ريتشارد دوكنز's Blog, page 636
November 18, 2015
Childhood Cancer Risk Hides in Families
A substantial number of children with cancer carry cancer-predisposing mutations inherited from a parent, according to a new study published Wednesday in The New England Journal of Medicine. Researchers examined the genes of more than a thousand children with cancer and found that 8.5 percent of them—most of whom had little family history of cancer—carry handed-down gene mutations that make them more susceptible to the disease. The figure might seem small, especially within a relatively rare diagnosis, but its implications are large—for the young patients and for their family members who might also be at risk—and could help doctors select more appropriate treatments.
Pediatric cancer is a mysterious case. Most cancers in the general population are caused by genetic mutations accumulated over a lifetime. But kids have not been around long enough to experience large amounts of UV rays, chemicals or other exposures that can lead to or exacerbate errors in DNA and spur cancer growth.
These findings "give us fundamental insights into the etiology of pediatric cancer—to help treat patients," says James Downing, chair of Childhood Cancer Treatment, president and CEO of St. Jude Children's Research Hospital and co-author of the new study, which is part of the Saint Jude–Washington University Pediatric Cancer Genome Project.
Predispositions
The researchers analyzed the genes of 1,120 pediatric cancer patients (median age 6.9), honing in on 60 genes that are associated with cancer predisposition to look for DNA errors passed down from a parent, known as germ-line mutations. These cancer-linked errors were present in 95 patients, most commonly in children with solid tumors outside of the central nervous system—and least frequently in those with leukemia. "This kind of work helps in understanding where the tumors are coming from—and also what are some of the underlying driving mutations," says Lisa Diller, chief medical officer of Dana–Farber/Boston Children's Cancer and Blood Disorders Center, who was not involved in the new work
For comparison, the team also analyzed these same genes in 966 (noncancer patient) adults in the general population as represented by the 1,000 Genomes Project and found these germ-line mutations in only about 1.1 percent of people.
The researchers uncovered data from the pediatric cancer population that might alter long-standing traditions. "A big surprise is the family history," says Jinghui Zhang, chair of the Computational Biology department at Saint Jude's and a co-author of the study. Or, more precisely, the lack thereof. Family histories have been a central tool for understanding the nature of a cancer and identifying persons who might be at risk. But Zhang and her colleagues found that of the patients with these germ-line mutations and with family cancer data, only 40 percent had a family history of cancer (which was a similar rate to the pediatric patients who did not have one of these flagged mutations). Furthermore, only 57 percent of the family cancers matched with the genetic predisposition.
Test and screen?
The heritable nature of these genetic mutations means that some in a patient's family—parents or siblings—might indeed harbor the same errors. But instituting testing and screening for all close relatives of a patient's is not an automatic next step. Although a family will likely want to know: "How likely is it that the germ-line mutation would progress to a harmful cancer?" Downing notes the answer will vary for different mutations. Heritable syndromes, including cancer predisposition, have a wide range of likelihoods of actually causing the disease, a concept known as penetrance. Many mutations—which exponentially raise risk for carriers against that of the general population—only go on to cause cancer in a relatively small fraction of carriers, Zhang explains. For most of these variants, however, "the penetrance is unknown," she says
Some of the risk might become known when a parent is diagnosed with cancer. Interestingly, a handful of children with cancer harbored germ-line mutations on the BRACA1 or BRACA2 genes, which are typically associated with adult-onset cancers. In her hospital, Diller says, they reassure mothers with BRACA-associated breast cancer that any risk they might have passed down to their offspring is only for cancer later in life. Now, Diller says, "we'll have to look at if we need to change that policy—whether we should consider children of BRACA carriers at a higher risk" for cancers much earlier in life.
Treatment
In the meantime knowing that a patient has one of these mutations can help their doctors select treatment. "When a child has a mutation in these genes, it really tells us to stop and pause," Downing says. "We really need to approach that individual patient differently." Some gene signatures, for instance, raise the individual's susceptibility to the effects of radiation, a treatment that might otherwise be standard.
