Richard Tubb's Blog, page 41
January 20, 2022
SuperSummit – Supercharge Your MSP’s Success
 A heads-up that the first ever SuperSummit for MSPs is taking place virtually on January 27th 2022!
A heads-up that the first ever SuperSummit for MSPs is taking place virtually on January 27th 2022!
The SuperSummit is organised by SuperOps.ai, who believe that everyone in the MSP world has stories to tell.
But some stories are shared less than others.
For example, the nightmarish stories of starting up for the first time, losing your biggest customer or having to let go of your best employee.
It’s these unspoken, powerful stories that will be uncovered at the SuperSummit.
And, I’m honoured to have been invited to be a part of the SuperSummit to share my story, too!
How To Scale Your MSP Business Through PartnershipsBefore selling up, I used to run my own Managed Service Provider (MSP) business.
I learned the hard way that no MSP business can be all things to all of your clients.
Therefore, at the SuperSummit, I’ll be sharing the story of how I scaled my business through partnerships with other technology companies.
I’ll be sharing exactly how these partnerships can:-
Mitigate the need to recruit staffIncrease the value of the deals you can closeBuild trust between you and your clientOn hand to ask the right questions of me in this session will be my old friend, Mark Crall of SuperOps.
Mark and I “grew up” in this industry running MSP businesses at the same time.
Therefore, I expect Mark to pull no punches in the questions he asks me! 
At the end of the session, I hope you’ll go away feeling confident and empowered to get started with scaling your own MSP business.
But Mark and I aren’t the only people sharing their stories at SuperSummit!
20+ MSP Expert Speakers in Three TracksSuperOps have secured 20+ MSP stalwarts speaking on three tracks – sales & marketing, scaling MSP operations, and starting an MSP in 2022.
Some of my fellow speakers include:-
Mark Copeman sharing how to make a great MSP websitePaul Green offering a peek at the number 1 MSP marketing channel in 2022Nigel Moore talking underrated marketing strategies for the modern MSPJoe Panettieri sharing the top ten MSP trends for 2022… plus Chris Timm, Ian Luckett, Marnie Stockman, James Vickery and more!
Phew, what a line up! 
Each talk is compressed with a 1-page actionable summary. At the end of each session, you can go back to their desks and start executing
Plus, did I mention that every MSP can refer 3 of your peers, and enter a lucky draw to win amazon vouchers worth $3,000!
How to Register for the SessionThe SuperSummit takes place on Thursday 27th January 2022.
The all-day event starts at 9am PT (5pm GMT) and registration is now open!
Therefore, make sure you register for the SuperSummit now!
Will There be a Recording?Yes! All sessions at the summit will be recording.
As a result, all attendees to the SuperSummit will be given lifetime access to all the speaker sessions.
If you register for the SuperSummit now, you’ll be notified when the recordings become available.
Get 2022 off to a Great Start!SuperOps.ai have put together an amazing line-up of speakers with some truly valuable content for you to take away.
As a result, I can tell you that I’m really looking forward to being a part of this event!
Do you have any questions for me or our other speakers? If so, leave me a comment below, or get in touch!
You Might Also be Interested inPodcast Interview with fellow SuperSummit speaker Paul Green: Why MSPs Need to Embrace MarketingPodcast Interview with fellow SuperSummit speaker Mark Copeman: How to be a Helpdesk Superhero.The List of Awesome Events for MSPsThe post SuperSummit – Supercharge Your MSP’s Success appeared first on Richard Tubb.


Why Network Monitoring for MSPs Is A Strong Opportunity
 Why is Networking Monitoring for MSPs a strong opportunity?
Why is Networking Monitoring for MSPs a strong opportunity?
When it comes to running a Managed Service Provider (MSP) business, any good MSP has a Remote Monitoring & Management (RMM) tool.
A good RMM tool will enable your MSP to manage endpoints such as servers, PCs and other workstations.
But when it comes to the infrastructure the devices work on — the network — many MSPs only have limited tools.
RMM vs Network Monitoring for MSPsIn terms of managing the network infrastructure, most MSPs are able to tell you which devices their RMM tells them are connected to the network.
However, if I asked most MSPs the following questions…
What type of traffic might be consuming the bandwidth on your clients network?Do you know which devices — other than PC’s and Servers — actually live on your clients networks?Are you able to manage Wide Area Network (WAN) and Local Area Network (LAN) activity?A traditional MSP might be scratching their heads to find answers.
This is not a knock on any MSP.
I would say that the job of managing the network has become exponentially more difficult in recent years.
Clients’ networks have sprawled over the past decade, with all manner of new devices and pain points being added.
Traditionally RMM tools help manage the PCs and servers on a network, but what about the network itself?
As a result, Network Monitoring for MSPs is a growth opportunity.

