L.A. Sartor's Blog, page 22
June 10, 2018
R&R: Raves and Rants from Multi-Published Author Amanda Cabot

I'm so pleased that Amanda Cabot is going to be a monthly contributor to this blog. I've always admired her mastery of grammar as I suffer from grammar-itis.Thank goodness we have folks like Amanda around to help us.Take it away, Amanda.
Welcome to R&R. No, we’re not going to talk about rest and relaxation today. R&R is shorthand for “One Writer’s Raves and Rants.”
When L.A. invited me to write a monthly column, she suggested I discuss grammar, perhaps because she knows that I’ve been known to throw books across the room – at least figuratively – when I encounter basic grammatical mistakes. She might also have made the suggestion because she knew I once wrote a column whose original title was “In Defense of the Semicolon.” Even though I suspect most of you are rolling your eyes, wondering if you’re going to be subjected to a discourse on that much maligned punctuation mark, I can assure you that there will be no semicolons … at least not today. Furthermore, as the column’s title implies, there will be more than rants about grammatical mistakes here. I’ll also talk about things that I see other authors doing well. But today, we’re talking about grammar, and I’m going to rant about the misuse of the apostrophe.

I can’t imagine writing without apostrophes. They’re used for contractions and to indicate a word’s possessive case, but – except in one extremely limited instance – they are NOT used to make a word plural. (Did you notice how I used apostrophes in that sentence? Those are the correct usages.)
Now, let’s start the rant. I can’t tell you how many times I’ve seen sentences like the following in published and supposedly edited books. “They’re having dinner with the MacLean’s.”
What’s wrong with that? If this were a book set in Scotland where the head of the clan is called “the MacLean,” the only problem might be that it’s missing a noun at the end of the sentence. Perhaps the author meant to say that someone was having dinner with the head of the clan’s daughter.
Unfortunately, 99.9% of the time when I see a sentence like this, it’s a mistake. A big one. In all likelihood, the author’s intent was to say that someone was having dinner with several people whose last name was MacLean. But our grammatically challenged author didn’t know that the correct way to form the plural of MacLean is very simple – MacLeans.
No apostrophe!
The same rules that apply to common nouns apply to proper ones like names. The plural of chair is chairs, not chair’s. The plural of horse is horses, not horse’s. Why would anyone think that the plural of MacLean is MacLean’s or that the plural of Smith is Smith’s? There’s only one reason I can imagine, and that’s that they didn’t know any better.
What if you were having dinner with several people whose last name is Simmons? How would you form that plural? No, it’s not Simmons’. The answer is Simmonses. If that seems awkward, I agree. That’s why I changed one of my characters’ names from Simmons to something that did not end in an “s.”
We’re almost done. Remember that I said there is one extremely limited instance when an apostrophe is used to create a plural. Do you know what it is? Lowercase letters, but only if the apostrophe is needed for easy comprehension.
Consider the first letter of the alphabet. I doubt anyone would misunderstand, “The child wrote a full line of As.” But what about “a full line of as.” Clearly, you need something to distinguish the word “as” from the plural of “a.” That’s where our helpful apostrophe comes into play. The same thing happens with the letters “i” and “u,” but those are the exceptions that prove the rule.
So, repeat after me. Apostrophes are almost never used to make a word plural .
End of rant.
~Amanda
 A lifetime of reading and writing, not to mention a host of teachers who believed that good grammar was one of the essentials of life, have given Amanda Cabot such firm opinions about the printed word that I asked her to share some with us in her Raves and Rants posts. Although her working career was in Information Technology, Amanda achieved her dream of selling her first novel before her thirtieth birthday and is now the author of more than thirty novels as well as a number of books and articles for Information Technology professionals. Her most recent release is A Borrowed Dream, the second of the Cimarron Creek trilogy.
A lifetime of reading and writing, not to mention a host of teachers who believed that good grammar was one of the essentials of life, have given Amanda Cabot such firm opinions about the printed word that I asked her to share some with us in her Raves and Rants posts. Although her working career was in Information Technology, Amanda achieved her dream of selling her first novel before her thirtieth birthday and is now the author of more than thirty novels as well as a number of books and articles for Information Technology professionals. Her most recent release is A Borrowed Dream, the second of the Cimarron Creek trilogy.Find all of Amanda's books, newsletter info and social media links here.
Tweet
Published on June 10, 2018 23:30
May 24, 2018
Prism Book Tour Featuring Author Jennifer Silverwood's ~ Silver Hollow
 On Tour with Prism Book Tours
On Tour with Prism Book ToursYe Olde English

I’ve always been a big fan of nonsense words, like in Lewis Carroll’s Jabberwocky poem. My first edition of Silver Hollow, I let that flight of fancy go to town. It was fun creating nonsense words for my local “hollow folk” and I felt enriched the experience. Plus, it was fun to confuse my main character. Unfortunately I also managed to confuse many a reader not accustomed to such fiddle-faddle. Thankfully, I had the sense to create a glossary for reference.
Six years later, while my love of language remains strong, my sense of control has greatly increased. So while we still have a few fun nonsense “Hollow” words, there are equally the amount of actual old and middle English thrown amix. I wanted to give you a better sense of realism this time and given the magical setting and history of the Borderlands, I pulled from true history. For your (and my) enjoyment, here are a list of phrases you’ll see in Silver Hollow 2018 with their meaning below:
Beek- to bask in the sun or a warm fire
Bilge Scum- comparing one to the filthy underbelly of a ship
Bellibone- A lovely maiden, pretty lass.
Carked- Fretfully anxious.
Chitty-face- A person with a thin, pinched face; a term of contempt.
Daggle-tail- An untidy woman.
Fonkin – a little fool
Gramercy- Thank you
Hufty-tufty- A braggart.
Kiss the Hare’s Foot - To be so late as to miss dinner; to eat leftover scraps.
Mumper - a beggar, one who sponges off others.
Poplolly- A little darling; a female favorite; or a mistress.
Reaks- Pranks or practical jokes.
Samded- Half-dead
Skive- an old crone’s tough hide
Waghalter- A rogue likely to swing in a gallows.
“We beseek you meekly”- Form of please in Medieval English
― Jennifer
Sources: - Peer Review: A948099 - The Geoffrey Chaucer Phrase Book. -Susan Kelz Sperling, Poplollies and Bellibones, A Celebration of Lost Words,1977
-Manorial Language: http://home.olemiss.edu/~tjray/medieval/manorial.htm

Silver Hollow
(Borderlands Saga #1)
By Jennifer Silverwood
Urban FantasyPaperback & ebook, 429 pages
May 31st 2018 by SilverWoodSketches
"I shouldn't have to tell you this isn't a fairy story..."
After her parents' car crash ten years before, Amie Wentworth trusts books more than people. She may be a writer, but she believes in reality over fiction. She ignores the unexplained mysteries surrounding her, never mind the dreams of a past life, or the fact she can fry technology with a touch. Not even a timely invitation from her long-lost uncle in England gives Amie incentive for anything other than ire.
Until she is stabbed in an alley and brought back to life by a handsome stranger. Soon Amie is dragged into the very sort of tale she is used to selling. To make matters worse, the man who saved her life keeps turning up and her would-be-murderer is still at large.
After crossing the Atlantic to her father’s homeland, she discovers a world beyond imagining. Silver Hollow is a place of ancient traditions and supernatural dangers, where everything is the opposite of what it seems and few escape sane. Faced with an impossible choice, Amie is forced to confront a deadly family legacy while remembering a life she soon wishes to forget.
**Previously published in 2012. This NEW EDITION has been FULLY REVISED AND EXPANDED. The original novel is now no longer available.**
Goodreads│Amazon│Barnes & Noble│Kobo│Smashwords

About the Author

Jennifer Silverwood was raised deep in the heart of Texas and has been spinning yarns a mile high since childhood. In her spare time she reads and writes and tries to sustain her wanderlust, whether it’s the Carpathian Mountains in Transylvania, the highlands of Ecuador or a road trip to the next town. Always on the lookout for her next adventure, in print or reality, she dreams of one day proving to the masses that everything really is better in Texas. She is the author of two series—Heaven's Edge and Wylder Tales—and the stand-alone titles Stay and Silver Hollow.