Additionally, Diller points out, having a germ-line mutation that is linked to a cancer in a paired organ, such as a kidney or retina, means that the other organ is also at higher risk. So instead of removing a kidney, as might be common in severe renal adenocarcinomas, doctors might prefer to do their best to save that organ, knowing that the other one might fall victim to cancer as well.
Bone marrow transplants, a common treatment for childhood cancers, might also need new considerations for these patients. Among the best marrow donors are matched siblings. But, as Diller notes, knowing these germ-line mutations' 50 percent probability of being present in a sibling, "you would want to make sure that the matched sibling is not also a carrier of the gene syndrome," she says.
Growing data, spreading syndromes
The findings provide the basis for a new program at Saint Jude's known as Genomes for Kids, or G4K, which will test all new admitted pediatric cancer patients for germ-line mutations. This will not only allow clinicians to use the results when deciding on treatment and family screening but help researchers pin down more links between heritable mutations and childhood cancer.
As more data come in, the frequency of these germ-line predisposition gene mutations will likely rise, Downing notes. "That frequency [of 8.5 percent] will probably be a lower limit," he says. "There will be more and more genes identified." And as the roster of potentially pathogenic gene mutations grows—and as more people have their genomes tested—Diller says we also need to be ready with better information about individual risk, along with helpful screening and lifestyle recommendations. For carriers of these mutations, Downing says, we still do not know if or when surveillance is appropriate. And that is no small issue, as Diller points out. Finding, for example, that a sibling of a cancer patient also carries the mutation, "you immediately make them into a patient rather than a healthy child—just because they carry a gene that we don't know how to interpret," she says.
The Encryption Wars: Everything Has Changed, and Nothing Has Changed
When eight men carrying assault rifles and wearing suicide vests killed 129 people in Paris last week, the issue of access to encrypted communications again reared its head. If the attackers planned their assault over secure data networks, doesn't it make sense to give law enforcement organizations access to those networks?
Not necessarily. The real question is whether anything has changed since the White House decided not to seek controls on encryption last month. In light of the carnage in Paris, even raising the issue may seem cold-blooded. In the wake of such an attack it is tempting to react with, “Let us do anything we can to prevent another such attack. Make law enforcement access to communications easy.” But there are national security reasons why routinely securing communications is important.
Such security decisions should be done with deliberation and thought, and not as a hurried emotional response to a crisis. (The latter can lead to actions that ultimately diminish security). A careful analysis shows nothing has substantively changed from when the White House made its decision last month. This rests on four observations:
The first is that no open society can be fully protected against attacks involving a handful of participants. It is extremely hard to accept that our societies will continue to be subject to such threats, and everyone—from local police to mayors to prime ministers and presidents—wants to promise that no terrorist attack will ever happen on their watch. Yet they cannot. To expect that law enforcement will always uncover plots involving a small group of collaborators means accepting a level of surveillance inimical to the very notion of an open and free society.
The second observation formed part of the rationale behind the White House decision. Manufacturing in modern societies consists of producing intellectual property— the design of airplanes, pharmaceuticals, software, hardware, etcetera. In such societies securing bits and bytes is crucial for industry and national security. This means securing both communications and data at rest, with cryptography as an essential tool to do so.
The third observation is that governments' desire for “exceptional access”—secured communications accessible to law enforcement under court order—has two very serious costs. First, the complexity exceptional access adds makes it far more difficult to get security right. Second, it prevents the deployment of two modern security tools: forward secrecy and authenticated encryption. Forward secrecy makes communications ephemeral; the encryption key disappears when the conversation ends, which means an intruder—a cyber thief—can only capture new data, not old. Authenticated encryption simultaneously secures and encrypts; if law enforcement insists on exceptional access, then these steps must be separated, increasing the risk for data compromise. Thus, designing communications systems for exceptional access means we make data theft easier. But such direction runs contrary to our national security interests.
