John Robb's Blog, page 12
October 28, 2015
Autonomous Weapons
Rapid technological changes can radically transform the way warfare is fought. In this instance, the improvements we are seeing in machine cognition are making possible something new: autonomous weapons.
What does this mean? If you look up the word autonomy, you'll see lots of competing definitions from technologists and sociologists. Most of these definitions are so complex and convoluted, they require entire research reports to fully explain the definition. To simplify things a bit, I've developed a somewhat easier definition that will scale nicely with current technological trends.
A weapon is autonomous if makes its own decisions.
This makes autonomous weapons different than the weapons we have today. Although many of the weapons we use today are smart, they don't make decisions on their own. They are simply following the instructions of their human beings that made them. This means that when a precision guided munition (PGM) is fired at a target, it is simply following the instructions it was given (relentlessly, terminator style) until it finds its target. In contrast, autonomous weapons develop their own ways of solving problems. They can accomplish this by mining big data sets, interacting with simulations and through real world exercise.
This should sound familiar. Think for a moment about how you learned to throw and catch a ball. You didn't need a formal education to learn this or knowledge of physics or math to do it. You learn to do it by doing it. You learned it through experience. These new weapons can do the same thing. They can learn to do something by doing it. The simple fact that these new weapons can build their own ways to accomplish missions and they aren't reliant on human beings for the instructions/models/approaches necessary to do it, makes them autonomous.
October 19, 2015
Beyond Automation
There's been a big change in the wind for a decade. Many of us have heard and felt it rumbling in the background, shaking the foundations of an already decrepit global socioeconomic system.
Depending on how you view the world, you see it differently. I see it as as technological transformation. A technological transformation that will upend everything.
Here's a taste of what is driving this change forward. It's real and it's coming.
>>
Up until three hundred years ago, the world relied on the work being done by people, largely by hand. The skills and methods required to do this work were largely inside the minds of the people doing that work. We created organizations to aggregate the people needed for doing work on a large scale and guilds to protect this knowledge.
To overcome the limits of a world made by hand, we developed something new: automation. We've transformed the world by building machines (in both hardware and software) that do work for us. Automation is based on a scientific process that figures out how things work and an engineering process that turns these scientific ideas into machines that actually do work.
However, we've now reached the limits of automation. How so? Automation is limited by the ability of human beings to construct the cognitive models (both scientific and engineering) needed to build the machines that provide it.
To overcome these limits, we're now building cognitive machines that can build their own models for how things work and how to accomplish tasks. Unlike the machines that provide us with automation, these machines aren't built in the traditional way and they can tackle problems far more complex than anything done by automation.
The big change is that these machines build themselves. They bootstrap their abilities in the same way human beings do: through learning, training, and experience. However, they can learn it MUCH faster (deep learning) than we do and once they do, they can share their new abilities with other machines all over the world instantly (cloud robotics).
If you don't think this is a big deal, you are wrong. It's the biggest shift in technology we've seen since the rise of automation over three hundred years ago and it's going to change everything. In particular, it's going to upend the rules of economics, warfare, and politics we thought were immutable.

August 18, 2015
The Snowden Effect
Since Snowden fled the US in May of 2013, the US has experienced an increasingly brazen series of massive cyber attacks by criminal groups and nation-states. These include (there are many more not listed):
Target.
Sony.
The Internal Revenue Service.
The Office of Personnel Management
The Joint Chiefs of Staff
The reason for this is simple. The US has lost its ability to deter cyber attacks.
Why?
Snowden, or more specifically, the US response to Snowden's theft.
What did the US do to Snowden after he fled the US with the equivalent of the crown jewels of national security data?
Nothing. Crickets.
This response told the world, in no uncertain terms, that the US will do NOTHING when it and its companies are hacked.
Unfortunately for us, that message is toxic is deterrence.
Deterrence is an important concept. The entire security system of the modern world is based on the effectiveness of nuclear deterrence. It's why we haven't had global conventional wars since World War 2. Wars that might have killed billions if they had occurred.
For deterrence (a psychological method of warfare) to be effective, it needs to be credible. The potential attacker needs to know his/her victim will respond with overwhelming force.
Cyber deterrence works the same way. Until Snowden, the US had credibility. A credibility gained by decades of holding the line during the Cold War and a slightly crazy response to 9/11 (in deterrence, being seen as crazy is often beneficial).
After the non-response to Snowden, the US lost all credibility. It showed that it was unwilling or incapable of responding to cyber attack.
At that moment, the US opened the floodgates to all potential cyber attackers and they have responded with glee.
The ability of the US to deter cyber attack has vanished and there is absolutely no way that this or the next administration is going to do anything to fix it.
