Aditya Chatterjee's Blog, page 50
February 28, 2023
Fault Tolerance in System Design
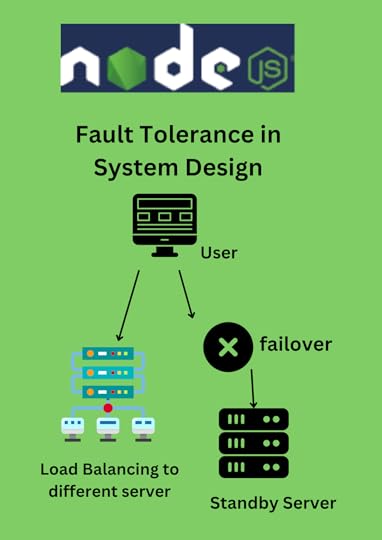
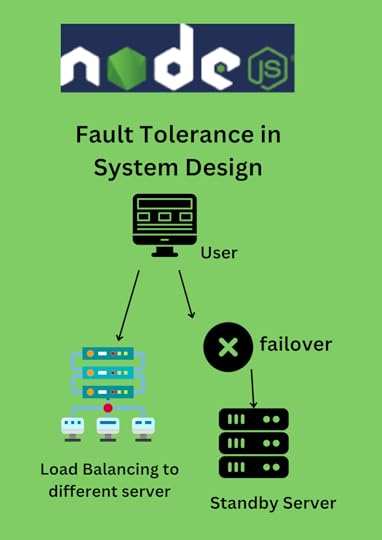
As technology continues to advance, we rely more and more on computer systems to store, process, and transmit important information. However, these systems are not perfect and can sometimes fail due to hardware, software, or network problems. That's where fault tolerance comes in. Fault tolerance refers to a system's ability to continue operating even when one or more components fail.
To achieve fault tolerance, system architecture uses a variety of techniques. One of the most common techniqu...
Pipelining in CPU [In-depth explanation]

Pipelining is an important concept in CPU optimization and utilization. It is a powerful technique used in modern CPUs to improve their performance and efficiency, but it also requires careful design and management to overcome the challenges and limitations associated with it. Let's dive into the world of Pipelining in CPU optimization and utilization.
Table of Contents:
Introduction to Pipelining in CPUBasic Principles of PipeliningBenefits and Drawbacks of PipeliningImplementing Pipelinin...Progress bar / indicator in Java
In this article, we will discuss several ways to program a Progress bar in Java in command line and as GUI.
Pre-requsites:
JavaStringStringBuffer / StringBuilderSwing libraryProgress bar in command line (easy method)In this method we will make our program by just using simple java without using strings and string built-in functions.
We create void method printMsgWithProgressBar with three parameters, String message to print the "Loading...." string, integer length to pass the length of o...Password generator, strength checker and password crack time estimator in Java
In this article, we will discuss several ways to code a program that generates random password, And another program that checks the strength of user's input password in Java, And final program that estimates the time needed to crack a user's password.
Pre-requisites:
JavaStringsTable of contents:
Using Java's Random classUsing Apache Commons Lang libraryCreating a password strength checkerUsing Java's Random classOne way to create a password generator in Java is to use Java's built-in ...
Stop Words in NLP
Data preprocessing is a process of working with the raw data to make it suitable for use with a machine learning model. It is the first and most crucial step while creating a machine learning model. In the context of NLP, it turns the raw text data into a format that ML models can understand by reducing noise and ambiguity in the text data.
Some examples of preprocessing tasks in NLP include:
Parts-of-speech (POS) taggingStopword removalTokenizationIn this article, we shall focus on the con...
February 26, 2023
Large Counts Condition and Large Enough Sample Rule
Large Counts Condition and Large Enough Sample Rule are two important concepts in the fields of machine learning and statistics that are used to make inferences about populations based on samples. These concepts are particularly useful in situations where the sample size is large or the counts in the sample are large. They are used to determine when it is appropriate to use certain statistical methods and to ensure that the results obtained from these are reliable and accurate. Let's get to know...
February 25, 2023
"Master C Programming with Practical Projects" book
"Master C Programming with Practical Projects" is a book on C Programming Language that focus on practical implementation skills and walks through multiple C projects with complete codebase.
This is one of the best C Programming book if you want to get a practical experience while learning the Programming Language.
#1 New Seller
Go to the Book and click on "Look Inside" to go through the preview and table of contents of the book.
The book comes with a code package which you can download and fol...
February 24, 2023
Built-in Hash Table in JavaScript
Hash tables are a popular data structure used in computer programming to store and retrieve data quickly. A hash table uses a hashing function to map keys to values, which can be accessed in constant time. In this article, we will explore how hash tables work in JavaScript, with examples and tips.
Built-in Hash Table in JavaScript involve using a Map with 2 key methods set and get.
What is a hash table?A hash table is a data structure that uses a hashing function to map keys to values. The hash...
Set, clear and toggle a bit in C++ [4 different methods]
Table of Contents:
Number and BitSetClearToggleOther ways of ImplementationConclusionIn this article, we will discuss about how to Set a bit, Clear a bit, and Toggle a bit of an integer in C . Before doing so, we need to discuss about how number and bit are interpreted here.
Number and Bit Given an integer N, when represented in its binary form, the kth bit of its binary value has to set, clear or toggle. to 1 if it is 0 and if it is 1, it will be unchanged. S...February 23, 2023
Functional and Non-Functional Requirements in System Design

In this article, we will walk you through the Functional and non-functional requirements, why it is needed, what are the benefits and why it can be useful for your application.
If you are making an application or managing its development, you need to first prepare you end goals, what the application or the website should achieve, what problem it will be solving, otherwise there is high chance that your product may not achieve its end goal, may be poor performing, unrealiable to the clients.
...