The fourth observation is that there is a solution to the above conundrum. End-to-end encryption of communications doesn’t prevent investigators from wiretapping but it does require the use of a somewhat different set of techniques. Every electronic communications device—every phone, tablet, laptop—has exploitable vulnerabilities. These enable remotely loading wiretaps onto a device. It’s a complex, two-step process. First law enforcement must remotely “hack” into a device to determine what operating system and applications are running on it; then authorities must revisit the device to download a wiretap using a vulnerability present in the operating system or one of the applications. This approach is very similar to how cyber theft is done, the difference being this “lawful hacking” is done under legal authority. This technique has been used by both law enforcement and national security agencies to read traffic of targets.
This solution is more expensive for law enforcement than if communications were unencrypted (and thus always accessible under a wiretap). But the latter puts all communications at risk. Encouraging widespread use of encryption while employing vulnerabilities for wiretapping allows targeting the bad guys and securing everyone else.
Last week everything changed and nothing did. For Parisians, a certain joie de vivre disappeared. Sitting in outdoor cafés and going to music clubs and soccer stadiums is likely to be difficult for quite some time. And fears have escalated for people in New York City, London, Madrid, Brussels, Beirut, Delhi, Mumbai and elsewhere.
The French have taught us many things. One is that plus ça change, plus c’est la même chose (the more things change, the more they stay the same). The realities regarding encryption have not changed. A careful analysis determined that securing private communications end to end is crucial for national security. In no way do the horrific events of last week change that conclusion.
Susan Landau is a professor of Cybersecurity Policy at Worcester Polytechnic Institute, author of Surveillance or Security? The Risks Posed by New Wiretapping Technologies (The MIT Press, 2011) and co-author of Privacy on the Line: The Politics of Wiretapping and Encryption (The MIT Press, rev. ed. 2007).
Moderate coffee drinking may be linked to reduced risk of death
By Science Daily
In a study reported in the American Heart Association journal Circulation, people who regularly drank moderate amounts of coffee daily –less than 5 cups per day — experienced a lower risk of deaths from cardiovascular disease, neurological diseases, Type 2 diabetes and suicide.
The benefit held true for drinking caffeinated and decaffeinated coffee, suggesting it’s not just the caffeine providing health perks but possibly the naturally occurring chemical compounds in the coffee beans.
“Bioactive compounds in coffee reduce insulin resistance and systematic inflammation,” said Ming Ding, M.D., the study’s first author and doctoral student at the Harvard T.H. Chan School of Public Health in Boston, Massachusetts. “They might be responsible for the inverse association between coffee and mortality. However, more studies are needed to investigate the biological mechanisms producing these effects.”
The findings are based on data from three large ongoing studies: 74,890 women in the Nurses’ Health Study; 93,054 women in the Nurses’ Health Study 2; and 40,557 men in the Health Professionals Follow-up Study.
Continue reading the entire article by clicking the name of the source below.
The World’s Biggest Volcano Is a Magnetic Mix-Up
Earth’s biggest volcano, its peak nearly two kilometers beneath the Pacific Ocean waves, is beginning to reveal its secrets.
New magnetic data suggest that the gigantic underwater mountain known as Tamu Massif, 1,600 kilometers east of Japan, is a kind of volcanic hybrid—a mash-up of long chains of volcanoes and one enormous eruption. “We’re looking at something that’s in between a mid-ocean ridge and a simple conical volcano,” says William Sager, a marine geophysicist at the University of Houston. Mid-ocean ridges are where fresh lava wells up from deep inside Earth to create newborn ocean crust; they run for thousands of kilometers along the centers of most ocean basins.
Sager and his colleagues collected the new data on a five-week-long cruise that ended on November 10 onboard the R/V Falkor, a research vessel run by the Schmidt Ocean Institute of Palo Alto, Calif. The trip was the latest attempt to unravel the mysteries of this enormous volcano, and showed that its birth was more complex than scientists had suspected.
Covering an area roughly the size of New Mexico, Tamu Massif towers more than four kilometers above the seafloor. “This volcano is a beast,” says Jörg Geldmacher, a marine geophysicist at the GEOMAR Helmholtz Center for Ocean Research Kiel in Germany.
