Aditya Chatterjee's Blog, page 157
September 2, 2021
Lempel Ziv Welch compression and decompression

In this article, we will learn about the Lempel Ziv Welch compression and decompression algorithm, a famous compression technique that is widely used in Unix systems and GIF format files.
Note that Lempel Ziv Welch algorithm was (USPTO) patented in 1985 by the company Unisys. The patent rights were not enforced but later, royalties were collected. It reduced the popularity of GIF at that time provided an alternative (PNG) was ready.
Table of content:
Introduction to Lempel Ziv Welch algorithmA...September 1, 2021
Lomuto Partition Scheme
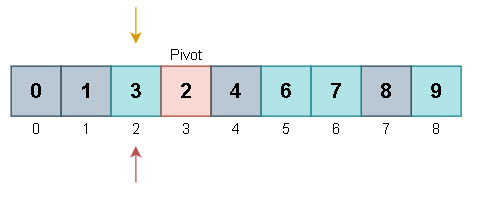
In this article, we have explained the Lomuto partition scheme, which is used in the famous Quicksort algorithm. It is an algorithm to partition an array into two parts based on a given condition.
Background and IntroductionAlgorithmQuick sort using Lomuto Partition Scheme - VisualizationWorking programComparison with Hoare Partition SchemeConclusion1. Background and IntroductionLomuto partition technique was made by Nico Lomuto and then eventually made its way into the spotlight when J...
Why SpaCy over NLTK?

We listed 10 aspects where spaCy shines better than NLTK. It also included information when NLTK outsmarts spaCy.

Before diving into comparing the two most popular Natural Language Processing (NLP) libraries, let's first understand what spaCy and NLTK are, who are the creators and why these packages were created on the first place?
(Feel free to skip this section if you already know these libraries)
Starting with Natural Language Toolkit, abbreviated as NLTK, is the earliest NLP libr...
August 31, 2021
Multiplication using bitwise operations
We have explained how to compute Multiplication using Bitwise Operations. We can solve this using left shift, right shift and negation bitwise operations.
Table of content:
Multiplication using Bitwise operationsExplanation with 2 step by step examplesImplementation of Multiplication using Bitwise operationsTime & Space ComplexityLet us get started with Bitwise Multiplication.
Multiplication using Bitwise operationsProblem
To find multiplication of two numbers num1 and num2 using bitwise ...
Boosting, an Ensemble Method
In this article, we have covered the idea of Boosting in depth along with different types of Boosting algorithms, benefits and challenges of Boosting.
Table of content:
Introduction to Ensemble MethodsBoostingBoosting Algorithms4. AdaBoost
5. Gradient Boosting
6. Extreme Gradient Boosting (XGBoost)Improvements to Basic Gradient BoostingBenefits of BoostingChallenges of BoostingConclusion
Let us get started with boosting.
Introduction to Ensemble MethodsMaybe almost all of you reading t...
August 30, 2021
How to use Console in Chrome DevTools?
In this article, we have covered how to use Console which is one of the development tools in the Chrome browser. The Console in Chrome DevTool helps to debug webpages and investigate external webpage as well.
Table of content:
How to open Console?View log messages + different console methodsRun JavaScript in ConsoleWe will explore the features by trying them on a sample HTML page.
How to open Console?To open the Console:
Use the keyboard shortcut Ctrl + Shift + I or Ctrl + Shift + J.Or ...August 27, 2021
Inside Outside Test [2 algorithms: Even-Odd and Winding Number]
In Computer Graphics, Inside Outside is performed to test whether a given point lies inside of a closed polygon or not. Mainly, there are two methods to determine a point is interior/exterior to polygon:
Even-Odd / Odd-Even Rule or Odd Parity RuleWinding Number Method

It is also known as crossing number and ray casting algorithm. The algorithm follows a basic observation that if a ray coming from infinity crosses through border of polygon, then it goes from ou...
Invert a Binary tree

Inverting a binary tree is one of the most common questions asked in the interviews of many companies. In this article, we will see in detail as to how one can understand and tackle this task of inverting a binary tree using recursion, stack and queue.
Table of Contents:Binary treeInversion of a binary treeMethods of InversionRecursionIterative solution using stackIterative solution using queueTime and space complexities of different solutionsBinary TreeWhen every non-leaf node in ...
August 26, 2021
Construct BST from pre-order traversal (using monotonic stack; no recursion)
This article discusses on a way in which, Binary Search Tree (BST) can be reconstructed when corresponding pre-order traversal of the tree is input, using a concept of monotonic stack.
Table of ContentsPre-requisitesIntroductionEdition 1Edition 2Step-by-step algorithmC codeQuestionComplexityReferences Pre-requisitesBinary search tree, Stack, Binary tree traversal
IntroductionBinary search tree contains nodes with each having maximum of 2 child nodes. Nodes are arranged such ...
Architecture of DenseNet-121
In this article, we have explored the architecture of a Densely Connected CNN (DenseNet-121) and how it differs from that of a standard CNN. An overview of CNNs and its basic operations can be found here.
Table of content:
Introduction to DenseNetDenseNet Architecture & ComponentsDenseNet-121 ArchitectureConclusionIn short, DenseNet-121 has the following layers:
1 7x7 Convolution58 3x3 Convolution61 1x1 Convolution4 AvgPool1 Fully Connected LayerWe will dive deeper.
Introduction to ...