You could describe network monitoring for MSPs as a platform.
A good network monitoring platform enables an IT business to understand whether their client’s network is working in terms of performance, uptime and availability of endpoints.
In short, a network monitoring platform will empower an MSP into gaining full visibility into their clients’ networks.
Some features that differentiate network monitoring from traditional RMM tools include:-
Asset inventory and topology mappingReal-time automated device discoveryMonitoring for network switches, routers, load balancers, printers, firewalls, cameras, audio video systems and any other devices that have an IP address and which a traditional RMM tool can’t monitorYou might describe network monitoring for MSPs as a type of specialised remote monitoring & management for networks and network devices.
Let’s take a closer look at some of the features in network monitoring for MSPs and see how they are of benefit to an IT company.
Proactive Alerting and Network Monitoring for MSPs When you adopt a network monitoring platform, you are alerted to issues at a network and device level.
When you adopt a network monitoring platform, you are alerted to issues at a network and device level.
For instance, most network monitoring platforms include features such as:-
SNMP resource usage monitoringTCP service monitoringDevice response monitoringThis allows an MSP to receive alerts as issues are reported, and proactively resolve these issues.
For example — you’ve flagged the teleconferencing system in a clients board room as an “Important Device”.
Your network monitoring platform will tell you when it doesn’t get a response from the teleconferencing system, and, indeed, when it was last turned on.
As a result, you can proactively power cycle the system, meaning that when the client jumps on that all important video call, they aren’t calling you in frustration asking you to troubleshoot the failed system.
The above example is a very simple one, but it demonstrates the difference between being reactive and being proactive.
A good network monitoring platform will alert you to WAN and LAN performance measures, and produce statistics, alerts, and graphs to make sure your clients’ network infrastructures are performing at their best.
Network Inventory Asset Management Another good use of network monitoring for MSPs includes inventory and asset management.
Another good use of network monitoring for MSPs includes inventory and asset management.
While an RMM tool will typically have some sort of discovery process, this process often only highlights new workstations and servers.
However, a network monitoring platform will do real-time automated device discovery of anything that has an IP address on a local network, or a VLAN (or even a multi VLAN).
For a simple example, when running the Domotz Network Monitoring platform on my home network, I’m automatically notified when a new device connects to my network.
That device could be a visitor’s smartphone, or a new smart home appliance, or a video games console.
In the case of Domotz, the platform will automatically identify (using chipset manufacturer, MAC address or other discernable information) who made the device, and the model number (where applicable).
Domotz will also classify the device, to enable easy management of groups of devices, such as:-
Audio & VideoCameraDesktopHeating & CoolingNASNetwork EquipmentNotebooks/LaptopsPower SystemsPrinters and FaxesSecurity SystemsSensorServerSmartphonesSmart Power PlugTabletsVoice Control (such as Google Home and Amazon Alexa devices)
Domotz can even auto-categorise home automation devices, smart doorbells, media players, RoboVacs, smart watches, eBook readers and games consoles!
In addition, devices connected to managed switches and wireless access points (APs) are automatically detected and located.
Which leads us to another useful feature of a network monitoring platform.
Network Topology Mapping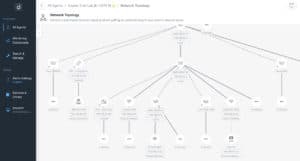 An example of a Domotz Network Topology report
An example of a Domotz Network Topology reportOnce your MSP business has started to gain full knowledge of the networks being managed, you have a wealth of useful information to assist you.
One of the most powerful ways to visualise this information is through network topology maping.
Network topology mapping provides full visibility and actionable insights on all network-based devices.
This information can be synchronised to your Professional Services Automation (PSA) tool or documentation platform.
It should become fairly apparent that having this real-time asset inventory system for your clients’ networks will also help your MSP with cybersecurity and compliance.
I can tell you from experience that, once you’re being made aware, in real-time, of new devices on your clients’ networks, then it becomes a lot easier to lock-down your clients against malicious players.
And talking of cybersecurity, another simple, but hugely powerful feature of network monitoring that is often overlooked is security scans.

 Let me ask you a question. Do you know which ports are open on your MSP’s office firewall?
Let me ask you a question. Do you know which ports are open on your MSP’s office firewall?
Probably, right?
What about your client sites?
Hopefully you’ve got the open ports documented, but are you really sure that list is up to date?
But what about those ports that your engineer opened for troubleshooting purposes, but forgot to close?
How about that client who insists on having admin access to the firewall, and then opens RDP to the world?
These are not uncommon situations for an MSP to face, and so one of the simplest but most powerful features of a network monitoring platform is the cybersecurity scan.
For instance, in real time, Domotz will do an open port scan of your clients’ networks and alert you to any existing open ports.
If the port is supposed to be open — great. You can let Domotz know that that open port is legit, and you won’t be bothered about it again.
But in speaking to many MSPs, they are shocked (and a little red-faced) to see the firewall ports that are open on their clients’ networks.
This ability to scan for security vulnerabilities can mean the difference between your clients being kept safe, and your MSP being held accountable for a preventable breach.
Furthermore, while we’re on the subject of unexpected device configuration changes, how does your MSP manage network device configurations?
Networking Device Configuration ManagementAs an MSP, you probably backup your clients’ data for them.
Plus, you may even have set a manual schedule (or recurring service desk ticket) to backup their network device configurations.
But, when it comes to troubleshooting a device in real time, it’s useful for an engineer to know what has changed recently.
A good network monitoring platform will automatically backup your network switch, firewall and router device configurations on a regular basis.
Plus, the platform will make it easy for you to restore a previous configuration when needed.
No more red faces for that engineer who made some changes during troubleshooting, but forgot to roll them back!

We’ve already talked about the relationship between a network monitoring platform and an RMM or PSA tool.
Any alerts that are generated by your network monitoring platform can raise a ticket in your PSA, or sent to your team via email or SMS.
As with any monitoring platform, you will need to find a balance between being swamped by alerts, and being alerted to the really important changes on your networks.
It’s worth being aware that most good network monitoring platforms will allow you to monitor device specific attributes such as:-
TemperatureConsumable Status (for example, toner in a printer)Packet Loss StatsWi-Fi signal levelSpeedPlus many more.
The ability to monitor the speed and bandwidth of devices is an interesting feature for MSPs, and can be turned into a powerful tool.
Speed Monitoring Most IT professionals are familiar with device response time monitoring.
Most IT professionals are familiar with device response time monitoring.
Therefore, it’s no surprise to know that a network monitoring platform has the ability to collect round trip delay (RTD) and packet lost stats for analysis.
But, if you run an MSP, then you’re also familiar with a support ticket being raised under the complaint of “The internet is running slowly”.
A good Network Monitoring platform will be able to help you monitor the external bandwidth being used between your client’s site and their Internet Service Provider (ISP).
Furthermore, though, you can also use your network monitoring platform to monitor internal device bandwidth.
For instance, if the conference room video conferencing service starts experiencing low bandwidth, then that causes real problems for video calls.
What if your MSP could quickly highlight any devices on a network (or network segment) that were hogging bandwidth, and dealing with them accordingly?
A good network monitoring platform will also store historical data, so that in addition to viewing real-time bandwidth, you can highlight problem devices over specific time periods in the past.
As a result, set parameters for “normal” behaviour and be alerted to any anomalies quickly.
Plus, you can report on this data.
As a result of this reporting, you can quickly help your clients to understand where they may need to invest in better internal networking equipment, or a fatter ISP pipe.