The largest volcano on Earth, Tamu Massif, is 1,600 kilometers east of Japan, on the Shatsky Rise. (Scale bars at top are approximate.) Image credit: William Sager, University of Houston
Tamu Massif’s size may trace back to the unusual circumstances of its origin. Around 145 million years ago lava began pouring out on the seafloor where three mid-ocean ridges came together in a geologic “triple junction.” Each ridge spewed out lava that cooled and preserved a record of the Earth’s magnetism at the time. Because the planet’s magnetic field has reversed direction many times over millions of years, the lava over time recorded stripes of alternating magnetic polarity on either side of the ridge where it was born.
Earlier research cruises had mapped hints of these magnetic stripes, by towing magnetic recording instruments behind ships as they sailed back and forth. But the information was spotty. Sager and Masao Nakanishi, a geophysicist at Chiba University in Japan, organized the Falkor cruise to gather the best magnetic data to date. They sailed up and back over Tamu Massif in an enormous grid covering nearly a million square kilometers.
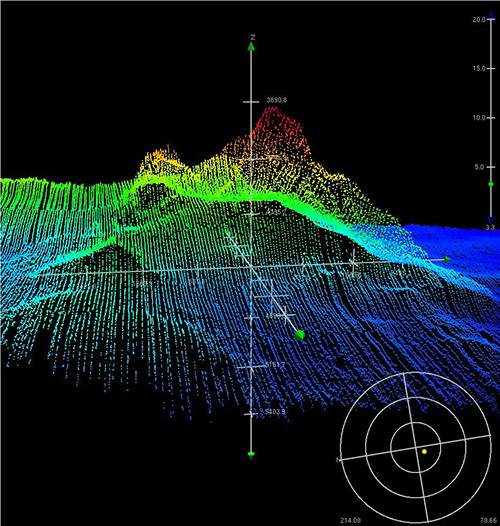
Tami Massif rises four kilometers from the seafloor. A 3D image shows various peaks that have formed over 145 million years. Image processing and credit: John Greene, Schmidt Ocean Institute
Some 1.7 million magnetic measurements later, the scientists confirmed what they had only suspected earlier: Tamu Massif seems to have coherent magnetic stripes on either side of it, like those seen at seafloor spreading ridges. That suggests at least part of Tamu Massif was born from fresh lava welling up in orderly stripes at the geological triple junction.
The main mountain itself is more of a shapeless magnetic blob, however. That blobbiness suggests something else is also going on—perhaps a plume of hot rock rising from deep within Earth up through the mantle, fueling an eruption on the surface like a welder’s torch blasting upward. If so, then Tamu Massif is one of the few places on the planet where a mantle plume may have interacted with a triple junction, Geldmacher says.
//
<![CDATA[brightcove.createExperiences();//]]>
The question is how much lava came from one as opposed to the other. “If you looked at a mid-ocean ridge and sliced it open, you’d find magma underneath,” Sager says. “How do you get a separate volcanic plumbing system at the same spot?”
The researchers still need to work through the Falkor data, but the new information should help unravel the mystery of the volcano’s birth, Nakanishi says. More broadly, Tamu Massif could help scientists better understand the volcanic phenomena that create the three fifths of Earth’s crust that lies beneath the oceans.
During the cruise, the Falkor also mapped Tamu Massif in unprecedented three-dimensional detail. Among other things it revealed a newfound small mountain off the west end. And steep cliffs at the base of Tamu Massif may represent places where it is subsiding into the seafloor or where underwater landslides occurred.
The Jew/Atheist Paradox
by Herb Silverman
When I recently wrote about Godless Jews, I cited a Harris survey that surprised a lot of people. The majority of Jews don’t believe in God. They are atheists. What makes this result even more interesting is another finding in a Pew Research Center survey on how Americans feel about different religious and nonreligious groups: Jews are viewed the most warmly of all groups and atheists the least warmly. Go figure!
