Aditya Chatterjee's Blog, page 39
April 14, 2023
Find Perimeter and Area of rectangle in C Programming
In this article at OpenGenus, we have explained how to find the perimeter and area of a rectangle by using length and breadth (as user inputs). We have demonstrated this with a C implementation.
Table of contentQuestionApproach to solutionImplementation in COutputQuestionThe problem is to find the area and perimeter of a rectangle using C Programming with length and breadth as user input.
Area is defined as the region within a given shape. Perimeter is defined as the total length of the ...
Bubble sort in C
In this article, we have explained bubble sort algorithm and implemented a program on it in C Programming Language.
Table of contentsWhat is Bubble sort?How bubble sort worksImplementation in C Programming LanguageOutputExplanation of C program for Bubble SortTime complexityDrawbacks of bubble sortWhat is bubble sort?In this problem, we will be understanding bubble sort algorithm
Bubble sort is one of the most simple sorting algorithms which swaps two adjacent elements in an array if ...
Typescript with jest

In this article at OpenGenus, we are going to talk about jest particularly in typescript scope, why should you test your code? Why use jest with typescript? And what developing method use?
Why test your code?You may think that tests are not that important, you can console.log() and find out what your output is going to be, with just a typeof you can find out the type of something in your function, and the QA’s job are there for testing already right? So why should I learn testing?
Testing is es...
How to use blockchain technology for secure data storage

Blockchain technology, which was initially designed as a safe and transparent mechanism to store and transmit cryptocurrency, has since grown to a variety of other applications, including data storage. In this post, we will look at how blockchain technology can be utilised to protect data storage.
Blockchain technology is built on a distributed ledger system, in which each data block is linked to the preceding block in a chain-like structure. Because the blockchain is distributed, any changes to...
5 benefits and drawbacks of Cloud Computing
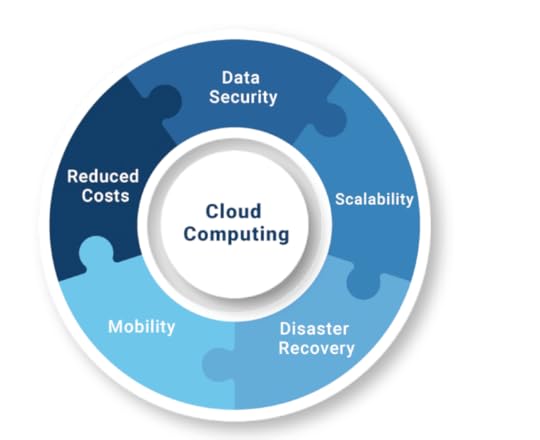
Cloud computing has grown in popularity in recent years, providing numerous benefits to both organisations and consumers. However, it is not without flaws. In this post, we will look at the advantages and disadvantages of cloud computing.

5 major Benefits of Cloud Computing are:
Cost Savings: By outsourcing their computing needs to cloud service providers, organisations can minimise their IT infrastructure expenditures. This eliminates the need to buy and maintain...
April 13, 2023
Binary Search in C using recursion
In this article at OpenGenus, we have explained Binary search algorithm and implement a program on the same in C programming language using recursion.
Table of contentsProblem statementHow binary search worksTime complexityDrawbacks of binary searchRecursion in Binary SearchImplementation of Binary Search in C using recursionOutputConclusionProblem statementIn this article, we will learn binary search algorithm.
Binary search algorithm is used to search an element in a given set of ...Predicting employee attrition [Data Mining Project]

In this article at OpenGenus, we have explained a Data Mining approach (with source code) to predict employee attrition.
Employee attrition is the process of employees leaving an organization for various reasons. It can be voluntary or involuntary and is often seen as a sign of low morale, a lack of job satisfaction, or difficulty in finding qualified replacements. Predicting employee attrition can help organizations anticipate staffing needs, reduce costs associated with recruitme...
Dot product in Python [with and without NumPy]
In this article at OpenGenus, we have explored different ways to dot product in Python Programming Language with and without Numpy.
Table of contents:
Introduction to dot productIntroduction to Matrix in Python and NumpyDifferent methods to do dot productPython: Naive approach in dot productDot product in python without NumPyDot product in Python with NumPyIntroduction to dot productMathematical process called the "dot product" produces a scalar from two vectors. The NumPy library, a we...
10 Impacts of quantum computing on cryptography and data security

Quantum computing has the potential to transform numerous industries, including encryption and data security. While typical computers store and process information using binary digits, or bits, quantum computers use quantum bits, or qubits, which can exist in several states at the same time. As a result, quantum computers may do some calculations significantly quicker than ordinary computers, such as those used in encryption and data security.
The influence of quantum computing on cryptography a...
12 benefits of using Machine Learning in healthcare

Machine learning is a potent tool that has transformed several industries, including healthcare. Machine learning may assist in the analysis of huge amounts of data, the identification of patterns and trends, and the prediction of outcomes based on that data. Machine learning has the potential to enhance patient outcomes, lower costs, and boost efficiency in healthcare. This post will go over the advantages of adopting machine learning in healthcare.
The 12 benefits of using machine learning in ...



