Brett Shavers's Blog, page 15
October 31, 2015
I had a blast presenting for ICAC at Microsot

 I gave two presentations today at the NW ICAC conference hosted by Microsoft in Redmond, Washington on the same topic in two parts. I met some great folks in the field doing so really awesome work to protect children. Plus, I got to see some people that I have not seen in a long time. All the sponsors set up a great conference with Microsoft providing the venue. I was only there for the first day and I'm sure the next two days will be just as beneficial to attendees.
I gave two presentations today at the NW ICAC conference hosted by Microsoft in Redmond, Washington on the same topic in two parts. I met some great folks in the field doing so really awesome work to protect children. Plus, I got to see some people that I have not seen in a long time. All the sponsors set up a great conference with Microsoft providing the venue. I was only there for the first day and I'm sure the next two days will be just as beneficial to attendees.  The first presentation (Part 1) was a broad overview of my first book,
Placing the Suspect Behind the Keyboard
. My primary goal was to give a ton of investigative tips in hopes that at least one will be able to save investigators hours (or weeks or months) of labor in their cases. I flew through the material like a firefighter putting out a house fire to make sure enough tips were given to fit as many investigators needed in their specific cases. Definitely covered a lot of ground in a short amount of time. Reading my book covers a lot more, but this was fun. [image error]
The first presentation (Part 1) was a broad overview of my first book,
Placing the Suspect Behind the Keyboard
. My primary goal was to give a ton of investigative tips in hopes that at least one will be able to save investigators hours (or weeks or months) of labor in their cases. I flew through the material like a firefighter putting out a house fire to make sure enough tips were given to fit as many investigators needed in their specific cases. Definitely covered a lot of ground in a short amount of time. Reading my book covers a lot more, but this was fun. [image error]  The second presentation (Part 2) was a brief intro to one chapter in my upcoming third book,
Hiding Behind the Keyboard
. Probably the best tips came from how to identify Tor users along with how to explain Tor to the layperson, which is sometimes one of the hardest things to do in a courtroom setting. Both Part 1 and Part 2 presentations are independent of each other but the information is complimentary just like both books are.
The second presentation (Part 2) was a brief intro to one chapter in my upcoming third book,
Hiding Behind the Keyboard
. Probably the best tips came from how to identify Tor users along with how to explain Tor to the layperson, which is sometimes one of the hardest things to do in a courtroom setting. Both Part 1 and Part 2 presentations are independent of each other but the information is complimentary just like both books are. If you are in law enforcement and would like a copy of both presentations, you can download them here for the next month or so before I update the presentations:
Placing the Suspect Behind the Keyboard-ICAC.
Send me a message after you download the file and I'll e-mail you the password (the slidedeck will be available for short time).
Read More
October 24, 2015
Book Review: Windows Forensic Analysis Toolkit, 4th Edition
 I’ve been waiting until I received the hard copy of this book to write the review. I had the fortune of being the tech editor for this book and enjoyed every minute of it. Although I do not have an ongoing financial interest in this book, I do have a vested personal interest based on the reasons Harlan Carvey lays out in many chapters. I’ll get to my personal interest later in this review. Also, Harlan has a post on updated book contents here: http://regripper.wordpress.com/2014/04/14/regripper-download-2/
I’ve been waiting until I received the hard copy of this book to write the review. I had the fortune of being the tech editor for this book and enjoyed every minute of it. Although I do not have an ongoing financial interest in this book, I do have a vested personal interest based on the reasons Harlan Carvey lays out in many chapters. I’ll get to my personal interest later in this review. Also, Harlan has a post on updated book contents here: http://regripper.wordpress.com/2014/04/14/regripper-download-2/
Without reading any reviews, those analysts who buy Harlan’s books will keep buying his books with the full expectation of having a well-written (as in easy-to-read) book on Windows OS forensics. There is no need to read any further in this review if you fit in this category. This is Harlan’s new book. That is all you really need to know. But if you just want my opinion, read on…
The topics in the 4th Edition of WFA are all eye-catching. Volume shadow copies, file analysis, registry, malware, timelines, tracking user activity, and more. Every topic detailed in all the chapters, is relevant to everyone that touches a Windows system to examine. The difference between Harlan’s books and others is the guidance given. For example, rather than reading a discourse on some technology, Harlan gives practical advice, suggestions, and real-life stories that relate to the points in the book. Since we have all made mistake (or will make mistakes, or have made mistakes but just don’t know it yet), having guidance that reduces mistakes in the way of stories and plain talk is well worthwhile to read.
The book has too much information to be covered in a review. There is more information on accessing volume shadow copies using several different methods than I want to review. The same can be said for file analysis, registry analysis, timelines, and every other topic. Harlan gives several options to accomplish the same task, using different software. Although I wrote a book on one software (X-Ways Practitioners Guide), I obviously use more than just one software. Any forensic book, other than a manual or software guide, that does not give options with various types of software does not give the reader options to solve problems.
