Secret Messages in Historical Fiction
 Please welcome Pamela Taylor, author of the historical fiction novel, Pestilence. Pamela Taylor brings her love of history to the art of storytelling in the Second Son Chronicles. An avid reader of historical fact and fiction, she finds the past offers rich sources for character, ambiance, and plot that allow readers to escape into a world totally unlike their daily lives. She shares her home with two Corgis who frequently reminder her that a dog walk is the best way to find inspiration for that next chapter. Pamela very kindly divulges the secrets behind the coding of messages, always important in dangerous and uncertain times. But how many methods could one use?
Please welcome Pamela Taylor, author of the historical fiction novel, Pestilence. Pamela Taylor brings her love of history to the art of storytelling in the Second Son Chronicles. An avid reader of historical fact and fiction, she finds the past offers rich sources for character, ambiance, and plot that allow readers to escape into a world totally unlike their daily lives. She shares her home with two Corgis who frequently reminder her that a dog walk is the best way to find inspiration for that next chapter. Pamela very kindly divulges the secrets behind the coding of messages, always important in dangerous and uncertain times. But how many methods could one use?Secret Messages in Historical Fiction
 Secrets are as old as time. As soon as humans realized they could gain an advantage by keeping others from finding out what they knew, they started devising methods to protect their knowledge. And when they needed to share that knowledge with an ally, they began developing techniques to transmit it in secret. Among the earliest were pictographic techniques – either hidden in graphical representation of language or in drawings. Eventually, men developed locks and keys. Secrets could be protected in locked chests or boxes. Over time, the locks and keys grew ever more complex and often included booby traps that could harm anyone trying to break into them. Puzzles could also hide secrets (think complex puzzle boxes that could contain hidden messages or contraband). Karen Brooks’ historical novel The Locksmith’s Daughter includes some nice depictions of these methods.
Secrets are as old as time. As soon as humans realized they could gain an advantage by keeping others from finding out what they knew, they started devising methods to protect their knowledge. And when they needed to share that knowledge with an ally, they began developing techniques to transmit it in secret. Among the earliest were pictographic techniques – either hidden in graphical representation of language or in drawings. Eventually, men developed locks and keys. Secrets could be protected in locked chests or boxes. Over time, the locks and keys grew ever more complex and often included booby traps that could harm anyone trying to break into them. Puzzles could also hide secrets (think complex puzzle boxes that could contain hidden messages or contraband). Karen Brooks’ historical novel The Locksmith’s Daughter includes some nice depictions of these methods.But boxes and chests and paintings and physical things are bulky. What if one needed to send a message that could be easily concealed by the messenger but not easily read if it was intercepted? Invisible writing – using citrus juice or milk as ink – could hide a message which would be revealed only when the paper was heated. Citrus juice or milk might not always be close at hand, though. That’s where coded messages come into play. Encryption (encoding a message) goes back as far as Julius Caesar, who used simple alphabetic substitution. His trusted allies knew that he always used an offset of three, meaning that the letter “D” would be substituted for “A,” so they could decode the message easily while his enemies, presumably, would remain confused.
In the Second Son Chronicles, Alfred (the protagonist) and his grandfather are both students of Roman history, so they know about Caesar’s method. When, in Second Son, Alfred needs to send an urgent message to his grandfather in secret, he encodes it as Caesar would have:Vxqgdb qhaw. Dwwdfn hduob pruqlqj dv phq dzdnh. Wzhoyh phq lq jdqj. Udqxoi, vrqv, vla qhz lq jdqj, Urqdq dqg vtxluh. Doiuhg
He knows his grandfather will recognize the garbled message for what it is and will know how to make sense of it. But what other precautions does he take to make sure his message isn’t intercepted. In Pestilence,Alfred faces an entirely different impediment to communicating with his friends while avoiding the prying eyes of his brother’s spies. His solution may surprise you. As the series progresses, Alfred’s lifelong interest in books and learning will lead him to new discoveries about secret communications. He finds a book from the ninth century by an Arabic mathematician that introduces the idea of polyalphabetic substitution. This concept uses a table like this:
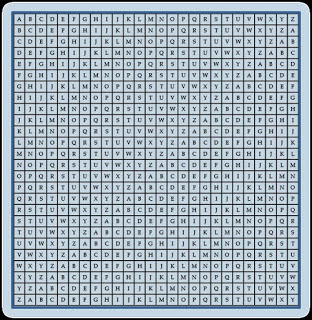 The sender would pick a row and make that the first letter of the message. So if the king wanted to tell all his commanders “Attack at dawn,” he could encode it as: Mmffmow mf pmiz.
The sender would pick a row and make that the first letter of the message. So if the king wanted to tell all his commanders “Attack at dawn,” he could encode it as: Mmffmow mf pmiz.The recipient would know that the first letter represents the row or column to be used for decoding – in this case, “M.” Throw away the first letter and then decode the rest of the message. The lovely thing about this method is that is doesn’t matter if either the sender or the recipient chooses a row or a column for the encoding and decoding. The results come out the same either way. And, just like the Caesar cipher, the sender or recipient can construct the code table when they need it and doesn’t have to carry anything with them that might fall into the wrong hands.
Follow the series to learn how Alfred puts that new knowledge to use and who he shares it with.
Published on July 07, 2020 05:30
No comments have been added yet.



