Stone Marshall's Blog, page 122
December 22, 2017
The Last Jedi Petition Ignores Luke’s Amazing Character Arc
Star Wars: The Last Jedi has lit the internet up with both praise and critique, an overflow of love and hate. It’s actually pretty poetic, considering a theme of the movie is about finding a balance between light and dark. As the debate continues a large petition circulating online right now focuses on Luke’s actions and argues the portrayal of the Jedi is so horrid, Disney should scrap the record-breaking box office hit from the official canon and completely redo the story. These people are wrong.
 Watch out! Spoilers below! Photo: Player.One
Watch out! Spoilers below! Photo: Player.One WARNING: Full The Last Jedi spoilers ahead. Read at your own risk.
The crux of the argument for the petition is that The Last Jedi depicted Luke Skywalker, and therefore the entire Jedi order, as less than pure good. “ It completely destroyed the legacy of Luke Skywalker and the Jedi. It destroyed the very reasons most of us, as fans, liked Star Wars,” the petition argues. “[R]e-make Episode VIII properly to redeem Luke Skywalker’s legacy, integrity, and character.”
The problem, if you haven’t seen the movie and are still reading this article, is Luke attempted to kill Ben Solo back when he was training his young nephew. Luke’s justification for this move is because he saw the evil lurking in Solo, and wanted to eradicate it before it could spread. Ironically, Skywalker’s actions further fueled Solo’s quest for power and was the driving reason for Solo to turn into his alter ego Kylo Ren.
If that moment felt off to you, like Luke was abandoning the ways of the Jedi and becoming evil, then congratulations. That’s how you’re supposed to feel. Luke even feels this, which is why he decided to run away to a small corner of the galaxy and hide for the rest of his life. He knew he did something wrong, and couldn’t face the repercussions of his actions, especially from Han and Leia.
This point is driven home even further when Rey shows up, asking what happened to the legendary Luke Skywalker. The rebellion is failing and the Ultimate Hero is needed once again to come save the day. However, Luke knows he isn’t what people want him to be. He can’t be the force of pure good people think he is, because of his actions in the past. He’s flawed, he’s human.
If this makes you stop and look critically at who your heroes are, that’s a good thing. Allegations against many notable people like Louis C.K., Al Franken and Matt Lauer have made us rethink if those we look up to should be put on pedestals and trumpeted as our favorites.
The petition ends with the line “let us keep our heroes.” Maybe our heroes know they have reason to not be seen as such. Maybe it’s time to make some new heroes.
So what do you think? Are you still upset with what The Last Jedi did to Luke Skywalker? Do you like the flawed portrayal of a man who is capable of error? Let us know your thoughts in the comments section below, but please keep it civil.
New Jumanji Mobile Board Game Is Actually Pretty Fun
Movie releases and casual mobile games seem to go hand in hand these days, so it’s no surprise the new Jumanji: Welcome to the Jungle film has a companion mobile game. In my experience, the majority of movie-themed mobile games turn out to be uninspired money grabs, so I went into Jumanji with some tacit eye-rolling. However, after spending a little time with the game, I was happy to discover it isn’t half bad. In fact, once I got a handle on the rules, it became downright fun..
 Jumanji: The Mobile Game manages to pull the best parts of Monopoly and apply them to a mobile CCG that’s surprisingly fun to play. Photo: Player.One
Jumanji: The Mobile Game manages to pull the best parts of Monopoly and apply them to a mobile CCG that’s surprisingly fun to play. Photo: Player.One The best way I can describe Jumanji: The Mobile Game is a mashup of Monopoly and Hearthstone, but simpler. While the combination may sound terrible, it actually comes off quite well in Jumanji. The game board consists of 12 spaces. 10 of them are like Monopoly properties you can purchase and then set up camp. Each time you pass START, you’ll earn income off these properties, so acquiring as many as you can becomes a central goal. The other two spaces are special features, similar to the corners in Monopoly. These change as the game progresses. Sometimes they are punitive and landing on them will cause you to be imprisoned and miss a turn. Others can give you boosts like gold coins or the ability to move to any spot you choose on the board.
Like Monopoly, the object of the game is to monopolize the board, forcing your opponent into bankruptcy. What makes Jumanji ingenious, however, is that it solves a major Monopoly gameplay problem that puts many people off. When you first start playing Monopoly, it can be fun, but once a player has gained control of the board, the outcome is unavoidable and inevitable. If you are the loser, you’ll be subjected to hours of tedious torture as your opponent slowly bleeds you dry of your resources.
 In Jumanji, when landing on an opponent’s property you can either pay a toll or attack. Photo: Player.One
In Jumanji, when landing on an opponent’s property you can either pay a toll or attack. Photo: Player.One Jumanji solves this problem by offering more options for what can happen when you land on an opponent’s property. Players have the option to pay a toll or attack the other player. If they choose to attack (which everyone pretty much does), then players move to an RPG-style dice battle. If your attack is higher than your opponent’s defense score, you win the fight and with it, not only steal that player’s property, but also some of his or her gold.
But the battle isn’t solely dependant on the toss of a dice. In fact, attacks are where the Hearthstone -like CCG elements come into play. Going into a game, each player takes with them a deck of six cards. These cards make up your team and each have varying amounts of attack and defense points, as well as special skills. When you purchase a property, its base defense level is the same as your team’s combined defense points. In the same way, when you make an attack, your base attack is equal to the combined attack points of your team. When an attack occurs, your base points are added to your dice roll and whichever player’s total is higher wins the match. When a game ends, whichever player wins will be awarded a backpack full of resources, including new cards you can unlock or duplicates used for upgrading cards.
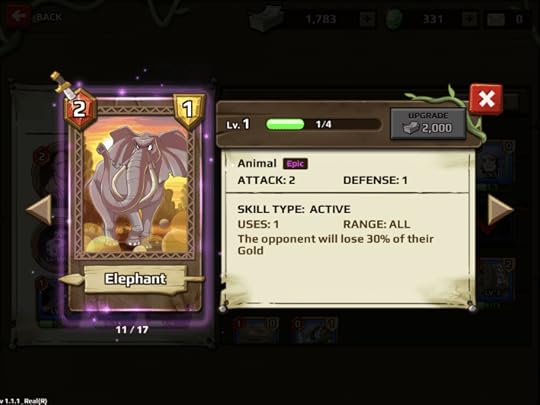 Assessing a card’s skills becomes important in deciding which to add to your deck. Photo: Player.One
Assessing a card’s skills becomes important in deciding which to add to your deck. Photo: Player.One In the first stage of Jumanji, this is as complex as the rules get, but Stage 2 introduces to skills, which add a greater element of strategy to the game. Each card in your deck comes with a particular skill that is either passive or active. Passive skills go into action under certain conditions (ex: increase defense by 1 during the day), while active skills can only be used once during a game. These include everything from destroying an opponent’s base to stealing coins and more. Some of these skills prove quite useful and become a key factor in putting together your team. You also get to choose one of four heroes for your game, each with a starting perk like additional coins or heightened attack scores.
Since Jumanji is meant to be played in five to 15 minutes, the developers have added two additional ways of winning the game if you can’t manage to bankrupt your opponent. 1) Gain control of all properties in a set, creating a monopoly or 2) have the most money at the end of 12 rounds.