 I’ve written a lot about how a Network Monitoring platform allows you to monitor and be alerted to changes in clients network infrastructures.
I’ve written a lot about how a Network Monitoring platform allows you to monitor and be alerted to changes in clients network infrastructures.
But when it comes to taking action on those alerts, one feature that is very useful is a Virtual Private Network (VPN) on demand.
A VPN on demand will allow your engineers to quickly put their computer on the clients remote network.
As a result, your helpdesk can quickly access multiple network devices simultaneously and debug network issues.
This ability to quickly troubleshoot devices from the network monitoring platform itself is a powerful time saver for your MSP.
Security Camera MonitoringAnother valuable feature of a network monitoring platform that may not immediately become obvious to an MSP is the ability to monitor security cameras.
With physical security being more important to businesses than ever, many MSPs have found themselves trying to support IP-based security cameras without much specialist knowledge.
However, wouldn’t it be useful for your helpdesk to be able to monitor any IP camera?
I’m not just talking about checking whether the camera is online, but checking:-
Camera configurationOperation statusTest video outputPlus, the ability to restart cameras remotely.
When it comes to security cameras, treat them similarly to a backup.
MSPs are used to checking backups for working data.
But what if your client asked to review some IP-based security camera footage, and you had to tell them the device was online but not recording?
Network monitoring opens up a whole new area of device monitoring which can be both reassuring for clients, and lucrative for an MSP.

There are a number of network monitoring platforms available to MSPs and IT Solution Providers.
The two main players in the MSP space are Auvik Networks and Domotz.
Both of these platforms have their strengths in specific areas, so I’d encourage you to do your own research into which network monitoring platform is the best fit for you and your clients.
There are many other platforms available, though.
Therefore, some questions I’d encourage you to ask of any vendor during your discovery process are:-
Is your platform MSP friendly? (many platforms are built for internal IT departments)Can we manage multiple networks at multiple locations?What does your pricing look like?Do you offer desktop and mobile versions of your platform?What integration do you offer with other MSP tools such as RMM and PSA platforms?Do you offer a public API for third-party service connectivityCan my whole team get access to your platform, and if so, do you offer granular access?Does your platform use Two-Factor Authentication (2FA) for security?Is the platform easy to use? (You don’t want to buy a tool that is super powerful, but your team scratch their heads on actually using!)How many endpoints can your platform manage? Conclusion
ConclusionAny Managed Service Provider (MSP) or IT Solution Provider worth their salt already uses a Remote Monitoring & Management (RMM) tool.
But the scope of a typical RMM tool will limit itself to workstations and servers. It provides very little information on the multitude of other IP-based devices which attach to a modern network.
A Network Monitoring platform will offer your MSP business the ability to be aware of *all* devices attached to your clients networks, in real-time.
Furthermore, the platform will help you shore up your cybersecurity efforts by alerting you to any changes in real-time.
As a result, when it comes to Managed Services, an RMM tool alone is no longer enough to keep track of complex, modern networks.
I’d encourage you to become familiar with how a network monitoring platform can help your MSP business.
The benefits you’ll get from using a network monitoring platform can help give you a competitive advantage.
I’m intrigued to hear what you think. Do you already use a network monitoring platform? If not, what’s holding you back?
Leave a comment below or get in touch.

The post Why Network Monitoring for MSPs Is A Strong Opportunity appeared first on Richard Tubb.


January 11, 2022
The Reason WiFi Hacking is a Scary Threat to Your Business
 Do you ever consider the threat posed by WiFi Hacking?
Do you ever consider the threat posed by WiFi Hacking?
As the former owner of a Managed Service Provider (MSP) business, and somebody who has worked in the IT industry all my life, I consider myself quite cybersecurity savvy.
However, I realised I had become complacement in connecting to public WiFi hotspots.
And then, I started to become aware of the very real dangers of connecting to an unfamiliar WiFi signal.
Can you really trust free WiFi?The dangers of connecting to a free WiFi signal hit home for me a few years ago, when my wife and I were staying at a very nice Airbnb.
Free WiFi was provided by the owners, and shortly after we arrived, my wife and I needed to log in to our online banking to make a funds transfer.
I opened my laptop and logged onto the Airbnb provided WiFi.
Then, I opened a web browser and went to log on to our online banking when the thought suddenly hit me.
While I was treating the Airbnb WiFi as trustworthy and reliable — how did I really know that?
The truth hit me that, in reality, I couldn’t trust the WiFi and so needed to err on the side of caution.
As a result, since that time, I’ve taken my WiFi security seriously.
And if you don’t think the threat of WiFi security applies to you, I’d encourage you to read on…

Business owners are told that WIFI hacking is a real danger to their business, but if you see how it’s done, it really brings it home.
Here, Privatise employee Claudia (‘the hacker’) demonstrates a live hack, and it makes for fascinating (albeit scary) viewing!
 How a WiFi Hacker Works
How a WiFi Hacker WorksWIFI data is sent as easily-intercepted radio waves, and hackers use interception tools.
One such interception tool (the one seen in the demo above), a WiFi Pineapple, is cheap to buy and is frequently used by cybersecurity professionals.
Although there are several ways a hacker can compromise your system, the ‘hacker’ in this demo clones the wireless network and sets up an evil twin.

The hacker achieves this by firstly doing a site survey.
A site survey scans for and displays not only the wireless networks available, but the devices looking to connect to a wireless network.
As a result, the top four lines of code you’ll see in the video represent four open networks in the region of the hacker’s computer.
Within the pineapple interface, the ‘hacker’ creates a fake wireless access point that mimics one of the available networks.
This fake access point is created in the hopes that victims will connect to it.
In the ‘open SSID’ section of the video, the hacker enters one of the networks found in the site survey, reduces the maximum number of clients to five and then updates the access points before saving the configuration.
The pineapple’s radius restarts, emitting the cloned fake access point.
As you can see in the video demo, a phone and a tablet are used instead of a real client, and these are shown as connected in the dashboard.
NB: during the course of this demo, the ‘hacker’ ensured that no other devices could connect to the cloned network.
The ‘Evil Twin’ Hack The Evil Twin WiFi Hack. How do you know which WiFi Access Point is real?
The Evil Twin WiFi Hack. How do you know which WiFi Access Point is real?The ‘hacker’ runs a second site survey, and in the demo, you’ll see that the network addresses are on two different channels, but with the same Service Set Identifier (SSID).
If you look closely, you’ll see that the BSSID (MAC address) is different, but it can be spoofed to make it look exactly like the original network!
The real danger of connecting to an evil twin access point is that the ‘hacker’ can now see all the traffic coming through his network from the victim’s devices using a TCP dump.
In the demo video, traffic from the devices connected to the cloned network is visible, including from Facebook, YouTube and other sites.
The ‘hacker’ saves all of this information to review and exploit at a later date.
Potential Damage from a WiFi HackIn the video, the split screen shows the victim’s computer, a PC running Windows 10 and Chrome, on the right.
On the left, the ‘hacker’s’ computer is intercepting WIFI data via the pineapple.
The ‘hacker’ has added a ‘man in the middle’ proxy, which sits between the victim’s computer and the web and reads information from the victim’s machine.

