Rick Falkvinge's Blog, page 24
June 8, 2013
So Just Exactly What Is NSA’s Prism, More Than Reprehensibly Evil?

Privacy: The US NSA’s PRISM program appears to be a set of specialized deep-packet inspection filters combined with pre-existing wiretapping points at high-level Internet carriers in the United States. Since the program’s revelation the day before yesterday, speculations have ranged far and wide about who does what to make this surveillance state nightmare possible. Adding it all together, it would appear that the social tech companies did not, repeat not, supply bulk data about their users at the US Government’s will – but that the situation for you as an end user remains just as if they had.
The day before yesterday, news broke – no, detonated – that the NSA named nine social communications companies as “providers” for spy data. Among them were Microsoft, Hotmail, Skype, Apple, and Facebook – no surprises there, activists in repressive countries say “Use once, die once” about Skype – but also companies like Google and Gmail. This raised a lot of eyebrows, not to say fury.
The idea that the companies you trust with your most private data were handing that data wholesale to today’s Stasi equivalents was mind-bogglingly evil and cynical. As the news of this broke, the companies would have been a lot better off if they had just been found out doing something like eating live children.
The impression that companies were playing an active part in providing private data to the NSA was strengthened by the precision of the presentation – that there were dates when each company had, as it seemed, voluntarily joined the surveillance program.
Seeing the companies in question scramble to deny the allegations of the NSA deck – first from on-duty spokespeople with their polished façade, then from CEOs – was the inevitable next step. But this is where things became interesting. While the initial polished façade was barely credible, the response from the CEOs came across as surprised, open, and candid.
So far, there are three parties to this story: the NSA with its leaked slide deck naming the nine companies as data providers, the media who reported on it, and the companies denying any active part in NSA spy activities. The first reaction is that at least one of them must be lying. But I don’t think any of them are. I think the leaked deck from the NSA is genuine, I think the Washington Post and Guardian didn’t conspire to make shit like this up, and I have come to believe the response from the companies. How could this be possible?
At this point, there are three possibilities of what PRISM is:
1: Social communication service companies are handing the NSA private data automatically, wholesale and/or on request. This was the initial impression from the deck and the Guardian / Washington Post articles, combined with NSA’s use of “provider” when naming the nine companies.
However, one interesting initial reaction from the companies in question said something quite relevant: “if this is happening, it is without our knowledge or consent”. That leads us to option 2.
2: The NSA is wiretapping a number of key junction points on the Internet in real-time, and have specialized real-time filters to extract information when people use services from the named nine social services companies. We already know about the fiber split box at AT&T, we know about Echelon, we know about at least one court order to Verizon. The fact that the Internet is wiretapped in real time by spy agencies is well-known. How that data is used and analyzed, not so much.
There is also a third option, which is the normal court route of getting a court order to give out a user’s private data, which the New York Times speculated was the Prism program:
3: When presented with a judicial order, companies abide with the law and present as much information as they are legally required, but not more. This has been the case for quite some time, and far predates social communications – and digital communications, for that matter.
Out of these, it would appear that options 2 and 3 are true, but of those, only option 2 is Prism. Option 1 is not true. Here’s why.
When the CEO of Google and their chief legal officer publish a joint blog post named “What the Fuck?”, there’s an element of very candid surprise there. When they word their rebuttal to the allegations in a way that leaves absolutely no loopholes whatsoever,
Press reports that suggest that Google is providing open-ended access to our users’ data are false, period.
…then that comes across as candid fact. So just to empty all possibilities, could they be unwittingly lying – would it be possible for a low-ranking network administrator to have received a secret letter and order to comply with wholesale wiretapping? Would it be possible for the CEO to not know about this? In a word, no. No. That would not be conceivably possible with the traffic volume and patterns required.
Second, this slide from the now-infamous 41-slide NSA deck demands some extra attention:
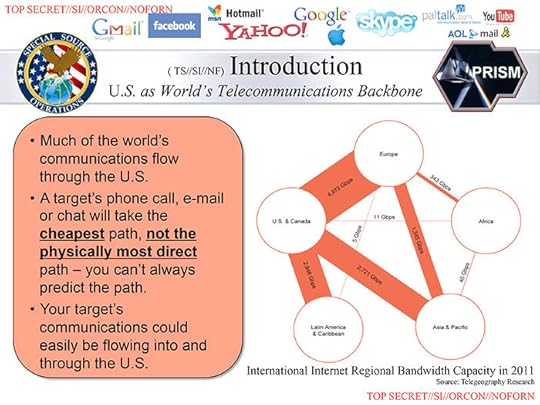
Slide showing how most of the global Internet traffic flows through the United States, with bandwidth between different continents specified.
The 41-slide leaked presentation is allegedly used to introduce the PRISM program to people at the NSA. If companies were willfully handing over private data wholesale as per option 1 above, this slide – worldwide Internet routing paths and bandwidth – would be completely irrelevant noise to the presentation. However, if option 2 was true, this particular slide would be absolutely key to understanding how and why the program worked. You would not be able to make good use of the data analysis without understanding the limitations of how the data is being collected, and this slide answers that question perfectly, albeit at a high level.
This leads us to the following conclusions:
The FISA court orders requiring disclosure of specific information for specific users are not PRISM. They exist, but are completely irrelevant to this discussion.
The nine companies named as “providers” have not played the active part that the word implies, or any active part at all.
So in conclusion,
PRISM appears to be an analysis method of the catchall Internet wiretapping we already knew about, an analysis method that specifically targets traffic to and from nine social communications services.
This is obviously still just speculation from the currently available data, but it’s the way all the pieces of the puzzle so far appear to fit together.
The earlier conclusions that privacy is your own responsibility, and the dangers of using a centralized service, well, those conclusions completely remain. But the early notion that the centralized services were complicit in governmental spying appears to have fallen. Active part or not, though, the important part here is that you’re still being wiretapped. You’re still being wiretapped when using these services, regardless of who does the actual wiretapping and who assists and who doesn’t.
To some extent, encryption could probably mitigate the situation. Do you know how to encrypt all your traffic and data? Do you do it? If your answer is no, your social life is getting on file with today’s Stasi, which – by the way – was a German abbreviation for Ministerium für Staatssicherheit, translating literally to National Security Agency.