Another facet of Harlan’s book is his never-ending harping of asking everyone to ‘share information’. That sentence may sound negative, but truthfully, I don’t know how Harlan has the energy to push the sharing of information for so long. The book is sprinkled with this tone and I echo the importance of sharing information. I did my best to keep up with Harlan’s book as I tech edited it, working his suggestions. Some of the methods he wrote were new to me, which I would not have found on my own without happening upon the method in a blog..maybe.
Those examiners who conduct investigations, not just an analysis of a machine, will enjoy the guidance on tracking user activity, writing reports, drawing conclusions, correlating data, and making inferences. Those topics are my personal favorites.
Harlan writes in this book that sharing helps us to know what is possible. That makes sense, because how can you know what you don’t know.
I can say unequivocally that writing a digital forensics book is primarily, if not solely, to share information. Few (no one?) gets rich writing a computer technical book in the niche of digital forensics. The market for a digital forensic book is probably a fraction of a fraction of a fraction when compared to a Tom Clancy or JK Rowling book. With that, consider that when Harlan says he writes to share, he really means that he writes to share, just like all other forensic book writers.
The personal risk to sharing, which everyone knows, is that you could be totally wrong, slightly inaccurate, poorly written, disproved later, or maybe you “discovered” something that everyone else already knew. This risk of sharing keeps the majority of examiners quiet and makes it seem that there are only a few examiners that share information. That is why we see the same names popping up online and conferences through the years. But in the audiences listening to these same names, there are smarter people, better examiners, and great investigators. They just don’t speak up or share information. (nudge..nudge...feel free to share...no one will bite you).
That is one of Harlan’s premises to keep going and he reiterates it in the book and his blog and when he speaks. We all get ‘smarter’ when we share. None of us move forward when we don’t share. To share is to take a risk of being wrong and embarrassed. Worse still is the fear to be wrong and get attacked online. However, for all those that share, either by asking questions, giving suggestions, or describing methods you have created or use, my hat goes off to you. It takes guts to put yourself out there, knowing that the sharks are circling and sniffing for blood.
Back to my personal interest in this book. When I have found a method or tool that I like, I want everyone to use it. I don’t hold it close to my chest or hide it. I share it. I become an evangelist to that tool or method to get the word out. The reason? The more examiners in the field that use it, the more chance the method/tool becomes an industry standard. Then it gets improved upon, further developed, “court accepted” in that the results obtained by that tool/method are accepted into a court, and I get to use the tool/method more.
The best personal example I can give to prove this point is with WinFE (http://winfe.wordpress.com). From a two-page Word document typed by Troy Larson of Microsoft, I marketed that little ingenious tool as if I was making a million bucks off it. It’s now in use by every country that does forensics and in just about every agency or company in those countries. It’s even taught in forensic training programs in both the public and private sector. So now, anyone can create and use WinFE without worry of using a non-industry accepted tool. This happened only because those that used WinFE, shared the knowledge of how to use and when to use it. Imagine if we did that with every “new” effective method or tool.
The key point in the prior two paragraphs is that Harlan’s book has lots of those types of ideas that he has shared. He gives credit to ideas created by others along with sharing his own ideas.
My only negative words on WFA/4 is…maybe X-Ways Forensics could have been put in it...but that's what we have the XWF Guide for..
My suggestion on WFA/4…buy the book. You will not regret it. My other favorite books are here http://winfe.wordpress.com/books/.
Read More
November 25, 2014
C4All X-tension update
Update November 14, 2014
Download link to version 3.6.2.d https://www.dropbox.com/s/zewn7myskf…6.2.d.zip?dl=0
This update changes the way the video stills are treated when extracting movies.
-now video stills are extracted if the parent movie is extracted, regardless of whehter
the video still has been type verified.
That is for version 3.6.2.d that fixes a few issues with C4All not handling some characters.
Videos and links to updated guides.
Steps for c4all X-tension updated November 2014.doc
www.dropbox.com/s/sfd3…4.doc?dl=0
Steps to prepare and run C4All X november 2014.doc
www.dropbox.com/s/23ts…4.doc?dl=0
I recommend downloading both guides. ***both Udpated November 2014***
Links to Youtube videos to run X-Tension
www.youtube.com/watch?v=HP6DTzpG0KI – part 1 of 3
www.youtube.com/watch?v=zCIcrA9CldI – part 2 of 3
www.youtube.com/watch?v=53cLlcogr40 – part 3 of 3
October 19, 2014
Updates to X-tension and Hash File Manipultator
Hashbrown program 64 bit version only http://1drv.ms/1tLsNnG updated October 10 2014
instructions http://1drv.ms/XNdgeJ
-New Version that handles many duplicates and many unsorted more efficiently posted.
X-tension
Update October 19 2014
download link to version 3.6.2.c http://1drv.ms/1prWU2h
-Fixed issue with extended character support of UTF-16 in XML. should show all but those 0xD800 – 0xDFFF characters.
-Adds the functions of 3.5.12.k as well as option to create a Picture/video library based on MD5 hash value as name and the option to include not confirmed files when extracting pictures and movies. (before the file had to have a type status of Confirmed or newly identified. see post from 27 September in this thread for more details)
– 3.5.12.k
option to include or not include metadata in XML
-The option to run against multiple evidence objects and better naming of folders in c4all folder tree.
-CETS users have toggle to create a CETS XML or not.