My biggest complaint with Jumanji is the opening tutorial lacked information about how to play and the strategy behind the game, which could be off-putting to new players. If you stick in there though, you’ll soon discover that Jumanji is a satisfying online multiplayer game. If you enjoy casual games that combine both luck and strategy this one is worth checking out. You can download Jumanji now for free on either the Apple App or Google Play store.
December 21, 2017
The Gifted’s Emma Dumont Thinks There’s No Happy Ending
Every conversation, every scene in The Gifted has a larger meaning. It’s what makes the X-Men series feel so big, despite being filled with lesser known characters. The fall finale was no different. The Stepford Cuckoos make their debut, telepathically forcing more than a dozen Sentinel Services agents to open fire on one another. This happens only hours after Agent Turner’s lengthy, and somewhat enlightening, conversation with the Strucker parents that culminated in an agreement to transport the captured Mutant Underground’s allies away from Trask Industries where Dreamer was murdered.
“It was very important the conversation included the wives,” series star Emma Dumont told Player.One. “We’ve seen conversation between Jace and Reed. It’s bigger than just these men and their egos, there are bigger risks. And it foreshadows that the X-Men say a war is coming — this scene specifically shows it may not just be a war between two parties. What does that mean for the mutant underground and the Struckers, and what does it mean for Lorna? There are so many factors that we get into in the last three episodes.”
 Sonia aka Dreamer was Lorna’s best friend. Dumont says her death will greatly affect Polaris in the upcoming episodes. Photo: Fox
Sonia aka Dreamer was Lorna’s best friend. Dumont says her death will greatly affect Polaris in the upcoming episodes. Photo: Fox At this point in the series, we don’t know much about the deadly “7/15” event that is tied to the disappearance of the X-Men and the Brotherhood, but the nature of the Stepford Cuckoos’ introduction was so ruthless, so dark, there’s no doubt Agent Turner is done hearing out the Mutant Underground.
“We can talk about 7/15 all day long and obviously understand what it’s a reference to, but until we actually see a mutant commit a horrible crime like this, we aren’t gonna understand why Jace is the hero of his own story,” she said. “The fact that this sweet little blonde girl could make armed, trained men do these things — it’s terrifying. But not only can she can do it, she will do it. We could kill each other every day of our lives, but we don’t, because we have empathy. That’s what makes us different than other animals. But to see someone who really doesn’t have that… The audience needed to see it.”
 Esme revealed herself as one of the Stepford Cuckoos and murdered dozens of Sentinel Service agents to save her sisters. Photo: Fox
Esme revealed herself as one of the Stepford Cuckoos and murdered dozens of Sentinel Service agents to save her sisters. Photo: Fox Dumont explains the scene highlights The Gifted’ s ongoing exploration of prejudice. You cannot blame an entire group, especially an entire minority group, for the terrible actions of one person. But for Polaris, the incident was particularly jarring because the Stepford Cuckoos actions are sort of an irrational version of her own Magento-esque mutant code. It’s a kill-or-be-killed world, but there are rules.
“If you are using your mutant ability, using mayhem and violence and chaos, and you are not saving someone… Lorna thinks it’s fine, kill Hitler, it’s totally fine, but if you are doing things that don’t benefit other people, that is disgraceful. Reed, in her mind, isn’t helping anyone. Putting those mutants away, ripping up families, those are bad things and they are not redeemable,” Dumont said. “However, if someone like Magneto were to kill one bad human and save hundreds of innocent mutant lives, that is okay with her, she sees the good in that. It’s a very sketchy fine line, but to her it’s very clear thinking. Lorna thinks it makes total sense.”
 Eclipse and Polaris have been dating for many years, but that’s not to say they are on the same page. Photo: Fox
Eclipse and Polaris have been dating for many years, but that’s not to say they are on the same page. Photo: Fox Eclipse doesn’t see it that way, and his relationship with Polaris illustrates the dynamic between Professor X and Magneto (and their real life counterparts) from the comics and cinematic universe.
“It’s an exact parallel to Professor X and Magento. Marcos wants peace. He will sit by and have change happen slowly. He thinks any change is good change, and Lorna won’t have it. She definitely believes if we all started acting a lot more, using our powers and taking a stand. If that means violence than so be it. But if things continue the way Marcos wants them to continue, then things will never change,” Dumont continued.
“The difference between slavery and current-day hate crime, it’s a difference but we are still living in a world where horrible things happening to minority groups — innocent people being hurt and killed — and it’s not okay. And Marcos sees those two time periods and says, ‘Oh, but look how different it is now? Now, people don’t own mutants, they just abuse them and hurt them.’ But to Lorna that’s an awful way of thinking. She thinks if you stand for nothing, you’ll fall for anything. She has a very Magento way of thinking politically. In the eyes of justice, that’s the right thing to do.”
 Dr. Roderick-Campbell is a researcher for Trask Industries and wants to learn more about the Strucker children’s powers. Photo: Fox
Dr. Roderick-Campbell is a researcher for Trask Industries and wants to learn more about the Strucker children’s powers. Photo: Fox Like Magento, Polaris isn’t even sure there is a place for people like Strucker — who have only recently displayed a willingness to understand the mutant cause — to be part of the way society moves forward to create equality.
“Someone that’s been raised up in bigotry, who now works for the government, not only do they do that because they are passionate about ‘protecting the general public,’ they are paid to do this. They get paid to hurt people. So, of course, the end goal we all say is to make this a peaceful environment for mutants and humans to live in together. But Lorna doesn’t know if that is possible. She’s almost to the point where she thinks these people need to be taken away,” she said.
 Sentinel Services Agent Jace Turner’s daughter was killed in the 7/15 incident. Photo: Fox
Sentinel Services Agent Jace Turner’s daughter was killed in the 7/15 incident. Photo: Fox The X-Men universe is defined by what exists between love and hate. Mutant discrimination never stops, political initiatives are never enough to incite real social change, the scientific experiments only get more invasive — and The Gifted will be no different.
“There will never be a happy ending, especially in the X-Men universe,” said Dumont. “The fall finale was heartbreaking in every way imaginable. On an individual level, people start to get what they want, but then in the overall goal of making peace between mutants and humans, it sort of falls apart.”
Dumont teases big things for the last few episodes, including an internal struggle about her character’s place in surviving such an oppressive world — a story arc Dumont isn’t shy to compare to that of Magneto. With a child on the way, Polaris will finally come to terms with what she believes needs to be done.
“She has this reputation, but finally now she’s at a place where she doesn’t care. She doesn’t care if you don’t like things about her because she is right. And she hates that she’s right — we will see this in the last few episodes — she hates that Magneto was right. She wishes it wasn’t this way, but it is, and she has to do what she has to do.”
The Gifted returns Jan. 1.
Watch Agents Of SHIELD Season 5 Episode 5 To See Lance Hunter Return
The Marvel’s Wanted pilot starring Lance Hunter and Mockingbird didn’t pan out, yet thankfully, Agents of SHIELD has found a way to bring a beloved team member we haven’t seen since Season 3 back to the series. Nick Blood will return as Hunter in episode 5, “Rewind.”