4 UX Problems Holding Back Crypto And Anti-Wiretapping Technology

Privacy – Zacqary Adam Green: Now that our worst wiretapping fears have been confirmed, millions of people are realizing that we need to start using decentralized, encrypted communication yesterday. Unfortunately, with the state these tools are in, billions of people are still going to choose convenience over security. The open source community has made amazing progress with crypto tools’ user-friendliness recently, but there’s still more work to be done before they can go mainstream.
Even if you’re savvy enough to comfortably use the most secure and decentralized technology, you should still care about mainstream adoption. Being the one of the few people in the world sending encrypted messages could make you more conspicuous, not less. This is why we need to make communicating securely as easy as using Facebook. You don’t get to 1 billion friends without having a damn good user experience.
So here’s what we need to work on. Some of these may be software engineering challenges, some of them social. Perhaps a little of both. Share your favorite solutions in the comments.
1. People Forget Passwords
Everyone forgets passwords from time to time. Then we forget where we wrote them down. Or our password manager didn’t save them for whatever reason. With centralized services, that’s generally okay: you can just click “forgot my password,” open an email or answer some questions, and you’re good to go.
With encrypted services, if you forget your password, all of your stuff is gone. Forever.
There’s (probably) no way to create a secure system that can tolerate you forgetting your password, though it’s certainly been tried. For OS X’s FileVault, Apple operates a service which will store your encryption key on their servers, in case you forget the password for your Mac. I hope I don’t have to explain why this isn’t a real solution.
This one could be as simple as a cultural shift in which people start taking their passwords more seriously. Alternatively, we might see hardware solutions — literal crypto “keys,” or maybe biometrics — becoming more popular.
2. Hosting A Home Server Isn’t Easy
This site is hosted right out of Rick’s flat. He’s fortunate enough to have the technical skills to do so. And the free time to set it up and maintain it. And high-speed Internet. And an ISP that allows home servers. And a home.
For the rest of us, having an always-online box to host our own personal mail server, Diaspora node, SparkleShare box, VPN, and everything else, can be problematic. This is why hosting services in datacenters are so popular: because somebody else can handle the technical stuff.
For those of us with homes, we need plug-and-play home servers which can configure themselves automatically. They should come with a package manager that’s as easy to use as the iPhone App Store. Open and hackable? Yes, definitely, but still usable by someone who doesn’t know what an operating system is. An Ouya for decentralized communications and storage.
People who move around a lot — students, traveling professionals, couchsurfers, homeless people — might be able to do something similar on their mobile devices. They can host the services right from their phone or tablet.
3. The “Cloud” Is Really Useful
Datacenters are really fantastic things, though. They can back up your hard drive in case your computer gets fried. They can host your website in case your electricity cuts out. In fact, the only real problem with datacenters is that we have to trust them not to hand over or destroy our data, or perform a man-in-the-middle attack with decryption.
Freenet stores all data by encrypting it, breaking it up into chunks, and randomly giving different chunks to different peers. Nobody knows whose data or what data they’re hosting. What if this idea could be expanded into a massive, global, completely anonymous and distributed “cloud”? Chunks of your encrypted private data would be hidden in plain sight on hundreds of different servers, computers, tablets, phones, and game consoles. There would be no need to trust a hosting company; neither of you would even know that you were a customer.
4. Some Things Won’t Work Without Sharing Data
To use DuckDuckGo, the favorite search engine of privacy advocates, you have to take the word of some guy in Pennsylvania that you’re not being tracked. To be fair, I do trust DuckDuckGo, but I trusted Google once too. Good news: right now, there’s a decentralized, P2P search engine called YaCy. Bad news: it kind of sucks.
The reason Google — and Bing, which is one of DuckDuckGo’s data sources — have such good search algorithms is because they can track a whole bunch of stuff. They collect a tremendous amount of data from their users, analyze it, and use it to make their search engines smarter.
Other Google services do this too. Google Voice’s transcription algorithm learns by analyzing millions of voice messages, getting better and better as it goes. Google Now on Android phones keeps track of everything you do on your phone to predict what you might want to know or do next, and it learns from everyone else’s phone too. Data from billions of Internet users does amazing things for AI research.
But that data — even when “anonymized” — can be used to find out very specific things about very specific people. Facebook can tell your sexual orientation based on your ‘likes’, for example. Combine that by getting a rough idea of where you live, who you’ve contacted, and a clever detective (or algorithm) can figure out who you are. This is the reason why many people want to keep their data private in the first place.
So the question is: can we have some of these wonderful things without giving up our privacy? Is there a way that encrypted, decentralized systems can replicate some of the spectacular results of Google, the suggestion features of Facebook, the recommendations of Netflix, and other very nice, very useful things?

June 7, 2013
Told You So: If You Have Been Using A Centralized Comms Service, You Were Wiretapped

Privacy: This night, news broke that the USA’s security agencies have been wiretapping essentially every major centralized social service for private data. Photos, video conferences, text chats, and voice calls – everything. We have been saying this for years and been declared tinfoil hat and conspiracy nuts; it’s good to finally see the documents in black on white.
This night, European time, the news broke that the USA’s National Security Agency (NSA) has had direct access to pretty much every social network for the past several years, dating back to 2007, under a program named PRISM. Under the program, a number of social services voluntarily feed people’s private data to the NSA. In short, if you have been using/uploading
video or voice chat
videos
photos
stored data
VoIP calls
file transfers
video conferencing
(and more)
…from any of…
Microsoft (incl. Hotmail et al), since Sep 11, 2007
Google, since Jan 14, 2009
Yahoo, since Mar 12, 2008
Facebook, since June 3, 2009
PalTalk, since Dec 7, 2009
YouTube, since Sep 24, 2010
Skype, since Feb 6, 2011
AOL, since Mar 31, 2011
Apple, since Oct 2012
…then you have been wiretapped, and still are.
This piece of news broke just after it was revealed that the same NSA is demanding phone records from one of the major telco operators in the USA, and presumably all of them.
In short, practically every single service you have ever been using that has operated under the “trust us” principle has fed your private data directly to STASI-equivalent security agencies. Practically every single one. The one exception notably missing from the list is Twitter (but Twitter uses broadcast messages – you shouldn’t write anything secret on Twitter in the first place).
Carefully note that this PRISM program is not unique to the USA: Several European nations have the same wiretapping in place, Sweden among them. Also, these agencies share raw data freely between them, trivially circumventing any restrictions against wiretapping the own population (“I’ll wiretap yours if you’ll wiretap mine”).
This piece of news practically detonated when it hit this night. We have been saying that this is the probable state of things for years – it’s good to finally get rid of those tinfoil hats, with facts on the table. Predictably, the social comms companies named in the NSA slides are out scrambling with statements and comments.
Google, for example, said in a statement to the Guardian: “Google cares deeply about the security of our users’ data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a back door for the government to access private user data.”
As a politician, what strikes me is how carefully crafted this statement is to give the appearance of denying the allegations, without doing so. It stops exactly short of saying “the presented allegations are lies”.
For example, a system could be in place that continuously fed the NSA data from Google servers in accordance with the NSA documents, and the above Google statement would still be true (if Google feeds data to the NSA, rather than the NSA fetching it from Google).
Microsoft – whose motto is “Privacy is our priority”, the Guardian notes – was the first to join the PRISM program in 2007. On the other hand, that company was never trusted much, so I don’t see a lot of surprise.
What we learn from this is something that us net liberty activists have known and practiced all along: if you want your data to be private, you can trust no one with it. No one. You must make sure to encrypt it yourself. Only then can you place it in the custody of somebody else. Putting an unencrypted file on Dropbox, Google Drive, sending it in e-mail, etc., is and has been the equivalent of shouting it out to the entire world.
A system that requires privacy, but is built on the assumption on trust in a third party, is broken by design.
You can only trust systems that are built around the principle of distrusting the entire world (like bitcoin, nota bene), or systems that are physically under your control. Note that I say physically: having virtual servers “in the cloud” is not enough, for an administrator of that cloud can trivially go in and take everything you’re processing there and feed it to whomever they like, and must be assumed to do so. For the same reason, having your own servers in a rented datacenter is not enough, either: an administrator of the datacenter can give access to your computers to whomever they like. That is the reason why I have servers for this site and other sites of mine running on my own balcony:

The servers for this journalistic site, and other sites with more sensitive personal information, are under my physical control.
This is the reason you cannot trust Dropbox, Gmail, Skype and similar services with anything remotely sensitive. If you have sensitive data, you need your own servers to store and communicate it. Servers that are physically under your control. That is why you should be running encrypted SparkleShare on your own file servers rather than Dropbox in the cloud; that is why you should be running default-encrypted Mumble on your own servers rather than using Skype; that is why you should be using RedPhone from your cellphone instead of regular voice calls.
It’s already a matter of life and death in many places on the planet. Also, do note that it may not be the laws today you have to worry about: Everything is recorded and stored, and your innocent words today may come back to haunt you 30 years down the line under a different administration.
Privacy is your responsibility. You can trust no one.
As a final note, this shows very much why pirate parties are needed – worldwide – to kick politicians who authorize these egregious violations out of office, off the coast and into the ocean. (I usually write “next state”, but people from that state always complain how people there don’t want them either.)

June 4, 2013
How Bitcoin Can Bring Down The United States Of America

Swarm Economy: Bitcoin represents a significant threat to the currency domination of the USA, which is the only thing propping up the nation’s status as a worldwide superpower. Following the USA’s defaulting on all its international loans on August 15, 1971, the US trade balance has been maintained using a combination of military threats and telling people to buy US dollars just to fund the ongoing consumption of the USA. Where other world currencies have failed to challenge the USD, and therefore this mechanism of maintaining US economic dominance, bitcoin may succeed.
To understand this scenario, we need to understand just how bankrupt the United States of America is. For some reason, most spotlights at the moment are pointed at the failing Euro; this is probably in part due to the fact that the US Dollar failed long ago, and is being kept alive by blowing up a bubble harder by the day. An ELI5 version can be found here (ELI5 meaning “explain it like I’m five”), but in a nutshell, the USA defaulted on its international loans following the Vietnam War, and has been borrowing more money to fund its extravagant consumption ever since. Since long ago, more money is now borrowed just to pay interest on the previous loans. Last year, the United States’ budget deficit was an astonishing 50% of the budget – for every US Dollar in revenue, two were spent. Remarkably, this isn’t discussed a lot – I imagine if it were, the US’ ability to pay back its loans would be called into question, something that would bring down the house of cards like a ton of bricks dumped on top, so nobody is really interested in rocking the boat too much. After all, everybody is sitting on USD reserves that would become worthless overnight if that were to happen.
The United States started its money printing presses on August 15, 1971, and has kept them going ever since. Just in 2011, 16 trillion dollars – that’s trillion with a T – were printed to prop up the US economy. How much is that in perspective? It’s slightly more than the US gross production combined. For every dollar produced of value, one more was printed out of thin air, in the hope that somebody would buy it. And people do. That’s the thing – there is a key mechanism here that forces people to keep buying US dollars.
The United States is kept alive as a nation by the fact that if anybody wants to purchase goods from another nation, like China, they first have to buy US Dollars from the USA, then exchange those USD for the goods they want in China. That, and the fact that this results in all countries buying tons of USD to put in their currency reserves.
The fact that people must keep buying USD to get what they want from anybody else in the world is the mechanism that props up the entire US economy, and more importantly, fuels its military which in turn enforces this mechanism (see Iraq, Libya, Iran, etc). It’s a cycle of violence-enforced economic dominance that leads to extravagant spending, and an enabled such spending, by the United States – mostly on military power to maintain that very dominance.
(As a side note, it’s questionable how much the middle class in the United States benefits from this any longer. A decade ago, this feedback loop made the normal standard of living in the US noticeably higher than in other parts of the Western world; today, the US comes pretty much last in every category of standard of living.)
As “end of the world” articles are typically discarded as tinfoilhattery, I wanted to start this article with establishing economic facts on the table. The USA is bankrupt, and the only thing keeping it from collapsing are its military and the fact that everybody else is so heavily invested in the USA that nobody wants it to go bankrupt on their watch. Thus, the borrowing and overspending continues for another day… until it doesn’t.
What would happen if the US were one day unable to continue its overspending? We would see a mighty crash of the global economy, but more importantly, the US would come down in a Soviet-style collapse, only much worse due to structural differences. (To understand these differences, consider the fact that public transport kept running through the Soviet collapse, and that most families were well-prepared for food shortages. In the US, you would instead have people stranded in suburbs with no fuel, food, or medicine – only lots of weapons and ammo. See Orlov’s collapse gap for more on this structural difference.)
Enter bitcoin, which can break the cycle of borrowing and overspending.
As we observed, the key reason that people are forced to buy US Dollars today is that it’s the international mechanism of exchange of value. If you want a gadgetoid from China or India, you need to first buy US dollars, and then exchange the US Dollars for the gadgetoid. But as we have seen, bitcoin far outshines the US Dollar in every aspect as a value token for international trade. Using bitcoin is cheaper, easier, and much much faster than today’s international systems for transfer of value.
Pretty much everybody I’ve spoken to who is involved in international trade would switch to a bitcoin-like system in a heartbeat if they were able to, venting years of built-up frustration with the legacy banking system (which uses the USD). If that happens, the US won’t be able to find buyers for its newly-printed money that keeps its economy propped up (and its military funded).
If the cycle of dollar lock-in breaks, the United States of America comes crashing down. Hard. It would seem inevitable at this point, and bitcoin may be the one mechanism that breaks the cycle.

May 31, 2013
Swarmwise – The Tactical Manual To Changing The World. Chapter Five.