Other than members of their own sect, evangelical Christians give Jews the highest rating. This is a case of unrequited love because Jews rate evangelical Christians the lowest, below Muslims. Not surprisingly, Jews and atheists regard each other warmly, while both rank evangelical Christians at the bottom.
Christians may not know that most Jews are atheists, but they do know that religious Jews believe Jesus was just an ordinary Jew with extraordinary delusions of grandeur.
And this rejection of Jesus inspired Christian anti-Semitism since the time of Jesus. So what has turned the anti-Semitism prevalent in my youth into today’s philo-Semitism?
Many Christians began deemphasizing certain biblical passages that contributed to anti-Semitism and perhaps even to the Holocaust. Less on Matthew 27:25, which says that the blood of Jesus will be on Jews and on their children. And less on John 8:44, the Devil is father of the Jews. Post-Holocaust Christians have concentrated more on Jews as “chosen people,” where God the creator/father says about Abraham and his descendants in Genesis 12:3: “I will bless those who bless you and curse those who curse you.” What these combined passages tell me is that God and the Devil are both absentee fathers. Thanks, dads.
It wasn’t until the late 1950s that I heard the term “Judeo-Christian,” meant to encompass perceived common beliefs of Christianity and Judaism. I found this phrase odd, since many key beliefs of the two religions are so different (think Jesus). And I’ve heard Judeo-Christian used only by Christians, not by Jews. If Christians wish to be inclusive of monotheists, why not refer to our “Judeo-Christian-Islamic” heritage? After all, Mary is mentioned more often in the Quran than in the New Testament, and the Quran asserts that Jesus was the result of a miraculous virgin birth.
Read more by clicking on the name of the source below.
Is Sex In Zero Gravity Possible?
Photo credit:
NASA
If you ever get the lucky chance to join the 250-mile-high club, you will obviously have to make a lot of practical considerations before getting down to business. Your freeze dried, nutrient-packed mush might not be the perfect romantic meal, and mission control watching you might be a bit of a mood kill, but your main concern is the weightlessness you will experience in space.
The Story of God: A Biblical Comedy about Love (and Hate)
by Gary Presley
God has never been this damned funny in this pseudo-sacred, sacrilegious piece of silliness.
In his debut comic novel, Chris Matheson, screenwriter for the Bill & Ted flicks, grabs a seat at the theater of the absurd for an on-the-scene report about The Story of God.
With the Bible as script, Matheson perceives a ready-made fantasy plot, ripe with conflict driven by a divine protagonist. As he leafs through the Bible’s books, he inserts parenthetical chapter-verse references when quoting, or reframing, scripture. Here Jehovah proclaims, “Don’t plant a field with an ox and an ass together; I’m not sure why, I just don’t like it! (Deut. 22:10).” With proclamations in or out of context, Matheson creates a God who soon defines himself as arbitrary, drama-obsessed, and misogynistic. As for Matheson, he adds “latent homosexual” to the description.
Read more by clicking on the name of the source below.
Mosques told to quiet down 5am call to prayer
Social media was still trending over the weekend over a ‘court’ decision in the occupied areas to ban three mosques from using a speaker for the call to the 5am prayer.
Although the decision was taken earlier this week, the news which travelled to Turkey was not greeted well by some users and was reported by Turkish media outlets.
According to reports, Feza Guzeloglu a lawyer in Lefka has been complaining for years over the sound that the three local mosques were making since the 1990s when making the call to prayer early in the morning.
Read more by clicking on the name of the source below.
November 17, 2015
Female Vocalists Are In the (Mouse) House
How do you attract a mate? If you’re a male mouse, you take the Frank Sinatra approach—you sing. Scientists have known about crooning male mice for years. And past experiments showed that if you leave male mice alone with an unconscious female or even with just a trace of her urine, the males will sing. If you reverse roles, the females do not sing. So scientists believed that in courtship, males made all the noise. Until now.
