Aditya Chatterjee's Blog, page 131
January 7, 2022
Language processing system
In this article, we discuss the language processing system whereby high level code is fed into a series of programs which form a system to produce code that can be understood and executed by the processor.
Table of contents.Definitions.The language processing system introduction.Components of a language processing system.Conclusion.References.Definitions.Preprocessor directives are directives for the preprocessor, the preprocessor resolves these directives before processing begins. e.g ...
Semantic analysis in Compiler Design
In this article, we discuss the third phase in compiler design where the semantic consistency of the code is validated.
Table of contents:Introduction.Semantics.Semantic Errors.Declarations.Processing declarations.Actions performed during semantic analysis.Limitations of CFGs.Syntax Directed Definition(SDD).Syntax Directed Translation(SDT).Attributes.Types of Attributes.Synthesized Attributes.Inherited Attributes.Attribute grammar.Defining an Attribute Grammar.Abstract Syntax Tr...January 6, 2022
Noisy Neighbor + Throttling pattern
In this article, we have explored the Noisy Neighbor problem and how Throttling pattern (a Cloud Design Pattern) can be used to resolve the issue.
Table of contents:
Description of the issue: Noisy NeighborResolving the issue: Throttling PatternClients' options for actionService providers can take the following actionsPutting everything togetherDescription of the issue: Noisy NeighborA noisy neighbor is a cloud computing infrastructure co-tenant who monopolizes bandwidth, disk I/O, CPU, ...
Types of Error correcting codes in Computer Network
In this article we are going to explore about error correcting codes in computer network. We will be discussing various types of error correcting codes, how they work, what are their applications etc.
Table of contents:
Introduction to ErrorsError Correcting CodesHAMMING CODESBinary Convolution CodeReed - Solomon CodeLow-Density Parity Check CodeIntroduction to ErrorsBefore moving on to the main topic we will first understand what are errors in computer network. Errors are basically som...
January 5, 2022
Infrastructure as a service (IaaS)
In this article , we are going to explore about Infrastructure as a Service (IaaS) and dive into some deeper and basic concepts included in this along with the steps to setup / implement IaaS.
Table of contents:
Infrastructure as a service (IaaS)Architecture of Infrastructure as a service (IaaS)Working of Infrastructure as a service (IaaS)Uses of Infrastructure as a service (IaaS)Pros of Infrastructure as a service (IaaS)Cons of Infrastructure as a service (IaaS)IaaS ProvidersHow to setu...RNN Based Encoder and Decoder for Image Compression
In this article, we will be discussing a about RNN Based Encoder and Decoder for Image Compression.
Table of Contents:
Introduction.Image CompressionRNN Based Encoder and Decoders3.1 Reconstruction Framework
3.2 Entropy Encoding
3.2.1 Single Iteration Entropy Coder
3.2.2 Progressive Entropy EncodingEvaluation Metrics
Pre-requisites:
Image Compression: ML Techniques and ApplicationsImage compression using K means clusteringIntroduction:The development and demand for multimedia goods ha...
Physical Layer in OSI model
In this article, we have explored Physical Layer in OSI model in depth along with functions and significance of Physical Layer.
Table of contents:
Introduction to Physical Layer in OSI modelFunctions of Physical layerSignificance of Physical layerIntroduction to Physical Layer in OSI modelOSI Model : It is a layered framework for the design of network systems that allows communication between all types of computer system. It consists of 7 separate layers that are: Application, Presentation...
Select Random Node from Binary Tree
In this article, we have presented two algorithms to select a random node from Binary Tree while maintaining the uniform randomness.
Table of contents:
Introduction to Randomized AlgorithmsEfficient ApproachSecond approach : Using ArrayListIntroduction to Randomized AlgorithmsIn Mathematics , we all have studied about the concept of random events,experiments and the probabilities govering them. For solving the above problem we generally use the concept of Probability and Randomised Algorit...
Firoozbakht’s conjecture
In this article, we examine the relationship between Farideh Firoozbakht's famous conjecture about prime numbers, which states that the sequence 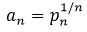 where
where  is the nth prime number, is strictly decreasing, and the prime gap function
is the nth prime number, is strictly decreasing, and the prime gap function  which is the difference between the nth and (n + 1)th prime numbers. Furthermore, Firoozbakht's conjecture is linked to upper limits for the prime gap function in terms of n. Asymptotic outcomes for both the conjecture and the function help us understand the interrelati...
which is the difference between the nth and (n + 1)th prime numbers. Furthermore, Firoozbakht's conjecture is linked to upper limits for the prime gap function in terms of n. Asymptotic outcomes for both the conjecture and the function help us understand the interrelati...
Law of Large Numbers
The law of large numbers is one of the intuitive laws in probability and statistics.
Table of contentsLaw of large numbersWeak Law of large numbersStrong Law of large numbersLaw of large numbers
In words, the law of large numbers states that As the number of trials or observations increases, the actual or observed average approaches the theoretical or expected average.
This makes it easier to predict how events will turn out in the long run and have confidence in our prediction made.
Ther...