Swarm Management: Anybody who has led guilds or raids in World of Warcraft can learn how to lead a swarm. Or, for that matter, most entrepreneurs who have led small-scale teams dependent on trust. In essence, it’s the same social and psychological mechanisms.
Swarmwise chapters – one chapter per month
1. Understanding The Swarm
2. Launching Your Swarm
3. Getting Your Swarm Organized: Herding Cats
4. Control The Vision, But Never The Message
5. Keep Everybody’s Eyes On Target, And Paint It Red Daily (this chapter)
6. Screw Democracy, We’re On A Mission From God (Jul 1)
7. Surviving Growth Unlike Anything The MBAs Have Seen (Aug 1)
8. Using Social Dynamics To Their Potential (Sep 1)
9. Managing Oldmedia (Oct 1)
10. Beyond Success (Nov 1)
The actual book is expected to be available by July 1, 2013.
If I had to pick one skill that was crucial in allowing me to lead the Swedish Pirate Party on its journey from two lines in a chat channel to taking seats in the European Parliament, it would be skills and experience in project management.
This term, project management, is somewhat of a misnomer in this context. When we talk about management, we talk about appointed positions — Dilbertesque pointy-haired bosses, all too often. But good project management is not so much management as it is leadership. Leadership is not an appointed position, like management; leadership is a state of group psychology.
The first time I was trained in the enormous difference between these two concepts was in my officer’s training in the Swedish Army. (I hold the rank of second lieutenant.) Any dolt with pointy hair can be appointed to become a boss in the organizational chart, but in order to lead, you must deserve people’s confidence and trust.
An organization works at its best when these two roles coincide in the same person. When they don’t, the organization works terribly.
This boils down to a breakdown of the concept of responsibility. It consists of two equally important parts — accountability for a certain result, and authority to make that result happen. Accountability and authority must always follow one another as responsibility is delegated.
All too often, you will hear somebody being asked to “take responsibility” for a development gone bad, but what they’re really being asked is to take accountability for something without the corresponding authority. Unfortunately, taking accountability without such corresponding authority is the same thing as taking the blame for events that go wrong outside of your control. Only the most forward and simultaneously naïve people accept such accountability, and sadly they are all too often sacrificed as corporate scapegoats by those with more ruthless ambitions.
The reverse, authority without accountability, is equally bad. You can almost hear Stalin’s maniacal laughter in the background as Eastern Europe was being enslaved when somebody manages to get authority without the accompanying accountability.
The takeaway here is that authority and accountability must always follow each other in the concept of responsibility. Your swarm’s leaders will not have much of either, though, to be honest. They may get responsibility for a small budget as your swarm progresses, matures, and grows, but as we recall, they never get to tell anybody what to do — nobody does.
This is also why, as we discussed in chapter 3, the organizational chart of the swarm’s scaffolding should lag slightly behind the observed reality. You don’t appoint somebody to lead a function — you observe that somebody is already leading a function, voluntarily taking accountability for it, and ask politely whether they would mind if that fact were made formal in an announcement together with the corresponding authority (if any).
Along the same lines, the crucial project management skills that helped me lead the Swedish Pirate Party into the European Parliament were not the skills you’d learn in a project management class — things about gates, schedules, budgets, or stakeholders. It was much more the soft skills that come with experience: how to maintain a group’s motivation, focus, energy, and commitment to deliver.
Incidentally, these were skills I learned as an entrepreneur and a project manager during the dot-com boom of the late 1990s.
I founded my first company at age sixteen and had my first employee at age eighteen, so there was plenty of time to learn. But the environment in the dot-com era was something truly challenging, as people didn’t work for the money.
There was such a shortage of skilled coders, system architects, and designers everywhere you went that people could basically walk into any company and say, “Hello, I would like to work here.” The response from the company would be, “Yes, sir/ma’am — what salary would you like?”
In this environment, where people would literally have a new job before lunch if they felt like leaving their current one at the morning meeting, it was obvious that people didn’t work for the money. People invested their energy, focus, and commitment into changing the world for the better. Having rent and food taken care of was just a necessity ticked off the everyday checklist.
Thus, the psychology of this era — leading companies and projects during the dot-com boom — matches leading a swarm almost to the letter. In swarms, people don’t work for the pay, either (there isn’t any, to begin with), but they invest their energy, focus, and commitment to make the world a better place. Therefore, the leadership styles that work well are pretty much identical.
Of course, this also dispels the myth that you can’t lead a group of volunteers the way you would lead a company. Leadership is exactly the same in both cases. Leadership is psychology, and has very little to do with a paycheck and much more to do with deeply ingrained social wiring in human beings.
When I led the Swedish Pirate Party, I used the exact same skill set I had used as an entrepreneur. And it did take the swarm into the European Parliament, so it’s hard to argue with the results.
PROJECT MANAGEMENT AND SELF-ORGANIZATION
The first time you see self-organization happen, it feels like magic. After having communicated a vision, you can see how the people who listened to you start to self-organize to make your vision happen, without you needing to give directions — or, indeed, interfere.
The trick, then, is how to communicate the vision. If I had to give a quick answer to that question, it would be “with all the passion you can muster, from the depths of your heart, through the fire of your voice and the determination of the depth of your eyes.” You need to be positively radiant with your desire to change the world for the better, and, above all, communicate three values:
— We can do this.
— We are going to change the world for the better.
— This is going to be hard work for us, but totally worth it.
You will notice that we’re talking about changing the world in “we” form. This is crucial. There is never “I need someone to do X,” nor is there ever “You should be doing X.” There is just “We all need X to happen.” You don’t need to point at somebody, or even imply who should do it. Somebody will.
Let’s take these three values one at a time.
We can do this: Part of what energizes a swarm is the realization that the sheer number of activists can make a real difference in the world, and that the task would seem impossible, utterly unattainable, before you came on stage with this crazy idea. It could be changing worldwide policy on a small but important matter, it could be going to Mars, it could be dropkicking an entire archaic industry out of existence with a new, disruptive product or service, it could be solving world famine, illiteracy, or disease. Shoot for no less than the moon! Once you’ve run the numbers as we discussed in chapters 1 and 2, and communicated to the swarm that your insane idea is actually achievable, blue sparks of energy will jolt across the swarm with loud, crackling noises. People will look high from the excitement of being a part of this. Feel high, too.
(You can and should push it even further, by the way. After all, we’ve already been to the moon. Everybody knows that. So shoot for Mars instead! That project would energize people, electrify people. In contrast, you’ll never get a swarm energized around the idea of making the most professional tax audit.)
We are going to change the world for the better: Even if you could get a short-term swarm focus around hate and intolerance, this book is about good causes. Everything you focus on tends to grow, and all your values become organizational values. Therefore, a swarm built on distrust would quickly be devoured from within by its own negative feelings, and collapse, splinter, and fragment into irrelevance. In contrast, the swarms that are the subject of this book aim to go into the history books based on mutual trust to achieve the impossible. The people who devote themselves to the goal of your swarm do so to get a footprint in history. You should communicate that this is exactly what will happen, once the swarm succeeds. (And indeed, getting to Mars would get into the history books, as would eliminating illiteracy.)
This is going to be hard work: One key value you must never falter on is your honesty. You must always communicate the situation of the swarm and its place in the world exactly as you perceive it, even if that means telling people that the swarm has problems or isn’t gaining momentum. (However, you should always think of at least one way out of a bad situation, and communicate that, too — as in we can do this.) The key point here is that people should not think that changing the world for the better is going to be easy or come lightly. You said totally possible. You didn’t say easy.