The new promo reveals Hunter’s return, and that Fitz has been held in captivity for six months. We don’t know who these people are (they look like military), but they have forced Fitz to help them find the missing SHIELD agents. Fitz has yet to come up with any plausible theories — the only thing he can come up with is that they’ve been abducted by aliens.
“You want to find them to bring them to justice, I want to find them so I know they are okay.”
Bring who to justice? It seems like a lifetime ago, but if you remember back to the Season 4 finale and the whole AIDA framework ordeal… there’s no question government officials need answers about what happened. Before the team was abducted, Fitz even offered to take the blame for messing with the Darkhold. But before he and Coulson can finish their discussion, the bald guy appears and next thing you know, everyone except Ftiz is in space. Even though AIDA and the Framework is Fitz’ fault, SHIELD is still on the hook and it appears the government officials are convinced they are on the run. And when Fitz said he thinks SHIELD was abducted by aliens, the woman tells him to enjoy spending his life in a cell.
Thankfully, Lance Hunter comes to the rescue. According to Blood, Lance and Fitz are integral to helping the team return from space.
“Oh yeah, I don’t think Fitz could have managed it without him — or at least that’s what I think Hunter tells himself ,” Blood told TV Line. “Fitz is very grateful to see him, despite the fact that some of his ideas don’t go quite according to plan.”
Unfortunately, it’s unlikely we’ll see Mockingbird join the fight. Adrianne Palicki is busy in The Orville, but who knows, maybe ABC is saving her return as a surprise. Blood did reveal his characters is at least still in touch with Bobbi.
“Well, he’s been up his usual tricks, doing some mercenary work and bickering with Bobbi… He doesn’t necessarily have access to all the bells-and-whistles and gadgetry that S.H.I.E.L.D. did, so he has to use his charm and his wit to break down doors, and call in a few favors from his dodgy friends — who at times are quite unreliable!”
The next episode of Agents of SHIELD airs at 9 p.m. on Friday. Are you excited for Lance’s return? Let us know in the comments.
Watch Agents Of SHIELD Season 5 Episode 5 To See Lance Hunter Return
December 20, 2017
Minecraft Marketplace Holiday Update Coming Thursday, Says Mojang
The holiday spirit will come to the Minecraft Marketplace before week’s end, announced developer Mojang on Tuesday. All of the content featured in the announcement will be premium DLC (because why would one of the best selling games in history give anything away for free?), and features a theme to celebrate Christmas in the world’s most popular sandbox game.
First up is the new Norse Mythology Mash-Up Pack, a relatively self-explanatory new addition to the list of Minecraft visual overhauls. The new mash-up pack lets Minecraft players visit blocky versions of the Great Hall, Hel, Yggdrasil and other iconic locales from Norse mythology. New skins include a who’s who of the Norse pantheon, from Odin and Thor to Sif and Heimdall, along with lesser mainstays like wolf and bearskin-clad berserkers. The Norse Mythology Mash-Up Pack also includes reskins for a shockingly long list of enemy mobs.
Mojang also highlights a sprawling array of new community-created holiday content on the Marketplace this week. Beginning Thursday, players will find mods who will invite them to winter festivals, join a pirate’s Christmas celebration or take a ride in Santa’s sleigh. Although than a dozen unique Minecraft add-ons will be part of the holiday promotion, today’s announcement didn’t include pricing information for any of the upcoming Marketplace content. A handful of the holiday additions are currently available, but the vast majority will arrive on/after Dec. 21.
It’s a bit disappointing to see that Mojang will not follow the lead of the many other studios, like Io Interactive and Blizzard, which release holiday content free of charge. The Minecraft Marketplace may have been created to give the community’s growing legion of content creators a chance to make a living (or at least some side income) off their work, but that doesn’t mean Mojang can’t produce a separate batch of holiday-themed content too. Most players probably wouldn’t want a holiday update if it meant slowing development of Minecraft Update 1.13. But it’s still a disappointing follow-up to last year’s Festive Mash-Up Pack.
Minecraft is currently available on PlayStation 3, PS4, Xbox 360, Xbox One, Nintendo Switch, PS Vita, the New 3DS, PC and numerous smart devices.
Be sure to check back with Player.One and follow Scott on Twitter for more Minecraft news in 2018 and however long Mojang supports Minecraft in the years ahead.
Minecraft Marketplace Holiday Update Coming Thursday, Says Mojang
Minecraft video game gets big content update in time for the holidays
Minecraft has updated across the Xbox One family of consoles with a variety of changes and new content.
In addition to the new Norse Mythology Mashup Pack, the update also adds a Festive Tumble Arena where gamers can celebrate the holiday season. This update also changes some mechanics involving cauldrons, potions, water, and world generation that should please many Minecraft fans. Here’s the official release notes for this update.
Added Norse Mythology Mashup Pack.
Added Festive Tumble Arena.
Added New Horse Model.
Added Dyeable Leather Horse Armour.Cauldron changes
Cauldrons can be filled with potions.
Tipped Arrows can be created using an Arrow with Cauldrons filled with potions.
Water can be dyed.
Armour can be dyed in a Cauldron filled with dyed water.Baby Zombie jockeys can now ride any mobs.
World generation changes
Added Fallen Trees & Dying Trees.
Village Changes.
Tables have brown carpet instead of a pressure plate.
Added Ice Plains & Cold Taiga Villages.
Added Chests to Ice Plains and Cold Taiga Villages.
Ice Plains & Cold Taiga Villages won’t generate crops.
Paths around village wells now made up of grass path (sandstone in desert).
Dispenser changes.
Fireworks will fire in the direction the dispenser is facing.
Mob heads will drop to ground unless they are being placed on a block that would cause a Wither or Snow Golem to spawn.Updated Wither Boss behavior
Explodes and spawns Wither Skeletons on half health.
Change to dash attack.
Remove health regeneration.
New birth and death animations.
Armor Stands now have arms and multiple poses.
Do you play Minecraft on an Xbox One? Let us know if you like the console experience in the comments below.
Minecraft video game gets big content update in time for the holidays
December 19, 2017
Minecraft was the reason the Mirai botnet was created
“These kids are super smart, but they didn’t do anything high level—they just had a good idea. It’s the most successful IoT botnet we’ve ever seen—and a sign that computer crime isn’t just about desktops anymore.”
– FBI supervisory special agent Bill Walton on the creators of the Mirai botnet.
Wired recently published a piece interviewing several people who were involved in analyzing and investigating the biggest cyber security breach of 2016, caused by three college-aged individuals who were looking to gain an advantage in Minecraft by creating the Mirai botnet malware.
FBI supervisory special agent Bill Walton describes how the trio didn’t intend to create this sort of chaos. “Mirai was originally developed to help them corner the Minecraft market, but then they realized what a powerful tool they built,” he explains. “Then it just became a challenge for them to make it as large as possible.”
The creators of Mirai targeted French Internet provider OVH because it offered Minecraft DDoS mitigation tools and certain servers. “Why are these Minecraft servers getting hit so often?” FBI special agent Elliott Peterson remembers asking.