Website│Blog│Goodreads│Facebook│Twitter│Tumblr
Tour Schedule
May 21st:
Launch
It's All About the Romance
Red Pillows
Paulette's Papers
Reading for the Stars and Moon
May 22nd:
Min Reads and Reviews
Rockin' Book Reviews
May 23rd:
Hearts & Scribbles
E-Romance News
May 24th:
Mythical Books
The Cozy Reading Corner
K. D. Jones: Epic Fantasy Author
May 25th:
An Indie Adventure
Colorimetry
May 28th:
Jorie Loves A Story
Wishful Endings
May 29th:
Singing Librarian Books
Bri's Book Nook
May 30th:
Nicole's Book Musings
Becky on Books
May 31st:
Locks, Hooks and Books
What's Beyond Forks?
June 1st:
Stacking My Book Shelves!
Ms. J Mentions...
Teatime and Books
Bookworm Lisa
June 2nd: Grand Finale
Tour Giveaway

PRIZE PACK #1: 1 winner will receive new Silver Hollow swag, themed bookmarks, stickers, bookish themed tote, and B&N Illustrated Hardcover Editions of Grimm's Fairy Tales and The Story of King Arthur & His Knights (US only)
PRIZE PACK #2: 1 winner will receive signed swag (mainly Silver Hollow and Wylder Tales), ebooks of the Wylder Tales Collection, and a free voucher for Bound Beauty to be published later in 2018 (open internationally)ENDS: June 6th
a Rafflecopter giveaway
 Tweet
Tweet
Published on May 24, 2018 23:30
May 22, 2018
My Book Series Bible ~ Hints, Helps and Musts!!

A series bible? Yep, if you're writing a series, then you need this. Seriously.
When I mentioned the need to have one at a recent writer’s meeting, there were a lot of nods indicating agreement. But in another, unscientific, survey, I found that although the writers I’d polled knew it was needed (sadly, including me) they hadn’t started one, in fact, most didn’t know where to begin. It felt like a daunting task.
My aim today is to help you start.
I currently have 4 series and a new cozy mystery series about to begin, and I’m making a stand-alone book into a series!! So that will be 6. And yet, I hadn’t started on any of my bibles. I told myself umpteen times that I needed to but failed to do so. Sound familiar?Well, now I had to get cracking, as my latest WIP begins at a house you’ve met before, with characters you’d grown to love, and the timeline was nearly simultaneous with the beginning of Believe In Me This Christmas Morn.
I knew if blew details, my readers wouldn’t forgive me. Nor did I want to repeat names. In seven books I have more than 100 names. Some names are important, some walk-on parts.
Published on May 22, 2018 23:30
May 20, 2018
Mental Can Openers & Writer's Hash ~ Let's Give That Smelly Rose Another Name
 Welcome back, Brad Leach...err, or maybe....
Welcome back, Brad Leach...err, or maybe....“A rose by any other name...” is a line oft quoted from Shakespeare’s Romeo and Juliet. While Juliet was a Capulet, a name deemed hateful by Romeo Montague’s family, Romeo found her enchanting. Why, he reasons, should a name matter so much? That’s a question many authors ask today.
Pen names – the assumed appellation of our key-stroke commandos, present, and past. Many famous authors have them. Voltaire was actually Francois-Marie Arouet. George Eliot was actually Mary Ann Evans. Lewis Carroll was known to his mother more properly as Charles Lutwidge Dodgson.
Authors sometimes have more than one. Joanne Rowling not only used her initials J.K. when she wrote Harry Potter (fearing Joanne would discourage boys), she’s also published under Robert Galbraith, Newt Scamander & Kennilworthy Whisp. Benjamin Franklin? Think Richard Saunders of Poor Richard’s Almanac, Anthony Afterwit and Silence Dogood; Dogood even featured in the movie, National Treasure. Samuel Langhorn Clemmens, otherwise known as Mark Twain, used many monikers, including Thomas Jefferson Snodgrass. Clemmens used so many names in fact, historians today aren’t sure we have identified all his works.
So why use a literary sobriquet? After all, don’t we want everyone to associate our written works with who we are? Isn’t it simpler to avoid false names? Shouldn’t we stand behind what we write – even if it’s way behind?

There are several reasons to use a pen name. Security concerns, and marketing top the list. When John le Carre wrote the Spy Who Came in Out of the Cold, he was actually working for MI-6. It wouldn’t do to have his real name, David John Moore Cornwell, splashed about. One writer, whom I know personally, had her house broken into on the assumption that all writers are fabulously rich. It was too easy to track down an address with a real name.
Others may need to avoid association with materials unacceptable to their culture, such as Salmon Rushdie. Many Jewish European writers during the 1920's, 30's and 40's used pen names to protect themselves and family members. And for some, they simply might not wish to embarrass family, such as P.L. Travers, aka Helen Goff, who wrote Mary Poppins based on her own father’s harsh practices.
More often, the use of a nom de plume, as the French say, comes down to marketing. Readers come to associate a name with a certain reading experience. Lester del Rey, aka Leonard Knapp, is associated with Science Fiction. He even started the Del Rey imprint, under Ballantine books. Del Rey publishes Science Fiction. So if Lester were to write a romance set in Amish Pennsylvania, readers who buy it, based on his name, would be greatly disappointed. And romance readers who’ve been around a bit would hardly look up Lester for an Amish romantic love-tussle. A possible answer, had Lester wished to write romance? Become “Marietta Greenplows” and watch interest jump.
Name association is not the only reason. Association with divisive issues can also be helped with a pen name. If you’re a spokesperson making statements regarding gay rights, abortion alternatives or some political candidate, why choose to alienate a large segment of the public? It’s not a case of being ashamed of what you write or what stand you take on social issues, it’s simply economics - separate names lessens the loss of audience?
Of course, another reason is a name that just doesn’t work either on the shelf placement an author might receive or a name that doesn’t fit the genre. Frederick Schiller Faust sounds like some gothic mystery writer or even a German philosopher. But change that name to Max Brand, and western cowboys spring to life. Anne Rice, whose real name is Howard Allen Frances O’Brien, might have felt such an Irish name wouldn’t help her Vampire mystic. Pearl Grey sounds like a tea, but change it to Zane Grey and it smacks of sage and saddles. Who wants advice from Pauline Phillips? But change it to Abigail Van Buren – well, of course, a Boston sophisticate would know what is proper to do or say in any situation!
My reason for a pen name? Romanticism. To be someone a little larger than ordinary life. It’s hard to imagine an audience getting excited over some fantasy written by a leech – horror maybe. But Roulf Burrell and his magic candles? Ask yourself, who doesn’t want to see Lemony Snicket rather than Daniel Handler or Dr. Suess instead of Theodore Geisel? Seigfried Q. Hornblatt crouching below a balcony does not inspire. But change the name to Romeo Montague and now that rose sweetens.
Published on May 20, 2018 23:30
May 17, 2018
Cyberattacks And How To Protect Your Computer and Data by Cyber Expert Josh Moulin ~ Part 3
 This is the final installment of Josh's 3-part series. I hope you've found it as scary and as useful as I have. Thanks, Josh, for your time and your expertise.
This is the final installment of Josh's 3-part series. I hope you've found it as scary and as useful as I have. Thanks, Josh, for your time and your expertise. If you have been following this blog series, you know that the first blog discussed the cyberattack kill chain and how hackers target individuals and systems and the second blog covered common cyberattacks and how they are perpetrated and identified. In this final post, I am going to discuss what users can do to harden their systems against attack.
Typically, criminals are lazy and take the path of least resistance. Just like locking your doors and having an alarm system will deter the majority of home burglars, there are preventative steps a computer user can take to cause a criminal to move on to someone else who is easier to compromise. The major caveat to this is if you happen to be specifically targeted by the attacker, who may not be easily deterred by basic preventative measures.