Once you have communicated this to the swarm, you will start to see people thinking in terms of “how can I help make this happen?” When a couple of thousand activists think like this, magic happens.
Also, it is crucial that you allow the swarm’s scaffolding to keep growing organically. Train your closest officers in swarm methodology and techniques, as described in this book or remixed with your own flavors of style, and help them recruit new officers into the empty boxes that their own box connects to. Your swarm will always grow from the inside out — it can only grow on its edges, a concept we will return to in chapter 8.
This is part of the necessary scaling out.
DRAW THE TIMELINE FOR ALL TO SEE
A key tool in project management is the timeline. Between now and success, you will need to set subgoals to be met that are spaced about eight weeks apart. This may seem like a contradiction to self-organization, but it’s not: you’re telling the swarm the things that need to happen to get from point A to point B. You’re not saying who should be doing what and when.
There are many good reasons to do this. The first, of course, is to back up the initial energy with credibility in the swarm’s ability to deliver:
— Let’s go to Mars!
— Yeah!
— Yeah…but, eh, how do you do that, again?
— Um…
Setting subgoals, or milestones in project lingo, spaced about two months apart on the timeline communicates a path from now to success that not only helps people believe in the swarm, but also helps people choose to do things that are relevant for the current stage of the project. Each subgoal needs to be credible, relevant, achievable, and clearly contributing to the end success. It will also help jell the swarm into crack working teams that perform magic on shoestring budgets (or, more commonly, no budgets at all).
As a tangible example, the first subgoal of the Swedish Pirate Party was registering the party with the Swedish Election Authority. When the party was founded on January 1, 2006, the deadline for registration was eight weeks out. We needed fifteen hundred signatures from identified citizens with voting rights in the imminent elections. This proved to be a perfect task to jell the geographic subgroups: it was a hurdle to clear, there was a deadline, it was doable, and it contributed in a very graspable way to the end success. We arranged a competition between the thirty initial geographic subgroups, where the winners in total count of signatures, as well as the winners in signature count relative to the size of their geography, both would get an original certificate of registration. A silly prize which we paid a small premium for — getting multiple originals of the certificate — but very, very symbolic and worthwhile when you’re building a movement that will change the world.
You will notice that I didn’t tell anybody how to collect those signatures. That’s where swarmthinking kicked in and everybody started sharing his or her experiences in a giant hivemind hellbent on success, not being the slightest bit afraid of learning by trial and error, as we discussed in the previous chapter. One of our best signature collectors at the end of the day was an activist named Christian Engström, who set the benchmark: it was possible to collect twenty signatures per hour if you were out on the streets in midshopping hours. That particular activist is now a Member of the European Parliament.
The second reason you need subgoals about eight weeks apart on a visible, published timeline is to create a sense of urgency. In general, if something is farther out than eight weeks, we don’t care about it at all, it’s just an arbitrary goal in the future. Your vision needs to be broken down into parts that are small enough that everybody can always see a closing goal on the near-term horizon.
I could mention many software projects here by name, projects that started out as two-year projects without such subdivision, and which, it was invariably realized, wouldn’t make it as the deadline approached. Even though it’s water under the bridge, I won’t name those projects by name here — mostly out of courtesy but possibly also due to nasty NDAs — but I’ll share this wisdom of project management:
— How does a project get to be a year late?
— One day at a time.
The key to shipping on schedule at the end of a project is to stay on schedule every day. This doesn’t mean that a failure to adhere to the schedule is a failure of the swarm; rather, you as a project manager should have anticipated possible deviations in both directions from the start and allowed for them in the plan. When making development plans, it is typically prudent to leave 10 percent of the time of every subgoal unallocated for unforeseen events. Only you can know how this translates to your swarm, but the key is to adjust the schedule and the plan every day to account for changes in a fluid reality. You can’t change the events of the past, but you can replan for the future to accommodate for what has already happened.
Every day, you need to make sure that everybody in the swarm can check how far the swarm as a whole has progressed toward the nearest subgoal and toward the end goal. Paint the targets bright red on a daily basis for everybody to see; make all the targets visible and show the progress toward them.
SETTING VISIBLE, ACTIVATING AND INCLUSIVE GOALS
Have you ever played World of Warcraft (or, for that matter, pretty much any modern game)? One thing that catches people’s sense of addiction is that there are always many different paths to choose from for getting a reward of some kind. Looking at World of Warcraft, you can level up (called “dinging” from the sound effect when that happens), you can learn skills, you can explore the map, you can get rich, etc. In Battlefield 3 and similar games, you can get all sorts of achievement awards based on how you play the game. There’s always something to strive for that suits your taste.
This phenomenon, that there’s always some visible, public reward to strive for, no matter your taste, is key to a successful swarm. A lot of this can be achieved by just measuring a lot of things visibly. Anything that you measure in public, people will strive and self-organize to improve without further interference from you.
Let’s take that again, because you probably skimmed it while speed-reading, and it is key to the whole swarm leadership concept:
Anything that you measure in public, people will strive and self-organize to improve.
It’s basically that simple, and that complex. The Swedish Pirate Party posts its liquidity, assets, debts, and donation summaries openly (as many political organizations do now, but not a lot did so in 2006). This leads to people wanting to break new donation records.
Same thing with membership numbers, and in particular their growth rate.
Same thing with response times to mail. Exposure events in oldmedia (TV, radio, newspapers). Mentions on blogs and Twitter. And so on.
(Some people refer to this as gamification, a term that can come across as unnecessarily derogatory. This is not about producing work of low quality because you somehow goof off and think you’re playing games while producing it; rather, it’s about finding ways to engage the reward mechanisms of the brain for doing brilliant work in the same ways that successful video games do.)
Three things emerge as important here. First, the conclusion that things that aren’t measured don’t get handled well, or indeed at all. This is partly true. Some things are fun to do anyway and will get done just because of that — this particularly involves social and creative activities. Routine activities that are the same from day to day require some kind of motivating visible mechanism, or, more efficiently, a competitive element.
Let’s take mail responses as an example. Responding to mail addressed to the swarm at some public request-for-information address is hardly a very visible task, nor is it a very creative one, and yet it is one of the more important ones. Quick response times with proper and correct responses can make or break your swarm once oldmedia decide to try you out. Therefore, this is something we need to pay attention to.
A very working solution to this dilemma is to use internal competitions with silly prizes. (Tangible rewards should rarely be individual in a swarm — always foster teamwork.) Use divisions by geography or some other arbitrary line to create teams that compete against one another in providing helpful answers quickly.
This is the second observation that emerges. If measuring things gets them done (and indeed, there is no upper limit to how many metrics you can or should track publicly), measuring things in internal competitions gets them done even more. As I already mentioned, this is how we jelled the organization in the Swedish Pirate Party right after its founding when collecting signatures for the party’s formal registration. There is a social limit to how many competitions you can have working at a time, which is probably higher than one but lower than five — this is up to you and your swarm to find out.
The third observation is the crucial importance of measuring the right thing. There are many horror stories of people who measure the slightly wrong thing, and therefore end up with terrible results.
The takeaway for this third point is that some things can’t be measured directly, and so you have to find some other thing that you can measure that has an assumed or known correlation to the thing you want to actually measure. Take alcohol consumption, for example. You can’t measure alcohol consumption in a country directly, but you can measure alcohol sales. This was done in Sweden a couple of decades ago, and the authorities responsible for public health rejoiced as alcohol consumption — as it was assumed to be, and published as such — went down steadily, year after year.
