Steve Prentice's Blog, page 15
December 3, 2013
Bitcoin: a loop of faith
 In addition to my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post focuses on the rise of Bitcoin and what it might mean in an age of virtualization and decentralization.
In addition to my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post focuses on the rise of Bitcoin and what it might mean in an age of virtualization and decentralization.
Here is an excerpt:
If you find yourself in Allentown, Pennsylvania around lunchtime, feeling a little hungry but without any cash in your pocket, take heart: the Subway franchise on Hamilton Boulevard takes BitCoin. If you have the app on your phone, your sandwich will only cost you 0.006 BTC, or thereabouts.
BitCoin, the fabled virtual currency, developed in part by the Winklevoss twins, themselves famous for their early involvement with FaceBook, has upped its status in recent months, from being the currency most favoured by gun and drug runners on the Silk Road website, to receiving cautious endorsement from Fed Chairman Ben Bernanke…
To read more, please click here.


November 26, 2013
When The Cloud Comes To The Black Friday Table
In addition to  my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post asks why companies involved in business-to-business cloud sales do not take advantage of Black Friday promotion techniques like their cousins in retail do. Here is an excerpt:
my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post asks why companies involved in business-to-business cloud sales do not take advantage of Black Friday promotion techniques like their cousins in retail do. Here is an excerpt:
As of 2013, though, Black Friday still seems to be a retail-oriented phenomenon, aimed squarely at consumers – the public – the B2C arena. Seasonal deals in the business-to-business (B2B) sphere are few and far between, and seem relegated to the primary levels of the industry, such as the occasional cloud hosting or web page-hosting provider offering up extra space for any new customers that sign up on this special weekend.
How long might it be before the world sees “Black Friday” sales on a higher-level? A cloud industry level? For a start, the increased awareness of the need for high-performance cloud technology in support of this busy retail season can easily translate into a plethora of conversations about robust cloud technology in areas such as analytics, security, application development and migration…
To read more, please click here.


November 25, 2013
How to handle email: Stay Conscious
I write for Time Management for iPad Magazine, an authority on Time Management.This link takes you to the November 2013 issue, which includes an article I wrote on surviving email by staing “mentally conscious”. Here is an excerpt:
If email has to be used, it should ideally be used in block form, not ad hoc. This makes all the difference. Responding to a stimulus just because it is there is reactive, and the detrimental results are described in the paragraph above. However, choosing to respond to email on your own terms is the opposite; it’s proactive, and it allows the user to undertake the action consciously and by choice. This is very different and results in far more consistent levels of focus, concentration and stamina, because no urgent reaction is present, but instead, a genuine sense of control is.
Block form responding means assigning times in the day to respond, for example, 10:00 to 10:30 and 1:00-1:30, and so on, rather than immediately when the messages come in. Sure, there are some emails that may supersede this rule, like the ones from the boss, but most people can live with a delay of an hour or so before receiving a response, and even if they cannot, it is easy to educate people and manage their expectations by reassuring them that their emails will be responded to reasonably promptly.
To read more, please click here.


November 18, 2013
ActionMint Post: Optimism, Pessimism and Project Management
 In addition to my own posts, I also write for ActionMint an authority on cloud-based project management. This article focuses on the uses of optimism and pessimism in calculating accurate task durations, and how this technique grew from the Polaris Missile project during the Cold War. Here is an excerpt:
In addition to my own posts, I also write for ActionMint an authority on cloud-based project management. This article focuses on the uses of optimism and pessimism in calculating accurate task durations, and how this technique grew from the Polaris Missile project during the Cold War. Here is an excerpt:
Optimism tends to make people envision time-lines, budgets and end results the way they hope things will turn out, which seldom ever happens. That is what the critical path is all about: it identifies the absolute shortest period of time that a project could take if everything works out the way we hope it will and if we all cross our fingers and toes. Every project manager should take care to identify the critical path, of course, and then re-design his/her project plan to get off the critical path by squeezing in extra time between tasks for the inevitable delays and failures to come. Because, yes, stuff happens.
To read the full post, please visit ActionMint’s blog, “The Daily Mint,” here.


November 14, 2013
Signing Documents on the Dotted (online) line
In addition to my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post covers the new, highly convenient and secure world of signing documents online. There are quite a few cloud-based companies that offer this service, and it allows people one more good reason to put the fax machine away.
Here is an excerpt:
One area where the virtual world of the cloud leads to a sense of discomfort has to do with signing documents and contracts. For centuries, the binding value of an agreement was based on an individual�s capacity to sign his or her name at the bottom � a visual and permanent testament to a person�s consent to the terms of the agreement. Prior to the age of the fax machine, these documents were signed and then transported by courier or mail, but this changed once it became possible to enforce contracts based on a document�s own digital facsimile.
Today, in a world where almost everything is accessible instantly via the cloud, the act of physically printing a document in order to sign it, scan it and fax it back seems dated and time-consuming, and to that end a number of online solutions have appeared that allow individuals to append a graphic signature to an electronic document such as a PDF or Microsoft Word file.
To read more, please click here.