“The digital arms race in DDoS is inexorably linked to Minecraft,” says FBI special agent Doug Klein. “You look at the servers—those guys are making huge money, so it’s in my benefit to knock your server offline and steal your customers. The vast majority of these Minecraft servers are being run by kids—you don’t necessarily have the astute business judgment in the quote-unquote ‘executives’ running these servers.”
The piece also dives into how investigators tracked down the main culprit behind Mirai, as well as highlighting other servers and companies the malware infected during its reign.
December 18, 2017
How a Dorm Room Minecraft Scam Brought Down the Internet
It was a hard story to miss last year: In France last September, the telecom provider OVH was hit by a distributed denial-of-service (DDoS) attack a hundred times larger than most of its kind. Then, on a Friday afternoon in October 2016, the internet slowed or stopped for nearly the entire eastern United States, as the tech company Dyn, a key part of the internet’s backbone, came under a crippling assault.
As the 2016 US presidential election drew near, fears began to mount that the so-called Mirai botnet might be the work of a nation-state practicing for an attack that would cripple the country as voters went to the polls. The truth, as made clear in that Alaskan courtroom Friday—and unsealed by the Justice Department on Wednesday—was even stranger: The brains behind Mirai were a 21-year-old Rutgers college student from suburban New Jersey and his two college-age friends from outside Pittsburgh and New Orleans. All three—Paras Jha, Josiah White, and Dalton Norman, respectively—admitted their role in creating and launching Mirai into the world.
Originally, prosecutors say, the defendants hadn’t intended to bring down the internet—they had been trying to gain an advantage in the computer game Minecraft.
“They didn’t realize the power they were unleashing,” says FBI supervisory special agent Bill Walton. “This was the Manhattan Project.”
Unraveling the whodunit of one of the internet’s biggest security scares of 2016 led the FBI through a strange journey into the underground DDoS market, the modern incarnation of an old neighborhood mafia-protection racket, where the very guys offering to help today might actually be the ones who attacked you yesterday.
Then, once the FBI unraveled the case, they discovered that the perpetrators had already moved onto a new scheme—inventing a business model for online crime no one had ever seen before, and pointing to a new, looming botnet threat on the horizon.
The first rumors that something big was beginning to unfold online came in August 2016. At the time, FBI special agent Elliott Peterson was part of a multinational investigative team trying to zero in on two teens running a DDoS attack-for-hire service known as vDOS. It was a major investigation—or at least it seemed so at the time.
‘They didn’t realize the power they were unleashing.’
Bill Walton, FBI
VDOS was an advanced botnet: a network of malware-infected, zombie devices that its masters could commandeer to execute DDoS attacks at will. And the teens were using it to run a lucrative version of a then-common scheme in the online gaming world—a so-called booter service, geared toward helping individual gamers attack an opponent while fighting head-to-head, knocking them offline to defeat them. Its tens of thousands of customers could pay small amounts, like $5 to $50, to rent small-scale denial-of-service attacks via an easy-to-use web interface.
Yet as that case proceeded, the investigators and the small community of security engineers who protect against denial-of-service attacks began to hear rumblings about a new botnet, one that eventually made vDOS seem small.
As Peterson and industry colleagues at companies like Cloudflare, Akamai, Flashpoint, Google, and Palo Alto Networks began to study the new malware, they realized they were looking at something entirely different from what they’d battled in the past. Whereas the vDOS botnet they’d been chasing was a variant of an older IoT zombie army—a 2014 botnet known as Qbot—this new botnet appeared to have been written from the ground up.
And it was good.
“From the initial attacks, we realized this was something very different from your normal DDoS,” says Doug Klein, Peterson’s partner on the case.
The new malware scanned the internet for dozens of different IoT devices that still used the manufacturers’ default security setting. Since most users rarely change default usernames or passwords, it quickly grew into a powerful assembly of weaponized electronics, almost all of which had been hijacked without their owners’ knowledge.
“The security industry was really not aware of this threat until about mid-September. Everyone was playing catch-up,” Peterson says. “It’s really powerful—they figured out how to stitch together multiple exploits with multiple processors. They crossed the artificial threshold of 100,000 bots that others had really struggled with.”
It didn’t take long for the incident to go from vague rumblings to global red alert.
Mirai shocked the internet—and its own creators, according to the FBI—with its power as it grew. Researchers later determined that it infected nearly 65,000 devices in its first 20 hours, doubling in size every 76 minutes, and ultimately built a sustained strength of between 200,000 and 300,000 infections.
“These kids are super smart, but they didn’t do anything high level—they just had a good idea,” the FBI’s Walton says. “It’s the most successful IoT botnet we’ve ever seen—and a sign that computer crime isn’t just about desktops anymore.”
Targeting cheap electronics with poor security, Mirai amassed much of its strength by infecting devices in Southeast Asia and South America; the four main countries with Mirai infections were Brazil, Colombia, Vietnam, and China, according to researchers. As a team of security professionals later concluded, dryly, “Some of the world’s top manufacturers of consumer electronics lacked sufficient security practices to mitigate threats like Mirai.”
At its peak, the self-replicating computer worm had enslaved some 600,000 devices around the world—which, combined with today’s high-speed broadband connections, allowed it to harness an unprecedented flood of network-clogging traffic against target websites. It proved particularly tough for companies to fight against and remediate, too, as the botnet used a variety of different nefarious traffic to overwhelm its target, attacking both servers and applications that ran on the servers, as well as even older techniques almost forgotten in modern DDoS attacks.
No one had any idea yet who its creators were, or what they were trying to accomplish.
On September 19, 2016, the botnet was used to launch crushing DDoS attacks against French hosting provider OVH. Like any large hosting company, OVH regularly saw small-scale DDoS attacks—it noted later that it normally faces 1,200 a day—but the Mirai attack was unlike anything anyone on the internet had ever seen, the first thermonuclear bomb of the DDoS world, topping out at 1.1 terabits per second as more than 145,000 infected devices bombarded OVH with unwanted traffic. The company’s CTO tweeted about the attacks afterward to warn others of the looming threat.
Until then, a large DDoS attack was often considered to be 10 to 20 gigibits per second; vDOS had been overwhelming targets with attacks in the range of 50 Gbps. A follow-on Mirai attack against OVH hit around 901 Gbps.
Mirai was particularly deadly, according to court documents, because it was able to target an entire range of IP addresses—not just one particular server or website—enabling it to crush a company’s entire network.
“Mirai was an insane amount of firepower,” Peterson says. And no one had any idea yet who its creators were, or what they were trying to accomplish.
Normally, companies fight a DDoS attack by filtering incoming web traffic or increasing their bandwidth, but at the scale Mirai operated, nearly all traditional DDoS mitigation techniques collapsed, in part because the tidal wave of nefarious traffic would crash so many sites and servers en route to its main target. “DDOS at a certain scale poses an existential threat to the internet,” Peterson says. “Mirai was the first botnet I’ve seen that hit that existential level.”
Through September, the inventors of Mirai tweaked their code—researchers were later able to assemble 24 iterations of the malware that appeared to be primarily the work of the three main defendants in the case—as the malware grew more sophisticated and virulent. They actively battled the hackers behind vDOS, fighting for control of IoT devices, and instituting kill procedures to wipe competing infections off compromised devices—natural selection playing out at internet speed. According to court documents, they also filed fraudulent abuse complaints with internet hosts associated with vDOS.