Then, somebody in charge discovered that about one-third of what Swedes drink is moonshine vodka, au naturel or spiced into schnapps. (A proud handicraft of our people, I might add.) This was never sold in regulated stores, and therefore never measured. Bureaucrats who live for rules and regulations had been making false assumptions — that people cared in the slightest about what the law said in this aspect — and alcohol consumption had actually increased steadily, leading to bad conclusions and bad policy as a result of bad metrics.
In the software business, the examples of this are too numerous. People who are rewarded for finding bugs is a common example of such Heisenberg metrics.
(Werner Heisenberg was a physicist pioneering quantum mechanics. Quantum mechanics are mind-boggling, a study in masochism to learn, and fortunately quite beyond the scope of this book. The only relevant part here is that, at the quantum level, you can’t measure something without simultaneously changing it. This was not discovered by Heisenberg at all, but phenomena similar to this are named after him anyway as he was a famous quantum physicist who happened to discover something else entirely.)
When somebody is rewarded for finding bugs, then, by definition, you measure when they find bugs and probably make it public, in order to herald the best bug finders as an example to follow. However, the instant you measure this and reward people for it, a portion of the people tasked with finding bugs will split that reward with developers who introduce bugs and tell them where to look. Therefore, measuring the state of the swarm can change it completely in the measured aspect, if done wrong.
“I’m going to code me a new minivan this afternoon.” —Wally, from the “Dilbert” comic
This is a typical example of Heisenberg metrics. There was a similar effect with the site mp3.com, which was a pioneer in the music-in-the-cloud business. (They were so much a pioneer, in fact, that the copyright industry sued them out of existence, bought the remnants for scrap value, and closed them down.) They had this experiment in 2001 called pay-for-play where an artist would get a piece of the site’s revenue, shared between the artists on mp3.com according to how much they were played on the site.
Thus, a fixed portion of money was to be distributed to the artists of mp3.com, according to objective metrics of their popularity, as measured by number of track plays on the site for a particular artist.
Bzzzzt. Very bad idea. But thanks for playing.
What happened was utterly predictable — everybody wanted to support their favorite artist financially, and therefore set all computers they could access to play music from that particular artist from the site mp3.com, but with the volume turned off as to not disturb anybody. Some people coded playbots that would repeatedly stream an artist’s music to boost artificial numbers that translated into money. Heisenberg metrics.
At the end of the day, the conclusion here is that you not only need to visualize the progress toward the nearest subgoal and the end goal of the swarm, but many other metrics as well that indicate the overall health of the swarm’s performance. You should pay particular attention to the fact that as you increase the number of metrics visualized, the tasks that don’t get measured at all will get less priority. Some of them may be important.
DIFFERENT LEADERSHIP STYLES FOR DIFFERENT PHASES
Group psychology and individual proficiency of tasks mature as they gain experience. In different phases of group cohesion and individual proficiency, you need to lead in different ways.
Let’s look first at what it takes to train an individual in a new task. It can be something as everyday as handing out flyers, or it can be doing a live debate on CNN or al-Jazeera in front of several million people. The principles are the same, and people can sweat in anxiety before doing either one for the first time.
In general, I find that a model with four leadership styles works well.
These four leadership styles are quite different, and you need to use all of them when leading a swarm, reading each situation and applying the corresponding style. A frequent comparison of these leadership styles is the progression of the narrative in the movie Karate Kid (the original, not the remake), and the combination of these styles and the ability to shift between them has been described as situational leadership.
It is a vital part of the leadership role to personally train those who regard you as their leader.
When somebody is entirely unskilled in an art, you need to give direct, specific, and explicit instructions. Hold his or her hand entirely. At this stage, you need to focus on the actions to take and how to do them properly, rather than explaining their purpose in the greater scheme of things.
— Paint fence. Up, down, up, down. Strong wrist.
— Wax on, wax off.
In a swarm scenario, we observe that direct instructions for donations yield much greater results than vague ones. The more decisions you leave up to the reader when doing a call for donations, the less money you’ll get. For example,
— We are out of flyers. It’s a luxury problem, as we are handing out more than we thought possible, but it is still a problem. Help us! Log onto your bank and transfer 25 euros into account 555-1337-31337 right now, exactly just right now!
will yield a result almost an order of magnitude stronger than this version:
— We’d appreciate if you’d help us fund our handout materials. Please donate any amount you would like to contribute to account 555-1337-31337 at any time in the near future.
The difference in results lies in the very specific instructions. Every degree of uncertainty leads to inaction at this stage. If you make people comfortable with acting, and lower the bar as far as you can for people to take action within their comfort zone, then things will happen just as you instruct.
Same thing with handing out flyers, as we discussed in the last chapter. You need to make sure that every flyer handout is preceded by a very direct and inclusive instruction detailing every part of handing out, like the instructions described in that chapter. This is direct leadership.
The next stage and type of leadership is applied when people have mastered the basic actions, but are getting frustrated over their lack of context. They don’t see the road ahead and don’t feel progress. At this stage, you need to drop the direct handholding leadership and encourage and explain why these actions lead to positive results.
— You’re not teaching me karate! You’re just using me to paint your fence and wax your car!
— Show me: wax on!
The third stage comes when somebody is proficient in the skills needed, but still not in his or her comfort zone. He or she has the skills and the ability to deliver, but just doesn’t know it yet. This makes for yet a third type of leadership, which basically is endless encouragement.
— I’m never going to be any good at this! (makes a backflip from standstill)
Finally, the fourth and final stage is when somebody is self-motivated and self-reliant. At that point, he or she has more or less ascended to be your equal and doesn’t require much in the way of maintenance. The only important thing is that you periodically recognize him or her when he or she walks an extra mile. In this scenario, the one thing to keep in mind is that you recognize an extra mile only when it really is an extra mile — nobody in the fourth stage wants to be commended for performing trivial and routine tasks well.
You need to assess every individual you work with here — you need to assess where everyone is on this scale in his or her specific context. He or she may be in several different places at once if he or she is working in multiple contexts.
To wrap this up, you also need to pay attention to how groups form and mature. Groups, too, will pass through stages.
When new people first meet in a working environment, you can observe them being very polite and friendly with one another. If somebody appears offended, apologies follow immediately. These are symptoms of a group that cannot yet deliver effectively. Politeness is a sign of an inefficient group that hasn’t learned how to work as a team; people are keeping distance.
Over time, as these individuals learn to work together, they also explore where their limits go, and these limits of people’s roles will start to collide and flow into one another. This is when they start fighting between themselves over rules and culture in the group. This is a significant step forward from overfriendly politeness and shows that the group is well on its way to becoming a well-functioning team.
Finally, in the third phase, you see nothing of the clearly marked distances that were there at the outset. A functioning team can be observed by everybody seeming to know what to do without anybody spelling it out; the group has learned how to work together.
(If new people are added to the mix, the group temporarily reverts into determining roles, culture, and boundaries.)
You need to be aware of these group phases in group psychology, and, in particular, you need to know that a small amount of conflict is actually a step of progress. A group that remains polite to each other has not learned to work well together.
We’ll take a closer look at group psychology and the inevitable conflict resolution in the next chapter, as we discuss how to make people feel included and constructive.
This is the fifth chapter of Swarmwise, a book arriving this summer. Did you like it? It’s going to be free to share (it, like this excerpt, is CC-BY-NC), but you can also buy it hardcover.
EXCERPT FROM UPCOMING BOOK