September 30, 2014
New version of X-Tension
New version of X-Tension
3.6.2.a http://1drv.ms/1rrCJ7s
Changes
-adds the functionality to create a picture/video library.
-adds the ability to extract pictures or movies that are type status of ‘not confirmed’
(this was added as there are so many variations of avi formats, that even some valid working movies were not ‘confirmed’)
If the user does not want these files, they can be filtered out and the X-Tension run excluding filtered or excluded files

September 26, 2014
XWF II and III…
…are a little late coming out due to an emergency…but will be published soon. sorry for the delay.

August 18, 2014
C4All X-Tension for CETS users
 C4All X-Tension for CETS users
C4All X-Tension for CETS usersThis is the same as version 3.5.12.k except adds the function to create a CETS manifest XML needed for those using CETS.
Arnold will post information for CETS users regarding changes needed to properly use the X-Tension.
C4All X-Tension CETS compatible version 3.5.13.a
http://1drv.ms/1pajcsb
For use with CETS:
1. This will provide a generic “CETS Media Manifest.xml” file
2. This generic file will not include the digital signature InvestigationID, ManifestID, or CategorizationID. However, the CategorizationID can be added manually.
3. With the CETS Media Uploader you can “re-sign” the manifest file if you use “adminmode” of the CETS Media Uploader.
To enter into Admin Mode:
1. Right Click on “CETSMediaUploader.exe”
2. Select: Sent To, Desktop (create shortcut)
3. Locate the shortcut on your desktop
4. Right Click on the shortcut and select : Properties
5. In the Target Field append to the end of the line(after the closing “): -adminmode
6. Double click the edited Short Cut
When you launch the CETS Media Uploader in Admin Mode you will a new button to “Sign Manifest” file.
Clicking on the button will bring up a dialogue window to manually select a user and the related investigation.
Keep in mind, that you must manually cut and paste your Categorization settings into the XML file.
Arnold Guerin
Canadian Police Centre for
Missing and Exploited Children.