“They were trying to outmuscle each other. Mirai outperforms all of them,” Peterson says. “This crime was evolving through competition.”
Whoever was behind Mirai even bragged about it on hacker bulletin boards; someone using the moniker Anna-senpai claimed to be the creator, and someone named ChickenMelon talked it up as well, hinting that their competitors might be using malware from the NSA.
Days after OVH, Mirai struck again, this time against a high-profile technology target: security reporter Brian Krebs. The botnot blasted Krebs’ website, Krebs on Security, knocking it offline for more than four days with an attack that peaked at 623 Gbps. The assault was so effective—and sustained—that Krebs’ longtime DDoS mitigation service, Akamai, one of the largest bandwidth providers on the internet, announced it was dropping Krebs’ site because it couldn’t bear the cost of defending against such a massive barrage. The Krebs attack, Akamai said, was twice the size of the largest attack it had ever seen before.
Whereas the OVH attack overseas had been an online curiosity, the Krebs attack quickly pushed the Mirai botnet to the FBI’s front burner, especially as it seemed likely that it was retribution for an article Krebs had published just days earlier about another DDoS-mitigation firm that appeared to be engaged in nefarious practices, hijacking web addresses that it believed were being controlled by the vDOS team.
“This is strange development—a journalist being silenced because someone has figured out a tool powerful enough to silence him,” Peterson says. “That was worrisome.”
The IoT attacks began to make big headlines online and off; media reports and security experts speculated that Mirai might have the fingerprints of a looming attack on the internet’s core infrastructure.
“Someone has been probing the defenses of the companies that run critical pieces of the internet. These probes take the form of precisely calibrated attacks designed to determine exactly how well these companies can defend themselves, and what would be required to take them down,” wrote security expert Bruce Schneier in September 2016. “We don’t know who is doing this, but it feels like a large nation-state. China or Russia would be my first guesses.”
Behind the scenes, the FBI and industry researchers raced to unravel Mirai and zero in on its perpetrators. Network companies like Akamai created online honeypots, mimicking hackable devices, to observe how infected “zombie” devices communicated with Mirai’s command-and-control servers. As they began to study the attacks, they noticed that many of the Mirai assaults had appeared to target gaming servers. Peterson recalls asking, “Why are these Minecraft servers getting hit so often?”
The question would lead the investigation deep into one of the internet’s strangest worlds, a $27 game with an online population of registered users—122 million—larger than the entire country of Egypt. Industry analysts report 55 million people play Minecraft each month, with as many as a million online at any given time.
The game, a three-dimensional sandbox with no particular goals, allows players to construct entire worlds by “mining” and building with cartoonish pixelated blocks. Its comparatively basic visual appeal—it has more in common with the first-generation videogames of the 1970s and 1980s than it does the polygon-intense lushness of Halo or Assassin’s Creed—belies a depth of imaginative exploration and experimentation that has propelled it to be the second-best-selling videogame ever, behind only Tetris. The game and its virtual worlds were acquired by Microsoft in 2014 as part of a deal worth nearly $2.5 billion, and it has spawned numerous fan sites, explanatory wikis, and YouTube tutorials—even a real-life collection of Minecraft-themed Lego bricks.
‘They were trying to outmuscle each other. Mirai outperforms all of them.’
Elliott Peterson, FBI
It has also become a lucrative platform for Minecraft entrepreneurs: Inside the game, individual hosted-servers allow users to link together in multiplayer mode, and as the game has grown, hosting those servers has turned into big business—players pay real money both to rent “space” in Minecraft as well as purchase in-game tools. Unlike many massive multiplayer games where every player experiences the game similarly, these individual servers are integral to the Minecraft experience, as each host can set different rules and install different plug-ins to subtly shape and personalize the user experience; a particular server, for instance, might not allow players to destroy one another’s creations.
As Peterson and Klein explored the Minecraft economy, interviewing server hosts and reviewing financial records, they came to realize how amazingly financially successful a well-run, popular Minecraft server could be. “I went into my boss’s office and said, ‘Am I crazy? It looks like people are making a ton of money,’” he recalls. “These people at the peak of summer were making $100,000 a month.”
The huge income from successful servers had also spawned a mini cottage industry of launching DDoS attacks on competitors’ servers, in an attempt to woo away players frustrated at a slow connection. (There are even YouTube tutorials specifically aimed at teaching Minecraft DDoS, and free DDoS tools available at Github.) Similarly, Minecraft DDoS-mitigation services have sprung up as a way to protect a host’s server investment.
The digital arms race in DDoS is inexorably linked to Minecraft, Klein says.
“We see so many attacks on Minecraft. I’d be more surprised sometimes if I didn’t see a Minecraft connection in a DDoS case,” he says. “You look at the servers—those guys are making huge money, so it’s in my benefit to knock your server offline and steal your customers. The vast majority of these Minecraft servers are being run by kids—you don’t necessarily have the astute business judgment in the quote-unquote ‘executives’ running these servers.”
As it turned out, French internet host OVH was well-known for offering a service called VAC, one of the industry’s top Minecraft DDoS-mitigation tools. The Mirai authors attacked it not as part of some grand nation-state plot but rather to undermine the protection it offered key Minecraft servers. “For a while, OVH was too much, but then they figured out how to even beat OVH,” Peterson says.
This was something new. Whereas gamers had become familiar with one-off DDoS attacks by booter services, the idea of DDoS as a business model for server hosts was startling. “This was a calculated business decision to shut down a competitor,” Peterson says.
“They just got greedy—they thought, ‘If we can knock off our competitors, we can corner the market on both servers and mitigation,’” Walton says.
In fact, according to court documents, the primary driver behind the original creation of Mirai was creating “a weapon capable of initiating powerful denial-of-service attacks against business competitors and others against whom White and his coconspirators held grudges.”
Once investigators knew what to look for, they found Minecraft links all over Mirai: In an less-noticed attack just after the OVH incident, the botnet had targeted ProxyPipe.com, a company in San Francisco that specializes in protecting Minecraft servers from DDoS attacks.
“Mirai was originally developed to help them corner the Minecraft market, but then they realized what a powerful tool they built,” Walton says. “Then it just became a challenge for them to make it as large as possible.”
On September 30, 2016, as public attention piqued following the Krebs attack, the maker of Mirai posted the malware’s source code to the website Hack Forum, in an attempt to deflect possible suspicions if he was caught. The release also included the default credentials for 46 IoT devices central to its growth. (Malware authors will sometimes release their code online to muddy investigators’ trail, ensuring that even if they’re found to possess the source code, authorities can’t necessarily identify them as the original author.)
That release opened the tool for use by a wide audience, as competing DDoS groups adopted it and created their own botnets. All told, over five months from September 2016 through February 2017, variations of Mirai were responsible for upwards of 15,194 DDoS attacks, according to an after-action report published in August.
As the attacks spread, the FBI worked with private-industry researchers to develop tools that allowed them to watch DDoS attacks as they unfolded, and track where the hijacked traffic was being directed—the online equivalent of the Shotspotter system that urban police departments use to detect the location of gunshots and dispatch themselves toward trouble. With the new tools, the FBI and private industry were able to see a looming DDoS attack unfold and help mitigate it in real time. “We really depended on the generosity of the private sector,” Peterson says.