This is a part of the upcoming book Swarmwise, due in the summer of 2013. It is an instruction manual for recruiting and leading tens of thousands of activists on a mission to change the world for the better, without having access to money, resources, or fame. The book is based on Falkvinge’s experiences in leading the Swedish Pirate Party into the European Parliament, starting from nothing, and covers all aspects of leading a swarm of activists into mainstream success.

May 30, 2013
Why Google Is Not A Search Engine But An Investigative News Agency, And Why That Matters

Infopolicy: Google has long been the number one “search engine”. Perhaps that’s the entirely wrong way to think about the service, leading to a number of unintended and bad legal consequences. The term “search engine” was a word made up on the spot in the dotcom era, after all. The job Google does has been considered to have a different job title altogether since way back.
When Google was launched, that was in the middle of the dotcom boom – and everybody was calling themselves something that wasn’t a traditional analog job title, just to underscore how “new”, “digital” and “dotcom” everybody was. And to some extent, what Google did was new – but not in character, just in execution, equipment, and efficiency. To underscore its efficiency in searching the world for facts related to a topic, Google was called a “search engine”.
What Google does is to find tons of material related to a specific subject, judge its relevance, and present a report on the subject. We have had professionals for centuries who do exactly this. We call them investigative reporters.
You don’t call a car something radically different than “car” just because it goes much, much faster and cheaper than the previous generation of cars. A next-generation car may be attractive, full of want, and desirable, but it’s still a car. In the same way, what Google is doing is still investigative journalism: they are searching the world for everything that people say or write that is related to a specific topic, then presenting a report on it. The fact that the journalism in question is blazingly fast – milliseconds instead of weeks – does not factor into the fundamental type of work that is performed.
The reason this is important is that the term “journalism” has a long-established legal standing in law, whereas any job title invented on the spot in the dotcom bubble hasn’t. Constitutional protection for the journalistic activity that Google is performing date as far back as 1766, far predating the dotcom bubble (and electricity, for that matter).
This is relevant as certain obsolete industries have started to demand that Google change their “search results” – more accurately described as journalistic findings – to present a distorted view of reality rather than the journalistic truth. More precisely, the copyright industry is demanding of Google that just because a lot of people are talking about sharing culture and knowledge in violation of their monopolies, that doesn’t mean that Google should be allowed to accurately report on that fact, because doing so shows the copyright industry as incompetent.
This needs to be seen in the light of Google doing investigative journalism.
When the copyright industry is demanding that Google censors “search results” from their investigative reports, they are demanding that an investigative news agency alter their journalistic findings because those findings of fact happen to be starkly embarrassing to the copyright industry. Further, the copyright industry is also demanding that the news agency should lie to the public about what the world actually looks like.
That shows just how obscenely repulsive the copyright industry’s behavior is. Nobody would dare dream of asking an investigative reporter to alter their journalistic findings just because the result of those findings happens to be inconvenient for a particular industry, by means of putting its incompetence out into the sunlight. Well, nobody except the copyright industry, anyway.

May 24, 2013
With European Elections One Year Out, Pirate Representation Expected To Triple

Pirate Parties: This week, the end of May 2013, the European Elections are exactly one year out, and as things stand today, Pirate representation in the European Parliament can be expected to triple. This would follow a Swedish re-election, a German entry, and a Finnish entry following Peter Sunde’s candidacy. While the Pirate movement is still nascent, tripling representation would obviously advance the movement.
One year from the European Elections, we can take a quick look at the lay of the land, country by country for the Pirate Party.
In Sweden, it is reasonable that the Pirate Party defends (at least) one seat of its current two. Seeing that Sweden has twenty seats in the European Parliament, you theoretically need 5% of the vote total per seat in Parliament. (Here, we can also observe that the Swedish Pirate Party’s two seats for 7.13% was a rounding error working heavily in the party’s favor – hence, with a repeated result of 7%, one seat can be expected. In fact, anywhere between 4% and 9% will probably yield one seat.)
In Germany, the Piratenpartei is currently polling at between 3% and 4%. It’s possible that this is enough to get to 5% on September 22 of this year, when Germany has its national election, which would be a huge boost to the movement. But even without such a success, 3%-4% is enough for four German seats in the European Parliament (out of Germany’s 99) in the elections in May 2014.
In Finland, it has been announced that Peter Sunde is running for the European Parliament on a Pirate Party ticket, and his fame could quite probably carry his candidacy all the way.
So the Pirate representation in the European Parliament can be expected to triple in two ways – both in terms of countries represented (one to three) and in terms of Members of the European Parliament (two to six).
Additionally, seeing that there are Pirate Parties in 70 countries and counting, there are a number of dark horses that could break through between now and then, particularly among the Pirate Parties in Eastern Europe.
Onward to a brighter future!

May 22, 2013
Swedish Government: “Total Surveillance Doesn’t Harm Freedom Of Speech, Because It Is Covert”

Civil Liberties: The Swedish Minister of Foreign Affairs Carl Bildt has claimed that the blanket net wiretapping already being performed by the Swedish government is completely compatible with freedoms of speech and expression, as it is “performed discreetly”. This remarkably Orwellian statement was made in a panel at the Stockholm Internet Forum today, where Bildt is trying to portray himself as net-friendly. The Swedish government’s credibility is below zero in these matters among activists, as the recently-enacted FRA law mandates the government to wiretap all traffic online in bulk without a warrant, if it happens to cross a country border (which you can’t know in advance if yours does).

