, etc and send it back to the hacker’s server. This also has the capability to download and run other programs like key loggers . Millions of systems are suspected to be compromised.
Researchers identified the app was making calls to suspicious domains. Normally, this would happen when the app is download from an untrusted source. However, in the case of CCleaner, the installer was obtained from the official site and was signed by a valid digital certificate. This makes the situation even worse because, the development or signing process of the company seems to be compromised.
Don’t panic, just update your CCleaner version to v5.34. This should fix the issue. Only Windows/Cloud offering of CCleaner seems to be affected. If you are on macOS, you should be just fine.
Follow Hackernoon and me (Febin John James) for more stories. I am also writing a book to raise awareness on the Blue Whale Challenge, which has claimed lives of many teenagers in several countries. It is intended to help parents understand the threat of the dark web and to take actions to ensure safety of their children. The book Fight The Blue Whale is available for pre-order on Amazon. The title will be released on 20th of this month.

CCleaner compromised, your computer could be infected was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
CPU mining would be one of the possibilities or it could be just bad code.
CPU mining would be one of the possibilities or it could be just bad code.