We can expect to see many more, and increasingly aggressive attacks in the future. Unfortunately, the folks in charge won't be paying the price for this abject failure.
We will.
June 24, 2015
The OPM Infobomb Explodes
A couple of years ago I wrote a short post InfoBomb.
When a government or corporation collects so much information on a citizenry that the unintentional release, theft, or misuse of it is a catastrophic event.
The most immediate danger from the government collecting data on us isn't that they will use it against us... it is from the damage it will do when they inevitably lose control of it.
This analysis was spot on: the failure at the Office of Personnel Management (OPM) is an infobomb.
Chinese hackers were able to steal records on 18 m current and former government employees + sensitive background information submitted by people applying for security clearances.
I believe this infobomb has done catastrophic damage to US security. How? Big data + bots (made smarter via AI) will be able to turn this data into a decisive instrument of warfare.
For example: want that guy on the button to stand down?
Call him up with a threat to his family. Threaten to release information on him. Etc.
Worse, through automation this can be done on a scale and with a speed far, far greater than what old school spooks are capable of.
Mark my words: This infobomb is a catastrophe.
A catastrophe we won't understand the consequences of until the US loses the next big conflict.
PS: If you are interested in seeing how incompetent, unrepentant, pretentious, and dangerous government bureaucrats can be, watch the Director of OPM Katherine "it's not my fault" Archuleta in action. Her behavior is very similar to what we saw from the big bankers after the 2008 meltdown. Her recent Congressional testimony is emblematic of why Wall Street bankers and Washington bureaucrats are the #1 threat to our future prosperity.
March 2, 2015
It's Open Season on the Tech Elite
Battles between the corporate allies of hollow nation-states and the gangs and tribes of black globalization are at the center of this century's epochal war. That war will eventually put the senior executives of US tech and financial companies in the crosshairs. Here's a good example. Over the weekend, ISIS threatened the life of Jack Dorsey, a co-founder and Chairman of Twitter. Why? Twitter, at the urging of the US government, has been shutting down the accounts of ISIS supporters for months. So, ISIS supporters responded by making a threat with a nifty graphic:
We told you from the beginning it’s not your war, but you didn't get it and kept closing our accounts on Twitter, but we always come back. But when our lions come and take your breath, you will never come back to life
The CEO as an Objective of War
Unfortunately for the suits in Silicon Valley, ISIS isn't as much of a pushover as al Qaeda was. They have mass and momentum and they are smart enough to understand the role of the Internet in this struggle. Additionally, they have lots of experience coercing CEOs and other senior executives. They did it quite a bit of it during the war in Iraq (and it worked).
Regardless, the targeted killing of a well known tech executive in sunny California by ISIS jihadis does appear impossible to imagine. Few places are more remote from each other, and not just geographically. Silicon Valley is a hyperconnected, financially mainlined zone striving for a tech nirvana. ISIS is a disconnected autonomous zone striving to return to the 7th Century. However, that's probably a bad assumption. Charlie Hebdo showed the world that terrorism is evolving and corporate targeting on global scale is now on the agenda. This means an attack on a tech CEO isn't just possible, but probable. Worse, once an attack on a senior tech executive happens, future threats will be instantly credible and highly coercive.
If that occurs, we are going to find out very quickly that the corporation, and particularly tech companies, are particularly bad organizations for warfare. One reason is that they are too centralized. In particular, the institution of the CEO is a grave weakness (a systempunkt in global guerrilla lingo). The CEO's centrality to the corporate network makes him/her a single point of failure for the entire organization. Another is that executives in most of the western world are very soft targets. Easy to find (Google and Google maps), easy to isolate, and easy to kill...
February 27, 2015
Leaving the Global Grid And Being Arrested For It
Larry Fink, the CEO of BlackRock, controls about $4.3 trillion in assets (and has influence on how $10 trillion more is allocated). As a point of reference, that is about the size of the entire US economy.
Larry sees the world as a tightly interconnected "financial grid." Larry believes that a big part of his job is to know which parts of this global grid represent opportunities and which parts are dangerous.
That makes sense. Asset allocation accounts for about ~80% of any big financial fund's performance and BlackRock's extraordinary success implies that Larry has been getting it right for decades.
What's interesting to me is the mindset. For example: Larry dismisses the threats posed by Russia adventures in the Ukraine. Why?
He understands that all of the people involved in this conflicts are part of his financial grid. He also knows that everyone is utterly dependent on the financial flows coursing through it. They couldn't get through the day at work and at home without it.
So, to him, this dependence means that Russia isn't an actual threat, but merely a problem to be dealt with.