The decision to open source Mirai also led to its most high-profile attack. The FBI says Jha, White, and Dalton were not responsible for last October’s DDoS of the domain name server Dyn, a critical piece of internet infrastructure that helps web browsers translate written addresses, like Wired.com, into specific numbered IP addresses online. (The FBI declined to comment on the Dyn investigation; there have been no arrests publicly reported in that case.)
‘I’d be more surprised sometimes if I didn’t see a Minecraft connection in a DDoS case.’
Doug Klein, FBI
The Dyn attack paralyzed millions of computer users, slowing or stopping internet connections up and down the East Coast and interrupting service across North America and parts of Europe to major sites like Amazon, Netflix, Paypal, and Reddit. Dyn later announced that it might never be able to calculate the full weight of the assault it faced: “There have been some reports of a magnitude in the 1.2 Tbps range; at this time we are unable to verify that claim.”
Justin Paine, the director of trust and safety for Cloudflare, one of the industry’s leading DDoS mitigation companies, says that the Dyn attack by Mirai immediately got the attention of engineers across the internet. “When Mirai really came on the scene, the people who run the internet behind the scenes, we all came together,” he says “We all realized that this isn’t something that just affects my company or my network—this could put the entire internet at risk. Dyn affected the entire internet.”
“The concept of unsecured devices to be repurposed by bad guys to do bad things, that’s always been there,” says Paine, “but the sheer scale of insecure modems, DVRs, and webcams in combination with how horribly insecure they were as device really did a present a different kind of challenge.”
The tech industry began intensively sharing information, both to help mitigate ongoing attacks as well as working to backtrack and to identify infected devices to begin remediation efforts. Network engineers from multiple companies convened an always-running Slack channel to compare notes on Mirai. As Paine says, “It was real-time, we were using Slack, sharing, ‘Hey, I’m on this network seeing this, what are you seeing?’”
The power of the botnet was made even more clear as the fall unfolded and Mirai attacks targeted the African country of Liberia, effectively cutting off the entire country from the internet.
Many of these follow-on attacks also appeared to have a gaming angle: A Brazilian internet service provider saw its Minecraft servers targeted; the Dyn attacks also appeared to target gaming servers, as well as servers hosting Microsoft Xbox Live and Playstation servers and those associated with gaming hosting company called Nuclear Fallout Enterprises. “The attacker was likely targeting gaming infrastructure that incidentally disrupted service to Dyn’s broader customer base,” researchers later declared.
“Dyn got everyone’s attention,” says Peterson, especially as it represented a new evolution—and a new unknown player fiddling with Anna-senpai’s code. “It was the first truly effective post-Mirai variant.”
The Dyn attack catapulted Mirai to the front pages—and brought immense national pressure down on the agents chasing the case. Coming just weeks before the presidential election—one in which US intelligence officials had already warned about attempts by Russia to interfere—the Dyn and Mirai attacks led officials to worry that Mirai could be harnessed to affect voting and media coverage of the election. The FBI team scrambled for a week afterward with private-industry partners to secure critical online infrastructure and ensure that a botnet DDoS couldn’t disrupt Election Day.
The plague unleashed by Mirai’s source code continued to unfold across the internet last winter. In November, the German company Deutsche Telekom saw more than 900,000 routers knocked offline when a bug-filled variant of Mirai accidentally targeted them. (German police eventually arrested a 29-year-old British hacker in that incident.) Yet the various competing Mirai botnets undercut their own effectiveness, as an increasing number of botnets fought over the same number of devices, eventually leading to smaller and smaller—and therefore less effective and troubling—DDoS attacks.
What Anna-senpai didn’t realize when he dumped the source code was that the FBI had already worked through enough digital hoops to finger Jha as a likely suspect, and had done so from an unlikely perch: Anchorage, Alaska.
That one of the big internet stories of 2016 would end up in an Anchorage courtroom last Friday—guided by assistant US attorney Adam Alexander to a guilty plea barely a year after the original offense, a remarkably rapid pace for cybercrimes—was a signal moment itself, marking an important maturation in the FBI’s national approach to cybercrimes.
Until recently, nearly all of the FBI’s major cybercrime prosecutions came out of just a handful of offices like Washington, New York, Pittsburgh, and Atlanta. Now, though, an increasing number of offices are gaining the sophistication and understanding to piece together time-consuming and technically complex internet cases.
Peterson is a veteran of the FBI’s most famous cyber team, a pioneering squad in Pittsburgh that has put together groundbreaking cases, like that against five Chinese PLA hackers. On that squad, Peterson—an energetic, hard-charging, college computer science major and Marine Corps adjutant who deployed twice to Iraq before joining the bureau, and now serves on the FBI Alaska SWAT team—helped lead the investigation into the GameOver Zeus botnet that targeted Russian hacker Evgeny Bogachev, who remains at large with a $3 million reward for his capture.
Often, FBI agents end up being pulled away from their core specialties as their career advances; in the years after 9/11, one of the bureau’s few dozen Arabic-speaking agents ended up running a squad investigating white supremacists. But Peterson stayed focused on cyber cases even as he transferred nearly two years ago back to his home state of Alaska, where he joined the FBI’s smallest cyber squad—just four agents, overseen by Walton, a longtime Russian counterintelligence agent, and partnering with Klein, a former UNIX systems administrator.
The tiny team, though, has come to take on an outsized role in the country’s cybersecurity battles, specializing in DDoS attacks and botnets. Earlier this year, the Anchorage squad was instrumental in the take-down of the long-running Kelihos botnet, run by Peter Yuryevich Levashov, aka “Peter of the North,” a hacker arrested in Spain in April.
In part, says Marlin Ritzman, the special-agent-in-charge of the FBI’s Anchorage Field Office, that’s because Alaska’s geography makes denial-of-service attacks particularly personal.
“Alaska’s uniquely positioned with our internet services—a lot of rural communities depend on the internet to reach the outside world,” Ritzman says. “A denial-of-service attack could shut down communications to entire communities up here, it’s not just one business or another. It’s important for us to attack that threat.”
Putting together the Mirai case was slow going for the four-agent Anchorage squad, even while they worked closely with dozens of companies and private sector researchers to piece together a global portrait of an unprecedented threat.
Before they could solve an international case, the FBI squad first—given the decentralized way that federal courts and the Justice Department work—had to prove that Mirai existed in their particular jurisdiction, Alaska.
To establish the grounds for a criminal case, the squad painstakingly located infected IoT devices with IP addresses across Alaska, then issued subpoenas to the state’s main telecom company, GCI, to attach a name and physical location. Agents then criss-crossed the state to interview the owners of the devices and establish that they hadn’t given permission for their IoT purchases to be hijacked by the Mirai malware.
While some infected devices were close by in Anchorage, others were further afield; given Alaska’s remoteness, collecting some devices required plane trips to rural communities. At one rural public utility that also provided internet services, agents found an enthusiastic network engineer who helped track down compromised devices.
‘I’ve run against some really hard guys, and these guys were as good or better than some of the Eastern Europe teams I’ve gone against.’