Cybersecurity is a fine balance between convenience and security; users and businesses must make an informed risk-based decision when determining the level of security that should be applied to systems and applications. Too much convenience and your systems are wide open to attacks. Too much security and work is inhibited
In no particular order, here are my suggestions and opinions on how to keep yourself cybersafe:
Multifactor Authentication
I have an entire blog post dedicated to Multifactor Authentication (MFA). If you want the details, please read it – but to summarize here, use MFA for everything that you possible can. Can it be a hassle to always have your phone with you? Yes. Does it make it nearly impossible for someone to access your online information without your phone? Yes. Use MFA like Google Authenticator or text messaging for banks, Dropbox, iCloud, Google, etc. If you are wondering what sites and services offer MFA, look at this website.
Physical Security
Equally as important as having good cybersecurity, you must protect your devices. Once an attacker has physical access to your phone, tablet, computer, etc. it is game over. Use strong passwords, use screen savers that require a password once they come on, don’t share your password with others, and don’t leave your devices unattended. Never, ever, connect your phone or device to charging stations in public places or to a rental vehicle via USB cables. Studies have shown that in some cases, data is collected within rental car computers and in charging stations and malware can be implanted on the connected device. If you must charge, use power plugs or cigarette lighter chargers and never directly connect a USB cable to a hub. The only exception is if you buy a USB cable that has had the data wire removed or use a data blocking device in line like this one.
Password Manager
I have already mentioned in my second blog post what the dangers are of reusing the same password for everything, but it is impossible to remember multiple passwords. I have a few recommendations when it comes to passwords and it involves another risk-based decision. For instance, if you have enabled MFA on your accounts, then you have greatly reduced the risk of unauthorized access, so the complexity of your passwords is not as important as it would be if you didn’t have MFA (the convenience – security balance). Even reusing passwords on accounts with MFA is more tolerable because the one time password (OTP) used with your app or text message provides the extra security.For me, I use a password manager to maintain all of my passwords. I don’t like having my browser save my passwords because if my system or browser is compromised, those passwords will most likely get stolen. I also don’t trust cloud password managers because if the cloud provider is compromised, my passwords may also be compromised (this has happened).
I recommend standalone databases that are installed on your system and encrypted themselves. I like KeePass and a lot of security research has been done on this program. It uses excellent encryption and you can place the database in a shared location if you want (such as a home network attached storage (NAS) device) and it is usable on mobile devices. It’s not stored in the cloud and allows you to maintain usernames, URLs, passwords, and other secure notes. It also has a password generator, which allows you to create very complex passwords immediately.
I actually do not know most passwords to websites, I use KeePass to generate hugely complex passwords for sites that don’t utilize MFA and just store them within KeePass. If I need to access the site I copy/paste the complex password into the browser and never see it.
Make sure you are using PINs, fingerprints, or complex passwords to access your mobile devices. There are pros and cons to using different methods, but make sure you are at least using something and preferably more than just a four-digit PIN.
Patch, Patch, Patch
Make sure that your Operating System (OS) (i.e., Windows, Mac OS X, iOS, Android, Linux) is setup to automatically download and install updates. Frequent patching is one of the best ways to prevent cyberattacks that leverage known vulnerabilities. In addition to patching the OS, make sure to patch all other third party software installed on your devices. This is relatively simple with iPhones for example because it will automatically update the OS as well as apps installed on the device.
This becomes more complex with computers because although the OS may update, other software like Java, Adobe, Office, Chrome, Firefox, etc. usually don’t. Mac is generally better at third party app management than Windows, but Windows is getting there with Windows 10. There are apps available to help keep your Windows third party software updated, look at https://ninite.com/ for example.
Install and Maintain Security Software
Just as malware has come a long way, so has security software. Today’s (good) security software really does a lot more than the old antivirus software (hence calling it security software instead of just antivirus). Because of the sharing of common information and malware, the market for specialized security software is much different than it used to be and in fact many great products are completely free. Windows Defender for example is actually a decent security software tool and built in to Windows. The nice thing about Defender is that it updates as Windows updates and you don’t have to worry about an incompatibility with your security software anytime you upgrade your OS (used to be a common issue).
Although there are many myths around Macs being more secure than Windows computers, they face many of the same vulnerabilities as PCs. The difference really is that because Windows systems has the greatest market share and are more common in businesses, most malware is written and directed at PCs. There is plenty of Mac malware though and running a Mac without security software is no longer an option.
There is a mix of commercial and open source security software tools available and they range in price from free to an annual subscription of around $50 to $60. Ideally, look for a software that provides anti-malware, firewall, intrusion prevention, web protection, and crypto-attack detection. Here are a few examples of security software tools I would consider (these are my own personal opinions and I’m not endorsing any particular vendor, but have personal knowledge of the tools below).
Sophos (home version is free, or they have a paid version with advanced features) https://home.sophos.com/ Microsoft Windows Defender (free with Windows) https://www.microsoft.com/en-us/windows/comprehensive-security Norton by Symantec (paid product) https://us.norton.com/antivirus Trend Micro (paid product) https://www.trendmicro.com/en_us/forHome.htmlIf you really want to compare different security software vendors, check out this site.

Use Encryption
Encryption has come a very long way and is now built-in to devices and free to use. Encryption essentially scrambles the data on your device and without the key (a password in most cases) the data cannot be descrambled and read. Any Windows device and especially those that travel like tablets and laptops should be encrypted with BitLocker. Don’t discount your home computers though, because if they are stolen in a burglary you don’t want your data in the hands of someone else.
For Mac computers, use the built-in FileVault 2 encryption option. I would caution against having the key stored within Apple’s cloud though. Apple offers to store the key online as a backup (because if you forget your password, you will never get to your data), but this creates a vulnerability. Another option is to take a screenshot of the emergency backup key, print it, and maintain it somewhere like a safe deposit box (same is true for BitLocker and storing the key with Microsoft).
While no one wants a device stolen, if your device is stolen and you have ensured that it is always password protected (including auto-locking after 15 minutes of no use) and it is encrypted, you can rest assured no one will be looking through your data.
Maintain Backups
There are two primary reasons to have backups; one is for the accidental file deletion that you need to restore, and the other is for full disaster recovery. Backup software has also come a long way and both Windows 10 and Mac OS X have built-in backup solutions. My recommendation is to always have frequent incremental backups occurring at least once a day, if not hourly. These backups can be to a connected drive (such as a USB hard drive), or wirelessly to a device like a NAS. Windows and Macs both carve out a portion of the system’s hard drive for incremental backups too, for those times when something is accidentally deleted and just needs to be recovered immediately.
For disaster recovery though, I recommend having a completely separate portable hard drive that you do full backups on. You must decide how frequently you want these backups done (weekly, monthly, quarterly, etc.) and the question you must ask yourself is how much data are you willing to lose if something happens (this is called the Recovery Point Objective in IT-speak). For example, if I decide to do full backups monthly, am I willing to potentially lose a month’s worth of work, photos, etc. if my computer was stolen or destroyed? Remember that the disaster recovery disk is for those situations where you cannot access the original computer for some reason like a fire, flood, or theft. You may also do ad-hoc backups if you just completed some important work and you don’t want to wait until the next month to backup. Just put a recurring appointment on your calendar for full backups and make sure to stick with it.
There are two very important items to remember with your backups. First, the backup disk must also be encrypted. If your backup data is unencrypted and your home is burglarized, the criminals will just get your data off of the backup drive instead of the computer. Both Mac and Windows will allow you to encrypt external drives with FileVault 2 or BitLocker, respectively. Or, you can purchase hardware encrypted drives, such as an Aegis drive (https://www.apricorn.com/).
Second, the disaster recovery backup needs to be stored offsite. Local backup drives are for convenience, but disaster recovery backups are used in the event the original data or system is unavailable. If your disaster recovery drive and computer are in the same place and they are both destroyed, you are completely out of luck. Some people may store an encrypted hard drive at their office, at a friend or family member’s home, in a safe deposit box, or somewhere else they have access to.
