Jithin Alex's Blog
May 9, 2025
Boundary Marker | Extracting images from a PCAP file
A boundary marker is a delimiter used in multipart data transmissions, particularly in HTTP responses, to separate individual sections within a stream. This technique is commonly used in MJPEG video feeds, live image transmissions, and multi-part file uploads where multiple objects need to be sent over a single HTTP connection. The boundary marker is explicitly defined in the HTTP headers and serves as a way to identify the start and end of each transmitted object within the stream.

To identify a...
April 25, 2025
Microsoft Sentinel : KQL extend operator
Used to extend the current dataset to columns as per the requirement. In this example, a new column named “BootSince_newColumn” is added to the output using the extend operator. This new variable calculates the time difference since boot time and now.

The output shows the newly added column BootSince_newColumn with the value 2342, which is the number of hours since the boot time.
For a more commonly applicable real world example, extend operator can be used to calculate the number of days sinc...
Microsoft Sentinel : KQL project operator
Project operator is used to customize the query result output as per your needs. This doesn't remove or modify any logs. It only affects how it is presented for that particular query, for that particular run.
To keep only one particular column details instead of all available columns.
If you wish to remove only a column and keep all other available columns, then use project-away
project-rename option can be used to rename the column name. Here in this example, the column with name "Computer" is re...
Microsoft Sentinel : KQL search query with examples
To search for all logs that contain a particular keyword. This is useful when you are unsure about a table.
search “keyword”

And, or combining with the search operator.
search “admin” and “login”
search “admin” and (“login” or “logout”)

To search only on particular tables.
search in (SigninLogs ,SecurityEvent) "failed"
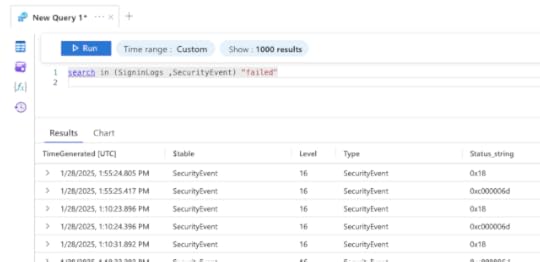
Typically the search is case insensitive. To Search with case sensitive, use
search kind=case_sensitive “admin”

Lets try another case sensitive search,

Return no result as in...
Free resources to learn Kusto Query Language (KQL) for Microsoft Sentinel
Free resources to learn Kusto Query Language (KQL) for Microsoft Sentinel1) Must learn KQL
This repository from Rod-Trent contains the code, queries, and a free eBook included as part of the Must Learn KQL series.There is also a YouTube playlist related to this.
https://github.com/rod-trent/MustLearnKQL
2) Udemy: Learn KQL for Microsoft Sentinel
An Udemy free course created by Samik Roy, designed to refresh your KQL learning and help you to boost your application for Sentinel
April 23, 2025
Unauthenticated Remote Code Execution in Erlang/OTP SSH (CVE-2025-32433)
Erlang, a programming language for building scalable real-time systems with high availability, forms a powerful ecosystem with the Open Telecom Platform (OTP) framework. Erlang/OTP SSH, an implementation of the SSH protocol, enables secure shell access and file transfers within Erlang-based systems.
On April 16, 2025, a critical vulnerability in the Erlang/OTP SSH server was disclosed. This vulnerability could allow an unauthenticated, remote attacker to perform remote code execution (RCE) on an ...
April 22, 2025
Ingest Data in Microsoft Sentinel
After deploying Sentinel by creating/assigning a Log Analytics Workspace, next phase is to ingest logs in to Log Analytics Workspaces using data connectors. Data connectors are used to get logs from various sources. This includes the cloud native sources as well as third party sources.
Microsoft Sentinel Content hub enables you to discover and install out of the box solutions for Sentinel. This solution is like a package that includes analytics rules, data connectors, playbooks etc pertaining to...
April 21, 2025
Log Analytics Workspace and Microsoft Sentinel
Log Analytics Workspace serves as the centralised repository for the logs. The logs are piped using connectors and agents. A retention policy can be set on Log Analytics workspace for compliance requirements. The logs are then used for analysis...
About Microsoft Sentinel

A Security Operations Centre is a centralised unit that monitors traffic, triage alerts, participates in incident response, perform threat hunting and often performs vulnerability assessments. The individuals who work in a SOC are often referred to as SOC analysts.
When it comes to Microsoft Azure SOC, the analysts work predominantly on Microsoft Security, Compliance and identity products and solutions such as Microsoft 365, Defender for Cloud, Microsoft 365 Defender, Sentinel etc.
Let's go throug...
March 30, 2025
CREST CPSA Exam resources
As exam candidates, it might be quite difficult to prepare for the CREST CPSA certification exam as there is no official courseware from CREST. Though there are recommendations from CREST, it is cumbersome to go through each one for the preparation. Therefore, I have written a book on CREST CPSA, aligned with the exam syllabus, covering all knowledge groups.
The book is available from Amazon as both Paperbook and eBook format.
Amazon link : htt...



