Practically Paperless with Obsidian, Episode 23: Protecting My Data in Obsidian
Photo by Pixabay on Pexels.com
" data-medium-file="https://i0.wp.com/jamierubin.net/wp-c..." data-large-file="https://i0.wp.com/jamierubin.net/wp-c..." width="900" height="600" src="https://i0.wp.com/jamierubin.net/wp-c..." alt="black android smartphone on top of white book" class="wp-image-21775" srcset="https://i0.wp.com/jamierubin.net/wp-c... 1880w, https://i0.wp.com/jamierubin.net/wp-c... 400w, https://i0.wp.com/jamierubin.net/wp-c... 550w, https://i0.wp.com/jamierubin.net/wp-c... 768w, https://i0.wp.com/jamierubin.net/wp-c... 1536w, https://i0.wp.com/jamierubin.net/wp-c... 1200w, https://i0.wp.com/jamierubin.net/wp-c... 1800w" sizes="(max-width: 900px) 100vw, 900px" data-recalc-dims="1" />Photo by Pixabay on Pexels.comWelcome to my blog series, “Practically Paperless with Obsidian.” For an overview of this series, please see Episode 0: Series Overview.
As I go through the process of migrating from Evernote to Obsidian, I have moved all kinds of notes and documents into Obsidian. Some of these, like tax documents, for instance, raise the question: Is it safe to put sensitive data into Obsidian?
This is nothing new. When I was writing my Going Paperless posts using Evernote ten years ago, one of the most common questions I got was, “But don’t you worry about exposing your data?” The question came in different forms–what if Evernote is hacked? Don’t you worry that Evernote staff can read your notes and documents?–but the general idea was always the same. People were worried about others gaining access personal information and want to know if a tool is safe to use in this regard. I thought I would spend this Episode talking about how I think about data protection and describing some of the tools I use to protect my in the context of going practically paperless with Obsidian.
Layers of a security onionWhen I think of protecting the notes I keep in Obsidian, I think in terms of layers of an onion, with each layer representing one method of protection that I am comfortable with. Each method alone is not perfect. Combined, however, they provide me with enough sense of security that I don’t lose any sleep over the matter. These layers remind me of those doors that Maxwell Smart passed through to get to and from his office each day.
In the case of the data I keep in Obsidian there are three layers of security working together to protect my data: physical access, digital access, and data encryption. I illustrate this as follows:
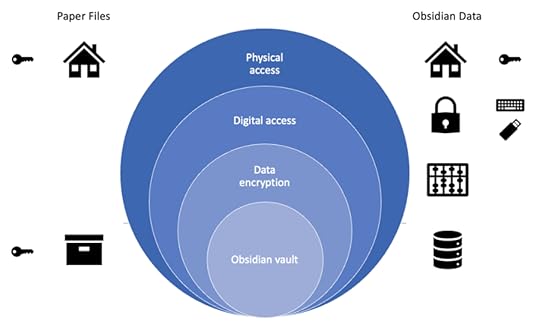 1. Physical access to Obsidian data
1. Physical access to Obsidian dataOne of the big selling points of Obsidian is that data resides locally by default. My Obsidian notes are stored on the hard disk of my desktop or laptop computer. Let’s set aside cloud-syncing services and mobile devices for the moment–I’ll come back to it later, I promise. For now, my Obsidian vault sits in a folder on a hard disk on my Mac Mini, and that Mac Mini sits on shelf in my office.
If someone wants to access my Obsidian notes, they need access to my Mac Mini and that means they need access to my office. Access to my office requires access to my house. This is illustrated in the “physical access” layer in the image above. On the right side, the house represent physical access to my Obsidian data.
Now let’s pretend that instead of storing my notes in Obsidian, I followed Niklas Luhmann’s Zettelksaten model and all of my notes were on slips of paper stored in a slipbox that resided in my office where my Mac Mini currently sits. This is illustrated in the “physical access” layer in the image above. On the left side, the house represents physical access to my slip box.
So far physical access to my notes is identical in either case. A person needs to gain access to my office to get to either the Mac Mini or the slipbox. Physical security of my notes is the same in both cases. I make this point because I sometime hear arguments that people don’t want to store certain types of data in digital form. This is perfectly reasonable. Everyone needs to find their own comfort level. But from my viewpoint, physical security for locally stored data in Obsidian and the same data stored on paper in a slipbox is identical.
Physical security itself can include a number of layers. (1) We lock the door to our house. (2) We may lock the door to our office within our house1. (3) We may have an alarm system installed to discourage an unauthorized breach.