The victim logs on to an Apple account, an Amazon Web Services management console and a WordPress admin area with their usual usernames and passwords.
It appears to the user that the sign-in has failed, but his information has successfully been captured on the hacker’s computer.
The ‘hacker’ then closes the hack session, the victim returns to a regular session and is able to log in as usual.
As a result, the user is none the wiser that their username and password have been stolen!
The reality is that their login details have been syphoned off and entered onto the ‘hacker’s’ network to be used at their convenience.
In five minutes, we’ve watched an extremely successful hack quickly set up and at minimal cost.
However, the victim may only find out they’ve been hacked at a later date when their compromised data is used.
How Can You Avoid WiFi Hacking?If the above scenario scares you (and it should do!) then you’re not alone.
How many hotel, coffee shop, pub or other public WiFi hotspots have you connected to under the assumption they are secure?
As a result of watching the video, you may be wondering how you can stay safe using WiFi.
The quickest method would probably be to avoid using free WiFi.
Instead, rely on connecting to the Internet via your smartphone’s 4G or 5G connectivity.
However, this is not always practical (or possible).
Therefore, one way to stay safe when connecting to a WiFi connection is to use a Virtual Private Network, or VPN.

 You can use a VPN tool to mitigate some risk when using a WiFi connection that you don’t trust.
You can use a VPN tool to mitigate some risk when using a WiFi connection that you don’t trust.
Very simply put, a VPN tool encrypts any data that is transmitted by your computer.
As a result of the encryption, your data is virtually unreadable by hackers.
I’ve written before about consumer-grade VPN tools including:-
ProtonVPN – Protect Your Privacy with a Free VPNExpressVPN – High-Speed, Secure & Anonymous VPN ServiceTunnelBear – VPN for ChromebooksMany of these tools are low-cost, or free to use.
Consumer tools like this could be recommended for friends or family. They will help them stay safe when away from the home or office.
However, if you’re an IT Solution Provider or Managed Service Provider, these consumer tools won’t be a good fit for your clients.
For example, you don’t want to be managing dozens, hundreds or even thousands of users working with different consumer products!
Therefore, if you’re an IT business, I’d recommend reading my article on How To Secure Clients with a Managed VPN for MSPs.
For instance, within my business, we use Privatise VPN.
Privatise is easy to deploy and manage for MSPs, and very easy to use for end-users.
ConclusionWhen it comes to WiFi security, the majority of us think that we would never become a target. However, the reality is that everybody is a target for Cybercriminals!
Therefore, when it comes to using any type of public WiFi connection you need to stay safe.
This public wifi connection might be a hotel, restaurant, coffee shop, pub, or even an Airbnb.
Using your 4G or 5G connectivity is safer than connecting to an untrusted WiFi connection. However, this is not always practical, and so I’d always recommend the use of a Virtual Private Network (VPN).
A VPN tool will encrypt your WiFi traffic, making your data inaccessible to hackers.
The bottom line here is, you cannot blindly trust WiFi connections. Hackers can, and will, easily fool you into giving up your confidential data via WiFi.
Make sure that you use a VPN tool and stay safe on WiFi!
I’m intrigued — have you experienced a WiFi hack? What are your thoughts on staying safe when away from your home or office?
Please, leave a comment below or get in touch.

The post The Reason WiFi Hacking is a Scary Threat to Your Business appeared first on Richard Tubb.


January 10, 2022
TubbTalk 103: Business for Good and How to Juggle Everything
Amanda Stewart is the managing director of Edinburgh-based MSP Illuminate, which supports local businesses  and charities. And the business has a very strong focus on putting MSP clients first, with customer service as their number one priority.
and charities. And the business has a very strong focus on putting MSP clients first, with customer service as their number one priority.
She started the business when her daughter was six months old to give herself the flexibility her employer wouldn’t.
Amanda says it’s been a lifestyle business so she can be available for her kids whenever they need her.
How Amanda Spots MSP Clients That Aren’t a Good FitClient satisfaction is a priority for Amanda, and she works with people who see their IT systems as important for their business. In 14 years, Illuminate has only parted ways with five MSP clients.
Amanda explains that she’s careful to choose clients whose ethos matches hers. “The people who come and ask for a price list and aren’t interested in what the tech can do for them aren’t right.
“Also anyone who’s negative about their previous IT support or fell out with them is a flag that makes me hesitant. It makes me think that the complaints aren’t really down to the other company.”
How to Talk about Cybersecurity with MSP ClientsAmanda says it’s a challenge to talk about cybersecurity without scaring your MSP clients. “They often switch off, so it’s hard to make them aware of the issues.” However, she adds that she’s worked with a number of people who have been hacked.
They come to Illuminate for help to make their systems more secure. Amanda explains the minimum requirements to keep them safe, and talks them through additional tools she recommends.
“I know they often have budget issues, so I work with them to see what’s affordable. But you need a good relationship with your MSP clients, because otherwise they think you’re just trying to sell to them. Education is the most important thing to stop cyber crime, so we focus on that.”
The Culture of Customer Service Within IlluminateCustomer service is important to Amanda, and she hires engineers based on how they’ll interact with clients. “Technical skills can be learned, but the soft skills are more important.”
Amanda makes sure the engineers communicate clearly and consistently with their MSP clients. She encourages them to put themselves in the customer’s shoes and imagine how they feel. Engineers keep clients in the loop about how they’re fixing problems.
Being a Woman in a Male-Dominated IndustryIn her early days in the IT industry, Amanda did get comments along the lines of “Oh, if you use that tool you might break a nail”, but she says it doesn’t happen as much anymore. Or she just doesn’t notice!
“Sometimes salespeople come into the business and speak to the men about tech. They assume I’m from sales or HR. Sexism still happens, but many men are conscious that it’s an issue, and are trying really hard for it not to be anymore.”
How Amanda Juggles Being a Mother and a Business OwnerIlluminate was founded to give Amanda flexible working, and she’s always been able to drop things to be there for her kids. “But it’s difficult. Women never think they’re doing it right. They either think they’re failing at being a mother or they’re failing at running a business.”
Juggling work and family commitments is stressful, Amanda says, but women are always doing a far better job than they give themselves credit for. “My wish is for women to stop making so many demands of themselves in the future. I want my daughter to know that some things have to give and that’s ok.”
Business for GoodIlluminate supports an organisation called Business for Good (B1G1). If a customer buys from you, you give something back. Amanda says it’s not a huge financial commitment, but once you sign up you choose causes to donate to.
“It could be a bookkeeping course for someone in Zambia, books for children in a third world country, or feeding a homeless person. At Christmas, each of our MSP clients gets a certificate to say where the donation has gone. We try to tie it to their business, so if they’re an architect it’s about hosting.
“If every small business got behind something like B1G1, we could eradicate a lot of the major issues in the world like homelessness and hunger. It’s a fantastic organisation to be involved in.”
How to Connect with Amanda StewartIlluminate ITFollow Illuminate IT on LinkedInConnect with Amanda on LinkedInHow to Connect With MeSubscribe to TubbTalk RSS feedSubscribe, rate and review TubbTalk in iTunesSubscribe, rate and review TubbTalk on Stitcher RadioSubscribe and rate TubbTalk on SpotifyFollow TubbTalk on iHeartRadioFollow @tubblog on TwitterMentioned in This EpisodeusecureBusiness for GoodCompTIAThe Tech TribeConnectWise EvolveFederation of Small BusinessesBritish Chambers of CommerceYou Might Also be Interested inPodcast: Advancing Women in ITIs Your Customer Service About Your Customer or is About You?How to Keep Your MSP Clients SafeThe post TubbTalk 103: Business for Good and How to Juggle Everything appeared first on Richard Tubb.