Some people may choose to back up to the cloud, which is certainly more convenient but may be less secure. There are ways to encrypt data within the cloud so only you can access it, but this takes additional steps and some advanced knowledge.
Do Not Ignore or Disable Security Settings
Read security warnings that pop up and don’t disable security settings are that designed to keep you safe. For example, automatic software downloads and installation, or user access control (UAC) may be frustrating, but they are extremely important. Also make sure your computer’s built-in firewall is turned on. Windows 10 and Mac OS X both have good firewalls.
Never Use an Administrative Account for Normal Use
This is called the rule of least privilege. Always use the least privileges on a computer necessary to do your work. Your computer should have at least two accounts on it and every user should have their own account (especially kids). One is a full administrator account that you can use to change settings, install software, do maintenance, etc. This admin account should have a password that is unique and hard to guess and should never be used for normal tasks such as web surfing or checking email. If a computer is attacked while logged in as the admin, the likelihood of malware being able to execute and install is much greater. The subsequent accounts should be normal user accounts and not have admin privileges. This is where you conduct the majority of your work such as email, web surfing, etc. If you need to install something under your normal account, you will be prompted to temporarily provide your admin username and password. This is good, as it causes you to think and make sure what is being done is something you requested and not malicious.
To make sure I am never logged in to the wrong account, I make the desktop background of my admin account a bright red solid color. Then, just by looking at my desktop, I know that I should not be doing anything online.
About The Author:
 Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force.
Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force. Moulin has a Master’s Degree in Information Security and Assurance and has over a dozen certifications in law enforcement, digital forensics, and cybersecurity including as a Certified Ethical Hacker. For more information, visit JoshMoulin.com or connect with him on LinkedIn or Twitter.
Tweet
Published on May 17, 2018 23:30
May 16, 2018
Cyberattacks And How To Protect Your Computer and Data by Cyber Expert Josh Moulin ~ Part 2

In my first blog, I discussed the cyber kill chain and how hackers move through predictable steps to launch an attack against a target. In that blog, I used the example of an author who was targeted because of their controversial writings and the author’s system was compromised with ransomware. In this second post, I am going to discuss the most common cyberattacks and how computer users can become savvy to detect potentially malicious activity. While there are many kinds of attacks, I’m going to highlight some of the most common attacks that I see. Additionally, while the technical execution of many of these attacks are different, the methods for detection and prevention are similar if not identical.
Phishing Attacks
The most common way that computers and networks are compromised is through phishing attacks. In my scenario in the first post, the author was tricked into clicking a link within an email that caused the author’s system to reach out to a server and download malicious code. Phishing is a very easy attack to create and is more of a social engineering attack than anything technical.
Sometimes these messages are clearly phishing attacks; the message contains grammatical and spelling errors, it is sent by an organization you never do business with, or it is sent by a prince in Nigeria or the U.K. lottery asking you to claim your winnings. Clever hackers though take time in crafting their message and even if it is blasted to millions of email accounts, all they need is to steal the credit card information of just a few people to make a huge return on their investment.
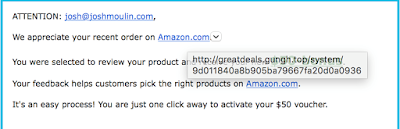
Below is an actual phishing email that came to me. As you can see, the message looks legitimate and there are no obvious signs of it being malicious. Remember, the rule is to never click any links until and unless you are positive the message is legitimate.

When I hovered over the links within the email, none of them went to the Amazon.com domain. Instead the links all pointed to hxxp[://]greatdeals.gungh.top/system/9d011840a.... This URL has since been taken down as malicious, but had I actually clicked the link when the URL was still active, my system very well may have become infected.
In some cases of phishing, instead of getting a link to click, the attacker will send a specially crafted attachment. PDFs and Office documents (e.g., Word, PowerPoint, Excel, etc.) can be embedded with malicious code and once a user opens the document the code may be able to execute. This is why in the latest version of Microsoft Office, documents are opened in safe mode and in order to edit or print, users must click a button. This safe mode prevents the document from running any macros or other code that may compromise the computer.
If you are ever unsure of a URL or a file, there are several free online resources to help. For instance, URLQuery.net allows you to enter a URL and scan it for malware, complaints, or other warnings. It also tells you the country it is hosted in and gives a screenshot of the website you looked up. Another site, VirusTotal.com, is owned by Google and allows both URLs and files to be scanned for malware. If you receive a file from someone and you want it scanned before you double click it, upload it to VirusTotal to see if it’s malicious first.
Drive-By or Watering Hole Attacks As organizations and individuals have become more adept at identifying phishing emails, attackers have had to change their modus operandi. One such example of this evolution is changing phishing emails so instead of sending an attachment within an email that is compromised or a link that begins the download of a piece of malware, the email (or Facebook post, or Tweet, etc.) sends the user to a website. The website is most likely legitimate and the user’s system would not detect anything suspicious at this point because nothing is attempting to download.
In the background however, the attacker has compromised the website, hosting malware on the site itself. Once the victim’s browser begins to read the contents on the website, it delivers a payload of malware to the system. This may come in the form of a download where the user is prompted to run something, or it may be a piece of JavaScript that when the browser sees the code, it automatically runs it without user interaction.
These attacks are called “drive-by” attacks because they can indiscriminately target anyone who browses the site, or watering hole attacks because the malicious activity is just sitting in the site, waiting for people to stop by. There have been some very popular websites compromised and embedded with malware such as CNN and Forbes so this kind of attack can be extremely widespread.How do you spot this attack? Well, this one is tricky and there is a possibility that nothing on your system will notify you that an attack is taking place. Some more advanced anti-malware software may catch it, or if you notice strange things happening on your computer (website crashes, or your computer begins running slow with high CPU or memory utilization), or being prompted to download and run something may all be indications of a problem.
Wireless Attacks / Man in the Middle (MiTM) Attacks While it has long been known that Wi-Fi, Bluetooth, and other wireless technologies are vulnerable to attacks, it is still a common and successful attack because people continue to connect to open access points out of convenience or to save their data consumption. Many people do not configure their home wireless access points correctly either, leaving them vulnerable to attacks by people in the area.
When I was in law enforcement, I remember a case where an Internet Protocol (IP) address was identified as downloading hundreds of images of child sexual abuse. My team wrote a search warrant and executed it, only to find that the home we went to had nothing to do with the crime. Our investigation later revealed that a neighbor about three homes down was a registered sex offender and had been using this neighbor’s Wi-Fi to commit their crimes. It was a huge inconvenience (not to mention a traumatic event) to not secure their Wi-Fi network and it all could have been easily prevented by taking some basic security steps.
Beyond securing your personal network, you must be extremely careful with the networks you allow your devices to connect. If you are connected to an unsecure wireless network (e.g. Starbucks) anything that your device transmits or receives that isn’t otherwise encrypted is fair game for someone also connected to that same wireless network. Wireless networks acts as a hub, meaning that anyone else connected to that network can see all the traffic, not just the traffic between their own device and the wireless router. Because of this, I can setup my device on the Starbucks network to promiscuously listen to all traffic and capture it, allowing me to compile it and view anything you typed, downloaded, uploaded, etc. as long as you were doing it unencrypted (http instead of https for example). If you navigate to a website that is not using encryption like http[://}yoursite.com and enter a username and password, I can sniff that out of the air and later use it.
It is true that more and more sites, especially sites that involve finance or healthcare use encryption because it’s mandated, there are still many sites that do not. The other danger is that most people reuse passwords, so even if your bank uses encryption (i.e., https[://]yourbank.com) but your favorite news site does not and you use the same password between the two, once I get the unencrypted username and password and see in your traffic you navigated to US Bank’s website, I can try your username and password on that site to see if it works. This is another huge reason to always use multifactor authentication on everything (more on this in the next post).