I never lost sleep about data security when most of my files were on paper and stored in a filing cabinet in my office, long before Evernote or Obsidian. Given that the physical security is the same when storing my data locally in Obsidian, I don’t lose sleep over the physical security of my data their either.
2. Digital access to Obsidian dataSuppose, however, that someone managed to breach the physical security layer and was able to sit in front of my Mac Mini2. The second layer of the onion–protecting digital access to my Obsidian data–kicks in.
To gain access to my notes in Obsidian, a person would first need to be able to sign into my Mac Mini using an account that has permissions to the vault. At its most basic level, that means a person needs a password to sign into the computer. Good password practices help here. For instance, I use a different password for everything. Gaining access to one password only gets a person access to one specific device or service. A password manager helps with this. I’ve also made it a practice to use long passwords as they are much harder to crack.
Suppose, however, for the sake of our exercise, that the person who managed to break into my house has figured out my unique and hard-to-guess password for my computer. What then? Just as physical access can have many elements to it (keys, alarms, etc.) so does digital access. In addition to a strong, unique password, I also make use of multi-factor authentication. A password alone isn’t enough to get into the computer. A second form of verification is required. There all kinds of multi-factor authentication: biometric, an authenticator tool, a text message to another device, or a separate device entirely like a YubiKey.
The likelihood of someone breaching my physical security, figuring out my password, and getting past the multi-factor authentication is so small that it really isn’t worth worrying about, at least in my view. Suppose, for instance, that my notes were stored on paper in a slipbox, as my illustration shows on the left side. In this case, the digital access layer of the security onion doesn’t exist. Here, then, is a side-by-side comparison of what someone has to do to gain access to my notes in Obsidian in case, and on paper (slipbox) in another:
LayerSlipbox (Paper)Obsidian (Digital)Physical access1. Access to house (key, alarm code, etc.)2. Access to office
2. Access to slipbox (key?)1. Access to house (key, alarm code, etc.)
2. Access to officeDigital accessNone1. Know my strong, unique password.
2. Have access to my second form of authentication
It would actually be easier to gain access to my data if it were stored on paper in my office than in Obsidian with the vault stored locally on my computer.
3. Data encryptionSuppose our frustrated villain, able to get into my office, but unable to breach the digital security of my computer, decides to just take the computer with them, with the idea off gaining direct access to the data on the hard disk within, perhaps by mounting it on another device. At this point, the scenario is getting a bit preposterous, but let’s just go with it. This is where the data encryption layer comes into play.
The hard disks on my computers are all encrypted using FileVault, MacOSs native disk encryption software. FileVault uses 128-bit AES encryption with a 256-bit key. The data on the disk is encrypted at rest until proper authorization has been granted at which point the data is decrypted. “Proper authorization” in this case means the access required in part 2 above. Without a password and valid authentication from a separate authenticator, there is no practical way to decrypt the data. Our villain would have obtained a computer, but it would be useless to them unless they wiped the drive, in which case, they lose access to the data.
With these three layers of the onion working in conjunction. I feel perfectly safe storing my notes, even sensitive ones, in my local Obsidian vault. The risk of a breach is not impossible, but it is so unlikely that I don’t worry about it.
Syncing notes and cloud securityAh, but what if I want to access my notes from multiple devices? Don’t I worry about someone gaining access to my data in the cloud? I don’t.
For Obsidian data to sync across multiple devices, some kind of syncing service must be used. I have experience with two of these services: iCloud and Obsidian Sync. When I began using Obsidian in January 2021, I used iCloud to sync data between my computer and my iPhone. In that scenario, the data lives on my hard disk (which is still encrypted) is synchronized through the iCloud service to iCloud servers, which in turn synced the data to my iPhone (where the data is also encrypted). Indeed the entire synchronization process is encrypted.
Eventually, I ran into sync issues that seemed to be entirely related to iCloud and I switched to Obsidian’s Sync service. This is a fast, reliable sync service that I setup once and then never had to mess with again. It just works.
There are two models to Obsidian Sync: end-to-end encryption and managed encryption. To ensure complete privacy, I use the end-to-end encryption model. In this model, the data (already encrypted on my hard disk thanks to FileVault) is encrypted when being sent to and from Obsidian’s sync service. It is encrypted at rest on Obsidian’s servers. Best of all, I am the only one who can access the data. The encryption uses a password and Obsidian developers do not have access to that password. The downside of this is that if I ever forget my password, I would not be able to access the vault in the Obsidian Sync service3.