January 5, 2022
My 3 Words for 2022 And How They Motivate Me
 I’m a big fan of my friend Chris Brogan’s My 3 Words project.
I’m a big fan of my friend Chris Brogan’s My 3 Words project.
If you’re not familiar with the process, back in 2006, Chris started his year by choosing three words to serve as a guide for the upcoming year.
Chris has shared his 3 words every year since then.
The Three Words aren’t your goals, per se, but are more values to help you enjoy the year you want to have.
As a result, I’ve been using the 3 Words practice for a few years now.
The last time I shared my 3 words publicly was during My 2018 Year in Review And How It’s Done.
Therefore, for 2022, I thought I’d share my words publicly again.
I hope that in doing so, it might inspire you to think about how you craft your year ahead!
My 3 Words for 2022My words for 2022 are:-
SubtractTo give me more margin and to add to the quality of my life, I will subtract the tasks, obligations, people and items that no longer bring me joy.ForgivenessTo improve my peace and wellbeing, I will forgive myself and other people for things that haven’t gone as I would have liked.FunTo increase my happiness, I will commit time to doing more things that nourish me personally and professionally.How to use your 3 Words Photo by Vek Labs on Unsplash
Photo by Vek Labs on UnsplashI’ve learned that my words act as a guide.
As a result, any time you think you need think you need a reminder of what you’re aiming to achieve, you can review your 3 words.
For instance, I have my 3 words printed and pinned to my main work desk. The words act as a daily reminder to myself.
If you’d like to learn more about the process, then Chris Brogan gives an excellent overview on his blog.
What are YOUR words for 2022?Now, it’s over to you!
What are your 3 words for 2022?
Remember that, as always, I’d love to hear from you. You can get in touch with me, or share more about your words in the comments below.
For instance, feel free to share a link below to a blog post with more about your words.
Plus, if you need some inspiration, other people are already sharing their three words on social media with the hashtag #my3words.
Here’s to a heathy and happy 2022 for us all!
You Might Also Be Interested InThree Questions To Ask Yourself Before Setting Your New Years GoalsWhy you should write down your goalsPerseverance and Consistency = SuccessThe post My 3 Words for 2022 And How They Motivate Me appeared first on Richard Tubb.


