Aditya Chatterjee's Blog, page 204
June 9, 2020
NamedTuples objects in Python

Reading time: 20 minutes | Coding time: 5 minutes
A Tuple is an ordered and immutable collection of objects. Once initialized you may not change them.
Tuples are used to hold together multiple objects. Think of them as similar to lists, but without the extensive functionality that the list class gives you. One major feature of tuples is that they are immutable like strings i.e. you cannot modify tuples.
Read about Tuples in Python
NamedTuples are Tuples that allow you to:
Name each Tuple f...
June 8, 2020
Typing speed testing tool using Vanilla JavaScript
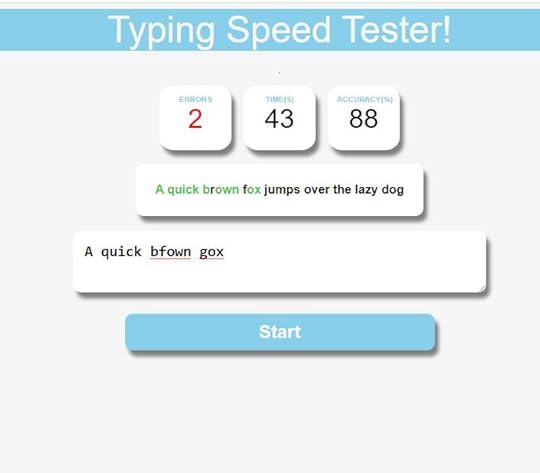
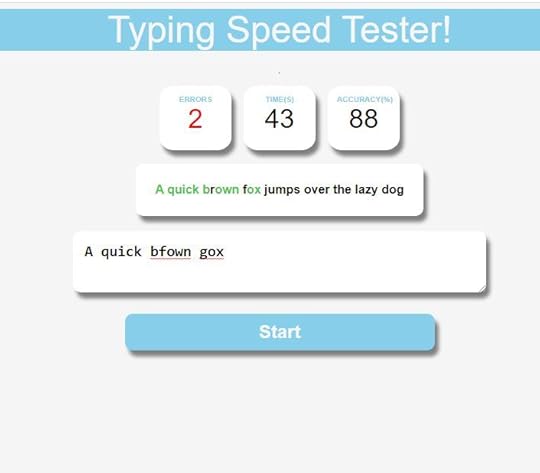
In this article, we will know how to build a simple tool that can test the typing speed of the users. We will develop this using JavaScript along with HTML and CSS.
Tech stack to be used:
HTML, CSS, JavaScript
Setting up the structure using HTML:
Let's create the skeleton structure of the project.
Typing Speed Tester!
First, we need to inlcude our CSS and JS file link, as shown above.
Now, let's make the boxes where we will show the number of words typed, timer, number of mistypes ...
An Introduction to BERT
Reading time: 25 minutes
In Oct 2018 , Google AI released a pre-trained model for performing various Natural language processing tasks .It instantly started getting attention due to the fact that it attains state of art results on most of the NLP tasks . They even claimed that the model has surpassed human level performance which is generally the benchmark for all the Machine learning Algorithms.
You can find the released paper here in which they talked about the process of training the model ...
June 7, 2020
Knuth's optimization in Dynamic Programming
Knuth's optimization is used to optimize the run-time of a subset of Dynamic programming problems from O(N^3) to O(N^2).
Properties of functions
Some properties of two-variable functions required for Kunth's optimzation:
1. Quadrangle inequalities
For a two-variable function $f(x, y)$ :
Convex quandrangle inequality : $\forall_{a \leq b \leq c \leq d}(f(a, c) + f(b, d) \leq f(a, d) + f(b, c))$
Concave quadrangle inequality : $\forall_{a \leq b \leq c \leq d}(f(a, c) + f(b, d) \geq f(a, d) +...
Class based Generic Views in Django
Django is a high-level open-source Python-based Web framework that provides rapid development with pragmatic design. Django often called Batteries-included framework as it provides built-in tools for many functionalities in a web application.
What are views?
Views are just a function that is callable each time a request is made to an application, it takes a request as an argument and returns a response.
Class-Based Generic Views are a superior set of Built-in views that are used for the impleme...
Tim Sort
Reading time: 30 minutes | Coding time: 15 minutes
Tim Sort is a hybrid stable sorting algorithm that takes advantage of common patterns in data, and utilizes a combination of an improved Merge sort and Binary Insertion sort along with some internal logic to optimize the manipulation of large scale real-world data. Tim Sort was first implemented in 2002 by Tim Peters for use in Python.
Operation
Tim sort uses Binary insertion sort and improved merge sort by using galloping in a combination. Bi...
Overview of Maximum Flow Problem
Flow networks are fundamentally directed graphs, where edge has a flow capacity consisting of a source vertex and a sink vertex. The aim of the max flow problem is to calculate the maximum amount of flow that can reach the sink vertex from the source vertex keeping the flow capacities of edges in consideration. The flow at each vertex follows the law of conservation, that is, the amount of flow entering the vertex is equal to the amount of flow leaving the vertex, except for the source and the ...
June 6, 2020
Creating JWT Authentication in REST API in Flask
JSON Web Token is a string which is sent in HTTP request from the browser to the server to validate authenticity of the client. The browser stores the JWT and includes the token with every request in the header.
Now we will create app.py file.
app.py
#import necessary library
from flask import Flask, request
from flask_restful import Resource, Api, reqparse
from security import authenticate, identity
from flask_jwt import JWT, jwt_required, current_identity
#configuring your application
app = ...
Algorithm to find the maximum power of N that divides M factorial (M!)
Reading time: 40 minutes | Coding time: 10 minutes
We are given two numbers M and N. Our aim is to find the highest power of N that divides Factorial of M (M!). We often come across such problems in competitive programming where we require an optimal solution.
First we will discuss about the Brute Force approach and then we will be discussing this problem using Legendre’s formula.
Underlying are some examples which would help in better understanding of the problem.
EXAMPLES
Input : M = 5, N = ...
Adversarial Machine Learning
Adversarial Machine learning is the technique which involves applying different methods in order to construct or generate examples that are meant to fool the machine learning model. These types of examples are called adversarial examples.
In this article, we will explore how an adversary can exploit the machine learning model i.e. methods to generate adversarial examples and we will also talk about some defense strategies against these adversarial examples.
What is an adversarial example?
An ad...