Elliott Peterson, FBI
After seizing the infected devices and transporting them to the FBI field office—a low-slung building just a few blocks from the water in Alaska’s most populous city—agents, counterintuitively, then had to plug them back in. Since Mirai malware exists only in flash memory, it was deleted every time the device was powered off or restarted. The agents had to wait for the device to be reinfected by Mirai; luckily, the botnet was so infectious and spread so rapidly that it didn’t take long for the devices to be reinfected.
From there, the team worked to trace the botnet’s connections back to the main Mirai control server. Then, armed with court orders, they were able to track down associated email addresses and cell phone numbers used for those accounts, establishing and linking names to the boxes.
“It was a lot of six degrees of Kevin Bacon,” Walton explains. “We just kept stepping down that chain.”
At one point, the case bogged down because the Mirai authors had established in France a so-called popped box, a compromised device that they used as an exit VPN node from the internet, thereby cloaking the actual location and physical computers used by Mirai’s creators.
As it turned out, they’d hijacked a computer that belonged to a French kid interested in Japanese anime. Given that Mirai had, according to a leaked chat, been named after a 2011 anime series, Mirai Nikki, and that the author’s pseudonym was Anna-Senpai, the French boy was an immediate suspect.
“The profile lined up with someone we’d expect to be involved in the development of Mirai,” Walton says; throughout the case, given the OVH connection, the FBI worked closely with French authorities, who were present as some of the search warrants were conducted.
“The actors were very sophisticated in their online security,” Peterson says. “I’ve run against some really hard guys, and these guys were as good or better than some of the Eastern Europe teams I’ve gone against.”
Adding to the complexity, DDoS itself is a notoriously difficult crime to prove—even simply proving the crime ever happened can be extraordinarily challenging after the fact. “DDoS can happen in a vacuum, unless a company captures logs in the right way,” Peterson says. Klein, a former UNIX administrator who grew up playing with Linux, spent weeks piecing together evidence and reassembling data to show how the DDoS attacks unfolded.
On the compromised devices, they had to carefully reconstruct the network traffic data, and study how the Mirai code launched so-called “packets” against its targets—a little-understood forensic process, known as analyzing PCAP (packet capture) data. Think of it as the digital equivalent of testing for fingerprints or gunshot residue. “It was the most complex DDoS software I’ve run across,” Klein says.
The FBI zeroed in on the suspects by the end of the year: Photos of the three hung for months on the wall in the Anchorage field office, where agents dubbed them the “Cub Scout Pack,” a nod to their youthfulness. (Another older female suspect in an unrelated case, whose photo also hung on the board, was nicknamed the “Den Mother.”)
Security journalist Brian Krebs, an early Mirai victim, publicly fingered Jha and White in January 2017. Jha’s family initially denied his involvement, but on Friday he, White, and Norman all pleaded guilty to conspiracy to violate the Computer Fraud and Abuse Act, the government’s main criminal charge for cybercrime. The pleas were unsealed Wednesday, and announced by the Justice Department’s computer crimes unit in Washington, DC.
Jha was also accused of—and pleaded guilty to—a bizarre set of DDoS attacks that had disrupted the computer networks on the Rutgers campus for two years. Beginning in the first year Jha was a student there, Rutgers began to suffer from what would ultimately be a dozen DDoS attacks that disrupted networks, all timed to midterms. At the time, an unnamed individual online pushed the university to purchase better DDoS mitigation services—which, as it turns out, was exactly the business Jha himself was trying to build.
In a Trenton courtroom Wednesday, Jha—wearing a conservative suit and the dark-rimmed glasses familiar from his old LinkedIn portrait—told the court that he aimed attacks against at his own campus when they would be most disruptive—specifically during midterms, finals, and when students were trying to register for class.
“In fact, you timed your attacks because you wanted to overload the central authentication server when it would be the most devastating to Rutgers, right?” the federal prosecutor queried.
“Yes,” Jha said.
Indeed, that the three computer savants ended up building a better DDoS mousetrap isn’t necessarily surprising; it was an area of intense intellectual interest for them. According to their online profiles, Jha and White had actually been working together to build a DDoS-mitigation firm; the month before Mirai appeared, Jha’s email signature described him as “President, ProTraf Solutions, LLC, Enterprise DDoS Mitigation.”
As part of building Mirai, each member of the group had his own role, according to the court documents. Jha wrote much of the original code and served as the main online point of contact on hacking forums, using the Anna-senpai moniker.
White, who used the online monikers Lightspeed and thegenius, ran much of the botnet infrastructure, designing the powerful internet scanner that helped identify potential devices to infect. The scanner’s speed and effectiveness was a key driver behind Mirai’s ability to outcompete other botnets like vDOS last fall; at the peak of Mirai, an experiment by The Atlantic found that a fake IoT device the publication created online was compromised within an hour.
According to court documents, Dalton Norman—whose role in the Mirai botnet was unknown until the plea agreements were unsealed—worked to identify the so-called zero-day exploits that made Mirai so powerful. According to court documents, he identified and implemented four such vulnerabilities unknown to device manufacturers as part of Mirai’s operating code, and then, as Mirai grew, he worked to adapt the code to run a vastly more powerful network than they’d ever imagined.
‘We all realized that this isn’t something that just affects my company or my network—this could put the entire internet at risk.’
Justin Paine, Cloudflare
Jha came to his interest in technology early; according to his now deleted LinkedIn page, he described himself as “highly self-motivated” and explained that he began to teach himself programming in seventh grade. His interest in science and technology ranged widely: The following year, he won second prize in the eighth-grade science fair at Park Middle School in Fanwood, New Jersey, for his engineering project studying the impact of earthquakes on bridges. By 2016, he listed himself as proficient in “C#, Java, Golang, C, C++, PHP, x86 ASM, not to mention web ‘browser languages’ such as Javascript and HTML/CSS.” (One early clue for Krebs that Jha was likely involved in Mirai was that the person calling themself Anna-Senpai had listed their skills by saying, “I’m very familiar with programming in a variety of languages, including ASM, C, Go, Java, C#, and PHP.)
This is not the first time that teens and college students have exposed key weaknesses in the internet: The first major computer worm was unleashed in November 1988 by Robert Morris, then a student at Cornell, and the first major intrusion into the Pentagon’s computer networks—a case known as Solar Sunrise—came a decade later, in 1998; it was the work of two California teens in concert with an Israeli contemporary. DDoS itself emerged in 2000, unleashed by a Quebec teen, Michael Calce, who went online by the moniker Mafiaboy. On February 7, 2000, Calce turned a network of zombie computers he’d assembled from university networks against Yahoo, then the web’s largest search engine. By mid-morning it had all but crippled the tech giant, slowing the site to a crawl, and in the days following, Calce targeted other top websites like Amazon, CNN, eBay, and ZDNet.
On a conference call announcing the guilty pleas Wednesday, Justice Department Acting Deputy Assistant Attorney General Richard Downing said that the Mirai case underscored the perils of young computer users who lose their way online—and said that the Justice Department planned to expand its youth outreach efforts.
“I’ve certainly been made to feel very old and unable to keep up,” prosecutor Adam Alexander joked Wednesday.