Another wireless attack is called the Man-in-the-Middle or MiTM attack. This kind of attack, which can also be carried out with cellular devices using devices like the Stingray can be very dangerous. In this kind of attack, the criminal creates a rogue access point (AP) and advertises it for users to connect to. On one side of the rogue AP are the victim devices and the other side is a path to the Internet. This allows the attacker to capture, decrypt, and record all of the traffic between the victim device and the Internet. It also allows the attacker to inject malicious traffic or redirect websites using the Domain Name Service (DNS).
To illustrate an MiTM attack, imagine you are seated at the airport and see a variety of wireless APs available to connect to. One has the name of “Free WiFi” and the other says “Free High Speed WiFi.” The “Free WiFi” is the legitimate Internet connection offered by the airport, but the “Free High Speed WiFi” is a malicious AP. An attacker sitting in your general proximity has created an AP using free software on his laptop. As your device scans for open APs it locates the High Speed AP and since anyone would want high speed over standard speed, you click to connect to the high speed AP. Once you click to connect, your device associates itself with the attacker’s laptop.
Now that you are connected to the attacker’s laptop, he essentially owns your device and the communications between your device and the Internet. Since the attacker is routing your traffic through to the Internet, as a user nothing seems out of the ordinary. In fact, the attacker is probably leveraging the airport’s free Wi-Fi to get your device out to the Internet. However, the attacker is now capturing all of the traffic coming into and out of your device and as we have already learned, anything typed in the clear (unencrypted) is recorded by the attacker in plaintext.
The attacker could make things even more interesting by using his laptop as a proxy between your device and the Internet and decrypting your encrypted traffic between your device and wherever you are browsing. Essentially what happens is your device connects to the attacker’s laptop where he breaks your connection to your bank or Facebook account, or whatever it is you are navigating to and decrypts your traffic, then re-encrypts it between his laptop and the destination (we’ll use your bank in this situation). Now the attacker can record even encrypted traffic such as usernames and passwords in plaintext. This attack however, will prompt the user’s device with an error message that the encryption certificate that you are using to visit your bank does not match the domain name of the bank and will require the user’s interaction to continue. If you’re interested in the technical details of encryption, certificates, etc. send me a note and I’ll be glad to discuss it.
Suffice it to say that if you get an error message about mismatched certificates (as shown below) on any device there is a high likelihood that the certificate has been compromised or you are the victim of a MiTM attack. No matter the reason, if you get this error, stop browsing, try connecting later from a different access point or from your cellular data to see if you get the same error, or contact the institution you are trying to access.
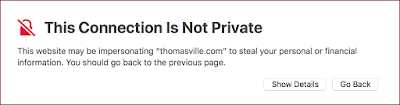 An error message generated by Safari showing there is a problem with the website encryption certificate
An error message generated by Safari showing there is a problem with the website encryption certificate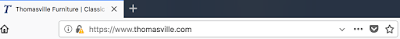 The same website visited in Firefox; notice the alert over the padlock
The same website visited in Firefox; notice the alert over the padlock
An example of Firefox showing a correctly implemented website encryption certificate
As mentioned above, the attacker can also inject malicious traffic into your session or redirect your computer. For example, if you type google[.]com into your browser, the attacker can create DNS entries that says if a user types google[.]com, actually send them to duckduckgo[.]com. In an even more sinister scenario, the attacker could create a rule that if you type wellsfargo[.]com, send the computer to wellsfargoamerica[.]com which might be a fake website that looks exactly like the real Wells Fargo (see Pharming attacks below).
How do you spot this attack? First, don’t connect to free Wi-Fi hotspots. If you absolutely must, then make sure you are using a Virtual Private Network (VPN) connection (either through your employer or use some of the VPN services available) which creates an encrypted tunnel between you and the VPN service before you navigate the Internet. Spotting a simple MiTM rogue AP may be nearly impossible. Spotting a rogue AP acting as a proxy will give you the browser certificate error messages shown above.
Pharming and Illegitimate Websites
Pharming, like it’s sister Phishing, is an attack that socially engineers a user. Instead of sending a message out, pharming is more like the watering hole attack where it waits for victims to stop by. Pharming is usually done by an attacker when they create a fake website but make it look legitimate and trick users to visit the site and enter their sensitive information (like credentials). Take this scenario: an attacker knows that because of a recent disaster, many users will be donating money to the American Red Cross on the legitimate website redcross[.]org. So, the attacker uses a free tool to “scrape” the actual Red Cross website, purchases the domain name of redcross[.]info, and then uploads the copy of the real Red Cross website to a server being hosted with Amazon Web Services (AWS). The attacker then begins a massive spam campaign for people to donate and provides the link of redcross[.]info and as people go to that site, it looks completely legit just like the real site. Users begin to donate millions of dollars to the PayPal account, which all goes to the attacker’s bank account.
This kind of attack can also be used by taking advantage of common misspellings or known letter combinations that people may not notice in the URL bar of their browser.
How do you spot this type of attack? This one may be difficult or impossible. Since nothing malicious is actually running on your computer (unless the attacker is combining Pharming with another attack) and you are just entering information into a website, there may be no signs or alerts at all. The best way to prevent this type of attack is by being very careful what you type into the URL address bar of your device, using known good bookmarks instead of relying on searches each time, and if you are given a link to click, make sure it matches the known website. Sometimes if I get a link from someone to follow, instead of clicking the link I will Google the organization and go to it that way, or at least confirm that what was in the link matches what is in Google.
In all of these attacks the bottom line is to pay attention, don’t click links that you don’t absolutely trust, actually read error messages that pop up on your screen before just clicking “OK”, don’t connect to public Wi-Fi APs, and make sure the certificate of an encrypted website you are visiting matches the domain name. In the last post of this series I will discuss the preventative strategies you can take to help harden your systems from attack and some proactive steps you can take to reduce the likelihood of being compromised.
About the author:
 Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives with the world’s leading IT advisory and research firm. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force.
Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives with the world’s leading IT advisory and research firm. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force.Moulin has a Master’s Degree in Information Security and Assurance and has over a dozen certifications in law enforcement, digital forensics, and cybersecurity including as a Certified Ethical Hacker. For more information, visit JoshMoulin.com or connect with him on LinkedIn or Twitter.
Tweet
Published on May 16, 2018 23:30
May 15, 2018
Cyberattacks And How To Protect Your Computer and Data by Cyber Expert Josh Moulin ~ Part 1
 I'm incredibly honored that Josh Moulin, who was my cyber expert for Forever Yours This New Year's Night, responded with a "yes" when I asked him to do a series on what is a cyberattack, how to recognize them, and how to protect yourself. Take it away, Josh.
I'm incredibly honored that Josh Moulin, who was my cyber expert for Forever Yours This New Year's Night, responded with a "yes" when I asked him to do a series on what is a cyberattack, how to recognize them, and how to protect yourself. Take it away, Josh.Cyberattacks and data breaches are unfortunately commonplace in the daily news cycle. Many of us have had our personal, healthcare, and financial data breached so much that we are used to receiving letters notifying us of unauthorized disclosures or getting signed up for yet another credit monitoring service. Cybercrime is out of control and the most infuriating part is that most of the attacks are not sophisticated or require an expert hacker. Indeed, most of the successful attacks use the same modus operandi that they have for a decade.
The fact that the majority of attacks are not sophisticated is as troublesome as it is helpful. Since we know what most attackers do, it makes the identification and prevention of these attacks easier. Individuals and small to medium businesses often assume (incorrectly) that if the United States Federal Government or massive corporations such as Home Depot, Anthem, Yahoo!, Target, and Equifax, who spend millions of dollars each year in cybersecurity can’t keep hackers out, then there is no possible way they can defend themselves.
It is true that many cyberattacks are easily preventable and only effective because mistakes have been made which create vulnerabilities. However, it is also true that this world has nation-state military units and sophisticated hackers which target government agencies, universities, corporations, and high-value individuals. When a skilled attacker has set their sights on a victim and has the means, opportunity, and intent to launch a cyberattack against that victim, these attacks may use techniques, tactics, and procedures that are highly complex and extremely difficult to detect. For the purposes of this article, I am not discussing these advanced attacks.