November 8, 2013
Gamification: the fun way to bring a horse to water and make him drink
 There is an excellent book called Ender’s Game, written by Orson Scott Card and which is now a big-budget movie starring Harrison Ford. It uses the concept of children playing video games and perfecting their skills, all the while not realizing that their “playing” has much deeper military applications. This story differs from other movies such as “War Games” and “Tron,” in that it focuses on the “playing” and the need for continuous improvement against a computerized opponent who continually raises the difficulty level.
There is an excellent book called Ender’s Game, written by Orson Scott Card and which is now a big-budget movie starring Harrison Ford. It uses the concept of children playing video games and perfecting their skills, all the while not realizing that their “playing” has much deeper military applications. This story differs from other movies such as “War Games” and “Tron,” in that it focuses on the “playing” and the need for continuous improvement against a computerized opponent who continually raises the difficulty level.
This fascinating notion of integrating games into mainstream life, exists in many forms today, including simulators for piloting planes, boats and trains, as well as the comparatively new trend of rewarding visitors to social media sites with tokens or stars for registering, participating or referring friends. It is called gamification. Officially, gamification it is described as applying game mechanics to otherwise non-game scenarios. It has been around for decades but, as with all things technology-related, its use is now on the rise.
One of the most fascinating areas in which gamification is used is in software development. Every developer strives to write perfect code, but the fact is that they are human – and prone to error; and even with new technologies and techniques available that can assist them with writing better code, developers can be resistant to adopting these solutions if they disrupt the way they work. The tech world therefore needed a method that would not only help, but also incentivize developers to write better software, and gamification offered a solution.
 Jennifer Johnson is Chief Marketing Officer at Coverity, a development testing company headquartered in San Francisco. She describes how her company, which grew out of a project at the Computer Systems Lab at Stanford University in 2003, has developed a fundamentally unique way to apply static analysis technology – enabling it to automatically detect software glitches and defects in complex source code, on real-world codebases that can span into millions of lines of code.
Jennifer Johnson is Chief Marketing Officer at Coverity, a development testing company headquartered in San Francisco. She describes how her company, which grew out of a project at the Computer Systems Lab at Stanford University in 2003, has developed a fundamentally unique way to apply static analysis technology – enabling it to automatically detect software glitches and defects in complex source code, on real-world codebases that can span into millions of lines of code.
Whereas traditional quality control had been put into the hands of QA teams, it was thought that by making the discovery of bugs and errors more fun – like a contest – the perfection of code could be put back into the hands of the developers themselves. This principle coincided with the rise in popularity of social media where gamification was being used to engage users. The notion of making a game out of quality hit the tech arena strongly and in a positive way, since most developers love games and competition. As Johnson points out, “They take pride in coding. It is as much of an art as a science. Bug contests and leader boards are subtly creating a culture of accountability and responsibility.”
Although using competition to garner higher quality is not a new concept, the principle behind online gamification seems to have brought great advances in the areas of education, employee engagement, quality control, change management, time management and continuous improvement, by aligning with the human instincts of competition, pride and love of fun.
Coverity has enjoyed great success with its development testing technology; some of its more famous achievements have included its work with CERN on the software employed in the Large Hadron Collider; and with the NASA Jet Propulsion Laboratory during the flight software development of Curiosity, the Mars rover.
Large organizations around the world are seeking to embrace gamification as a new and promising tool for driving change and excellence through the corporation; not through mission statements or team-building getaways, but by tapping into existing human instincts. “Large global organizations involve people having to work together,” says Johnson. “Gamification assists in collaboration, and puts them under a common purpose. Even with geographically disbursed teams, it gives them something enjoyable and compelling.” In other words, she says, “How do you take a group that is ultra-important to software quality and resistant to change and make them enjoy the process of perfection? You use technology itself to make it fun”


October 27, 2013
Read and review my novel. Please. It’s right here.
“Mouth” by Steve Prentice
I am looking for people to review my new novel, entitled Mouth and then blog or tweet about it. Social media is the new frontier for everything, and despite having had two books published by a major publisher (John Wiley & Sons), I want my first work of fiction to get to people through electronic word-of-mouth.
Mouth is a work of light-humor. Some readers have likened my writing style to Douglas Adams of The HitchHikers’ Guide to the Galaxy – a huge honor, but probably because his work was a major influence on me, and to this day my favourite number is 42.
Here’s the Summary:
Sandy Parkinson and Christine Lee are co-owners of a small eatery in the downtown core based on the concept of offering small bites instead of large meals. Recently things have been going well, mostly due to the patronage of a mysterious Chinese man who uses the office space above the restaurant. All that ends, however, when the Chinese man disappears and a long line of people come along looking for him. His upstairs business, it turns out, was not entirely what it seemed. Sandy and Chris are thrown into the adventure of their lives as they seek to keep their restaurant alive and discover that everyone around them has secrets.. Filled with double meanings, secret pathways, hidden agendas and mysterious loyalties, the characters that frequent Mouth intertwine and influence each other with results that go well beyond the limits of their own imagination and comfort. Mouth is an upbeat urban adventure story, filled with humorous episodes that skewers our busy lifestyles and love of technology while weaving a narrative of plot twists and engaging characters.
Here’s the Deal:
I have made the whole book available for you to read right here. That’s it. Your own ebook copy. I have chosen PDF because its more universal than Kindle or EPUB formats. I am asking to you try it out. If you like it, take the time to review it or talk about it on your own blog, FaceBook, Twitter feed or on a specific book site such as Amazon or Goodreads. (I have provided a summary of these with your eBook copy.)
In return, I will do the same for you or for any other author that is looking for exposure.
I am quite proud of my little book, and I would be grateful for a few more readers.