What really surprised investigators, though, was that once they had Jha, White, and Norman in their sights, they discovered that the creators of Mirai had already found a new use for their powerful botnet: They’d given up DDoS attacks for something lower-profile—but also lucrative.
They were using their botnet to run an elaborate click-fraud scheme—directing about 100,000 compromised IoT devices, mostly home routers and modems, to visit advertising links en masse, making it appear that they were regular computer users. They were making thousands of dollars a month defrauding US and European advertisers, entirely off the radar, with no one the wiser. It was, as far as investigators could tell, a groundbreaking business model for an IoT botnet.
As Peterson says, “Here was a whole new crime that industry was blind to. We all missed it.”
Even as the case in Alaska and New Jersey wraps up—the three defendants will face sentencing later on—the Mirai plague that Jha, White, and Dalton unleashed continues online. “This particular saga is over, but Mirai still lives,” Cloudflare’s Paine says. “There’s a significant ongoing risk that’s continued, as the open source code has been repurposed by new actors. All these new updated versions are still out there.”
Two weeks ago, at the beginning of December, a new IoT botnet appeared online using aspects of Mirai’s code.
Known as Satori, the botnet infected a quarter million devices in its first 12 hours.
These MINECRAFT Low-Res Pixelated Funko POP!s Are Amazing
We often fawn over the intricate design elements of Funko’s vinyl figurines and really can’t fathom the journey one of these collectibles takes from initial drawing to their final home on our shelves. Yet, every so often we’re floored by how awesome some of the simpler designs end up looking. Case in point, these Minecraft Pops! Funko’s done low-res figures before but there’s something about these Minecraft characters that works so perfectly. Their blocky design transfers perfectly into the tangible third dimension that it’s like they jumped right out of the screen.
Funko’s done low-res figures before but there’s something about these Minecraft characters that works so perfectly. Their blocky design transfers perfectly into the tangible third dimension that it’s like they jumped right out of the screen. As with most Funko lines, they’ve planned a bit of an “exclusive” hunt in order to get your hands on all these beauties. Once they hit stores in February of 2018, a glow version of Creeper can be found at FYE, a Charged Creeper at Gamestop, Walmart will have Steve in Gold Armor and Alex in Enchanted Armor, and you’ll have to head to Target to find the Skeleton with Fire.
As with most Funko lines, they’ve planned a bit of an “exclusive” hunt in order to get your hands on all these beauties. Once they hit stores in February of 2018, a glow version of Creeper can be found at FYE, a Charged Creeper at Gamestop, Walmart will have Steve in Gold Armor and Alex in Enchanted Armor, and you’ll have to head to Target to find the Skeleton with Fire. A real-life quest for these to adorn our shelves seems perfect for any Minecraft fan and is substantially easier than some of the accomplishments in the game. When players are so dedicated to a game they can create functional clocks, calculators, and accurate recreations of Westerosi locations from Game of Thrones—headed to a few different stores seems like a breeze.
A real-life quest for these to adorn our shelves seems perfect for any Minecraft fan and is substantially easier than some of the accomplishments in the game. When players are so dedicated to a game they can create functional clocks, calculators, and accurate recreations of Westerosi locations from Game of Thrones—headed to a few different stores seems like a breeze.
What do you think of these new Pop! figures? Which Minecraft elements would you like to see them produce in the future? Let’s discuss in the comments below!
December 17, 2017
After Two Years Minecraft Finally Gets A New World Record
Ender Dragon is Minecraft’s final boss, a serpentine collection of dark blocks that launches fireballs at the player. Minecraft speedrunners have long struggled with it, but this week speedrunners finally discovered how to bypass the Dragon altogether. It’s already led to a world record.
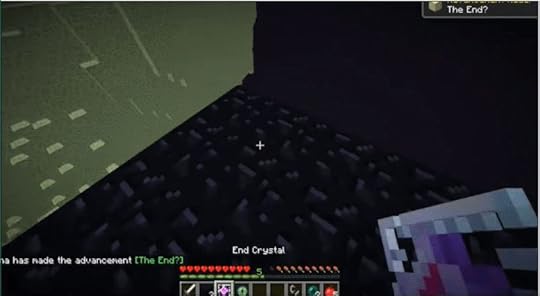
Part of what makes the fight against the Ender Dragon time consuming is a series of End Crystals that sit atop pillars and heal the Dragon when it flies near. However, players can also craft their own End Crystals and bring them into the final level to wreak havoc. Originally players were trying to place extra End Crystals in specific places to influence the Dragon’s path during the fight and also deal some extra damage (they can be exploded like land mines).
Recently, experimenting with this strategy yielded an even better discovery. Placing an End Crystal as soon as the player enters the Dragon’s level causes it to glitch and never spawn while still yielding the portal to the end credits that marks the completion of a run.
 [image error]
[image error]
Placing Crystals after the Dragon has already been defeated summons a new Dragon. If this happens, the game checks to see if the end portal that spawns after the battle is already there, in which case it doesn’t create one. However, timing things right can confuse the game. By placing the crystal before the battle starts, the player is able to trick the game into skipping the fight entirely. “Because we place the crystal before the Dragon fight is fully loaded, it fails to find evidence of another portal, and so it creates one,” explained the MineCraft glitch hunter Matthew Bolan.
A player by the name of Geosquare discovered the glitch by accident while researching a tool-assisted speedrun for the fight. His findings in turn helped one of the game’s most prolific speedrunners, Illumina, to break the world record of 4:07:400, held by Joshgaming4 and which had previously stood for over two years, with a 3:20.9 run.
“It was from mid 2015,” Illumina said in an email. “It was a very daunting time to beat and that’s why it stood for so long.” Illumina thinks the run still has room for improvement.
There’s a lot of randomness in a Minecraft speedrun, and speedrunners try to find the ideal parameters for spawning a new world. In Minecraft these parameters are known as seeds. Players select a seed at the beginning of a run, and they determine what flavor of map will be generated by the game. In Illumina’s case, using the new Ender Dragon glitch meant finding a seed that would give him a world conducive to crafting the necessary End Crystal. In addition to discovering the glitch, Geosquare also helped find the best seed for executing it.
“The seed was found by Geosquare by writing a program using variables that would make the seed optimal,” Illumina said. “He ran the program for about 5 minutes and they spent a couple hours looking through the seeds that came up. There is probably a better seed than the current one as it only took a couple hours to find, but when there are 2^64 seeds, it is not easy to go through all of them.”
Illumina’s world record was specifically in Minecraft’s “seeded” category. There are other categories that prohibit both glitches and seed optimization, but Illumina thinks that misses half the fun. “A benefit from [seeds] is that it keeps the category more interesting as you never know when a new seed would be found,” he said. “Some runners said that we should just stick to one seed to make one route consistent but I disagree in doing that.”
“Every category of this game is too RNG and takes a lot of grinding to get a great run,” said Illumina who’s been running the game since 2011. “But it’s always fun to see if you will get lucky in a run, kind of like gambling. It’s definitely much different of a game to run from any other I’ve seen. Things like the Dragon skip and seed optimization programs help marry the chaos of the game to the practiced skill expert players want to bring to it.”