In this first blog post of a three-part series, I am going to focus on the cyberattack kill chain and lay the foundation for how cyberattacks happen. The focus audience of this post is individuals who are trying to protect their personal devices and data from cyberattacks. The next blog post will discuss the most common attacks and how to spot them, and finally I will discuss preventative strategies that people can take including security software, configurations, and backup strategies.
Cyberattack Kill Chain
Each cyberattack goes through a series of steps to accomplish its mission. Depending on the target, mission objectives, and abilities of the attacker this kill chain may happen very quickly or may take months to years to accomplish. Sometimes an attack is to simply disrupt a business competitor or political adversary. Attacks like this are generally carried out through Distributed Denial of Service (DDoS) attacks or website defacement. Other attacks are performed with the intent of gaining intelligence about a competitor or government agency, and yet others are to steal intellectual property, harass someone, or to support a political ideology (hacktivism).
The attack kill chain is comprised of the following steps:
1. The target is defined: This may simply be a target of opportunity (e.g., a person in close proximity to a hacker that has a vulnerable mobile device) or could be targeted due to the person’s position, the value of their data, etc
2. Reconnaissance: The attacker begins to research the target. What information is available via public open source intelligence (OSINT) such as Facebook, LinkedIn, Google, public databases, etc. What IP addresses are assigned to the target, what operating systems do they use, and are there any known vulnerabilities for the target’s Internet connected systems?
3. Weaponization: The attacker develops their weaponized attack, which is generally malware (malicious software) such as a Trojan horse, virus, ransomware, worm, etc. or may utilize a previously unpublished exploit known as a zero-day (0-day). The weapon must be able to exploit a vulnerability, which is what the attacker discovers during the recon stage.
4. Delivery: The attacker delivers the payload to the victim. This may be done in a variety of ways such as via an email attachment or embedded link (phishing), through a chat session, uploading a file to a server on the Internet, compromising a website and then sending the victim to the compromised website (also called drive-by attacks), or several other methods.
5. Exploitation: Once the payload has been delivered, the malicious code must execute to exploit the system. Malicious code can be executed by the attacker, by the system itself, or frequently by a user who clicks something and executes the malware.
6. Installation: After the vulnerability is exploited the malware is installed on the system. Most attackers want one thing: persistence. They want to get on a system and stay on a system, having the ability to do internal recon now that they are inside the network and laterally move to other systems to stay within the network and spread their attack. Some advanced malware only lives in RAM and never actually “installs” on a hard drive, making post-mortem examinations of systems difficult.
7. Command & Control: Once the malware is installed it generally opens up the system to receive commands from the attacker (known as Command & Control, or C2). Malware may “phone home” occasionally asking for any new commands from the C2 which may tell the malware to perform functions such as copy and send data from the computer to the attacker’s system, activate the system’s webcam, or any number of other things.
8. Exfiltration: Generally the main goal, this is the step where the attacker gets access to data and begins sending (exfiltrating) the data from the system to the attacker.
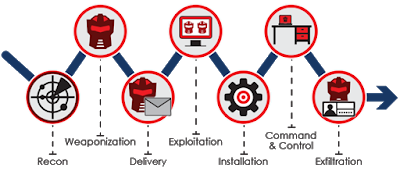 Source: EventTracker
Source: EventTrackerThere are several ways to make yourself less susceptible to a cyberattack, such as reducing the attack surface, target hardening, and learning how to identify potentially dangerous situations online or in emails.
A Practical Scenario An author is putting their finishing touches on their latest work in preparation of sending it off for review. This author is somewhat controversial and critics are anticipating the release of the new book, posting negative comments all across the Internet. A hacker decides to make a statement by attempting to hack this author’s computer and disrupt the author’s ability to publish the book as well as steal a copy of the book before it is released. Step 1, target acquisition is complete.
The hacker begins by finding out as much as possible about the author through social media, Internet posts, interviews, and any other source of OSINT. The hacker is able to determine through social media that the author has a daughter in the fourth grade and because of geotagged photos posted of the author’s daughter, the hacker determines what school the daughter attends. The hacker now downloads the logo of the elementary school as well as an offline copy of the school’s website. Step 2, reconnaissance is complete.
The hacker obtains a variant of ransomware from a hacker website and places the malicious code on a server controlled by the hacker and sitting inside of Amazon Web Services (AWS). The malicious code is just waiting to be downloaded and executed by anyone who visits the server. Step 3, weaponization is complete.
Next, the hacker drafts an email using the same logo, colors, and “look and feel” of the elementary school’s website. The hacker addresses the email to the author’s email address (which was obtained via Google) and sends an email to the author during school hours that there has been an active shooter incident at the school. Included in the email is a link that tells the author to click for further details.
As any parent would, the author clicks the link of the email. When the author clicks the link, they are directed to a webpage that looks exactly like the school’s site. They receive some bothersome pop-up that the don’t read because they are terrified about their child’s safety and just click “ok” to close the window and see what is going on at the school. In reality, when the author clicked the link they navigated to a fake site hosted by the attacker and their computer downloaded the ransomware code. When the code attempted to execute, a pop-up appeared asking for administrative privileges to execute the code. When the author clicked “ok” they just executed the ransomware on their computer. Steps 4, 5, and 6 (delivery, exploitation, and installation) are complete.
The ransomware on the author’s computer begins immediately encrypting data on the hard drive and searches the drive for any .doc or .docx files, compresses them, and exfiltrates them to the attackers C2 server located in AWS. The author has now lost their latest manuscript and cannot access any files on their computer due to the ransomware encryption. Steps 7 and 8 (C2 and exfiltration) are complete.
This scenario is exactly the kind of targeted social engineering attacks that occur on a daily basis and are extremely easy to perpetrate. In future blog posts I will discuss how to recognize attacks and how to harden your systems to try and prevent malicious activity.
About the author:

Josh Moulin serves as a trusted advisor to federal government IT and cybersecurity executives with the world’s leading IT advisory and research firm. Previously, Moulin was the Chief Information Officer for the Nevada National Security Site, part of the U.S. Department of Energy’s Nuclear Weapons Complex and before that spent 11 years in law enforcement including 7 years as the commander of a cybercrimes task force.
Moulin has a Master’s Degree in Information Security and Assurance and has over a dozen certifications in law enforcement, digital forensics, and cybersecurity including as a Certified Ethical Hacker. For more information, visit JoshMoulin.com or connect with him on LinkedIn or Twitter.
Tweet
Published on May 15, 2018 23:30
May 1, 2018
Author Spotlight Featuring Dana Wayne & Her Latest Book ~ Whispers On The Wind
 I've said this many times, but it never gets old. I love finding new-to-me authors and their books to bring you. Please welcome Dana Wayne!!
I've said this many times, but it never gets old. I love finding new-to-me authors and their books to bring you. Please welcome Dana Wayne!! Thanks, L.A. it's wonderful to be here.
Thanks, L.A. it's wonderful to be here. Writers hear voices in their head all the time and virtually anything can spark that internal dialog. Sometimes, those voices happen in a dream. That’s how Whispers came about. I woke up with this voice in my head telling me about Cooper Delaney and the voice in his head. I knew I could not go back to sleep until those thoughts were captured on paper, so at 3:30 a.m., I get up, turn on my computer and type away for two hours.
My husband, bless his heart, is now accustomed to waking in the wee hours of the night to find himself all alone in the bed. He used to get up and check on me, but now he knows my imaginary friends are talking and I’ll come back to bed when they’re done.
We were headed to Dallas recently and I had this scene going on in my head and blurted out “Don’t make me do that.” He cut his eyes over and quipped “Are you talking to me or your imaginary friends again?”
That’s how it is living with a writer.