December 20, 2021
TubbTalk 102: How to Niche Your MSP and Navigate M&As

Nancy Sabino is the VP of Sales and Marketing for Synetek Solutions. They’re an integrated, outsourced IT  department in Texas. Previously, Nancy was CEO of SabinoCompTech, a niche MSP.
department in Texas. Previously, Nancy was CEO of SabinoCompTech, a niche MSP.
SabinoCompTech has recently merged with Synetek Solutions. Nancy explains that when she and her husband and business partner set up their MSP the goal was to sell it at some point.
They both had roles that they could step out of and let other people take over. And they had processes in place to make this as easy as possible.
Why Nancy uses the Niche Term Outsourced IT DepartmentNancy explains that she pays attention to the language people use when talking about the services her business provides. “When they talked about us, they didn’t say we were their MSP. They called us their IT department.”
Saying they had a team was an ego boost to her clients. But it also let them feel that the company was integrated. So, Nancy adopted that and described it as an extension to the client business – outsourced IT.
Why Nancy Chose to Niche into Compliance StrategySabinoCompTech was based in Houston, where there are lots of private health care organisations. In the US, they have to follow HIPAA guidelines regarding data sharing.
Nancy realised that there wasn’t a lot of support to help those businesses stay compliant. So, they built a platform to do that. As well as healthcare providers, accounting and law firms also have to be HIPAA compliant. They helped with the tech and carried out security risk assessments.
Why might a niche help your MSP to grow? This blog might help.
The Best and Worst Parts of Running an MSPNancy says the best bit is the people she meets and works with. As a teenager, she was an early adopter of the latest tech and interested in the user experience. She now brings that into her own business to ensure customers get a great tech experience.
She also admits that people can be the worst part of the job, too. “Business owners don’t always prioritise tech. They don’t keep things updated. So, it’s something I try to educate our customers on consistently. Otherwise, it’s frustrating.”
What it’s Like Working with Your HusbandNancy and her husband, Angel, have been together since high school and set up their first business when they were quite young. She says they’ve had to learn to work together and be a team.
“The balance of work and home sometimes is non-existent. The kids help a lot to remind us that we have a life outside of work. It’s difficult, but we do manage to have time where we don’t talk about work. It’s hard but definitely doable.”
Why Nancy Thinks Branding is Important for MSPsNancy says people often think of branding as a logo and company colours, which of course is part of it. But she feels it’s really the soul of the business. If you get it wrong, your business won’t come across right.
“It’s an unspoken language between every aspect of your company and how it comes across to your customers. And then you add the pretty bits on top, which is what we usually think branding is.”
Encouraging More Girls into TechWhen she started in the tech industry, Nancy felt intimidated. Imposter syndrome made her feel like an outsider. But she was soon part of supportive communities. And there are a lot of women in the space now, who help each other.
She was the president of Nerdy Girl Success for a while. The charity supports young girls and women to consider STEM as a career. “You need to give exposure to them so they know they can fit in and find a place.”
Nancy still mentors and speaks to girls about her own experience in the MSP world. She recommends that IT and tech companies are welcoming and encourage young women who are interested in being part of the sector.
How to Connect with Nancy SabinoSynetek SolutionsFollow Synetek Solutions on LinkedInConnect with Nancy on LinkedInFollow Nancy on TwitterSabinoCompTech on YouTubeHow to Connect with MeSubscribe to TubbTalk RSS feedSubscribe, rate and review TubbTalk in iTunesSubscribe, rate and review TubbTalk on Stitcher RadioSubscribe and rate TubbTalk on SpotifyFollow TubbTalk on iHeartRadioFollow @tubblog on TwitterMentioned in This EpisodeKaseyaThe Tech TribeKirthana Ramisetti Dava Shastri's Last Day Jim Collins Good To Great: Why Some Companies Make the Leap... and Others Don't ASCIIChannelFutures 501Podcast: IT4WhiskeyChannelPro NetworkNerdy Girl SuccessYou Might Also be Interested inPodcast: How an MSP can Thrive in the Security NicheWhy do IT Outsourcers not Outsource More?Podcast: Why Personal Branding is Important for Standing out in the MSP SpaceThe post TubbTalk 102: How to Niche Your MSP and Navigate M&As appeared first on Richard Tubb.


December 15, 2021
The 2022 List of Awesome Events for MSPs
 Each year I produce a list of events for MSPs. I’ve attended many of these events myself, and they are indeed awesome!
Each year I produce a list of events for MSPs. I’ve attended many of these events myself, and they are indeed awesome!
These events are all conferences and meetings that will be of interest to IT Solution Providers and Managed Service Providers (MSPs) based in the UK and Europe.
All dates are subject to change and I’d strongly encourage you to contact the event organisers directly before making any travel plans based on the information listed here.
NotesFor readers in the USA and Canada, my good friend Karl Palachuk has a great MSP event listing in Karl’s Weekly Email Newsletter.I also publish a list of User Groups for UK Managed Service Providers that are of interest to MSPs.To receive a regularly updated list of events by email, sign up for my weekly MSP Insights email. You can take a look at the events I’m attending as well as events I’m speaking at. If you’d like to engage me to present at or report from your own event, please feel free to contact me to discuss my availability.Updates and AmendmentsI try to keep this list regularly updated, so if you have an event then please feel free to contact me and let me know about it.
Last Edit: 16th December 2021.
Annual IT Channel Events2022Jan 6th 2022 – Tribal Gathering Behind The Geeks Show with Nigel Moore, Richard Tubb, Pete Matheson– Virtual EventJan 12th 2022 – Giacom/Microsoft – Maximising Your MS Partnership – WebinarJan 13th 2022 – Tribal Gathering Behind The Geeks Show with Nigel Moore, Richard Tubb, Pete Matheson– Virtual EventJan 20th 2022 – CompTIA Benelux Business Technology Community Meeting – AmsterdamJan 26th 2022 – Pax8 – The Latest in the Microsoft New Commerce Experience – WebinarMarch 2nd-3rd 2022 – Cloud Expo Europe – LondonMarch 4th 2022 – National day of UnpluggingMarch 9th 2022 – Giacom/Microsoft – Incentives Workshop – WebinarMarch 30th-31st 2022 – Channel Live – BirminghamMay 11th-12th 2022 – Service Deskshow – ExCeL LondonJune 12th-16th 2022 – Cisco Live 2022 Las Vegas – Las Vegas, United StatesJune 21st-23rd 2022 – Info Security Europe – ExCeL LondonCan you help?Will you be attending any of these events?
Do you have an event that you feel should be included in this list?
If so, please get in touch!
You Might Also Be Interested In3 Good Reasons to attend your local User Group MeetingA list of User Groups for UK Managed Service ProvidersA list of Professional Service Automation tools for MSPsThe post The 2022 List of Awesome Events for MSPs appeared first on Richard Tubb.