October 22, 2013
Cyberattacks: Alarmingly Easier and More Frequent
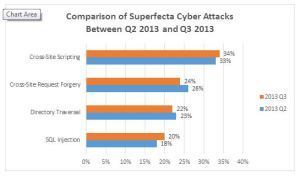
Firehost – Cyberattack chart
In addition to my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post covers a report released by the security company Firehost, detailing the quarter-over-quarter increase in cyberattacks, such as SQL injections. The report shows that these attacks are not only becoming more frequent, they are also becoming easier, and therefore no longer the domain of just the most sophisticated of hackers. Here is an excerpt:
There are always wolves at the door, and they are relentless in both their creativity and determination when it comes to getting in. This is the message that can be gleaned from a report released Tuesday October 22, by FireHost, (www.firehost.com) a provider of managed, secure cloud IaaS. Their Superfecta report highlights upticks in Cross-site Scripting (XSS) and SQL Injection activity that specifically target applications carrying sensitive information about organizations and their customers.
[They are] noticing the attacks becoming more prevalent and automated, meaning that of the nearly 32 million attacks that Firehost blocked in the third quarter of 2013 alone (a 32 percent increase over Q2 2013), the increase in attempted SQL Injection and Cross-Site Scripting attacks signifies that what was once the domain of the sophisticated hacker has now become commoditized, which poses a greater risk to any businesses with hosted resources.
To read more, please click here.


October 21, 2013
Waging Cyberwar on US Banks: A Case Study
 In addition to my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post covers a recent event in which several U.S. banks were attacked through a sophisticated Distributed Denial of Service (DDoS) attack launched by a Middle- Eastern extremist group. The way it was done, and the manner by which the website security company Incapsula foiled it and traced its origins, reads like an airport thriller novel. Here is an excerpt:
In addition to my own posts, I also write for CloudTweaks, an authority on cloud computing. My most recent post covers a recent event in which several U.S. banks were attacked through a sophisticated Distributed Denial of Service (DDoS) attack launched by a Middle- Eastern extremist group. The way it was done, and the manner by which the website security company Incapsula foiled it and traced its origins, reads like an airport thriller novel. Here is an excerpt:
Dark Clouds On The Horizon: The Rise Of Sophisticated Cybercrime
“The story reads as if it were pulled from the pages of a Tom Clancy novel: a collection of US banks suddenly starts receiving Distributed Denial of Service (DDoS) attacks that are carefully timed to re-strike just as their systems start to repair themselves. The attacks are carried out by waves of botnet zombies pouring from infected servers across the world and aimed at the United States. The main source of the outbreak is an innocent general interest website based in the UK that has been poisoned by a web design company out of Turkey. The alleged perpetrators of the attack: a shady extremist group based in the Middle East.”
To read more, please click here.


October 11, 2013
Time Management: Motivation
I write for Time Management for iPad Magazine, an authority on Time Management. This link takes you to Issue 13, which includes an article I wrote on motivation. Here is an excerpt:
 “The formula is quite simple: to be motivated to do something means that your body wants to do it, but not your mind. Take gold or diamond prospecting, for example. It involves a great deal of back-breaking work, for small-time operators anyway. They persevere, day in and day out, spurred on by the possibility of striking pay dirt and its promised riches. Intellectually, the mind knows that a lot of labour is involved, but the body, with its instincts for survival and a better, safer life, is motivated to continue, regardless.”
“The formula is quite simple: to be motivated to do something means that your body wants to do it, but not your mind. Take gold or diamond prospecting, for example. It involves a great deal of back-breaking work, for small-time operators anyway. They persevere, day in and day out, spurred on by the possibility of striking pay dirt and its promised riches. Intellectually, the mind knows that a lot of labour is involved, but the body, with its instincts for survival and a better, safer life, is motivated to continue, regardless.”
“It is the same for all tasks, even those smaller in scope than panning for gold. Motivation must speak to the body, not the mind.”
“Leadership, for example, is a school of knowledge in which certain people learn, or try to learn, how to extract consistently great behaviour from other human beings. Good leaders learn that motivation and quality are best achieved through positive reward as opposed to punishment, and great leaders learn that positive reward is a process that requires consistent conscious application. Great leadership though, comes down to a few simple concepts, such as acknowledgement of other peoples’ hard work, a vision and communication style that inspires confidence, and the skills to build great teams and realistic plans. All of these attributes inspire confidence in others, and confidence, just like the potential riches of a gold mine, speaks to comfort and security: very human, very instinctive, very basic desires.”
To read more, please click here.