Excerpt:You let him kill her.The angry female voice in the pre-dawn hour jolted Cooper Delaney from a restless sleep.Adrenalin pumping, he rolled to the right and automatically grabbed his pistol from the nightstand, fully expecting to see a stranger beside the bed.Nothing but moonlit shadows. He swiveled his head to the left. The room was empty. He blinked and drew in a deep breath, trying to dispel remnants of the dream making sleep all but impossible for over a month. Always the same dream; a shadowy figure begging Coop to find her. That was it…find me, please. Two weeks ago, the voice changed and insisted Coop had to stop him. Stop who? From what?Tonight, the dream exploded into a full-blown nightmare.He put the gun back on the table and lay down, right arm over his eyes. “Shit,” he whispered as the vision replayed through his mind. Powerful hands gripped her throat, the eerie silence punctuated by ragged gasps as she struggled for air. Blood trickled from her nose and the corner of her mouth. Dark hair wedged into a jagged cut across her forehead. Terror-filled eyes stared at the figure bent over her. All the while, the voice reproached…you didn’t stop him.At forty-three, Coop considered himself a straight-forward, no nonsense lawman, well known and respected as the Sheriff of Baker County, Texas. He looked at the facts, the evidence, and made logical, rational decisions. And yet, the dream was so real, he smelled the metallic odor of blood, felt the dampness of the earth around her. “Dammit.” He lowered his arm and punched the bed. I’m losing my fricking mind. It was bad enough when the voice invaded his sleep, but two days ago, he heard it at the kitchen table where he sat eating breakfast. Wide awake. This time, she warned he – whoever he was – would kill again.He tossed the sheet aside and sat on the edge of the bed. Heart pounding, his breath hissed as he gulped in air. Elbows on his knees, he cradled his head in his hands. “Just a dream,” he murmured, “a bad dream.”He stumbled to the window and shoved it open with an angry thrust, gasping when the rush of cool night air caused gooseflesh to prickle his sweat-coated body. “A dream,” he whispered, willing himself to believe. “Nobody died.” He pulled down the sash and pressed his forehead against the glass pane. “Nobody died.” When his racing heart finally slowed, he pushed away and headed for the bathroom, stopping at the foot of the bed as he tried to remember if Miss Eva had guests tonight. A curse escaped parched lips as he grabbed his jeans from a chair. Why in the world did she want to go into the B&B business anyway? Even as the thought flitted through his mind, he knew the answer. She decided he needed a wife and used the lovely Antebellum home to lure prospects. Hence, the majority of her guests were single women looking for a good time, or to change their marital status. He lost track of the propositions, both subtle and otherwise, thrown his way in the last six months. When had women become so forward? He opened the door and padded on bare feet to the bathroom he shared with his son, Jason, when he was home from college. Guests used the one across the hall. Since sleep was out of the question at this point, he threw on a shirt and headed downstairs for coffee. Light showing under the kitchen door stopped him cold. “Crap. Company.”
 Buy: Amazon | Website | Draft To Digital
Buy: Amazon | Website | Draft To Digital
Blurb:You didn’t stop him. He killed her.
Dire warnings from a voice only he can hear makes Sheriff Cooper Delaney doubt his sanity. When a body is found matching one from a recent nightmare, he believes he’s gone off the deep end. The dead do not talk to the living. Or do they? One body becomes two. Are there more?
Heart broken by betrayal, Dr. Samantha Fowler finds herself starting over at thirty-three. When she meets the local sheriff, the attraction is instant and fierce, threatening to crumble the defensive walls around her heart. Once burned, twice shy, she vows to stay far away from him for the duration of her stay at the quaint B & B they share. But when she finds one body, then another, avoiding the handsome Texan is impossible.
He’s not done.
Quarry in sight, he watches and waits. “I am the master. I cannot be stopped.” The clock is ticking…
 Bio:Awarding winning author Dana Wayne is a sixth generation Texan and resides in the Piney Woods with her husband, (and biggest fan), a Calico cat named Katie, three children and four grandchildren. She routinely speaks at book clubs, writerHer debut novel, Secrets of The Heart, was awarded First Place - Contemporary Romance, 2017 by Texas Association of Authors, was a finalist for the 2017 Scéal Award for Contemporary Romance, Reviewers Top Pick and included on the Top 10 Books to Read This Winter from Books & Benches online magazine.
Bio:Awarding winning author Dana Wayne is a sixth generation Texan and resides in the Piney Woods with her husband, (and biggest fan), a Calico cat named Katie, three children and four grandchildren. She routinely speaks at book clubs, writerHer debut novel, Secrets of The Heart, was awarded First Place - Contemporary Romance, 2017 by Texas Association of Authors, was a finalist for the 2017 Scéal Award for Contemporary Romance, Reviewers Top Pick and included on the Top 10 Books to Read This Winter from Books & Benches online magazine. Her second novel, Mail Order Groom, released in April, 2017, received 4.5 Stars and the Crowned Heart from InD’tale Magazine, 5 Stars from Readers Favorite and Books & Benches, and was included in the list of 100 Best Indie Books to Read Before You Die. Her third book, Whispers on The Wind, is a romantic suspense released in March, 2018, garnered 5-Star review from Readers Favorite.
Affiliations include Romance Writers of America, Texas Association of Authors, Writers League of Texas, East Texas Writers Guild, Northeast Texas Writers Organization, and East Texas Writers Association.
Find Dana:Facebook | Twitter | Website | Instagram
Tweet
Published on May 01, 2018 23:30
April 25, 2018
Five Secrets With Author Donna Wichelman & Her Latest Release ~ Undaunted Valor
 It's my pleasure to bring you Donna Wichelman and Book 2 of The Waldensian Series, Undaunted Valor
It's my pleasure to bring you Donna Wichelman and Book 2 of The Waldensian Series, Undaunted Valor  Thanks, L.A. for hosting me again, it's a pleasure to be on your blog.
Thanks, L.A. for hosting me again, it's a pleasure to be on your blog.
I discovered my true passion for writing novels at the United World College of the Atlantic in Wales, where I focused on English Literature. I loved all the classics, reading books by Jane Austin, William Shakespeare, Charles Dickens, Ellie Wiesel and Victor Hugo. They awakened a desire in me to write books that touched the human spirit.
While I was at Atlantic College, I wrote a thesis on Emily Brontë’s Wuthering Heights and visited the Brontë parsonage in Haworth, England. Walking the heather-dressed moors on a drizzly day is forever etched in my mind, because I happened upon an old man with a cap and a cane whose ancestors knew the Brontës. Not only was he the quintessential British gent, but he fascinated me with stories about the family. I felt like I was actually living a storybook tale.
When I returned to the States, I majored in sociology and political science at Case Western Reserve University in Cleveland, but writing was still in my blood. Several years later, I mastered in Mass Communication/Journalism and worked as a communications professional before writing full-time.
Since writing as a full-time career, I’ve authored short stories, essays and articles in various inspirational publications and live my dream writing novels and screenplays.
Hi Donna, please tell us Five Secrets we may not know about Undaunted Valor, Book 2 The Waldensian Series or you, but will after today!
1) Undaunted Valor went through three stages before the book found its rightful story. In the original plotline, after Jamie found a letter from her ancient cousin Anne Charbonnier, she felt a desire to go on a pilgrimage to understand the heart and soul of her ancestors. Though such a soul searching story had its merits, the plotline didn’t feel compelling enough. So I added the element of the mob coming back to avenge the death of their mob boss from Book 1 Light Out of Darkness. Still, the book needed something more sinister that Jamie and Alessandro cared deeply enough about to fight for. That’s when the plot took a turn and Alessandro’s grandmother was kidnapped and a ransom demanded for her return. Now they had a cogent reason to hike a part of the trail of the Glorious Return with all its danger and pitfalls.
2) As the plotline for Undaunted Valor evolved, so did the working titles for the book. The first working title was The Glorious Return based on the original plotline when Jamie wanted to go on a pilgrimage. Against All Odds, suggested by a good writer friend, became the working title when the mob element developed and could have worked as a permanent title. However, given the Waldensians’ historical reputation for valor and enduring faith during centuries of persecution from the Church in Europe, Undaunted Valor, also suggested by a writer friend, seemed fitting as Jamie and Alessandro traveled the same roads as their ancient ancestors and fought against formidable foes for their beloved grandmother’s life.