May 16, 2013
Prosecutor Hints That Root Domain Registry Is Criminally Liable For Copyright Monopoly Infringements On The Pirate Bay

Copyright Monopoly: Prosecutors in Sweden have sued the root domain registry of .SE domains to kill the domain name of The Pirate Bay. The root registry fights back heavily. This case is important to watch, as it can have thoroughly chilling results for the Internet’s domain name system if criminal secondary liability is established at the DNS level.
Nobody can say that the prosecutors are after justice – they are after results. In the initial lawsuit against IIS, the foundation that manages the root .SE domains, they insisted on an ex parte decision – meaning that they demanded the court to issue a domain seizure order, a final decision in this case, without allowing the accused to speak in their defense. That is not any normal kind of justice.
Just so we’re clear – this is not your average domain registrar, like GoDaddy, EuroDNS, or DomainDiscover. This is the domain registry, the root database of .SE domains, managed by the Swedish Internet Foundation (the IIS), which is the technical back-end to all those domain registrars you see. This makes the prosecutor’s actions even more jaw-dropping.
UPDATE
For the really technically minded, the registry referred to here is the top-level .SE ccTLD, managed by the IIS foundation. It is popularily described as Sweden’s root registry, but calling it a “root registry” would not be appropriate in the purest of technical settings, where it would be called a “top-level ccTLD” instead.
The IIS tells its side of the story, that;
In the eyes of the prosecutor, .SE’s catalog function has become some form of accomplice to criminal activity, a perspective that is unique in Europe as far as I know. There are no previous cases of states suing a registry for abetting criminal activity or breaching copyright law. Anyhow, Sweden strives to be the best and first in terms of the Internet, even if the country’s track record for this is highly questionable.
And they want to do it quickly as well. Right before the Ascension holiday, we received the petition with two weeks to respond. The time to respond have now been prolonged until the beginning of June. The prosecutor believes that this is so pressing that the district court would be able to make a decision on the matters without deliberations.
The IIS is having none of it, of course, and are fighting back. This angers the prosecutor even more, who went on record in the newspapers saying this:
Ingblad [the prosecutor] also states that the foundation makes itself guilty of aiding and abetting assistance of criminal copyright monopoly infringement by not de-registering piratebay.se.
“No charges have been filed”, says Ingblad, “but objectively, they are charging money to maintain a domain name for an activity that they know is criminal.”
This takes secondary liability, not to mention criminal secondary liability, to a whole new level.
(Fredrik Ingblad is one of Sweden’s two prosecutors that are dedicated to persecuting sharers of culture and knowledge, which is itself a questionable priority of judicial resources, seeing how confidence in Sweden’s judicial system is dropping like a rock.)
Even the mere hint of criminal secondary liability at the DNS root registry level for everything that happens on the web is nothing short of catastrophic for the Internet infrastructure and future economic development.
If secondary liability is established at the DNS level, not to mention criminal secondary liability, I predict the Internet community will drop DNS as a backbone protocol like a bad habit, and replace it with something different that is resilient to lawsuits and prosecutors. This would not be unprecedented, even for a backbone standard; it has happened many times before when technology has proven to be vulnerable to legal action, such as when the mature and ubiquitous Gopher protocol was dropped in favor of the new and untested HTML as hints of Gopher license requirements surfaced, when PNG was developed as a replacement for the suddenly lawsuit-riddled GIF format, and perhaps most pertinently, when BitTorrent replaced the vulnerable Napster protocol.
The IIS comments end on a quite relevant note:
This will be an expensive process and, although our lawyers will find it an interesting case, these are funds that we would rather spend on our investments in schools or digital inclusion.
See also the IIS’
May 13, 2013
Swedish National Prosecutor Says Sharing Music/Movies Must Be Punished Harshly, Because “It Funds Terrorism”

Copyright Monopoly: In a remarkably ignorant statement, the Swedish National Prosecutor has appealed a culture-sharing sentence to the Supreme Court with the motivation that sharing culture and knowledge “funds terrorism”. This follows a verdict from the Appeals Court that would have put an end to the witch-hunt of people sharing culture in Sweden, as it had handed out a sentence that was effectively too low to justify further persecution. In appealing to the Supreme Court, Kerstin Skarp of the Swedish National Prosecutor’s Office has shown every conceivable bit of ivory-tower ignorance.
The man had been sentenced to a fine of SEK 8000 (about 900 euros) for sharing 57 movies, a fine that had been raised by the Appeals Court. Normally, that would be the end of it, and people would move on with their lives, clenching their fists in their pockets in anger that people were persecuted at all for the good deed of sharing culture and knowledge (even if the risk of being indicted remains lower than being struck by lightning).
However, this verdict posed a problem for the copyright monopoly extremists, as it prevented the police from raiding ordinary people’s homes to collect evidence of sharing culture: only crimes that carry a jail sentence are proper grounds for a search warrant in Sweden. This verdict was a fine, not a jail sentence. Thus, this verdict carried a promise that it would mean an end to the persecution of the 250 million Europeans and 150 million Americans that do the good act of sharing culture and knowledge – well, at least, it would mean an end to the persecution in Sweden, unless somebody would voluntarily confess to this non-crime on the rare occasion.
Deputy National Prosecutor (vice riksåklagare) Kerstin Skarp would have none of it. In a remarkably ignorant appeal to the Supreme Court, sent directy from the office of the National Prosecutor, she urges the Supreme Court to overturn the verdict of the Appeals Court and issue a jail sentence, so that the persecution can continue. She justifies this with the opinion that sharing culture is a crime that is dangerous to the fabric of society (Swedish samhällsfarlig), a word normally reserved for system-threatening crime such as Hells Angels and large-scale police bribery. But she doesn’t stop there. Apparently, people sharing movies with one another is what funds terrorism. From the appeals document (in Swedish):

“Accordingly, it is of particular weight that courts regard this type of crime seriously, as it is nowadays commonly tied to international organized crime, funding terrorism, etc., and also results in substandard or dangerous products coming to market.”
I don’t know where to start. The logic of how a generous act of sharing, where no money is involved, is able to fund anything at all (which, you know, requires money in the first place?) is completely absent from the reasoning. It is a paper filled to the brim with corporate scaremongery bullshit, deliberately trying to tie honest people sharing knowledge and culture with one another to terrorists killing children for political gain.
This individual – Kerstin Skarp – is seriously dangerous to Swedish society, for real, in her position as Deputy National Prosecutor. She needs to step down or be fired immediately, having shown this kind of disastrously bad judgment, and there probably needs to be picketing outside her house until that happens.
If anybody should desire to discuss this issue further with Deputy National Prosecutor Kerstin Skarp (which I would encourage), she can be reached at e-mail registrator@aklagare.se (writing in the body text that the mail is addressed to Kerstin Skarp) or by phone, to the switchboard of the National Prosecutor’s Office at +46 10 562 50 00.
Shame, Kerstin Skarp. Seriously – your actions draw shame over your office, your person, and your country.

Rick Falkvinge's Blog
- Rick Falkvinge's profile
- 17 followers