December 13, 2021
TubbTalk 101: How to Build and Grow a Thriving MSP as a One-Woman-Band
 Diana Giles is the president and owner of Skyline IT Management, an MSP based in Oklahoma.
Diana Giles is the president and owner of Skyline IT Management, an MSP based in Oklahoma. 
And, she’s also the founder of sensible cyber parenting.com. It’s a free resource website to help parents protect their children online.
Diana got into IT by accident after her degree – she was always the go-to person in the office to fix computing problems. And she enjoyed it so much that she decided to make it her career.
The Challenges of Being a One-Man Band MSPDiana says the most challenging thing is when she needs to be in several places at once. She adds that she strives to provide good service, so sometimes she rushes to get work done that isn’t that urgent for the client.
“I have to see if it’s really necessary or if it can wait. And having an outsourced helpdesk makes a difference. I can respond quickly to people even if I’m tied up with other work.”
How Diana Spots Potential Clients Who Aren’t a Good FitMany MSPs will write someone off immediately if they mention price straight away. However, Diana says if that’s their only focus it’s a red flag. “And another one is if they have really outdated technology.
“They’re not interested in upgrading. They just want to manage with what they’ve got. Limping along with unsupported operating systems is bad for them and for you. It’s better if they know they need help to upgrade.”
The Most Challenging Part of Running an MSPLike many MSP owners, Diana admits that sales are hard. She got plenty of referrals but she wasn’t as busy as she wanted to be. And she didn’t do any marketing, but things ticked over.
Most SMBS are loyal to their IT support person until something goes wrong and they need someone else. But getting people to switch provider is hard. The other challenge is security. “Especially now, because we’re all thinking about it all the time.”
Being a Female MSP Owner in a Male-Dominated SpaceDiana is often the only woman in the room when she goes to events. However, she says that has never been a problem. When she started in the industry in the 90s, she was hired by a woman. And half of her colleagues were women too.
“There don’t seem to be many women business owners around. But I’m not sure what the solution is. Because I don’t think they’re being left out intentionally. So maybe they aren’t interested in the industry.
“It would be good to have more women around. I think I have more patience in some situations. But asserting authority is easier for men. We all have different strengths that we bring to the table.”
Being a Mother and Running a Successful MSPDiana has always managed to make being a mother and a business owner. But she admits there were times she had to take the kids with her. Or drop them at her husband’s office.
She did most of her work when the children were at school, but her plan was to build a lifestyle business. So she was as busy as she wanted to be. “But there were still times when I was pulled in different directions. And the kids did their homework in customers’ offices sometimes!”
The Sensible Cyber Parenting WebsiteOn a few occasions, Diana has helped clients and friends whose child had been exposed to undesirable content. Or even become addicted to pornography or similar and had a problem.
Diana stepped in and securing the device to prevent the young person accessing harmful material. She had to work hard to keep her own kids safe, so she realised that there were less techy parents who would really struggle to do the same.
“I could set the security up for them, but sometimes another problem would occur with the computer. And the parents have no idea what to do. So, I wanted to empower them to do it themselves. The website is designed to provide them with the right resources.”
How to Connect With Diana GilesSkyline IT ManagementFollow Diana on FacebookConnect with Diana on LinkedInHow to Connect With MeSubscribe to TubbTalk RSS feedSubscribe, rate and review TubbTalk in iTunesSubscribe, rate and review TubbTalk on Stitcher RadioSubscribe and rate TubbTalk on SpotifyFollow TubbTalk on iHeartRadioFollow @tubblog on TwitterMentioned in This EpisodeTo DoBook: Richard Tubb: The IT Business Owner's Survival Guide: How to save time, avoid stress and build a successful IT business CompTIAThe Tech TribePax8Sensible Cyber ParentingYou Might Also be Interested inVideo: Best Practices for Running a Successful MSPDinoPass: Password Generator for KidsPodcast: Advancing Women in ITThe post TubbTalk 101: How to Build and Grow a Thriving MSP as a One-Woman-Band appeared first on Richard Tubb.


December 6, 2021
TubbTalk 100: Tomorrow’s World, Teen Tech Initiative and Encouraging Girls in Tech
Maggie Philbin, OBE, has worked in radio and television for over 30 years on a wide range of science, medical and  tech programmes from Tomorrow’s World to Bang Goes the Theory.
tech programmes from Tomorrow’s World to Bang Goes the Theory.
In 2008, she co-founded TeenTech, an award-winning organisation which works across the UK getting young people innovating, creating building skills and preparing for a fast-changing future.
They help young people to improve their technology and digital skills. And they support them to find career opportunities in a range of organisations within their local area.
The Role the UK Government Plays in Encouraging Young People into STEMMaggie tells me the government needs a serious rethink about what happens in schools. There are challenges on every front, especially poverty, education, health and equality.
Young people can’t always see the point of what they’re learning. Schools should be able to educate students to be the kind of employees who will succeed in the workplace. The pressure of exams means students don’t realise their own potential.
The government should support a seismic change in how schools approach learning. And teachers should be supported to help young people learn things that are relevant for the 21st century.
How Young People View IT and TechMany young people don’t know a lot about IT, and so their enthusiasm varies. If they know someone who works in tech, they have a better idea about what might be possible for them.
Maggie adds that once they do know about the opportunities available, there’s no stopping them. They become really enthusiastic because they see it’s an important area. And they see that they could do something and make a difference.
How Business Owners can Encourage Young Women into the IT IndustryMaggie thinks the majority of businesses don’t set out to exclude women. There is a retention issue, though. And the higher up the organisation you go, the fewer women there are.
Sometimes there’s a culture of promoting men, too. When you’re advertising for a role, make it clear you’re flexible around childcare and so on. Some roles require specific skills that take years to acquire. But most don’t, so let people learn on the job. Does one person really need to do lots of tasks?
What Maggie Finds Exciting in the Tech Space“5G has the potential to be a game-changer in so many industries. For instance, if you play games but you only do it at home plugged in. 5G has such low latency that everything speeds up. And lots of people can do things at the same time.”
Another example Maggie gives is the music industry, which has a very heavy carbon footprint. With technology, you could have a gig in your local pub. The bass player is there in person but the singer is in Mexico. These things are a real possibility.
Why Maggie was Attracted to a Career in TechWhen it comes to tech, Maggie says it’s not about the widgets; it’s about the people. They’re all trying to solve problems. “Until I did Tomorrow’s World, I hadn’t realised how many problems existed.
“People had seemingly wacky inventions that were actually really needed. One guy had a light-up fishing rod. Because you can’t see your rod in the dark! The innovation and tenacity of these inventors was so inspiring.”
If you’ve never seen Tomorrow’s World, then you might enjoy this compilation!
Quick Fire TubbTalk Listener Questions Craig Sharp: Do you think we as a society have lost the wow factor on tech?One big difference between when Maggie did Tomorrow’s World and now is the internet. It allows people a window into what’s going on in the world, and that wasn’t possible in the 1980s.
Another major difference, she says, is around secrecy. “We always showed products that were in prototype. Partly because the inventors hoped they might get funding from a viewer at home. Now, we focus on the latest iPhone iteration, and it’s kept secret.”
Tracy Pound: What can we do to support men looking to increase gender diversity in their business?Men need to be part of the conversation. Sometimes, Maggie says, businesses want to achieve diversity. But they don’t want to change things to get there. You need to be committed to making improvements.
Sometimes, a cultural shift is what’s needed. “What makes a difference to women? Can you offer part-time or flexible working? People have all kinds of priorities in their lives. And ALWAYS value your talent.”
Polly Brennan: Does Maggie think robots and AI will ever replace humans at work, leaving us to pursue a life of pure adventure?The idea was that robots would give us a life of freedom, but they just create more work. But the pandemic has encouraged people to re-evaluate what matters. And they see they’d like to work less and spend time with their loved ones. But robots probably won’t make that happen.
David Miller: Will we ever be able to transfer electricity via a wireless medium?“Yes, definitely. There’s been some very interesting early experiments into this. But I couldn’t say when it’ll happen.”
David Withington: What was your reaction when you first saw smartphones?“We saw things like cell phones on Tomorrow’s World. We heard all the time about having a computer in our pockets. That seemed unfeasible, because computers were huge! And so were mobile phones, so I didn’t imagine that was how it would work.”
Pascal Fintoni: Which sci fi TV or movie franchise would Maggie like to have starred in?“I would have quite liked to have been in Doctor Who, because that was something I watched as a child. Or in Star Trek. I might not have been very good at it, but it would have been fun.”
Col Gray: Was Maggie always interested in science and tech, or was it her presenting role on Tomorrow’s World that got her interested in the subject?“As a teenager I wanted to be a vet, and I was interested in the sciences. But unfortunately I wasn’t good at chemistry. So I switched to the arts, and worked in TV. The Tomorrow’s World role came out of the blue but it was a happy combination of what I was good at and what I was interested in.”
Gudrun Lauret: What was the most ridiculous invention you saw, and which didn’t make it that you wish had?“Those two things are often the same. The piece of technology I demonstrated that I thought wouldn’t go anywhere was car navigation. Because we had that before we had the satellite bit.
“There was a huge board on the windscreen with a computer in the boot. It didn’t seem practical. Once they had the satellite and made it smaller, then it worked.”
How to Connect with Maggie PhilbinMaggie’s websiteFollow Maggie on TwitterHow to Connect with MeSubscribe to TubbTalk RSS feedSubscribe, rate and review TubbTalk in iTunesSubscribe, rate and review TubbTalk on Stitcher RadioSubscribe and rate TubbTalk on SpotifyFollow TubbTalk on iHeartRadioFollow @tubblog on TwitterMentioned in This EpisodeTeenTechTeenTech Live NewcastleTomorrow’s WorldComputer Weekly Most Influential Women in Tech listNorthern Power WomenYou Might Also be Interested inPodcast: How the Government is Helping Women get Ahead in TechnologyCelebrating Five Amazing Women in Tech for International Women’s DayPodcast: Advancing Women in ITThe post TubbTalk 100: Tomorrow’s World, Teen Tech Initiative and Encouraging Girls in Tech appeared first on Richard Tubb.