3) I fell in love with the idea of Jamie and Alessandro’s love story paralleling the story of one of Anne’s ancient ancestors. I thought the notion was so compelling that I wrote Anne Charbonnier’s letter in one sitting. Anne’s love affair with the son of her people’s enemy is a universal love story, pitting family members against one another. Since Anne’s story is also based on a historical period of time, I am currently turning the story into a screenplay with a little bit of twist at the end. I’m also contemplating turning the letter into a full-length novel. Stay tuned for further developments.
4) I’ve always loved the name Anne. I had intended to give Anne to my daughter as a middle name, but half drugged in the delivery room, she received my middle name Lynn. If my husband and I had been able to have another daughter, we would have named her Anne. As fate will have it, after Anne Charbonnier became a character in my book, I found the name in the actual genealogical records of the Waldensian Church in Italy.
5) I am a history buff. Always have been. American History and Geography were my two favorite subjects in junior high school, and I did well in those subjects. That’s why, though I’m writing contemporary stories, something related to history will probably always appear in my books.
 Blurb:For nature lovers, ski aficionados, travel enthusiasts and history scholars, the French Alps offer some of the most spectacular scenery and outdoor recreation in all Europe with its majestic mountain peaks, cascading waterfalls, unspoiled forests and quaint mountain villages. People come to get away from the daily grind and rejuvenate their spirits.
Blurb:For nature lovers, ski aficionados, travel enthusiasts and history scholars, the French Alps offer some of the most spectacular scenery and outdoor recreation in all Europe with its majestic mountain peaks, cascading waterfalls, unspoiled forests and quaint mountain villages. People come to get away from the daily grind and rejuvenate their spirits. But when Alessandro Marianni’s grandmother Luciana is kidnapped during a church conference in Chamonix, the same landscape becomes an ominous height to scale, and Jamie Holbrooke and her fiancé Alessandro have difficulty distinguishing between friend and foe on the race to find her. They will have to weather a rainstorm on a mountain trail, negotiate a dangerous waterfall, outmaneuver a car chase, and defy an assassin’s gun in their search.
Will they find their beloved Luciana before it’s too late? Who will die on the way to the finish line? Who can they trust? And where will Jamie find the courage to confront her adversaries?
In this sequel to Light Out of Darkness, the answers will lie in unanticipated places and with unexpected allies and require Jamie to discover what it means to trust God with undaunted valor.
Buy: Amazon
 Find Donna: Website | Blog | Facbook Author | Twitter | Pinterest | LinkedIn
Find Donna: Website | Blog | Facbook Author | Twitter | Pinterest | LinkedIn
Tweet
Published on April 25, 2018 23:30
April 10, 2018
Author Spotlight Featuring Jill Haymaker's New Release ~ Mountain Hearts
 Please welcome Jill Haymaker and take a peek at her lastest novel in the Peakview Series, Mountain Hearts.
Please welcome Jill Haymaker and take a peek at her lastest novel in the Peakview Series, Mountain Hearts. Thanks, L.A., it's good to be back.
Thanks, L.A., it's good to be back.I’ve always wanted to write a book about someone who’d lost a child. It’s the most devastating thing anyone can live through. My heroine starts the story in this very dark place. This book is about recovery and coming through on the other side of grief. Love can help us get through just about anything. I decided to make my hero have his own past ghosts so they could heal together.
We’ve all experienced some kind of grief in our lives. My goal is to show hope to those who need it. I hope everyone will be able to relate to this story on some level.
Excerpt:Suzy Quinlan kicked the dark gray slush in front of her tire with the pointed toe of her high-heeled black boot. The clump fell off her car with a thud, as she grabbed the door handle with her free hand to avoid the same fate. In her other hand, she clung to the large, black umbrella. The cold, icy drizzle continued to fall from the sky. She glanced back in the direction she’d come, in time to see the coffin being lowered into the cold ground. She quickly turned away. The grave side service was bad enough—she didn’t want to think about what happened next.
She carefully walked to the driver’s side of her car. A solid layer of ice had formed on her windshields. Could this day get any worse? She slid her way to the trunk and grabbed out her ice scraper. This was a two-hand job. She collapsed the umbrella and threw it in the trunk. Her long, red hair, which she had so carefully straightened this morning, was sure to turn into a frizz ball in about ten seconds flat in this weather. It didn’t matter. Nothing really mattered anymore. She made her way back to the front of the car and started chipping away. Reaching across the snowy hood, she cursed as her ankle twisted in a pothole. Icy, cold water entered her boot which was made for fashion, not function.
She gave up and climbed behind the wheel and cranked the defrost button to high. She’d wait while the car did the rest of the work. She sighed and laid her head on the steering wheel. She wasn’t going to cry, not now.
Tap. Tap. Tap. Suzy looked up to see her mom knocking on her window. She pushed the button, and slush flew as the pane descended.
“You’re coming to the house, right?” Mom’s pretty face was creased with worry.
“Yes.”
“Do you want to ride with us?” Mom pointed over at Dad sitting behind the wheel of the next car.
“It would be silly to leave my car here at the cemetery. Besides, my feet are soaked. I want to stop at the apartment and change. You go ahead.”
“Alright, but don’t take too long. Aunt Julie says people from the church have been bringing food by all day. I know everyone wants to see you. Don’t forget that Grams and Alice have to catch a plane tonight.”
“I’ll be there.” She rolled the window back up and watched her mom climb in their vehicle, and her dad drive away.
Her windshield had semi-cleared. She turned on the wipers, pulled away from the curb, and drove down the slushy street. Not toward her apartment—not toward her childhood home—just ahead. She knew everyone wanted to give her their condolences, but she’d lose it if she heard one more person say, “I’m sorry for your loss” or “It’s going to be alright.” It wasn’t going to be alright—ever. No amount of casseroles could change that.
 Buy:
Amazon
Buy:
Amazon
Blurb: SUZY QUINLAN’S heart dies the day she buries her five year old son, Mason. Leaving the cold cemetery, she flees to the Colorado Mountains searching for peace. Unexpectedly caught in a blinding snowstorm, she seeks shelter in the tiny town of Peakview.
JERRY DECKER is known as the town’s hermit. Since returning from his service in Iraq eight years earlier, he lives a solitary life hiding from his demons, with only his dog, Bear, as company.
Two hearts damaged by grief drawn together as kindred souls. To move forward, they’ll have to face their pasts and lay their ghosts to rest. Can broken hearts dare to hope again?
COME HOME TO PEAKVIEW, COLORADO, WHERE EVERYONE HAS A CHANCE AT LOVE.
 Bio:Jill Haymaker was born and raised in Indiana and Ohio. After high school, she attended Bowling Green State University before moving to Fort Collins, Colorado. Ms. Haymaker made her home in Fort Collins until her recent move to East Texas. She practiced family law in Fort Collins for the past 20 years. She has three grown children, a son and two daughters. She also has three granddaughters.
Bio:Jill Haymaker was born and raised in Indiana and Ohio. After high school, she attended Bowling Green State University before moving to Fort Collins, Colorado. Ms. Haymaker made her home in Fort Collins until her recent move to East Texas. She practiced family law in Fort Collins for the past 20 years. She has three grown children, a son and two daughters. She also has three granddaughters. Jill has always had a passion for writing. Colorado Sunset was her first full length romance novel in her Peakview, Colorado series. Her latest book, Mountain Hearts is the eighth book in the series. If you love small town romance, you will love the characters in this series. She also has had several short stories published by Chicken Soup for the Soul, the most recent in the book Random Acts of Kindness.
When not practicing law or writing, Jill enjoys The Colorado mountains, horseback riding, gardening, long walks with her Shetland Sheepdog, Laddie, and spending time with her children and grandchildren. She enjoys their numerous sporting events. She is also an avid football fan and can be found on autumn weekends cheering on her favorite teams. She has a passion for working with high school youth- she is a youth group leader at her church, coaches a high school mock trial team and is a volunteer at cross country and track meets.
Find Jill:Email | Amazon Author Page | Website/Blog |Twitter | Instagram | Facebook |Goodreads
Tweet
Published on April 10, 2018 23:30