In contrast, Larry does see one threat as real and tangible: ISIS. Why?
ISIS isn't connected or dependent on the "grid." Worse, it's growing like a geographical cancer that can severely damage the grid.
This idea. The fear that a growing part of the world is being taken off the grid gives guys like Larry nightmares.
I don't think he is alone. It apparently gives more people than just Larry nightmares.
For example. Three men were arrested in New York this week, and will likely serve long prison sentences.
They weren't arrested because they were plotting an attack on the US or any other site in any meaningful way.
Instead, they were arrested because they planned to leave the US. They tried to drop off the grid by emigrating to ISIS and the government put them in jail for trying it.
It's an interesting twist.

PS: Thanks so much for all of the great thinking on drone warfare and protest. Working through the responses right now.
February 25, 2015
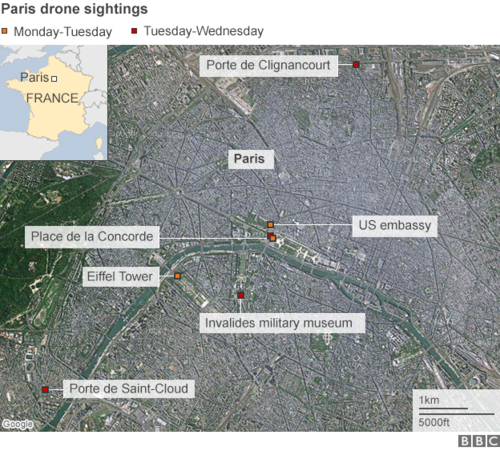
Drones over Paris
For two nights, up to five drones were spotted over landmarks in Paris. French police weren't able to track down the drones or the owners due to the difficulty of tracing their flight paths while on the ground. In response, a task force has been formed to focus on this "threat." Even the US secret service has been called in as consultants (although their track record with drones is pretty terrible).
This event demonstrates, yet again, that drones allow:
easy (with gps navigation, they can fly themselves),
low cost (hundreds, not thousands of dollars),
survivable (not being caught) access to any site.
Of course, drones have limitations:
short flight time,
slow speed, and
small payload (1-2 pounds).
The big questions:
how can small, consumer drones to disrupt urban environments?
given trends in drone technology, how could they be used for disruption and warfare in the near future (5-10 years)?
how can drones be used to advance protest?
I'd like to open these questions up to the 60,000 active readers of this site (from all over the world). IF you can write down a fictional scenario in a less than thousand words send it to me at
systemdisruption-web@yahoo.com
I'll publish the best ones on GG or do something even more interesting with them.

February 23, 2015
Three Saudi Options
Saudi Arabia sees ISIS as an existential threat. It has a reason to be scared, ISIS is a Wahabi jihad with updated technologies (social media) and techniques (open development). That means when push comes to shove, Saudi troops will either a) turn tail and run or b) join up in droves. To avoid this, the Saudis might attempt something radical:
Build a completely useless multi-billion dollar wall around the country. Oh wait, they are already doing that.
Ramp support for al Qaeda. Optimally, a big al Qaeda on a western target would force the US to fully engage ISIS, since ISIS is a physical target and al Qaeda isn't. Was al Qaeda's attack on Charlie Hebdo (and the Jewish deli) a Saudi funded endeavor to start the process?
Hire western mercenaries to push ISIS around. Erik Prince has been trying to sell this option for years and is waiting in the wings to get it going. A few billion spent this way might be sufficient to turn the tide on ISIS.
The Middle East doesn't Matter Anymore
Back in 2003, the US was headed towards complete dependence on foreign oil. Additionally, the demand for energy (particularly from China) was growing far faster than production, which meant an energy price spike was inevitable.
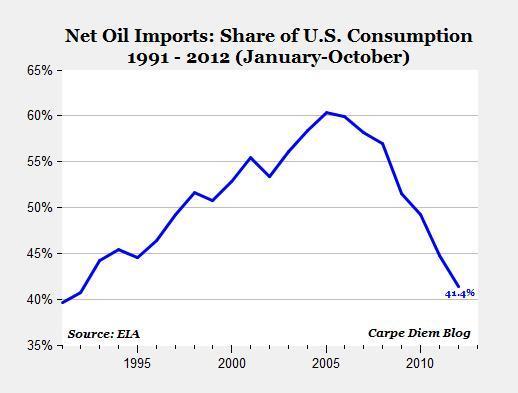
Of course, this could be avoided if another big source of oil was found and exploited. However, based on existing production technology, the only big fields left untapped were in Iraq, but due to sanctions (limiting production to 2m barrels a day, far less than the 8 m bpd projected to be possible).