November 30, 2021
National Computer Security Day: How to Keep Your MSP Clients Safe
As today is National Computer Security Day, following on from Cyber Monday, I thought it would be a good opportunity to share top tips. I’ve pulled together some advice from my TubbTalk guests, who are all experts in their fields.
We’re looking at what you can do to keep your MSP clients safe and encourage them into best practices. We also reflect on the importance of training, and why you need to be proactive.
The Future of CyberSecurity for MSPs(TubbTalk 78.5 with Rafi Ozick of Privatise)In the wake of the Covid pandemic, more employees are working from home than ever before. The MSP is responsible for ensuring the security of office and home based staff, as well as those who adopt the hybrid model. The MSP is also the gateway to hackers gaining access to all of their clients, so they need to reduce their own vulnerabilities.
Hybrid working is the future. Rafi explains that remote work and cybersecurity isn’t just a growth area anymore, but a survival factor. “The big growth factor in cybersecurity is really securing people who are not necessarily in the office or software based.”
Privatise offer a full stack network security solution for MSPs.

 Why MSPs Fail at Security Before a Breach Even Happens(TubbTalk 90 with Ian Thornton-Trump)
Why MSPs Fail at Security Before a Breach Even Happens(TubbTalk 90 with Ian Thornton-Trump)MSPs work on both preventative and reactive measures when it comes to cybersecurity, but the focus tends to be on reacting. Ian says the sooner you detect a breach, the less it will cost the client.
“Instead of reacting when the customer has a ransomware attack, what can you do to anticipate it and prevent it happening?
“Listen to what’s being talked about, pay attention to how other businesses are getting hurt and don’t let that happen to your businesses.”
Ian Thornton-Trump is CSO of Cyjax, a threat intelligence and cybersecurity company
How MSPs can Educate Their Clients about Ransomware Security(TubbTalk 91 with Fabian Wosar)Education is difficult, says Fabian. “If we could figure out effective ways to do it, then ransomware would be much less of an issue than it is. There are lots of resources you can use and share with your clients.”
Fabian also recommends supporting clients to build a playbook to outline how they would respond to a cyber hack. Having that ready will make things less stressful if the worst does happen.
Fabian Wosar is CTO of Emsisoft, who provide antivirus and antimalware software.

It’s understandable that people use the same password, because they’re difficult to remember, says Chris. To help your clients, ensure that people use unique passwords for every application and service. “You’re only as secure as your weakest password.”
Chris says that when it comes to password management, MYKI’s competition is not another tool but no password manager at all. They try to educate MSPs, SMBs and end users that they should use some sort of password manager.
Chris Tate is global strategic alliance director at MYKI. They offer a 2FA and password management solution.
Email Security Trends(TubbTalk 97 with Olesia Klevchuk)Email threats are increasing in complexity and succeeding quite a lot of times. Hackers have moved from spam and malware to emails that look genuine. They no longer rely on a spray and pray approach – they target an individual.
They’re organised and have a lot of resources at their disposal. “They research their targets carefully. And, the focus is no long getting inside and causing havoc – the hackers want money, and usually a lot of money.” Detection isn’t enough, because one day the email gets through. Then, you need a quick response to the attack.
Olesia Klevchuk is the Principal Product Marketing Manager for Email Security at Barracuda Networks, a cybersecurity company.
What are your thoughts on security? What measures do you have in place in your MSP or what will you introduce after reading this post?
You Might Also be Interested inHave I Been Pwned?Powerful Insights from the Future of the MSP and Security SurveyWorld Password Day: Advice for MSPsThe post National Computer Security Day: How to Keep Your MSP Clients Safe appeared first on Richard Tubb.