The 3 layers of my security onion still apply even with data stored in Obsidian Sync. Someone would need physical access to the server where the data was stored. They would need digitial access to the data on the server, and they would need a password for decrypting that data. Those three layers of security are good enough for me.
But what about a mobile device?Possibly the weakest link in this chain is my iPhone, and I say it is the weakest link only because it is the most likely place where someone can gain physical access. This doesn’t even have to be malicious. My phone could slip out of my pocket and I might not notice it is gone right away.
Even here, however, the other layers of the security onion kick in. If someone finds my phone, they need to gain digital access to my phone. And data on iPhones is encrypted so direct access to the solid state storage does no good. Moreover, security is set up on my phone so that after a certain number of failed attempts to sign into the phone, the phone will wipe its data, making it useless to anyone who was after the data. Also, I can wipe the data remotely, if I realize the phone is missing and the phone is turned on and able to access a cellular network.
Some additional protectionsProtecting data is more than just preventing unauthorized access to the data. It is also making sure that I have access when I need it. Here are some additional ways that I protect my data (including my Obsidian vault).
1. VPN serviceI use a VPN service to make sure my data is encrypted end-to-end, even when I am on 5G, cellular, or unfamiliar WiFi networks. This way, I don’t have to worry about someone snooping on networks that I have no control over. The VPN service ensures my data is encrypted end-to-end from the moment it leaves my device.
2. Data backupsMy data is regularly backed up. There are local and cloud backups:
I use TimeMachine to continually backup my data to an external disk on my home machines. This allows for quick local restores for times that I make a dumb mistake.All of our computers are also backed up to the cloud using CrashPlan’s Small Business backup plan. This service costs some money, but I look at it the same way I look at paying for insurance. The few times I’ve needed it, it has been there and restored all of my data quickly.In each case, the backed-up data is encrypted and only I can decrypt it.
Finding a security sweet spotIt is one thing for me to list out all of the reasons why I don’t worry about unauthorized access to my Obsidian data. It is another for others to feel comfortable on their own setup. Some people will insist that the three layers I find reassuring are just not reassuring enough. Others will think it is overkill. That’s fine. Everyone needs to figure out their own security sweet spot. Below is a diagram I sketched out for a post on this subject I wrote just about 10 years ago. I’m reusing it here because I think it is as true now as it was then. Given the practical theme of these posts, I might change the “low reward” and “low risk” to “low practicality” and “highly practical”, but otherwise, it stands.
Find a sweet spot you are comfortable with. And remember, you always have the option of not storing something in Obsidian, or in digital form period.
 Summary of Tools and Services
Summary of Tools and ServicesThe table below summarizes some of the tools and service I make use of in each of the layers discussed about. I should point out that I’ve had these practices in place for a long time. They do more than just protect my Obsidian data. They protect all my data.
LayerTools/Services1. Physical accessLock and keySecurity service2. Digital accessStrong, unique password (LastPass for password manager)
Multi-factor authentication (biometric / YubiKey)3. Data encryptionFileVault (128-bit AES encryption with 256-bit key)
Express VPN to ensure end-to-end encryption on “untrusted” networks
Obsidian Sync for end-to-end encryption for syncing Obsidian data between devicesAdditional ToolsTime Machine (MacOS) for local continuous backups
CrashPlan for Small Business for cloud backupsComing attractions
I have covered a lot of ground in the first 23 episodes of this series. A lot of this ground was me exploring the basic principles and functions of Obsidian, and figuring out how to make practical use of them. Over the next several episodes, I’ll be exploring specific use cases — practical examples of how I use Obsidian on a day-to-day basis.
I also wanted to put out a call for suggestions on topics you’d like to see covered here. I can’t say I’ll be able to meet every demand: I tend to avoid writing about situations for which I have no need or for which I have no experience, but I’ll do my best.
Thanks again for reading, and I’ll see you back here next weel.
Prev: Episode 22: Daily Notes Revisited: The Best of Both Worlds?
Next: Episode 24: Use Case: How I Capture Field Notes In Obsidian (coming March 29, 2022)
Written on March 12 and 20, 2022.
Did you enjoy this post?
If so, consider subscribing to the blog using the form below or clicking on the button below to follow the blog. And consider telling a friend about it. Already a reader or subscriber to the blog? Thanks for reading!
Email Address
Subscribe
For those home offices with doors. Mine home office has a doorway, but no door. ↩ Given that my Obsidian data would be completely uninteresting to anyone but myself, I have a hard time conceiving of someone going through the exercise of breaking into the house to gain access, but l’ll go with it for the purposes of this illustration. ↩ Of course, I’d still have my local vault, and any backups I have made ↩