The result was inevitable. The US invaded Iraq to free up production (that's largely why the fields were secured in the first couple of days of the invasion), but it screwed up. The national security "brain-trust" didn't anticipate that the Iraqi guerrillas would disrupt this production so effectively (I covered this in detail on this blog and in my book). The result? Iraq produced less oil, for years after the invasion, than it did under sanctions.
That loss of production in combination with disruption caused by Nigerian guerrillas (who copied the success of the Iraqis), produced an energy crunch that drove the global economy into a massive recession. Worse, this recession became a decade long depression due to the disruption caused by the banks and hedge funds we allow to hack the global financial system.
One of the benefits of this oil crunch was that high prices spurred technological innovation that led to an upheaval in the US energy system over the last decade. New technology has enabled US oil and natural gas production to boom. Not only that, this tech enables energy production to scale industrially -- that's a big change if you understand the implications.
The most immediate benefit of a return to US energy autonomy has been lower natural gas, oil, and gasoline prices (autonomy that will only grow as solar zooms). However, there's other benefits that should be obvious too. Since the US isn't dependent on Middle Eastern energy anymore, US national security policy will be decoupled from Middle Eastern conflicts. Like it or not, this is inevitable.
What does this mean?
If the US does get involved in Middle East conflicts it's due to outdated policy and doctrine.
Nobody in the West will do anything to stop the spread of ISIS (as a humanitarian crisis it rates well below Rwanda).
Saudi Arabia is going to get desperate to get the US to intervene. It sees ISIS as an existential threat. How will it do that? I've got some ideas...
February 14, 2015
The Open Jihad
Over the past couple of weeks, the open jihad has taken ground in Libya, Nigeria, Syria, and Iraq. It's ongoing success is due to innovations developed by a large and growing number of contributing groups. Groups like:
ISIS affiliated forces in Syria, Iraq, Libya, Afghanistan, and Yemen to
Boko Haram in Nigeria to
ISIS and AQ affiliated terrorist groups inside Saudi Arabia, UK, Egypt, etc.
Open jihad evolves (gets better) through massively parallel co-development. All of the groups in the open jihad, no matter how small (even down to individuals), can contribute. They do this by:
tinkering with tactics, strategies, and technologies that can be used to advance the open jihad.
testing the efficacy of these innovations by using them against the enemy. In other words, throwing them against the wall to see what sticks.
copying the innovations that work.
The groups in the open jihad can communicate successful innovations without even using the forms of communication we pay the NSA tens of billions a year to spy on. Instead, they communicate successful innovation through a process called stigmergy (which we do surprisingly little to analyze). I first wrote about stigmergy back in 2004. That earlier description is still valid today.
Stigmergy is a term used in biology (from the work of french biologist Pierre-Paul Grasse) to describe environmental mechanisms for coordinating the work of independent actors (for example, ants use pheromones to create trails and people use weblog links to establish information paths, for others to follow). The term is derived from the greek words stigma ("sign") andergon ("to act"). Stigmergy can be used as a mechanism to understand underlying patterns in swarming activity. As such, it can be applied to the understanding of swarming attacks by diverse bands of attackers. A knowledge of stigmergy is a key to understanding how these groups learn. Stigmergic systems use simple environmental signals to coordinate that actions of independent agents (each with their own decision making process). These signals are used to coordinate scalable, robust, and dynamic activity. This activity is often much more intelligent that the actions capable by the individual actors (in this case individual global guerrilla groups). There are four basic mechanisms used in stigmergic communication. They are:
Marker-based. Markers or signs left by actors influence the action of other actors. In the GG (global guerrilla) context this is the site of an attack and the news of the attack that is delivered by the media. The description of the attack in the media is stigmergic marker for others to follow.
Sematectonic. Environmental conditions influence the behavior of all actors in the system. For GGs, multiple attacks on a certain type of target can generate a security response by the nation-state that changes the potential of attacks against that type of target in the immediate future. An increased security presence for those types of targets is a sema-tectonic signal to select something else.
Quantitative. The environmental signals are of a single scalable type. The size of a Global Guerrilla attack on a given location can meter the scale of the security response.
Qualitative. The environmental signals are of a varied type. They message changes based on their combination. Different types of attacks on the same target will yield information on the type of attack that is the most effective.

PS: We have a tendency to dismiss tinkering as a foolish endeavor. All of the great breakthroughs in modern technology have been found through tinkering -- from airplanes to cars to PCs to telephones to anti-biotics to electricity -- and not through investment in big, industrial labs.
John Robb's Blog
- John Robb's profile
- 17 followers