August 12, 2014
BlockHasher for XWF
BlockHasher
http://d-forensik.de/download/

http://d-forensik.de/download/?did=14
BlockHasher helps you creating Block-HashSets for X-Ways Forensics
- Select Directory, directory-mode is atomatically activated
– Click ‘with sub-folders’ if you need recursive hashing
– Alternatively select some files, file-mode is atomatically activated
– you can switch everytime between both modes
– Choose your Entropy
– If you need to find a part of a single file use ‘one input – one output’ mode
– If you need to find a part of a bulk of files use ‘all in one’ mode
– Add ‘MD5′-Header is necessary for X-Ways Forensics
Start hashing now. A Logfile ist automatically generated.
BlockHasher is Freeware.
If you need source send mail to denny@d-forensik.de

X-Ways MD5 Hash Manipulator
X-Ways MD5 Hash Manipulator
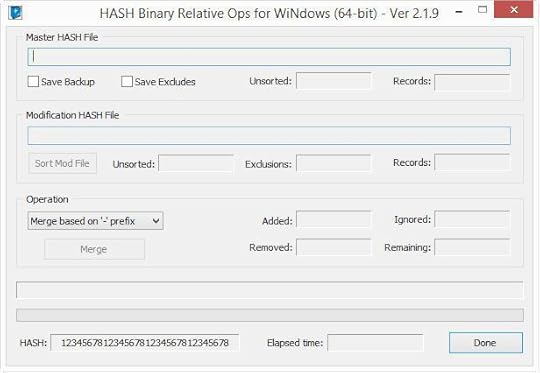
A program to manipulate your Hash sets from X-Ways.
It will allow you to Add hashes, Remove hashes, Compare hashes and remove the duplicates, create hash set of excluded files, and be in the proper format to quickly import to X-Ways.
This will allow users to maintain their hash sets and create small diff files if needed to distribute when hashes are added/removed from database.
It works on the basis of add or removing records, indicating duplicates and also the ‘-‘ prefix implemented in X-ways. files with ‘-‘ prefix can be anywhere in set, not at the beginning.
Thanks to X-Tension author Steve Frawley (who is also the author of the C4All X-Tension) and thanks to beta tester Derek Frawley.



July 16, 2014
Last day of discounted X-Ways Forensics online course
I’m sure there are a few more people left to register for the X-Ways Forensics online course (XWF I) with the discount code of “xwf1″. That’s 25% off, plus includes free tuition to the X-Ways Forensics II online course. XWF I is introductory, XWF II is more indepth, quite a bit longer, and will be released in August. XWF III, a shorter course will be released sometime after August.
Everyone registering by midnight tonight (Pacific time) for XWF I, gets access to XWF II and XWF III when published without cost. Otherwise, it’s a separate tuition payment for each course. From July 18, the XWF I is back to $195, XWF II will be $299, and XWF III will be $75. Each class is lifetime access, on demand training, including updates to the courses when XWF is substantially updated (should be a course update once a year).
Details on XWF II are here: http://xwaysforensics.wordpress.com/2014/07/05/x-ways-forensics-practitioners-guide-online-ii/
Register for X-Ways Forensics Practitioner’s Guide online course here: http://courses.dfironlinetraining.com/x-ways-forensics-practitioners-guide