“The problem with the field is that we’ve never had a way to figure out who’s vocalizing.” Neuroscientist Josh Neunuebel at University of Delaware. He realized that researchers needed better listening tools.
So Neunuebel built a mouse-sized recording studio. His team lined a small closet with nylon mesh and foam, which absorb sound rather than reflect it. And they installed ultrasonic microphones, because mice make sounds at a frequency that’s above the range of human hearing.
[Mouse singing sound]
That’s some mouse singing slowed down so we can hear it.
Neunuebel’s set-up made it possible for the researchers to determine that some songs were in fact coming from female mice. The gals that sang back to the males pursuing them also slowed down their pace, as if to say (Neunuebel’s voice): “Hey! I’m interested in you. Catch me if you can.” The study is in the journal eLife. [Joshua P. Neunuebel et al, Female mice ultrasonically interact with males during courtship displays]
Neunuebel still wants to work out more details about how these interactions occur. But with improved technology, maybe the researchers can pick out pick-up lines. At least the ones that sound nice…to mice.
—Eli Chen
(The above text is a transcript of this podcast)
Greater than the sum of its parts
It is rare for a new animal species to emerge in front of scientists’ eyes. But this seems to be happening in eastern North America.
LIKE some people who might rather not admit it, wolves faced with a scarcity of potential sexual partners are not beneath lowering their standards. It was desperation of this sort, biologists reckon, that led dwindling wolf populations in southern Ontario to begin, a century or two ago, breeding widely with dogs and coyotes. The clearance of forests for farming, together with the deliberate persecution which wolves often suffer at the hand of man, had made life tough for the species. That same forest clearance, though, both permitted coyotes to spread from their prairie homeland into areas hitherto exclusively lupine, and brought the dogs that accompanied the farmers into the mix.
Interbreeding between animal species usually leads to offspring less vigorous than either parent—if they survive at all. But the combination of wolf, coyote and dog DNA that resulted from this reproductive necessity generated an exception. The consequence has been booming numbers of an extraordinarily fit new animal (see picture) spreading through the eastern part of North America. Some call this creature the eastern coyote. Others, though, have dubbed it the “coywolf”. Whatever name it goes by, Roland Kays of North Carolina State University, in Raleigh, reckons it now numbers in the millions.
The mixing of genes that has created the coywolf has been more rapid, pervasive and transformational than many once thought. Javier Monzón, who worked until recently at Stony Brook University in New York state (he is now at Pepperdine University, in California) studied the genetic make-up of 437 of the animals, in ten north-eastern states plus Ontario. He worked out that, though coyote DNA dominates, a tenth of the average coywolf’s genetic material is dog and a quarter is wolf.
The DNA from both wolves and dogs (the latter mostly large breeds, like Doberman Pinschers and German Shepherds), brings big advantages, says Dr Kays. At 25kg or more, many coywolves have twice the heft of purebred coyotes. With larger jaws, more muscle and faster legs, individual coywolves can take down small deer. A pack of them can even kill a moose.
Coyotes dislike hunting in forests. Wolves prefer it. Interbreeding has produced an animal skilled at catching prey in both open terrain and densely wooded areas, says Dr Kays. And even their cries blend those of their ancestors. The first part of a howl resembles a wolf’s (with a deep pitch), but this then turns into a higher-pitched, coyote-like yipping.
The animal’s range has encompassed America’s entire north-east, urban areas included, for at least a decade, and is continuing to expand in the south-east following coywolves’ arrival there half a century ago. This is astonishing. Purebred coyotes never managed to establish themselves east of the prairies. Wolves were killed off in eastern forests long ago. But by combining their DNA, the two have given rise to an animal that is able to spread into a vast and otherwise uninhabitable territory. Indeed, coywolves are now living even in large cities, like Boston, Washington and New York. According to Chris Nagy of the Gotham Coyote Project, which studies them in New York, the Big Apple already has about 20, and numbers are rising.
Continue reading by clicking the name of the source below.
ريتشارد دوكنز's Blog
- ريتشارد دوكنز's profile
- 106 followers



